Oracle Quadruples Cloud Data Center Footprint
 The company is also expanding autonomous capabilities across its entire PaaS product line.
The company is also expanding autonomous capabilities across its entire PaaS product line.
 The company is also expanding autonomous capabilities across its entire PaaS product line.
The company is also expanding autonomous capabilities across its entire PaaS product line.
 Citrix will integrate Cedexis’ programmable traffic steering technology into its portfolio.
Citrix will integrate Cedexis’ programmable traffic steering technology into its portfolio.
 China Mobile wants the ITU to standardize slicing packet network for FlexE.
China Mobile wants the ITU to standardize slicing packet network for FlexE.
The headline feature in Docker for Windows Desktop 18.02 is the option for an automated Kubernetes cluster, enabling native support of your favorite Kubernetes tools with Linux containers on your Windows desktop. That’s a big deal. You can try it out by using the whale icon in the system tray to set Docker for Windows Desktop into Linux containers mode, and then enabling Kubernetes support via the Settings menu. If you use current Windows 10 Insider builds please be aware of a Windows platform issue that affects Linux containers in Docker for Windows Desktop.
But that’s not all. This post covers additional progress on experimental support for Microsoft’s Linux containers on Windows (LCOW). Docker for Windows 18.02 now supports Linux and Windows containers running side-by-side via LCOW, using a single Docker daemon.
More on the evolution of LCOW:
Docker for Windows Desktop 18.02 is an Edge channel release. If your copy of Docker for Windows Desktop is set to the Edge or Nightly channel you will receive the update Continue reading
Dave Ward has an excellent article over at the Cisco blog on the three year journey since he started down the path of trying to work the standards landscape (called SDOs) to improve the many ways in which these organizations are broken. Specifically, he has been trying to connect the open source and open standards communities better—a path I heartily endorse, as I have been intentionally trying to work in both communities in parallel over the last several years, and find places where I can bring them together.
While the entire blog is worth reading, there are two lines I think need some further thought. The first of this is a bit of a scold, so be prepared to have your knuckles rapped.
My real bottom line here is that innovators can’t go faster than their customers and customers can’t go faster than their own understanding of the technology and integration, deployment and operational considerations.
Precisely. Maybe this is just an old man talking, but I sometimes want to scold the networking industry on this very point. We fuss about innovation, but innovation requires customers who understand the technology—and the networking world has largely become a broad set of meta-engineers, Continue reading
 Versa hires SVP of Sales; Former Dell exec joins NetApp; Aryaka snags two from Big Switch.
Versa hires SVP of Sales; Former Dell exec joins NetApp; Aryaka snags two from Big Switch.
I realised just now that I didn’t share the names of the people who used my CCDE resources and got their CCDE numbers recently. I know all of them, their capabilities, technical strength. I am happy to see that they are CCDE now. Congrats to Ken Young , Jaroslaw Dobkowski , Malcolm Booden …
Continue reading "4 people passed CCDE Lab with my CCDE training recently"
The post 4 people passed CCDE Lab with my CCDE training recently appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
I realised just now that I didn’t share the names of the people who used my CCDE resources and got their CCDE numbers recently. I know all of them, their capabilities, technical strength. I am happy to see that they are CCDE now. Congrats to Ken Young , Jaroslaw Dobkowski , Malcolm Booden …
Continue reading "4 people passed CCDE Lab with my CCDE training recently"
The post 4 people passed CCDE Lab with my CCDE training recently appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
I realised just now that I didn’t share the names of the people who used my CCDE resources and got their CCDE numbers recently. I know all of them, their capabilities, technical strength. I am happy to see that they are CCDE now. Congrats to Ken Young , Jaroslaw Dobkowski , Malcolm Booden […]
The post 4 people passed CCDE Lab with my CCDE training recently appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
On today’s podcast episode of “The Interview” with The Next Platform, we focus on some of the recent quantum computing developments out of Oak Ridge National Lab’s Quantum Computing Institute with the center’s director, Dr. Travis Humble.
Regular readers will recall previous work Humble has done on the quantum simulator, as well as other lab and Quantum Insitute efforts on creating hybrid quantum and neuromorphic supercomputers and building software frameworks to support quantum interfacing. In our discussion we check in on progress along all of these fronts, including a more detailed conversation about the XACC programming framework for …
At the Cutting Edge of Quantum Computing Research was written by Nicole Hemsoth at The Next Platform.
Make before break and break before make. I shared many posts so far which was covering the terms used in different field of networking. This one is one of them. Also I will introduce, probably to many of you, a new terminology ‘ Break before make ‘ If you are from the IP/MPLS background …
Continue reading "Make before break and Break before make"
The post Make before break and Break before make appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
Make before break and break before make. I shared many posts so far which was covering the terms used in different field of networking. This one is one of them. Also I will introduce, probably to many of you, a new terminology ‘ Break before make ‘ If you are from the IP/MPLS background …
Continue reading "Make before break and Break before make"
The post Make before break and Break before make appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
Make before break and break before make. I shared many posts so far which was covering the terms used in different field of networking. This one is one of them. Also I will introduce, probably to many of you, a new terminology ‘ Break before make ‘ If you are from the IP/MPLS background […]
The post Make before break and Break before make appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
In the past couple of years, our engineering team at HelloFresh has experienced a huge growth spurt. Within 2 years our team grew from 35 engineers to well over 150. One of the biggest challenges we faced was how to enable over 20 teams to test their code independently to other teams in a stable environment.
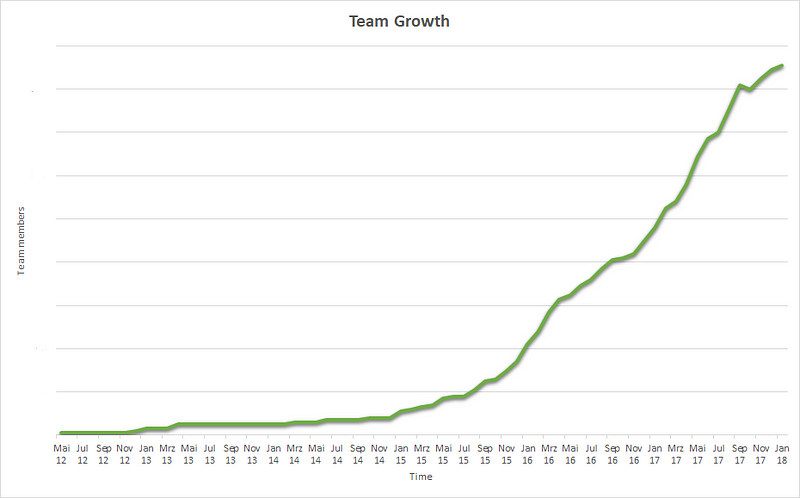
HelloTech Team Growth
I’m going to tell you about how we solved scaling our staging and local environments using phoenix environments.
When we were smaller we had only 2 environments, what we called stagingand production. This setup was great for simple applications and small teams. Once we moved to a microservice architecture with 90+ services it quickly became apparent that it was not a scalable solution.
With more teams blocking staging for their testing, the environment quickly became unusable. The solution seemed simple, create an environment for each team called team staging.
We hoped that by creating a staging environment (which is a subset of all services from the main staging) for each team, it would enable them to test whatever they wanted in isolation. Or so we thought; in reality, it was much more complicated than that.
The Continue reading
Google laid down its path forward in the machine learning and cloud computing arenas when it first unveiled plans for its tensor processing unit (TPU), an accelerator designed by the hyperscaler to speeding up machine learning workloads that are programmed using its TensorFlow framework.
Almost a year ago, at its Google I/O event, the company rolled out the architectural details of its second-generation TPUs – also called the Cloud TPU – for both neural network training and inference, with the custom ASICs providing up to 180 teraflops of floating point performance and 64 GB of High Bandwidth Memory. …
Google Boots Up Tensor Processors On Its Cloud was written by Jeffrey Burt at The Next Platform.
 The complexity of modern problems often precludes any one person from fully understanding them. Factors contributing to rising obesity levels, for example, include transportation systems and infrastructure, media, convenience foods, changing social norms, human biology and psychological factors. Designing an aircraft carrier, to take another example, requires knowledge of nuclear engineering, naval architecture, metallurgy, hydrodynamics, […]
The complexity of modern problems often precludes any one person from fully understanding them. Factors contributing to rising obesity levels, for example, include transportation systems and infrastructure, media, convenience foods, changing social norms, human biology and psychological factors. Designing an aircraft carrier, to take another example, requires knowledge of nuclear engineering, naval architecture, metallurgy, hydrodynamics, […]In a previous post my colleague, Stijn, discussed the enhancements to how NSX for vSphere 6.4 handles Remote Desktop Session Host, RDSH, systems with the Identity-based Firewall and Context-Aware Micro-segmentation.
Remote Desktop Services is an underlying technology from Microsoft that many vendors take advantage of to provide overlay management and application deployment technologies for. In this post, we’re going to discuss how NSX for vSphere 6.4 allows customers to run RDS hosts with granular security for VMware Horizon systems.
VMware Horizon can provide multiple users the ability to connect to a single system to access their applications using the RDSH technology. These users can be of the same type, for example all HR users, or of multiple types, HR and Engineering users. In previous versions of NSX, it was not possible to individually secure user sessions and create Distributed Firewall (DFW) rule sets according to the user session logged into an RDSH server. This meant less flexibility in controlling what users could access data center application servers without isolating one set of users to one RDSH server. This model created a very rigid architecture for Horizon customers to follow.
Horizon allows customers Continue reading