Linux Foundation Creates Open Source Event for Wall Street
 Blockchain, alone, should drive attendance at this event.
Blockchain, alone, should drive attendance at this event.
 Blockchain, alone, should drive attendance at this event.
Blockchain, alone, should drive attendance at this event.
On today’s podcast episode of “The Interview” with The Next Platform, we talk about exascale power and resiliency by way of a historical overview of architectures with long-time HPC researcher, Dr. Robert Fowler.
Fowler’s career in HPC began at his alma mater, Harvard in the early seventies with scientific codes and expanded across the decades to include roles at several universities, including the University of Washington, the University of Rochester, Rice University, and most recently, RENCI at the University of North Carolina at Chapel Hill where he spearheads high performance computing initiatives and projects, including one we will …
Looking Back: The Evolution of HPC Power, Efficiency and Reliability was written by Nicole Hemsoth at The Next Platform.
The field of competitors looking to bring exascale-capable computers to the market is a somewhat crowded one, but the United States and China continue to be the ones that most eyes are on.
It’s a clash of an established global superpower and another one on the rise, and one that that envelopes a struggle for economic, commercial and military advantages and a healthy dose of national pride. And because of these two countries, the future of exascale computing – which to a large extent to this point has been more about discussion, theory and promise – will come into sharper …
A Look at What’s in Store for China’s Tianhe-2A Supercomputer was written by Jeffrey Burt at The Next Platform.
 A new white paper by ACG Research focuses on the data center (DC) switching infrastructure aspect of that ecosystem, showing that Lenovo’s switching combined with server solutions provide for the full spectrum for a data center strategy for enterprises and cloud providers.
A new white paper by ACG Research focuses on the data center (DC) switching infrastructure aspect of that ecosystem, showing that Lenovo’s switching combined with server solutions provide for the full spectrum for a data center strategy for enterprises and cloud providers.
In case you missed it, DockerCon 2018 will take place at Moscone Center in San Francisco, CA on June 13-15, 2018. DockerCon is where the Docker community comes to learn, belong, and collaborate. Attendees are a mix of beginner, intermediate and advanced users who are all looking to level up their skills and go home inspired. With a 2 full days of training, more than 100 sessions, free workshops and hands-on labs, and the wealth of experience brought by each attendee, DockerCon is the place to be if you’re looking to learn Docker in 2018.
Want to go but need information to convince your manager? Here is a document to help you build a case for it including content, budget and reasons why you should attend.
From beginner to experts, DockerCon brings together the brightest minds to talk about all things containers including Docker Platform, Kubernetes, Digital Transformation in the Enterprise, Moby and CNCF projects, Container Security, Service Mesh and more. Although the full schedule won’t be announced until the end of the month, below is a sneak peak of some of the sessions we have lined Continue reading
In this History of Networking episode of Network Collective, Joel Halpern joins us to talk about the history of network modeling and policy based management in the standards bodies.
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post History Of Networking – Joel Halpern – Policy Based Management appeared first on Network Collective.
 Excellent piece on psychology of being a technology worker. MUST READ. For those of us who work in technology, we pride ourselves in our rationalism. We deal in the territory of binary math, algorithms, and logic. Yet we often fail to step back and see ourselves as mere mortals. We acknowledge some disciplines suffer from […]
Excellent piece on psychology of being a technology worker. MUST READ. For those of us who work in technology, we pride ourselves in our rationalism. We deal in the territory of binary math, algorithms, and logic. Yet we often fail to step back and see ourselves as mere mortals. We acknowledge some disciplines suffer from […] The company’s edge software aims to secure and manage IoT devices.
The company’s edge software aims to secure and manage IoT devices.
In the rush to the cloud, organizations may be tempted to simply move applications from their private data centers to the public cloud. In this video, Keith Townsend, principal at The CTO Advisor and Interop ITX infrastructure chair, discusses issues associated with lift-and-shift cloud migration, including security and cost.
Years ago, I decided to try out another idea: solving real-life challenges with the help of an easy-to-consume online consulting service. When I discussed the idea with my friends during one of the early Networking Field Day events the opinion was pretty unanimous: “this will never work”
Fortunately, they were wrong. Not only did ~100 customers decided to use it in the meantime, the simple idea grew to a point where I couldn’t do it all on my own.
Read more ...
I’m excited to announce that I’ve joined Cloudflare as Head of Asia. This is an important time for the company as we continue to grow our presence in the region and build on the successes we’ve already had in our Singapore office. In this new role, I’m eager to grow our brand recognition in Asia and optimize our reach to clients by building up teams and channel partners.
I’m a Californian with more than 20 years of experience growing businesses across Asia. I initially came to Asia with the Boston Consulting Group and since then I’ve helped Google and Twitter start and grow their businesses in Singapore and Asia. In many cases throughout my career, I’ve been one of the very first employees (sometimes the first) on the ground in this part of the world. To me, the Asian market presents an often untapped opportunity for companies looking to expand, and it’s a challenge that has appealed to me throughout my career.
 This year's Chinese New Year celebration
This year's Chinese New Year celebration
I’m driven by opportunities to work with global businesses that drive change and are full of ambitious and passionate people. Cloudflare’s mission is to help build Continue reading

Google just announced that beginning in July 2018, with the release of Chrome 68, web pages loaded without HTTPS will be marked as “not secure”.
More than half of web visitors will soon see this warning when browsing unencrypted HTTP sites, according to data from Cloudflare’s edge that shows 56.62% of desktop requests originate from Chrome. Users presented with this warning will be less likely to interact with these sites or trust their content, so it’s imperative that site operators not yet using HTTPS have a plan to do so by July.
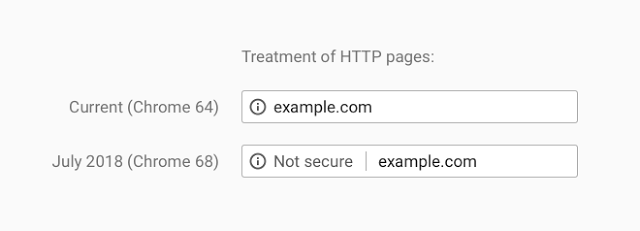
To those who have followed the Chrome team’s public statements, this announcement comes as no surprise. Google has been gearing up for this change since 2014, as Chrome boss Parisa Tabriz tweeted and Chris Palmer memorialized in a widely distributed email. While this step is an important and potentially jarring one for users, it’s by no means the last step that Google will take to influence website administrator behavior for the better.
But why are they making this change (now)? Google’s primary motivation for driving HTTPS adoption is simple: a safe browsing experience is good for business. Users that feel Continue reading
 The carrier deployed more than 300 microservices last year.
The carrier deployed more than 300 microservices last year.