Nutanix Enterprise Cloud Platform Shrinks Data Center Footprint
 It beat out HPE’s SimpliVity and Cisco's Hyperflex for the customer win.
It beat out HPE’s SimpliVity and Cisco's Hyperflex for the customer win.
Aparna Systems ‘Cloud-in-a-Box’ Targets Edge Computing
 It goes beyond hyperconverged by integrating the network switching.
It goes beyond hyperconverged by integrating the network switching.
The AdStage Migration from Heroku to AWS

This is a guest repost by G Gordon Worley III, Head of Site Reliability Engineering at AdStage.
When I joined AdStage in the Fall of 2013 we were already running on Heroku. It was the obvious choice: super easy to get started with, less expensive than full-sized virtual servers, and flexible enough to grow with our business. And grow we did. Heroku let us focus exclusively on building a compelling product without the distraction of managing infrastructure, so by late 2015 we were running thousands of dynos (containers) simultaneously to keep up with our customers.
We needed all those dynos because, on the backend, we look a lot like Segment, and like them many of our costs scale linearly with the number of users. At $25/dyno/month, our growth projections put us breaking $1 million in annual infrastructure expenses by mid-2016 when factored in with other technical costs, and that made up such a large proportion of COGS that it would take years to reach profitability. The situation was, to be frank, unsustainable. The engineering team met to discuss our options, and some quick calculations showed us we were paying more than $10,000 a month for the convenience of Continue reading
Introducing TLS with Client Authentication
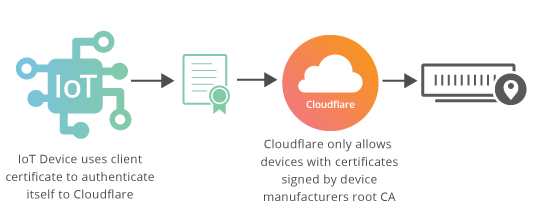
In a traditional TLS handshake, the client authenticates the server, and the server doesn’t know too much about the client. However, starting now, Cloudflare is offering enterprise customers TLS with client authentication, meaning that the server additionally authenticates that the client connecting to it is authorized to connect.
TLS Client Authentication is useful in cases where a server is keeping track of hundreds of thousands or millions of clients, as in IoT, or in a mobile app with millions of installs exchanging secure information. For example, an IoT company can issue a unique client certificate per device, and then limit connections to their IoT infrastructure to only their devices by blocking connections where the client doesn’t present a certificate signed by the company’s certificate authority.
Or in the case of a mobile banking app, where the bank wants to ensure customers’ secure financial data doesn’t get stolen by bots spoofing their mobile app, they can issue a unique certificate to every app install and in the TLS handshake validate requests are coming from their mobile app. Client authentication is also useful for VPNs, enterprise networks or staging sites, where corporations and developers need to lock down connections to only laptops Continue reading
Greenbug’s DNS-isms
Over the past few months there has been a lot of research and press coverage on the Shamoon campaigns. These have been the attacks on Saudi Arabian companies where a destructive malware known as Disttrack was deployed. The malware, using stolen credentials, spreads throughout the […]DockerCon 2017 Online meetup Recap
Weren’t able to attend DockerCon 2017 or looking for a refresher? Check out the recording and slides from the DockerCon 2017 Online Meetup highlights recap of all the announcements and highlights from DockerCon by Patrick Chanezon and Betty Junod.
Watch the General Session Talks
The videos and slides from general session day 1 and day 2 as well as the top rated sessions are already available. The rest of the DockerCon slides and videos will soon be published on our slideshare account and all the breakout session video recordings available on our DockerCon 2017 youtube playlist.
Learn more about the Moby Project
The Moby Project is a new open-source project to advance the software containerization movement and help the ecosystem take containers mainstream. Learn more here.
Learn More about LinuxKit
LinuxKit is toolkit for building secure, portable and lean operating systems for containers. Read more about LinuxKit.
Learn More about the Modernize Traditional Applications Program:
The Modernize Traditional Applications (MTA) Program aims to help enterprises make their existing legacy apps more secure, more efficient and portable to hybrid cloud infrastructure. Read more about the Modernize Traditional Apps Program.

Weren’t able to attend #dockercon? Watch this recap video for key highlights !
Click Continue reading
Worth Reading: How to choose a sandbox
The post Worth Reading: How to choose a sandbox appeared first on rule 11 reader.
Nokia 5G Report Webinar Q&A: Converging Transport Networks for 5G Success – The ‘Anyhaul’ Imperative
 Thanks to all who joined us for the Nokia 5G Report Webinar, Converging Transport Networks for 5G Success – The ‘Anyhaul’ Imperative. Read the full Q&A here.
Thanks to all who joined us for the Nokia 5G Report Webinar, Converging Transport Networks for 5G Success – The ‘Anyhaul’ Imperative. Read the full Q&A here.

