Show 274: Packet Pushers Live! Viptela & Three Real-World SD-WAN Deployments (Sponsored)
The Packet Pushers are recorded live in New York in a podcast sponsored by Viptela. Greg and Ethan talk to 3 Viptela SD-WAN customers about their experiences deploying and running SD-WANs. They dive into speed of deployment, operational wins, security, and more.
The post Show 274: Packet Pushers Live! Viptela & Three Real-World SD-WAN Deployments (Sponsored) appeared first on Packet Pushers.
Show 274: Packet Pushers Live! Viptela & Three Real-World SD-WAN Deployments (Sponsored)
The Packet Pushers are recorded live in New York in a podcast sponsored by Viptela. Greg and Ethan talk to 3 Viptela SD-WAN customers about their experiences deploying and running SD-WANs. They dive into speed of deployment, operational wins, security, and more.
The post Show 274: Packet Pushers Live! Viptela & Three Real-World SD-WAN Deployments (Sponsored) appeared first on Packet Pushers.
The 8 Worst Data Breaches Of All Time
Corporate security breaches are common, yet disastrous. Learn from the most severe breaches so far.
Storage Spending On The Rise
451 Research finds that companies plan to spend more on public cloud storage as they prioritize disaster recovery and backup.
Configure the Brocade NOS REST API to use HTTPS
Brocade VDX switches have REST and NETCONF interfaces. The REST API uses the built-in HTTP server. By default, this uses plain-text HTTP. As of NOS 6.0, you can (and should!) use HTTPS. If NOS has a certificate configured, it will automatically use HTTPS. Here’s how to configure it.
Pre-Change Tests
Let’s just do a couple of quick checks before we begin. Check that the switch is only listening on port 80, and that it responds to simple API queries:
Lindsays-MacBook:~ lhill$ nmap -p80,443 10.254.4.125 Starting Nmap 7.00 ( https://nmap.org ) at 2016-02-05 18:56 NZDT Nmap scan report for 10.254.4.125 Host is up (0.14s latency). PORT STATE SERVICE 80/tcp open http 443/tcp closed https Nmap done: 1 IP address (1 host up) scanned in 0.52 seconds Lindsays-MacBook:~ lhill$ curl -u admin:password -d "<activate-status></activate-status>" http://10.254.4.125/rest/operational-state/activate-status <output xmlns='urn:brocade.com:mgmt:brocade-firmware'> <overall-status>0</overall-status> <activate-entries> <rbridge-id>1</rbridge-id> <status>0</status> </activate-entries> </output> Lindsays-MacBook:~ lhill$ ssh [email protected] [email protected]'s password: Welcome to the Brocade Network Operating System Software admin connected from 10.252.131.4 using ssh on Leaf-203025 Leaf-203025# show http server status rbridge-id 1: Status: HTTP Enabled and HTTPS Continue reading
Introduction to BGP-LS and PCEP
Julian Lucek did a fantastic job describing how NorthStar controller uses BGP-LS and PCEP, so I asked him whether he’d be willing to do a deep dive on these two topics. He gracefully agreed, and the results are already online.
Read more ...CoreOS Aims rkt 1.0 at Improving Container Security
 It's about security, not about challenging Docker, CoreOS says.
It's about security, not about challenging Docker, CoreOS says.
BT Taps Its Own Cisco Routers for SD-WAN
 BT will manage the SD-WAN services.
BT will manage the SD-WAN services.
Docker 1.10: New Compose file, improved security, networking and much more!
We’re pleased to announce Docker 1.10, jam-packed with stuff you’ve been asking for. It’s now much easier to define and run complex distributed apps with Docker Compose. The power that Compose brought to orchestrating containers is now available for setting … ContinuedDocker 1.10: New Compose file, improved security, networking and much more!
We’re pleased to announce Docker 1.10, jam-packed with stuff you’ve been asking for. It’s now much easier to define and run complex distributed apps with Docker Compose. The power that Compose brought to orchestrating containers is now available for setting … ContinuedDocker Engine 1.10 Security Improvements
It’s been a crazy past few months with DockerCon and the holidays but yet we are still hacking away on the Docker Engine and have some really awesome security features I would like to highlight with the release of Docker … ContinuedDocker Engine 1.10 Security Improvements
It’s been a crazy past few months with DockerCon and the holidays but yet we are still hacking away on the Docker Engine and have some really awesome security features I would like to highlight with the release of Docker … ContinuedCollege students need food, sleep… and Wi-Fi. [VIDEO]
How important is Wi-Fi to education? When it comes to earning a college degree, reliable Wi-Fi is essential. Students want to be connected anywhere, any time in classrooms, dorm rooms, student centers, stadiums, or just walking across the quad. Reliable...SDN? I Still Don’t kNow what it is…

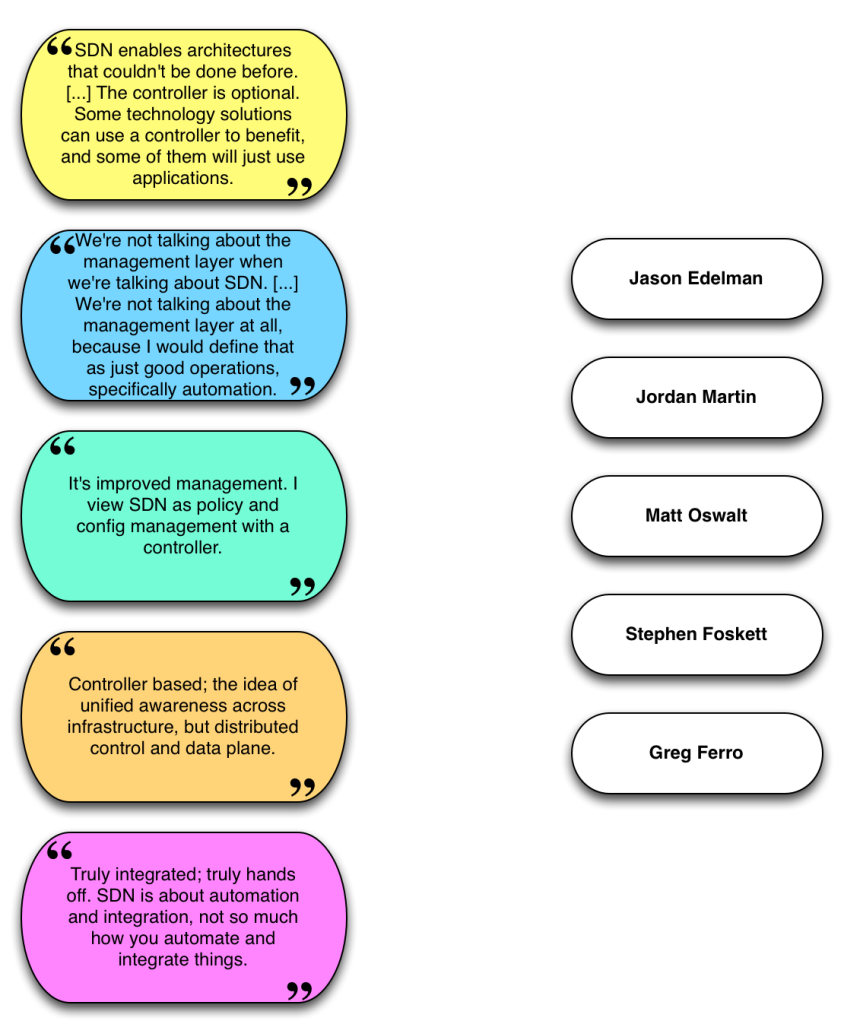
Today you get to play the SDN Definition Game: match the definition of Software Defined Neworking with the person who said it at the Networking Field Day 11 Delegate Roundtable. I’d make this exercise “drag and drop” but that sounds a bit complicated, so instead you’re on your honor not to cheat. Click on the image to see the answers in a new window.
SDN, Whatever That Is
I should note that the quotes I used were taken from conversation, so if I mis-transcribed anything or used it too far out of context I apologize to the speaker concerned. In actual fact though, who said what in this case doesn’t really matter. I shared the quotes to demonstrate that even when defined by a group of smart people like these, there doesn’t seem to be one definition of SDN that everybody can agree on. That has opened the door for marketing departments everywhere to use the SDN tag on anything and everything (aka “SDN Washing”) in the hopes that it sounds impressive and thus presumably increases sales. As a result, many people – both vendors and customers – believe that SDN is becoming a four letter word.