DCNM ISSU: Disaster or Triumph? Let’s Find Out.
If you’ve recovered from the shock of hearing me say something positive about Cisco’s Data Center Network Manager (DCNM) product, then you’ll want to hold on tightly to your underbritches as I tell you that I just used DCNM ISSU to perform disruptive software upgrades on eight of the switches in my ethernet fabric, and–spoiler alert–it was actually a fairly pleasant experience!

DCNM ISSU
DCNM offers management of ISSU (In-Service Software Upgrade). ISSU usually implies some kind of hitless (to the revenue ports) upgrade, historically made possible on the Nexus 7000, for example, by having dual supervisor modules and using Non-Stop Forwarding (NSF) to keep the forwarding plane intact while the supervisors failover. With the single-CPU layer-2 Nexus 5600 switches, however, the data plane can be told to continue forwarding frames while the control plane reboots with new code, allowing for an upgrade to take place without interruption.
Disruptive Upgrades
Unfortunately it’s not always possible to perform a non-disruptive upgrade. The code version I was installing included a fix to the linecard BIOS, so the linecards had to be reloaded as well as the main CPU. In other words, the switch has to be rebooted after the upgrade, and there’s Continue reading
A New Twist On Adding Data Persistence To Containers
Containers continue to gain momentum as organizations look for greater efficiencies and lower costs to run distributed applications in their increasingly virtualized datacenters as well as for improving their application development environments. As we have noted before, containers are becoming more common in the enterprise, though they still have a way to go before being fully embraced in high performance computing circles.
There are myriad advantages to containers, from being able to spin them up much faster than virtual machine instances on hypervisors and to pack more containers than virtual machines on a host system to gaining efficiencies …
A New Twist On Adding Data Persistence To Containers was written by Timothy Prickett Morgan at The Next Platform.
Intel Atom SoC bricking more than Cisco products
 Looks like the culprit in the recent Cisco debacle is the Intel Atom “System on Chip” (SoC) that Cisco used in it’s gear. My sources within Cisco won’t give up the goods, but many seem to be pointing to Cisco, although a single source at Cisco seemed to indicate there was another player included in this issue but wouldn’t comment. The real footing of these Intel accusations come from Intel itself. Back in Janurary 2017, they updated their spec document documenting an issue with the LPC clock on the Atom s2000, with no workaround and a system that is unable to boot, this depicts a grim outlook for our networking devices.
Looks like the culprit in the recent Cisco debacle is the Intel Atom “System on Chip” (SoC) that Cisco used in it’s gear. My sources within Cisco won’t give up the goods, but many seem to be pointing to Cisco, although a single source at Cisco seemed to indicate there was another player included in this issue but wouldn’t comment. The real footing of these Intel accusations come from Intel itself. Back in Janurary 2017, they updated their spec document documenting an issue with the LPC clock on the Atom s2000, with no workaround and a system that is unable to boot, this depicts a grim outlook for our networking devices.
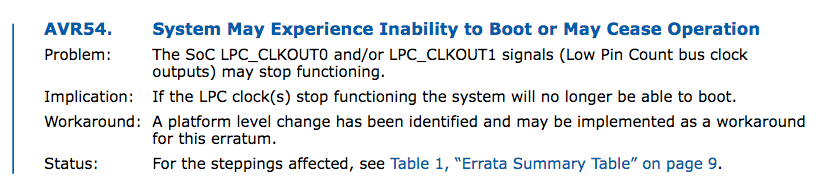
The news gets worse though, according to a recent article from The Register Cisco isn’t the only one experiencing issues.
People with Synology DS1815+ storage boxes have been reporting complete hardware failures; the DS1815+ is powered by an Intel Atom C2538. […]
Other vendors using Atom C2000 chips include Aaeon, HP, Infortrend, Lanner, NEC, Newisys, Netgate, Netgear, Quanta, Supermicro, and ZNYX Networks. The chipset is aimed at networking devices, storage systems, and microserver workloads.
For now, only time will tell what other devices are going to come out Continue reading
Cisco Study Says 5G Subscribers Will Top 25M by 2021
 5G will also generate 30 GB of data per month.
5G will also generate 30 GB of data per month.
BGP Basics: Internal And External BGP
Learn about Border Gateway Protocol fundamentals in this Cisco Press chapter excerpt.
IT Outages: The Costly Fallout
Survey provides insight into the impact of IT incidents and how companies respond.
And This Is Why Relying on Linux Makes Sense
Most networking operating systems include a mechanism to roll back device configuration and/or create configuration snapshots. These mechanisms usually work only for the device configuration, but do not include operating system images or other components (example: crypto keys).
Now imagine using RFC 1925 rule 6a and changing the “configuration rollback” problem into “file system snapshot” problem. That’s exactly what Cumulus Linux does in its newest release. Does it make sense? It depends.
Read more ...How to set up the EVE-NG network emulator on a Linux system
EVE-NG is a graphical network emulator that supports both commercial and open-source router images. It’s graphical user interface runs in a web browser. EVE-NG runs in a virtual machine so it can be set up Windows, Mac OS, or Linux computers.

In this post, I will show how to set up an EVE-NG virtual machine on an Ubuntu Linux system. I’ll show the basic steps to creating and running a simple lab consisting of emulated Linux nodes.
To support more complex labs using open-source routers and other open-source network appliances in EVE-NG, we need to create custom templates and build router images specifically for use in EVE-NG. I will cover these topics in a future post. In this post, we’ll focus only on getting an EVE-NG virtual machine set up and running on a Linux system.
EVE-NG Overview
EVE-NG is a clientless network emulator that provides a user interface via a browser. Users may create network nodes from a library of templates, connect them together, and configure them. Advanced users or administrators may add software images to the library and build custom templates to support almost any network scenario.
EVE-NG supports pre-configured multiple hypervisors on one virtual machine. It runs Continue reading
Installing VirtualBox 5.1 on Fedora 25
Last fall, I wrote a piece about why I had switched to VirtualBox (from VMware Fusion) for my Vagrant needs. As part of my switch to Fedora Linux as my primary laptop OS, I revisited my choice of virtualization provider. I’ll describe that re-assessment in a separate post; the “TL;DR” for this post is that I settled on VirtualBox. As it turns out, though, installing VirtualBox 5.1 on Fedora 25 isn’t as straightforward as one might expect.
After a number of attempts (using a test VM to iron out the “best” procedure), here’s the process I found to be the most straightforward:
-
Run
dnf check-updateanddnf upgradeto pick up the latest packages. If a new kernel version is installed, reboot. (I know this sounds contrived, but I’ve run into issues where some kernel-related packages aren’t available for the kernel version you’re actually running.) -
Install the RPMFusion repos. You only really need the “free” repository, but you can install the “nonfree” as well if you like (it won’t affect this process). I won’t go through the process for how to do this; it’s really well-documented on the RPMFusion web site and is pretty straightforward.
-
Next, use
Continue reading