Clear Pricing for Network Services
I had to buy some switches recently and needed to gather a second quote from another vendor. I went to the Dell website and was pleasantly surprised to quickly find a clear price and a buy-now button for each device on their website.
Normally you’d need an account of the vendors portal to get this information, so it is refreshing to have straightforward access to clear hardware pricing. However it was the list of professional services options shown in the attached image that caught my eye.
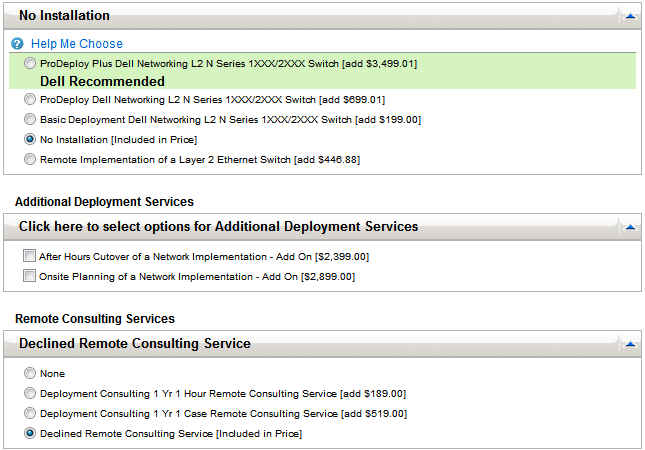 You can choose options for ‘rack and cable’ basic deployment or more comprehensive ProDeploy solution. The out-of-hours cut-over and other on-site planning options are a lot more expensive, but I’d imagine those tasks require more polished and experienced engineers to be engaged, and a lot more time-risk. Lastly you have the more tightly defined remote consulting options, with a 1-hour or a higher-priced 1-case options of the course of a single year.
You can choose options for ‘rack and cable’ basic deployment or more comprehensive ProDeploy solution. The out-of-hours cut-over and other on-site planning options are a lot more expensive, but I’d imagine those tasks require more polished and experienced engineers to be engaged, and a lot more time-risk. Lastly you have the more tightly defined remote consulting options, with a 1-hour or a higher-priced 1-case options of the course of a single year.
You could quibble with some of the prices but I was really surprised to see fixed pricing for professional services, presented in an easy-to-consume and transparent manner. I’ve always had an interest in business. Now that I’m more focused on network consulting I’m paying very close attention to how consulting effort is estimated Continue reading
Clear Pricing for Network Services
I had to buy some switches recently and needed to gather a second quote from another vendor. I went to the Dell website and was pleasantly surprised to quickly find a clear price and a buy-now button for each device on their website. Normally … Continue reading
The post Clear Pricing for Network Services appeared first on The Network Sherpa.
Intel Cuts 12,000 as It Navigates Toward Cloud & IoT
 It's a post-PC world.
It's a post-PC world.
Developing OpenSwitch With Linux VM/OS X Host

Note: This article was originally published here.
One of the purposes when we designed the build system in OpenSwitch, was to make it possible to develop on as many environments as possible. If you have some background with developing networking firmware, the typical developer love to have this VM where everything works perfectly, but makes it impossible to work in your laptop at 30000 feet. This is not really a sin (as long as you can have the VM hosted in your machine), but the problem is that usually is some IT team on charge of the VMs setup, and the deployment is not handled by some automated/version-controlled code.
So for OpenSwitch, we aimed to at least document the requirements and steps for manual setup of your environment. You can read this page to get your Linux machine to ready it for OpenSwitch development.
So, why to write an article about my particular setup? Well, I’m a Mac user, so in this article I’m going to detail my setup using a OS X host with a Linux VM. This provides some nice tricks that makes your workflow easier if you are using a similar setup. I will also explain Continue reading
Mesosphere Attracts Heavy Hitters to Its DC/OS Project
 Mesosphere leads the charge with Microsoft, HPE, Cisco, and EMC support.
Mesosphere leads the charge with Microsoft, HPE, Cisco, and EMC support.
Mirantis Gathers More Partners for OpenStack Appliances
 Making OpenStack easier, box by box.
Making OpenStack easier, box by box.
Back to Basics: Cooling – Part 1
In this pair of articles I will be dissecting the fundamentals of cooling and refrigeration from an IT engineering perspective, then going over the process of sizing a cooling system. As infrastructure engineers, we likely deal with the topic of cooling on occasion, and those occasions tend to be during a facility buildout/upgrade or outage […]
The post Back to Basics: Cooling – Part 1 appeared first on Packet Pushers.
Back to Basics: Cooling – Part 1
In this pair of articles I will be dissecting the fundamentals of cooling and refrigeration from an IT engineering perspective, then going over the process of sizing a cooling system. As infrastructure engineers, we likely deal with the topic of cooling on occasion, and those occasions tend to be during a facility buildout/upgrade or outage […]
The post Back to Basics: Cooling – Part 1 appeared first on Packet Pushers.