Keeping Up with Storage Demands by Pairing vNAS and vSAN
 This combined approach will give enterprises the flexibility and scalability they need.
This combined approach will give enterprises the flexibility and scalability they need.
 This combined approach will give enterprises the flexibility and scalability they need.
This combined approach will give enterprises the flexibility and scalability they need.

Have you noticed something new in your Cloudflare analytics dashboard this morning? You can now see detailed DNS analytics for your domains on Cloudflare.
If you want to skip to the punch and start exploring, go check it out here. Otherwise, hop on the DNS magic school bus - and let us show you all the neat stats in your now-available DNS analytics.
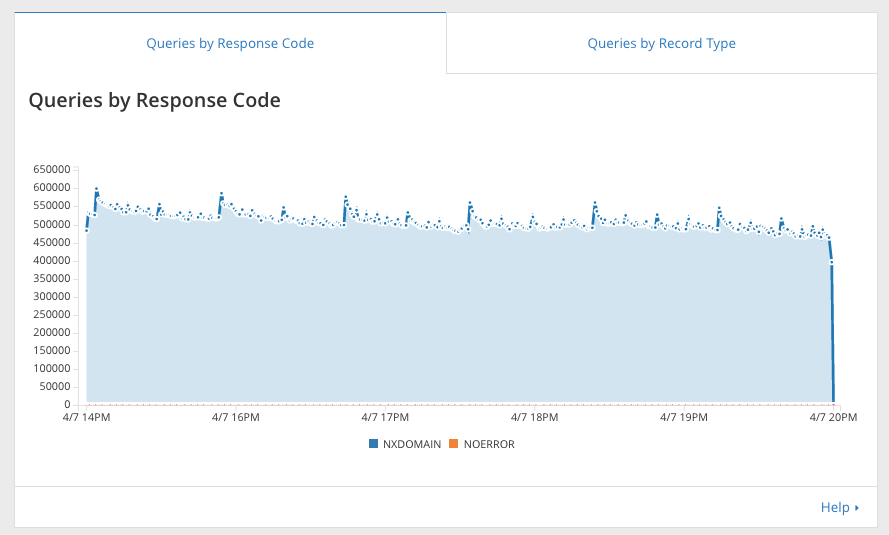
At the top of the DNS analytics dashboard you can see your DNS traffic health. This “Queries by Response Codes” graph breaks down queries by what response code Cloudflare DNS answered to the visitor. Like HTTP response codes, DNS response codes give an indication of what is happening behind the scenes. Mostly you will just see NOERROR, the HTTP 200 of DNS response codes, and NXDOMAIN, the HTTP 404 of DNS response codes. NXDOMAIN is particularly interesting - what are people querying for that doesn’t exist?
If you are an enterprise customer and you want to know what all the NXDOMAIN queries are, just scroll down a little bit where we show you the top queries for your domain and top queries for Continue reading
If any new hardware technology is going to get traction in the datacenter, it has to have the software behind it. And as the dominant supplier of commercial Linux, Red Hat’s support of ARM-based servers gives the upstart chip makers like Applied Micro, Cavium, and Qualcomm the leverage to help pry the glasshouse doors open and get a slice of the server and storage business that is so utterly dominated by Intel’s Xeon processors today.
It is now or never for ARM in the datacenter, and that means Red Hat has to go all the way and not just support …
Red Hat Is The Gatekeeper For ARM In The Datacenter was written by Jeffrey Burt at The Next Platform.
The post BGP over GRE Tunnel appeared first on Noction.
An engineer watching my IPv6 Transition Mechanisms webinar sent me this question:
We would appreciate any insight you might have as to which transitional mechanisms the ISPs are actually deploying.
All of them ;)
Read more ...We collect the top expert content in the infrastructure industry and fire it along the priority queue.