Change VM Hardware Version
The VM hardware version designates the virtual hardware functions supported by a virtual machine, which relates to the hardware on the host server. A VMware product will not be able to power on a VM with a hardware version higher than what it supports.
oVirt Now Supports OVS-DPDK
DPDK (Data Plane Development Kit) provides high-performance packet processing libraries and user space drivers. Open vSwitch uses DPDK libraries to perform entirely within the user space. According to Intel ONP performance tests, using OVS with DPDK can provide a huge performance enhancement, increasing network packet throughput and reducing latency.
OVS-DPDK has been added to the oVirt Master branch as an experimental feature. The following post describes the OVS-DPDK installation and configuration procedures.
Please note: Accessing the OVS-DPDK feature requires installing the oVirt Master version. In addition, OVS-DPDK cannot access any features located within the Linux kernel. This includes Linux bridge, tun/tap devices, iptables, etc.
Requirements
In order to achieve the best performance, please follow the instructions at: http://dpdk.org/doc/guides-16.11/linux_gsg/nic_perf_intel_platform.html
The network card must be on the supported vendor matrix, located here: http://dpdk.org/doc/nics
Ensure that your system supports 1GB hugepages:
grep -q pdpe1gb /proc/cpuinfo && echo "1GB supported"
- Hardware support: Make sure VT-d / AMD-Vi is enabled in BIOS
- Kernel support: When adding a new host via the oVirt GUI, go to Hosts -> Edit > Kernel, and add the following parameters to the Kernel command line:
iommu=pt intel_iommu=on default_hugepagesz=1GB hugepagesz=1G hugepages=NIn the event that 1GB Continue reading
Deutsche Telekom, Huawei Launch 5G Test Network in Europe
 The network is getting 2 Gb/s speeds and less than 3 milliseconds of latency.
The network is getting 2 Gb/s speeds and less than 3 milliseconds of latency.
OCP Hardware Could Lay Foundation for Open Edge Computing
 SDxCentral just published new research on MEC.
SDxCentral just published new research on MEC.
The 2017 SDxCentral SD-WAN and vCPE Survey is Here!
 Take survey and enter to win one of two $300 Gift Cards redeemable at various retailers including Amazon, Target, Visa Virtual Card, etc.
Take survey and enter to win one of two $300 Gift Cards redeemable at various retailers including Amazon, Target, Visa Virtual Card, etc.
SIDH in Go for quantum-resistant TLS 1.3
The Quantum Threat
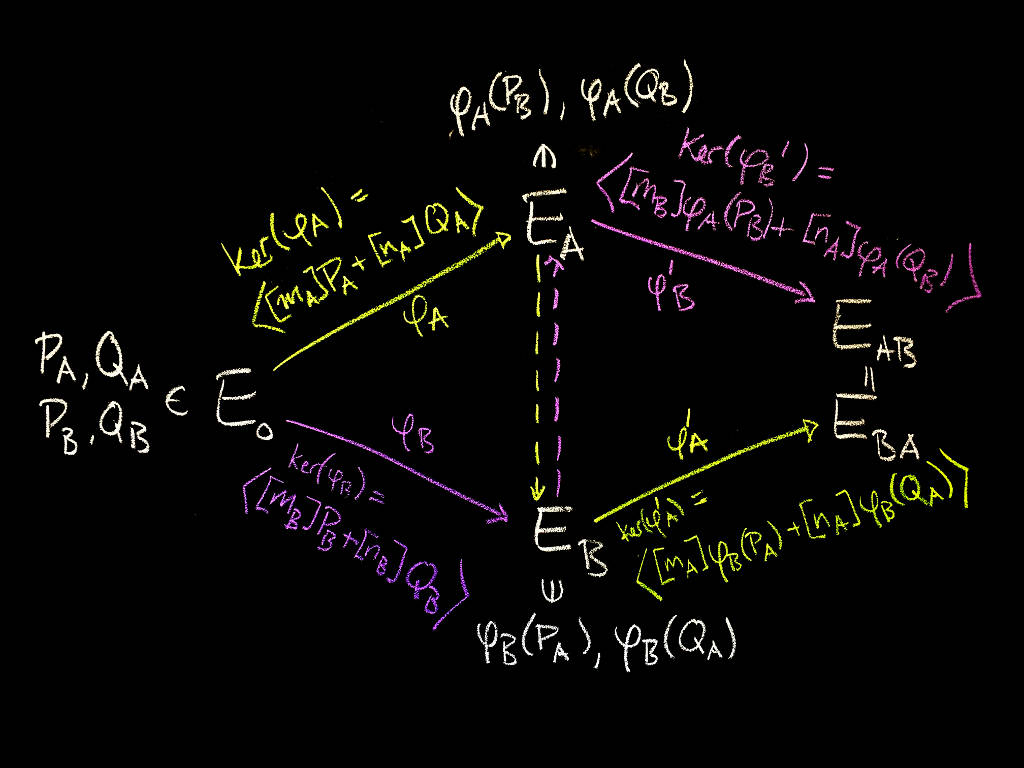
Most of today's cryptography is designed to be secure against an adversary with enormous amounts of computational power. This means estimating how much work certain computations (such as factoring a number, or finding a discrete logarithm) require, and choosing cryptographic parameters based on our best estimate of how much work would be required to break the system.
If it were possible to build a large-scale quantum computer, many of the problems whose difficulty we rely on for security would no longer be difficult to solve. While it remains unknown whether large-scale quantum computers are possible (see this article for a good overview), it's a sufficient risk that there's wide interest in developing quantum-resistant (or post-quantum) cryptography: cryptography that works on ordinary computers we have today, but which is secure against a possible quantum computer.
At Cloudflare, our biggest use of cryptography is TLS, which we use both for serving our customers' websites (all Cloudflare sites get free HTTPS), as well as for internal inter-datacenter communication on our backend.
In the TLS context, we want to create a secure connection between a client and a server. There are basically three cryptographic problems here:
Authenticity: the server Continue reading
New Study: Understanding MANRS’ Potential for Enterprises and Service Providers
Mutually Agreed Norms for Routing Security, or MANRS, was founded with the ambitious goal of improving the security and reliability of the global Internet routing system, based on collaboration among participants and shared responsibility for Internet infrastructure. These are undoubtedly essential pillars supporting the Internet’s tremendous growth and success, but we must better articulate the incentives of contributing to global security and resilience to grow MANRS participation and reach our goals.
To do so, we engaged 451 Research to understand the attitudes and perceptions of Internet service providers and the broader enterprise community around MANRS and how it relates to their organizations. The results of the study are documented in the report: https://www.routingmanifesto.org/resources/research/.
The study results demonstrate considerable unrealized potential for MANRS, showing that enterprises are interested in security and their interest should be a strong incentive for more service providers to participate. Market education could be particularly effective in overcoming the operational inertia that many providers face.
The key points from the study are:
- While MANRS itself is not well known by enterprises, its attributes are highly valued.
- Enterprises have high expectations for MANRS efforts.
- Enterprise perceptions of MANRS can translate into increased revenue for service Continue reading
Time Synchronization, Security, and Trust
Time is something that is often overlooked or taken for granted, but the accuracy and reliability of time is critical to our lives and must be protected. Time is a core concept underlying nearly all physical and virtual systems. Distributed computer systems, key to many functions inherent in our daily lives, rely on accurate and reliable time, yet we rarely stop and think about how that time is constructed and represented. Accurate and reliable time is needed to determine when an event occurs, in what order a particular sequence of events occurs, or when to schedule an event that is to occur at a particular time in the future. Finally, and of particular interest to our trust agenda here at the Internet Society, quality reliable time is required for many of the security technologies that help provide trust for the Internet. It is a vital and often overlooked part of the Internet infrastructure.
Some specific examples where accurate reliable secure time information is vital include:
- The finance sector where there are high demands on the time synchronization of business clocks in trading systems. This is especially true in the high frequency trading where a new EU legislation called Markets Continue reading
Worth Reading: Wave System’s DPU architecture
The post Worth Reading: Wave System’s DPU architecture appeared first on rule 11 reader.
Dictionary: Blame THeater
What is Blame Theater ?
The post Dictionary: Blame THeater appeared first on EtherealMind.
HPE Closes $8.8B Software Spinoff Deal with Micro Focus
 Micro Focus is now the seventh largest pure-play enterprise software company in the world.
Micro Focus is now the seventh largest pure-play enterprise software company in the world.
Microsoft Amps Container Support with Jenkins Plugin
 The company was unable to find required support from Jenkins to Kubernetes.
The company was unable to find required support from Jenkins to Kubernetes.
Portland (Oregon): Cloudflare’s 117th Data Center!

Even as the luckiest amongst us across the US West Coast dashed off to Oregon to be closer to the solar eclipse path of totality, Cloudflare engineers were busy turning up our newest data center in Portland.
This deployment serves as our 27th data center in North America alone, and our 117th globally. It also provides additional redundancy to our Seattle and San Jose data centers, while increasing our capacity to run services and fight growing attacks.
Special History
The Silicon Forest corridor around Portland holds a special place in the hearts of the Cloudflare team. It is both new (by way of our latest edge deployment bringing us closer to millions of Oregon Internet users), and familiar (since we have had an internal data center in this region for many years, enabling services such as analytics and enterprise logs).
The greater Portland area has played a pivotal area in building high-technology products from companies such as Tektronix (test and measurement equipment), Mentor Graphics (electronic design automation) and Intel (with nearly 20,000 employees across Oregon).
Expanding the edge
At our Portland data center, we locally interconnect with ISPs such as Comcast (into their regional area networks such as Beaverton and Continue reading
Show 355: What’s Wrong With BGP? – IETF 99
BGP is one of the fundamental protocols for routing in the Internet, but it also has its limitations. Today's Weekly Show drills into the uses of BGP and problems associated with it. Our guests are Sue Hares and Russ White. The post Show 355: What’s Wrong With BGP? – IETF 99 appeared first on Packet Pushers.New Study: Understanding MANRS’ Potential for Enterprises and Service Providers
[Note: This post was originally published on the MANRS Blog at https://www.routingmanifesto.org/2017/09/new-study-understanding-manrs-potential-for-enterprises-and-service-providers/.]
Palo Alto Customer Wins Soar in Q4 2017
 This is the most customer wins the company has ever had during a quarter.
This is the most customer wins the company has ever had during a quarter.
SDxCentral Weekly News Roundup — September 1, 2017
 Oracle hires 5,000 for its cloud business; Kolos builds the world's largest data center.
Oracle hires 5,000 for its cloud business; Kolos builds the world's largest data center.
Five Steps You Can Take Right Now to Increase Your Privacy
You should care about your privacy online even if you think you have nothing to hide. A key aspect of privacy is being able to choose what information you share publicly and what is private. Would you want your bank account balance displayed for anyone to see? What about your medical history?
Encryption is a vital tool for protecting private communications online from unwanted eyes. We use it every day, often without even realizing it. But, encryption is not magic. If you want to better protect your privacy online, here are five steps you can take right now:
- Use End to End Encryption for all Messages: End to End (E2E) encryption is a way to secure the messages you send via email or a messaging app so that they can only by read by those you intended to read it including your friends, bank, doctor, etc. Read the fine print – not all encrypted services are E2E. Use messaging apps that have E2E encryption (e.g. Signal, Wire). Encourage your friends and family to switch to an app that has E2E. Remember that sending an unencrypted message is like sending a postcard. Anyone can read it and you Continue reading
