Reducing DRAM footprint with NVM in Facebook
Reducing DRAM footprint with NVM in Facebook Eisenman et al., EuroSys’18
(If you don’t have ACM Digital Library access, the paper can be accessed either by following the link above directly from The Morning Paper blog site).
…to the best of our knowledge, this is the first study on the usage of NVM devices in a commercial data center environment.
We’ve been watching NVM coming for some time now, so it’s exciting to see a paper describing its adoption within Facebook. MyRocks is Facebook’s primary MySQL database, and is used to store petabytes of data and to serve real-time user activities. MyRocks uses RocksDB as the storage engine, and a typical server consumes 128GB of DRAM and 3 TB of flash. It all seems to work well, so what’s the problem? Spiralling costs!
As DRAM facing major scaling challenges, its bit supply growth rate has experienced a historic low. Together with the growing demand for DRAM, these trends have led to problems in global supply, increasing total cost of ownership (TCO) for data center providers. Over the last year, for example, the average DRAM DDR4 price has increased by 2.3x.
Just using less DRAM per server Continue reading
 C-V2X is a 3GPP-based cellular standard that is intended to help vehicles by using a cellular-like network to perform a variety of tasks including delivering real-time traffic reports, diagnostics, and emergency calls. It is also compatible with 5G.
C-V2X is a 3GPP-based cellular standard that is intended to help vehicles by using a cellular-like network to perform a variety of tasks including delivering real-time traffic reports, diagnostics, and emergency calls. It is also compatible with 5G. PacketFabric’s network could potentially provide underlying network transport for an SD-WAN vendor such as Aryaka.
PacketFabric’s network could potentially provide underlying network transport for an SD-WAN vendor such as Aryaka. Past acquisitions by Microsoft have fueled heated responses on social media to the latest multibillion-dollar deal.
Past acquisitions by Microsoft have fueled heated responses on social media to the latest multibillion-dollar deal. A recent Dell’Oro report found that the prevalence of 5G has triggered strong growth within the NFV market, specifically with cloud native VNFs.
A recent Dell’Oro report found that the prevalence of 5G has triggered strong growth within the NFV market, specifically with cloud native VNFs.
 The switches are not only programmable, they're re-programmable, making them available for future use cases, using the same device.
The switches are not only programmable, they're re-programmable, making them available for future use cases, using the same device. The company partnered with Microsoft, AWS, Pivotal, and Docker to determine how to take its low-code philosophy to containers.
The company partnered with Microsoft, AWS, Pivotal, and Docker to determine how to take its low-code philosophy to containers.
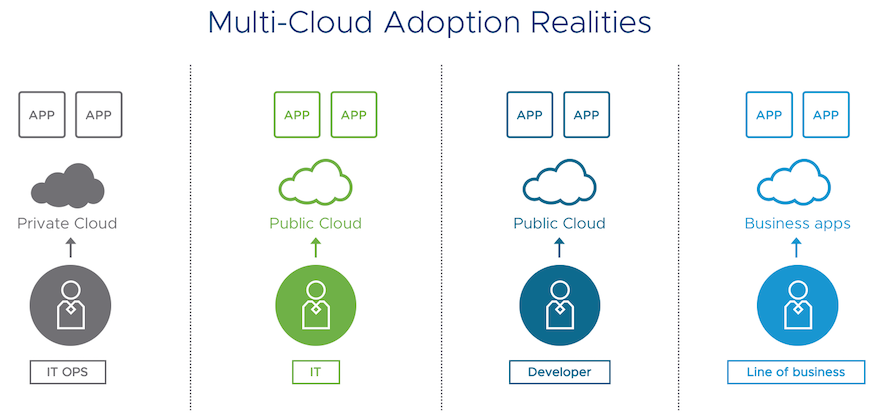
 A new white paper from Zscaler introduces a powerful solution for providing an efficient and secure experience between users and cloud/SaaS.
A new white paper from Zscaler introduces a powerful solution for providing an efficient and secure experience between users and cloud/SaaS.