Performance Monitoring Companies Attracting Private Equity Investment
 Global private equity M&A activity in the tech sector is on the rise.
Global private equity M&A activity in the tech sector is on the rise.
 Global private equity M&A activity in the tech sector is on the rise.
Global private equity M&A activity in the tech sector is on the rise.
 Docker security tracks all container runtime activity.
Docker security tracks all container runtime activity.
 The company’s edge analytics platform is attractive to IoT firms.
The company’s edge analytics platform is attractive to IoT firms.
 Google nearly tripled its big cloud deals in one year.
Google nearly tripled its big cloud deals in one year.
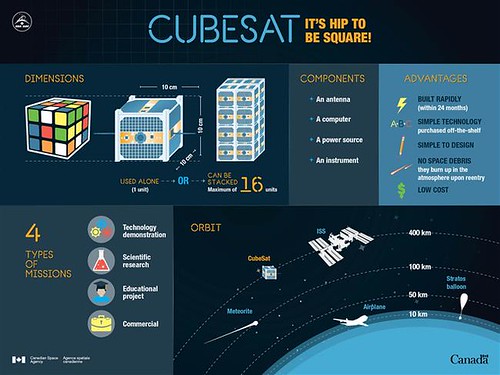
CubeSats are revolutionizing space exploration because they are small, modular, and inexpensive to build and launch. On an episode of embedded.fm, Professor Jordi Puig-Suari gives a fascinating interview on the invention of the CubeSat. 195: A BUNCH OF SPUTNIKS.
What struck in the interview is how the process of how the CubeSat was invented parallels how the cloud developed. They followed a very similar path driven by many of the same forces and ideas.
Just what is a CubeSat? It's a "type of miniaturized satellite for space research that is made up of multiples of 10×10×10 cm cubic units. CubeSats have a mass of no more than 1.33 kilograms per unit, and often use commercial off-the-shelf (COTS) components for their electronics and structure."
The post Worth Reading: Pursue Meaning appeared first on rule 11 reader.
Building on the successes of the Stampede1 supercomputer, the Texas Advanced Computing Center (TACC) has rolled out its next-generation HPC system, Stampede2. Over the course of 2017, Stampede2 will undergo further optimization phases with the support of a $30 million grant from the National Science Foundation (NSF). With the latest Xeon and Skylake processors, and enhanced networking provided by the Omni-Path architecture, the new flagship system is expected to deliver approximately 18 petaflops, nearly doubling Stampede1’s performance.
Stampede2 continues Stampede1’s mission: enabling thousands of scientists and researchers across the United States to deliver breakthrough scientific discoveries in science, engineering, artificial …
Texas Advanced Supercomputing Center Taps Latest HPC Tech was written by Nicole Hemsoth at The Next Platform.
 Using an MSSP means that organizations don’t have to hire security manpower
Using an MSSP means that organizations don’t have to hire security manpower
Chris Wahl relates his ongoing Full Stack Journey, including stops along the way for PowerShell and Git, as well as the newest directions where his technology compass leads him.
The post Full Stack Journey 013: Chris Wahl appeared first on Packet Pushers.
 QRNG generates random numbers without any pattern.
QRNG generates random numbers without any pattern.
 Intel helped fund the security product development.
Intel helped fund the security product development.
SDS can help keep IT costs low while supporting new data-intensive initiatives.
One of the more interesting presentations we had during Tech Field Day Extra @ Cisco Live Berlin was coming from Paessler, a company developing PRTG, a little-known network monitoring software.
More about PRTG in TFD videos and here, here, here and here.
Read more ...