Show 307: Teridion s New Take On SaaS Performance & Quality Of Experience (Sponsored)
Teridion, our sponsor for todays show, is changing the basic idea of how to select best paths across the Internet and deliver content quickly through its global network of virtual cloud routers. The post Show 307: Teridion s New Take On SaaS Performance & Quality Of Experience (Sponsored) appeared first on Packet Pushers.
HPE’s DCN / Nuage SDN – Part 2 – First Steps Creating Virtual/Overlay Customer Network
In the previous part 1, we have installed basic HPE DCN system on a group of ESXi hosts. But we didn’t actually done anything inside it, so lets fix this by creating a first “HelloWorld” customer that we will call “NetworkGeekStuff” and deploy some virtual machines to this virtual network. In this part we are going to fix that and we will create a very basic virtual customer, a username/password for that customers administrator and create a small 3 tier ( database / internal / dmz) network using HPE DCN’s overlay virtual network. And at the very end, we are going to connect to this network a few virtual machines.
Index of article series:
- HPE’s DCN / Nuage SDN – Part 1 – Introduction and LAB Installation Tutorial
- HPE’s DCN / Nuage SDN – Part 2 – First Steps Creating Virtual/Overlay Customer Network
Starting LAB state
We will start exactly where we ended on previous part 1, but to double-check, I am going to show the main views of my vCenter and VSD environment to show how “empty” it is after a pure install that we did so far. So starting with this, below is my view on vCenter boxes, with Continue reading
An overview of TLS 1.3 and Q&A
The CloudFlare London office hosts weekly internal Tech Talks (with free lunch picked by the speaker). My recent one was an explanation of the latest version of TLS, 1.3, how it works and why it's faster and safer.
You can watch the complete talk below or just read my summarized transcript.
The Q&A session is open! Send us your questions about TLS 1.3 at [email protected] or leave them in the Disqus comments below and I'll answer them in an upcoming blog post.
Summarized transcript

To understand why TLS 1.3 is awesome, we need to take a step back and look at how TLS 1.2 works. In particular we will look at modern TLS 1.2, the kind that a recent browser would use when connecting to the CloudFlare edge.
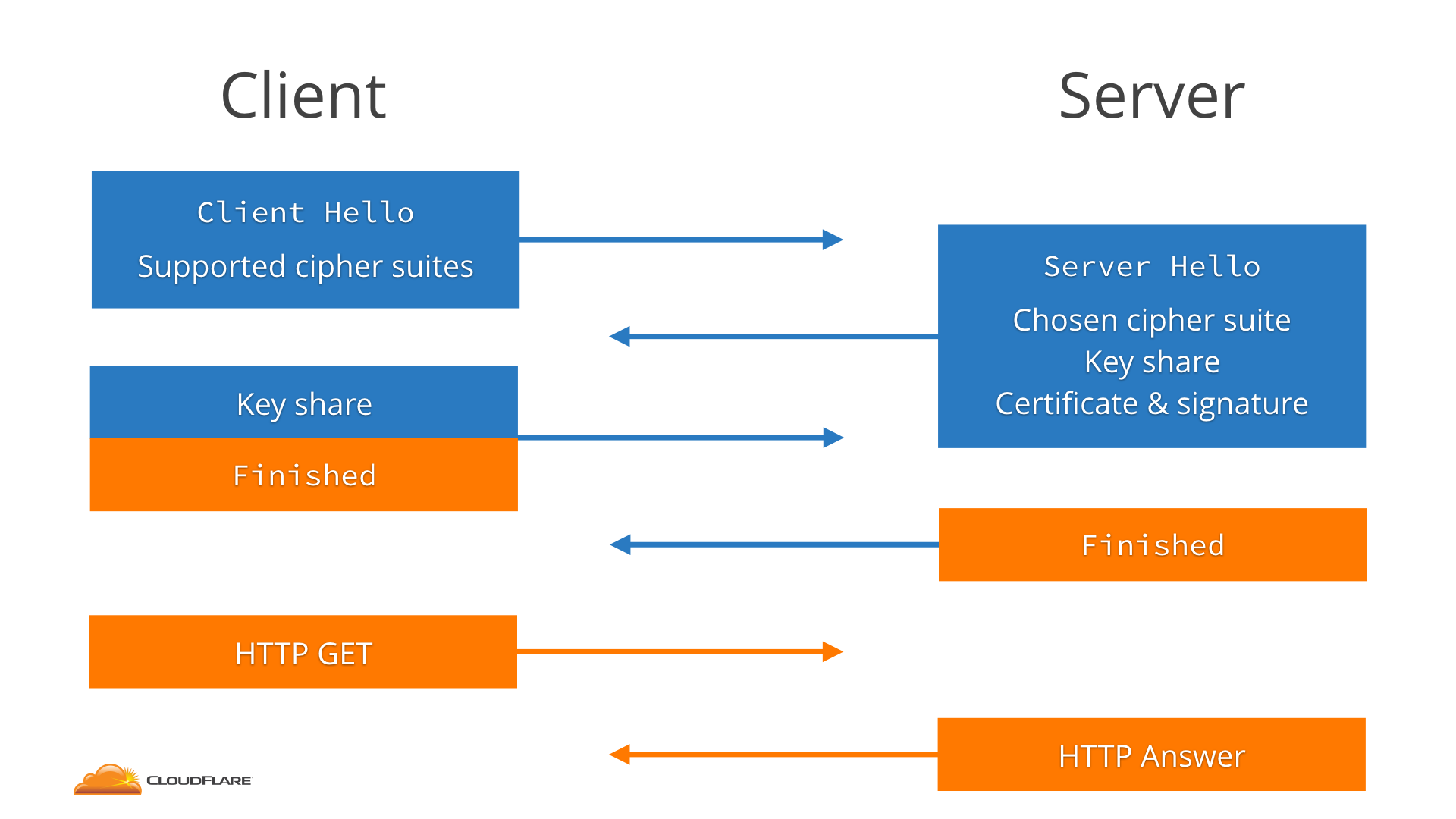
The client starts by sending a message called the ClientHello that essentially says "hey, I want to speak TLS 1.2, with one of these cipher suites".
The server receives that and answers with a ServerHello that says "sure, let's speak TLS 1.2, and I pick this cipher suite".
Along with that the server sends its key share. The Continue reading
Worth Reading: Google as an advertising gatekeeper
The post Worth Reading: Google as an advertising gatekeeper appeared first on 'net work.
How to Be A Continuous Testing Hero
 CT ensures that a new feature is tested at every stage from planning to design.
CT ensures that a new feature is tested at every stage from planning to design.
Common Criteria: Certified Products Galore!
If you track the WLAN security oriented certifications closely, you may have noticed that Ruckus was recently certified for Common Criteria.Junos MTU Handling on Access & Trunk Ports)
MTU is most important aspect for proper functionality of any application. In this blog post I will highlight MTU handling by Junos based devices for (802.3 un-tag and 802.1Q tag packets) .

Simple 802.3 packet header is shown above total packet size is 1514 bytes (14 bytes header + 1500 bytes max payload). Now we will see how Junos based devices handle MTU on access ports.
- LAB> show interfaces xe-1/0/32
Physical interface: xe-1/0/32, Enabled, Physical link is UpLink-level type: Ethernet, MTU: 1514, MRU: 0, Link-mode: Auto, Speed: Auto, BPDU Error: None, MAC-REWRITE Error: None, Loopback: Disabled, Source filtering: Disabled, Flow control: Disabled, Auto-negotiation: Disabled,
———-output omitted for brevity——————–
Protocol eth-switch, MTU: 1514 - LAB > monitor traffic interface xe-1/0/32 no-resolve layer2-headers print-hex 02:09:00.266841 Out 00:31:46:52:dd:80 > 00:1e:0b:d3:1d:1a, ethertype 802.1Q (0x8100), length 1486: vlan 243, p 0, ethertype IPv4, truncated-ip – 32 bytes missing!
(tos 0x0, ttl 64, id 49385, offset 0, flags [DF], proto: ICMP (1), length: 1500)
192.168.243.1 > 192.168.243.52: ICMP echo reply, id 29316, seq 5, length 1480
- As we can see an access interface “xe-1/0/32″ showing MTU 1514 but when we monitor traffic on Continue reading
Integrating RHV & OpenStack with Neutron
Hi folks, I recently posted an article on one of the official Red Hat blogs about the new Neutron integration between RHV and RHOSP. I have to say it’s very cool and might change the way you look at networking capabilities in RHV, at least if you’re also using RHOSP in the same data center.
As a side note, I’ve mentioned my friend and colleague, Tony James in recent posts and he makes another appearance this week. He helped pull together the configuration steps as well as the demo that we recorded. Big kudos to to “Big T”.
Back to the actual integration. If you don’t want to look at the other article, the condensed version of “why should you might care” is as follows:
- Run applications across RHV & RHOSP – front end of the app on RHOSP and the back end on RHV using the Neutron integration to bridge the network gap.
- Add SDN capabilities to RHV via the Neutron integration, even if the app only exists in RHV.
- Manage the SDN network topologies for both RHV and RHOSP from a single management space (web or programmatic).
Those are the 3 big use cases, in a nutshell. If Continue reading
