A Detailed Look at RFC 8446 (a.k.a. TLS 1.3)
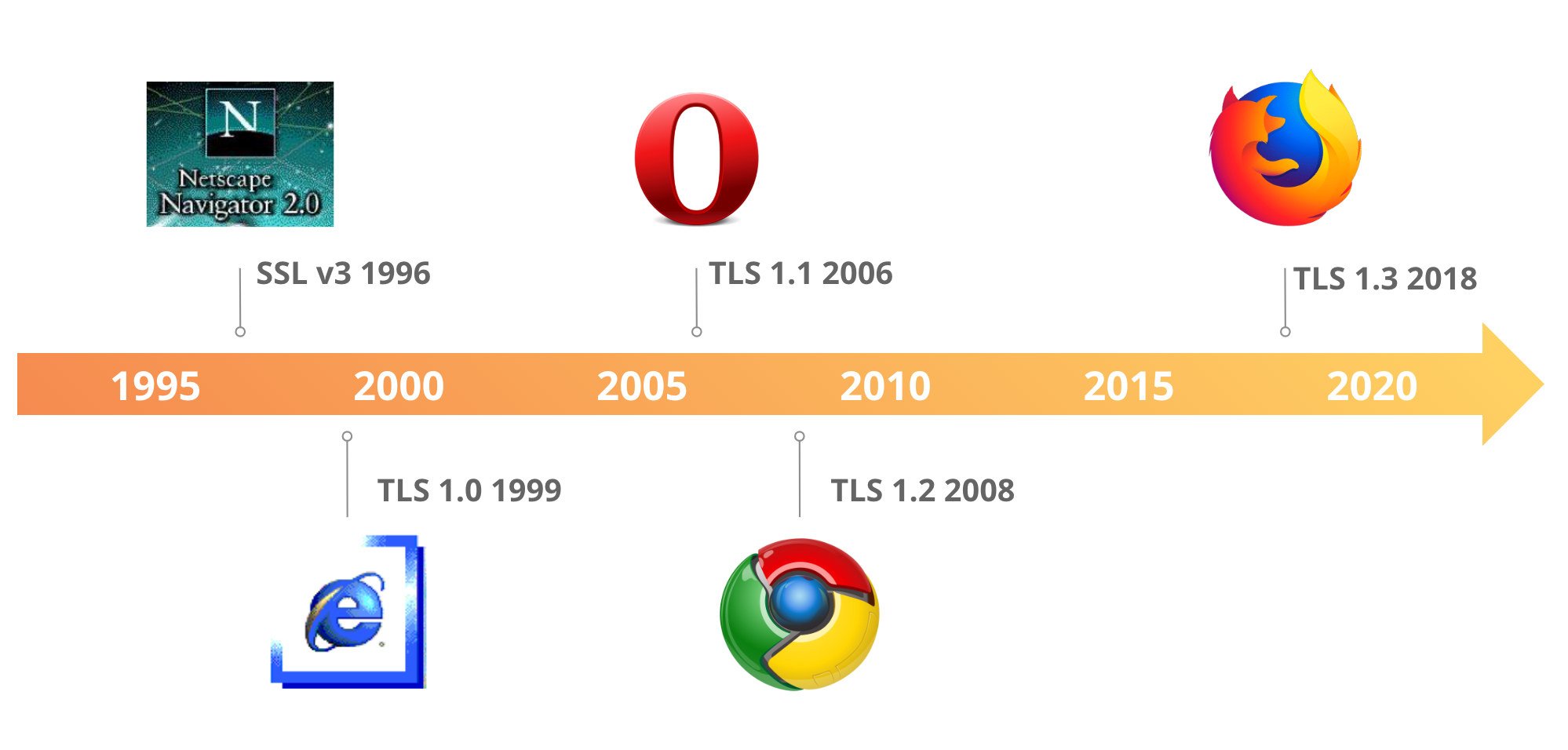
For the last five years, the Internet Engineering Task Force (IETF), the standards body that defines internet protocols, has been working on standardizing the latest version of one of its most important security protocols: Transport Layer Security (TLS). TLS is used to secure the web (and much more!), providing encryption and ensuring the authenticity of every HTTPS website and API. The latest version of TLS, TLS 1.3 (RFC 8446) was published today. It is the first major overhaul of the protocol, bringing significant security and performance improvements. This article provides a deep dive into the changes introduced in TLS 1.3 and its impact on the future of internet security.
An evolution
One major way Cloudflare provides security is by supporting HTTPS for websites and web services such as APIs. With HTTPS (the “S” stands for secure) the communication between your browser and the server travels over an encrypted and authenticated channel. Serving your content over HTTPS instead of HTTP provides confidence to the visitor that the content they see is presented by the legitimate content owner and that the communication is safe from eavesdropping. This is a big deal in a world where online privacy Continue reading
 Respondents to IHS Markit’s survey indicated they expect a 1.5x increase in the average number of physical servers in their data centers by 2019.
Respondents to IHS Markit’s survey indicated they expect a 1.5x increase in the average number of physical servers in their data centers by 2019.


 The investment plans include producing equipment stateside to be closer to its customers, opening a new software development center, and hiring several hundred employees.
The investment plans include producing equipment stateside to be closer to its customers, opening a new software development center, and hiring several hundred employees. Oracle debuts another autonomous database cloud service; Facebook open sources its transport layer security library; and AWS rolls out serverless option for Amazon Aurora.
Oracle debuts another autonomous database cloud service; Facebook open sources its transport layer security library; and AWS rolls out serverless option for Amazon Aurora. The security company that spun out of Alphabet’s secretive X research lab in January still hasn’t set a release date for its analytics platform.
The security company that spun out of Alphabet’s secretive X research lab in January still hasn’t set a release date for its analytics platform.




