Static Routing configuration different ways
- The next-hop address
- The exit interface
172.16.10.2 = next-hop address
Way-2 :The exit interface
Router(config)#ip route 172.16.20.0 255.255.255.0 s0/0
The post Worth Reading: What if we designed differently? appeared first on rule 11 reader.
 NaaS offers a balance between SLA MPLS services and high bandwidth broadband Internet.
NaaS offers a balance between SLA MPLS services and high bandwidth broadband Internet.
 The partnership will be back on track in 3 to 6 months.
The partnership will be back on track in 3 to 6 months.
The second Applied Networking Research Workshop will take place on Saturday, 15 July, immediately prior to the IETF 99 meeting in Prague, Czech Republic.

When we started Cloudflare we had no idea if anyone would validate our core idea. Our idea was what that everyone should have the ability to be as fast and secure as the Internet giants like Google, Facebook, and Microsoft. Six years later, it's incredible how far that core idea has taken us.
 CC BY-SA 2.0 image by Mobilus In Mobili
CC BY-SA 2.0 image by Mobilus In Mobili
Today, Cloudflare runs one of the largest global networks. We have data centers in 115 cities around the world and continue to expand. We've built a core service that delivers performance, security, availability, and insight to more than 6 million users.
From the beginning, our goal has been to democratize the Internet. Today we're taking another step toward that goal with the launch of the Cloudflare Apps Platform and the Cloudflare Developer Fund. To understand that, you have to understand where we started.
When we started Cloudflare we needed two things: a collection of users for the service, and finances to help us fund our development. In both cases, people were taking a risk on Cloudflare. Our first users came from Project Honey Pot, which Lee Holloway and I created back in 2004. Members Continue reading
Learn about the different types of cables and where they work best in the enterprise.
 |
| Fig 1.1- Sample OSPF Topology |
Here’s the question I got from one of my readers:
Do you have any data available to show the benefits of jumbo frames in 40GE/100GE networks?
In case you’re wondering why he went down this path, here’s the underlying problem:
Read more ...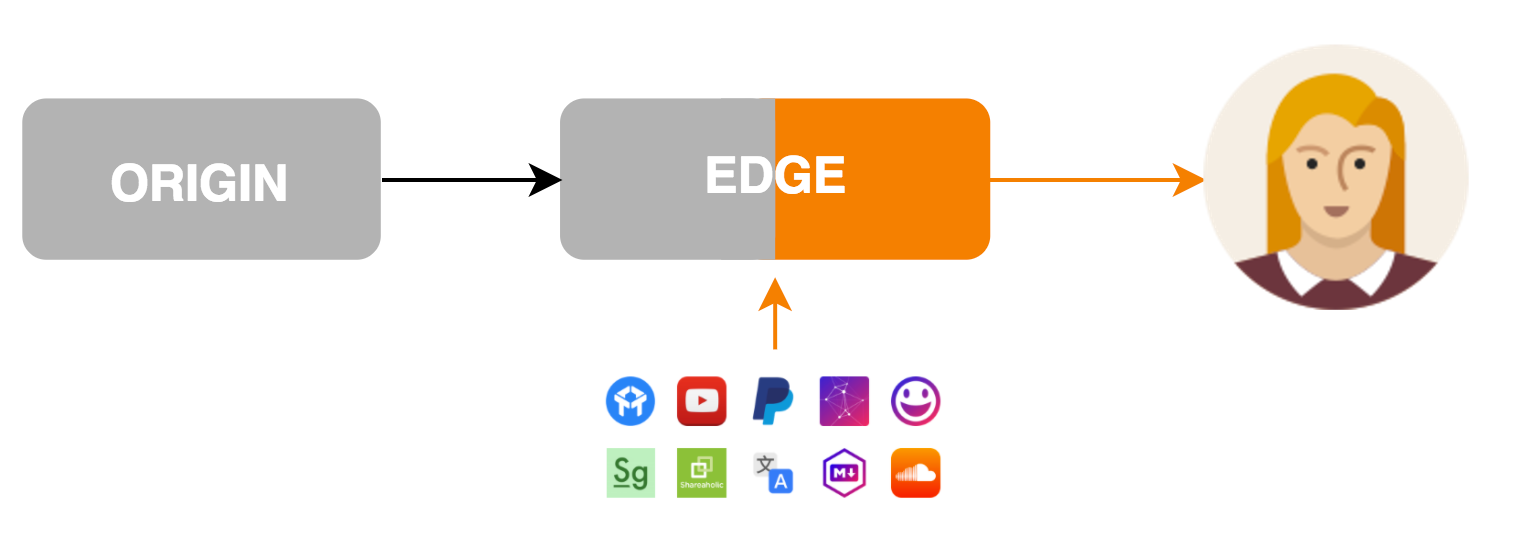
Today we’re excited to announce the next generation of Cloudflare Apps. Cloudflare Apps is an open platform of tools to build a high quality website. It’s a place where every website owner can select from a vast catalog of Apps which can improve their websites and internet properties in every way imaginable. Selected apps can be previewed and installed instantly with just a few clicks, giving every website owner the power of technical expertise, and every developer the platform only Cloudflare can provide.
Apps can modify content and layout on the page they’re installed on, communicate with external services and dramatically improve websites. Imagine Google Analytics, YouTube videos, in-page chat tools, widgets, themes and every other business which can be built by improving websites. All of these and more can be done with Cloudflare Apps.
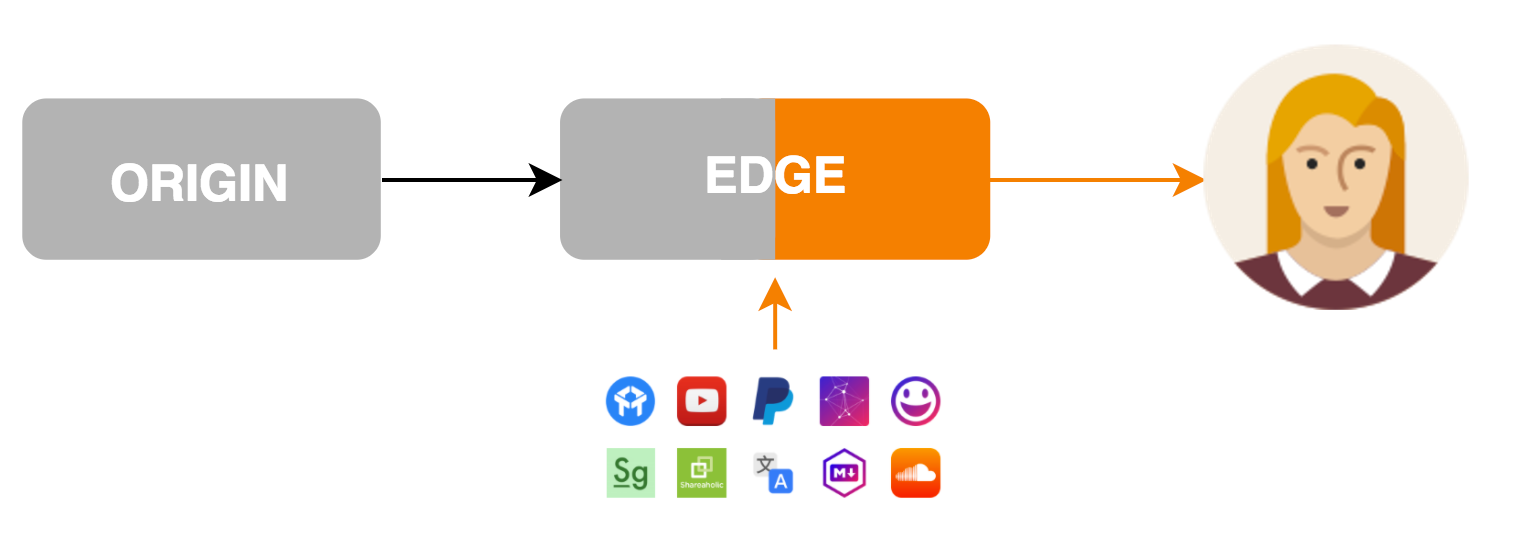
Cloudflare Apps makes it possible for a developer in her basement to build the next great new tool and get it on a million websites overnight. With Cloudflare Apps, even the smallest teams can get massive distribution for their apps on the web so that the best products win. With your help we will make it possible for developers like you to build a new Continue reading
 SevOne will soon be able to monitor VMware and Nuage SDN environments too.
SevOne will soon be able to monitor VMware and Nuage SDN environments too.