ポスト量子暗号が一般利用可能に
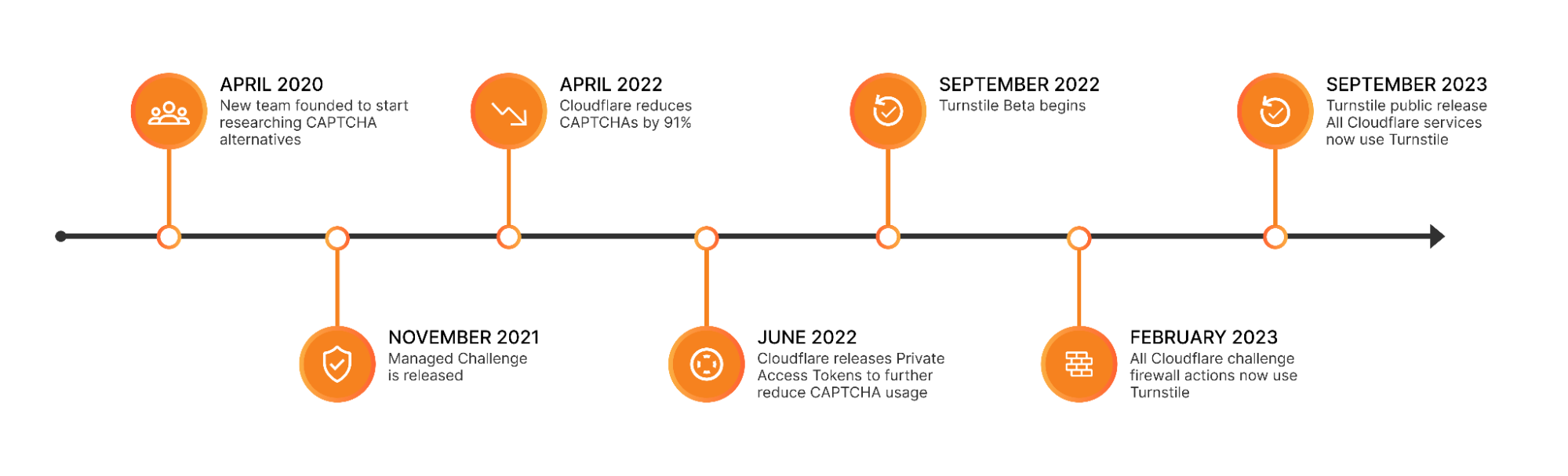
過去12か月間、当社はインターネット上の暗号化の新しいベースラインであるポスト量子暗号について議論してきました。昨年のバースデーウィークの間、Kyberのベータ版がテスト用に利用可能であること、そしてCloudflare Tunnelがポスト量子暗号を使用して、有効にできることを発表しました。今年初め、当社は、この基礎的なテクノロジーを誰もが永久に無料で利用できるべきだというスタンスを明確にしました。
今日、当社は6年を経てマイルストーンを達成し、31件のブログ記事を作成中です。以下に、より詳細に説明されているように、お客様、サービス、および内部システムへのポスト量子暗号サポートの一般提供のロールアウトを開始しています。これには、オリジン接続用のPingora、1.1.1.1、R2、Argo Smart Routing、Snippetsなどの製品が含まれます。
これはインターネットのマイルストーンです。量子コンピュータが今日の暗号を破るのに十分な規模を持つかは、まだ分かりませんが、今すぐポスト量子暗号にアップグレードするメリットは明らかです。Cloudflare、Google、Mozilla、米国国立標準技術研究所、インターネットエンジニアリングタスクフォース、および多数の学術機関による進歩により、高速接続と、将来も保証されるセキュリティはすべて今日可能になっています
一般提供とはどういう意味ですか?2022年10月当社はX25519+KyberをCloudflareを介して提供されるすべてのWebサイトとAPIに対し、ベータ版として有効にしました。しかし、タンゴを踊るには二人必要です。ブラウザがポスト量子暗号もサポートしている場合にのみ、接続が保護されます。2023年8月から、ChromeはデフォルトでX25519+Kyberを徐々に有効にします。
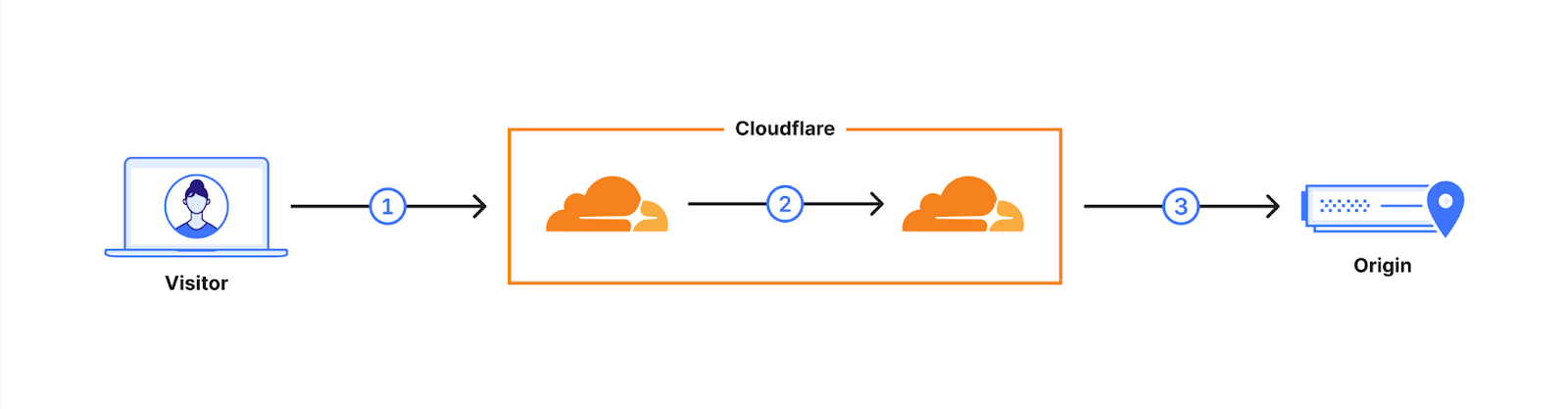
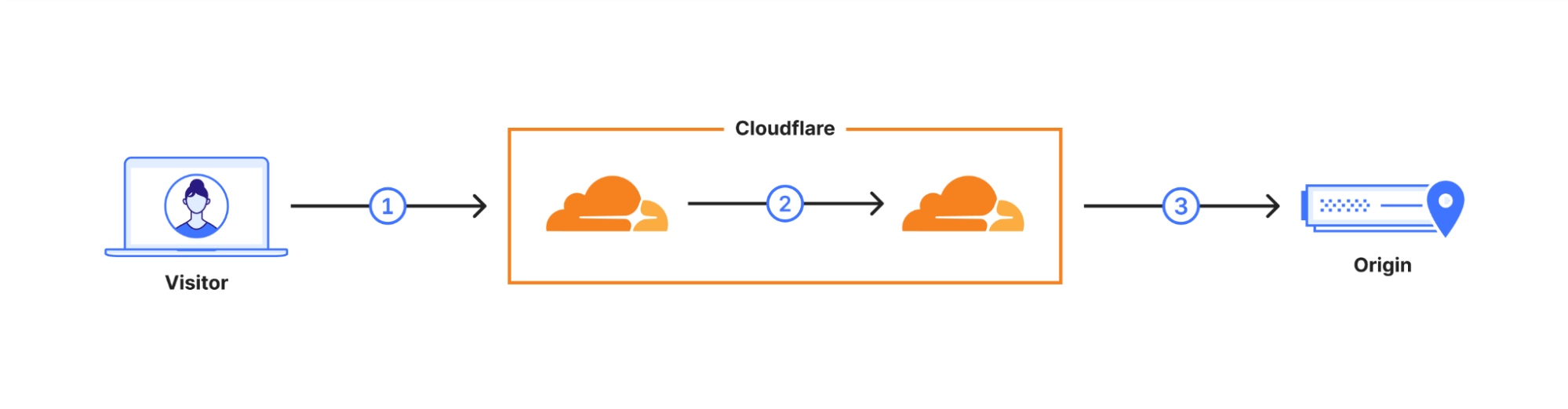
ユーザーのリクエストは、Cloudflareのネットワークを介してルーティングされます(2)。当社はこれらの内部接続の多くをポスト量子暗号を使用するようにアップグレードしており、2024年末までにすべての内部接続のアップグレードが完了する予定です。これにより、最終リンクとして、当社と配信元サーバー間の接続(3)が残ります。
配信元サーバーやCloudflare Workersのフェッチを含む利用に対し、ほとんどのインバウンドおよびアウトバウンド接続向けX25519+Kyberのサポートを使用の一般提供としてロールアウトしていることをお知らせできて嬉しく思います。
| プラン | ポスト量子アウトバウンド接続のサポート |
|---|---|
| Free | ロールアウトを開始。 10月末までに100%を目指す。 |
| ProプランおよびBusinessプラン | 年末までに100%を目指す。 |
| Enterprise | ロールアウト開始は2024年2月。 2024年3月までに100%。 |
Enterpriseのお客様には、今後6ヶ月にわたり、ロールアウトの準備に役立つ追加情報を定期的にお送りする予定です。Pro、Business、Enterpriseをご利用のお客様は、ロールアウトをスキップして、現在ご利用のゾーン内でオプトインすることも、コンパニオンブログ記事で説明されているAPIを使用して事前にオプトアウトすることもできます。2024年2月にEnterprise向けにロールアウトする前に、ダッシュボードにオプトアウト用のトグルを追加する予定です。
今すぐ始めたいという方は、技術的な詳細を記載したブログをチェックし、APIを介したポスト量子暗号サポートを有効にしてください!
何が含まれ、次に何があるのでしょうか?
この規模のアップグレードでは、まず最もよく使用される製品に焦点を当て、次に外側に拡張しエッジケースを把握したいと考えました。 このプロセスにより、このロールアウトには以下の製品とシステムを含めることになりました。
| 1.1.1.1 |
| AMP |
| API Gateway |
| Argo Smart Routing |
| Auto Minify |
| プラットフォームの自動最適化 |
| Automatic Signed Exchanges |
| Cloudflareエグレス |
| Cloudflare Images |
| Cloudflareルールセット |
| Cloudflare Snippets |
| Cloudflare Tunnel |
| カスタムエラーページ |
| フローベースのモニタリング |
| ヘルスチェック |
| ヘルメス |
| ホストヘッドチェッカー |
| Magic Firewall |
| Magic Network Monitoring |
| ネットワークエラーログ |
| プロジェクトフレーム |
| クイックシルバー |
| R2ストレージ |
| リクエストトレーサー |
| Rocket Loader |
| Cloudflare Dashの速度 |
| SSL/TLS |
| Traffic Manager(トラフィックマネージャー) |
| WAF、管理ルール |
| Waiting Room |
| Web Analytics |
ご利用の製品またはサービスがここに記載されていない場合は、まだポスト量子暗号の展開を開始していません。当社は、Zero Trust製品を含むすべての製品とサービスにポスト量子暗号を展開することに積極的に取り組んでいます。 すべてのシステムでポスト量子暗号のサポートが完了するまで、どの製品にポスト量子暗号をロールアウトしたか、次にロールアウトする製品、まだ、近々予定の製品を網羅する更新ブログをイノベーションウィークごとに公開する予定です。
ポスト量子暗号サポートを導入しようと取り組んでいる製品はまもなくです。
| Cloudflare Gateway |
| Cloudflare DNS |
| Cloudflareロードバランサー |
| Cloudflare Access |
| Always Online |
| Zaraz |
| ログ |
| D1 |
| Cloudflare Workers |
| Cloudflare WARP |
| ボット管理 |
なぜ、今なのでしょうか?
今年初めにお知らせしたように、ポスト量子暗号は、それをサポートできるすべてのCloudflare製品とサービスの中に無料で含まれます。最高の暗号化技術は誰もがアクセスできる必要があり、プライバシーと人権を世界的にサポートするのに役立ちます。
3月に述べたように:
「かつては実験的なフロンティアだったものが、現代社会の根底にある構造へと変わりました。これは、電力システム、病院、空港、銀行などの最も重要なインフラストラクチャで実行されます。私たちは最も貴重なメモリをそれに託しています。私たちは機密をそれに託しています。インターネットが、デフォルトでプライベートである必要があるのはそのためです。デフォルトで安全である必要があります。」
ポスト量子暗号に関する私たちの研究は、従来の暗号を破ることができる量子コンピューターが西暦2000年のバグと同様の問題を引き起こすという論文によって推進されています。将来的には、ユーザー、企業、さらには国家に壊滅的な結果をもたらす可能性のある問題が発生することは、わかっています。今回の違いは、計算パラダイムのこの破壊がいつどのように発生するかがわからないことです。 さらに悪いことに、今日捕捉されたトラフィックは将来解読される可能性があります。この脅威に備えるために、今日から準備をする必要があります。
当社は、ポスト量子暗号を皆さんのシステムに導入することを楽しみにしています。ポスト量子暗号の導入とサードパーティのクライアント/サーバーサポートの最新情報をフォローするには、pq.cloudflareresearch.comをチェックして、このブログに注目してください。
1当社は、ポスト量子鍵合意に関して、NISの選択であるKyberの暫定版を使用しています。Kyberはまだ完成していません。最終基準は、2024年にML-KEMという名前で公開される予定であり、X25519Kyber768Draft00のサポートを廃止しつつ、速やかに採用する予定です。