The Next Network Transformation: We have only just begun
Whenever we get to the end of a year we have this tendency to reflect on what has happened in the past year and how we can improve in the coming year. It’s natural to use the change of calendar year as a point in time to think back, even though practically speaking it is usually the most chaotic time of the year between shopping, family and year and quarter end at work.
Almost every industry will go through waves of change and transformation. Real change and transformation is driven by powerful market forces of demand coupled with technology leaps that allow an escape from incremental changes that drive day to day improvements. Networking has gone through several of these transformations. From dedicated main frame based connectivity, to coax based shared ethernet to switches ethernet in local area networks. From 1200 baud dialup serial connections through X.25 (yes, that’s the European in me) to leased T1 to ATM, to Frame Relay, to Packet over SONET to MPLS and various flavors of wide area ethernet services. Some of these were incremental, some of them truly transformational.
When you look back, each of these changes in network technology was very much Continue reading
Resources for learning HP Comware
HP is making more resources available to help with learning Comware. They’ve added free labs and courses to the already published simulators and virtual routers. This is a good resource for those looking to get started with Comware.
HP Network Simulator (HNS, aka Simware)
HP’s Network Simulator (HNS) is a modelling tool for simulating HP Comware networks. It includes Layer-2 functionality, and lets you test things like LACP & IRF. I found it too slow when I first tried it, but this has improved significantly with current versions. It is free to download.
HP has now started publishing simple labs you can work through with HNS:
- Lab 1 – Basic management
- Lab 2 – Port and link management
- Lab 3 – Port-based and protocol-based VLANs
These are short labs that cover HNS setup, and device configuration. Quick and easy, they show how to use the tool, and give you a taste of Comware configuration. They’ve also released a free 1-hour online course that goes through how to use HNS.
VSR1000
I’ve covered the HP VSR1000 previously. This Continue reading
VMs Running In My ESXi Networking Lab as of 23-Dec-2014
Over the last several months, I’ve been building a lab full of virtual machines related to networking. I am using 2 independent ESXi hosts running vSphere 5.5 running on Haswell motherboards with 32GB of RAM, 256GB local SSDs, and a Synology DS1813+ for big, slow remote storage I access with NFS. You can […]Dear Leader’s Lesson in Confirmation Bias
Brian Krebs has a blogpost citing those who claim evidence of North Korea involvement in the massive Sony hack. He uses as an example the similarities between the Sony defacement and a South Korean defacement that was attributed to the North Koreans. He shows these two images side-by-side so that you can see that they are obvious similar.- black background
- green, red, and white foreground
- "Hacked by" message
- WARNING banner
- Phrack-style headers (like ::: on either side of header)
- Powerful picture in center, often a skull
- Message that strokes the ego, often "we are legion" style
REST API for Cumulus Linux ACLs
RESTful control of Cumulus Linux ACLs included a proof of concept script that demonstrated how to remotely control iptables entries in Cumulus Linux. Cumulus Linux in turn converts the standard Linux iptables rules into the hardware ACLs implemented by merchant silicon switch ASICs to deliver line rate filtering.Previous blog posts demonstrated how remote control of Cumulus Linux ACLs can be used for DDoS mitigation and Large "Elephant" flow marking.
A more advanced version of the script is now available on GitHub:
https://github.com/pphaal/acl_server/
The new script adds the following features:
- It now runs as a daemon.
- Exceptions generated by cl-acltool are caught and handled
- Rules are compiled asynchronously, reducing response time of REST calls
- Updates are batched, supporting hundreds of operations per second
Fortunately, Cumulus Linux is a open Linux distribution that allows additional software components to be installed. Rather than being forced to add authentication and encryption to the script, it is possible to install additional software and leverage the capabilities of a mature web server such as Apache. Continue reading
Expiring The Internet
An article came out this week that really made me sigh. The title was “Six Aging Protocols That Could Cripple The Internet“. I dove right in, expecting to see how things like Finger were old and needed to be disabled and removed. Imagine my surprise when I saw things like BGP4 and SMTP on the list. I really tried not to smack my own forehead as I flipped through the slideshow of how the foundation of the Internet is old and is at risk of meltdown.
If It Ain’t Broke
Engineers love the old adage “If it ain’t broke, don’t fix it!”. We spend our careers planning and implementing. We also spend a lot of time not touching things afterwards in order to prevent it from collapsing in a big heap. Once something is put in place, it tends to stay that way until something necessitates a change.
BGP is a perfect example. The basics of BGP remain largely the same from when it was first implemented years ago. BGP4 has been in use since 1994 even though RFC 4271 didn’t officially formalize it until 2006. It remains a critical part of how the Continue reading
Happy Holidays from Packet Design
Happy Holidays from Packet Design
by Patrick Kilgore, Interactive Marketing Manager - December 23, 2014
It is that time of year again… and what a difference a year makes! We grew leaps and bounds in 2014, increasing our headcount as an organization and working hard to provide our customers with the best in route analytics technology.
To give back for all our good fortune in 2014, we adopted two families in the Austin area and provided additional "cheer" to make their holidays bright. Everyone at Packet Design came together to donate gifts and their time, and we could not have been happier at the participation in such a worthy endeavor. Packet Design would like to extend a special thanks to Angela Reyna, a key member of our marketing team, for putting it all together. It is moments like these that give us pause to remember that people, working as a team, make our organization a success. So from our Packet Design family to yours, we wish you Happy Holidays and a spirited New Year!
Below are photos from our wrapping party, where the Packet Design elves showed off their gift-wrapping and logistics skills:
Automating Cisco Nexus Switches with Ansible
The following video shows how Ansible can be used to automate interfaces and VLANs on Nexus switches. This will be the first in a Continue reading
PQ Show 38 – HP Networking, Helion, OpenStack and Cloud Networking
HP Helion is the cloud platform HP is bringing to Enterprise for private cloud and used by HP to build their Helion public cloud. In this show, recorded at HP Discover as part of our show coverege, we talk about Virtual Cloud Network (VCN) for OpenStack that uses OpenFlow and OVSDB as a basis for implementing features in the physical network in OpenStack and Helion.
Author information
The post PQ Show 38 – HP Networking, Helion, OpenStack and Cloud Networking appeared first on Packet Pushers Podcast and was written by Greg Ferro.
Merry Christmas to the PacketU Community
I wanted to take a moment to wish all PacketU readers a Merry Christmas and a Happy New Year. With that, I leave you with a short video clip of my son playing Silent Night at a church program last week. Longtime friends know that we had a pretty serious health scare with him 5 years ago and we count ourselves very blessed to have him in our lives.
The post Merry Christmas to the PacketU Community appeared first on PacketU.
Someone Disconnects North Korea – Who?

North Korea went off the Internet Monday, 22 December 2014, at 16:15 UTC (01:15 UTC Tuesday in Pyongyang) after more than 24 hours of sustained weekend instability. Dyn continually measures the connectivity and performance of more than 510,000 individual networks worldwide, identifying impairments to Internet commerce. It’s a rare event these days when an entire country leaves the Internet (as Egypt did, or Syria). Even so, when North Korea’s four networks went dark, we were not entirely surprised, based on the fragility of their national connectivity to the global Internet.
Who caused this, and how? A long pattern of up-and-down connectivity, followed by a total outage, seems consistent with a fragile network under external attack. But it’s also consistent with more common causes, such as power problems. Point causes such as breaks in fiberoptic cables, or deliberate upstream provider disconnections, seem less likely because they don’t generate prolonged instability before a total failure. We can only guess. The data themselves don’t speak to motivations, or distinguish human factors from physical infrastructure problems.
As the sun rises in Pyongyang, the national Internet disconnection continues. An outage of this duration is not without precedent for North Korea. As we’ve written before, Continue reading
Automating Cisco Nexus Switches with Ansible
For the past several years, the open source [network] community has been rallying around Ansible as a platform for network automation. Just over a year ago, Ansible recognized the importance of embracing the network community and since then, has made significant additions to offer network automation out of the box. In this post, we’ll look at two distinct models you can use when automating network devices with Ansible, specifically focusing on Cisco Nexus switches. I’ll refer to these models as CLI-Driven and Abstraction-Driven Automation.
Note: We’ll see in later posts how we can use these models and a third model to accomplish intent-driven automation as well.
For this post, we’ve chosen to highlight Nexus as there are more Nexus Ansible modules than any other network operating system as of Ansible 2.2 making it extremely easy to highlight these two models.
CLI-Driven Automation
The first way to manage network devices with Ansible is to use the Ansible modules that are supported by a diverse number of operating systems including NX-OS, EOS, Junos, IOS, IOS-XR, and many more. These modules can be considered the lowest common denominator as they work the same way across operating systems requiring you to define the Continue reading
North Korea Goes Offline
It was reported earlier today that North Korea was having Internet connectivity issues.
Now obviously given recent events with Sony, this sort of report is far more fascinating than it normally would be. The first question when you see this type of report is whether it’s purely a connectivity issue or whether an attack is behind it. While visibility into North Korean Internet is quite difficult, we are able to see quite a few attacks over the last few days.
1.) All targets are in this netblock:
inetnum: 175.45.176.0 – 175.45.179.255
netname: STAR-KP
descr: Ryugyong-dong
descr: Potong-gang District
country: KP
admin-c: SJVC1-AP
tech-c: SJVC1-AP
status: ALLOCATED PORTABLE
2.) pDNS Data on the specific targets
175.45.176.8 – This appears to be primary DNS
175.45.176.9 – This appears to be secondary DNS
175.45.176.10 – smtp.star-co.net.kp
175.45.176.67 – naenara.com.kp
175.45.176.77 – Unknown
175.45.176.79 – www.ryongnamsan.edu.kp
3.) Port Analysis
– All attacks on the 18th, 19th and 20th target port 80
– All attacks (except for one) on the 21st Continue reading
iPexpert Introduces Jarrod Mills, as CTO and Sr. Routing and Switching Product Portfolio Director / Instructor
As a former attorney, I often found myself drawn to the comfort and familiarity of my office computer. While the thought of spending countless hours toiling over legal briefs caused me much discomfort, spending that same amount of time on a computer was therapeutic. Now, many years later, I can see how my transition into IT was a natural progression, but at the time it seemed crazy to those close to me.
From my formative years on the competitive math team in middle school and high school, to attending college, graduate school and law school on full academic scholarships, I have always striven to excel. What I lacked in career path clarity, I made up for in sheer determination.
Over the past 20 years, I have been fortunate enough to pursue my passion in networking, designing and building world-class networks for Fortune 50 companies throughout the world. Through hard work and perseverance, I have been able to attain 4 CCIE’s (Routing and Switching, Security, Service Provider, Data Center – AND – Wayne has already given me a deadline for #5! ;-). I’ve also been able to amass countless other IT certifications, while simultaneously mentoring and teaching numerous friends and colleagues in Continue reading
Kyoto Tycoon Secure Replication
Kyoto Tycoon is a distributed key-value store written by FAL Labs, and it is used extensively at CloudFlare. Like many popular key-value stores, Kyoto Tycoon uses timestamp-based replication to ensure eventual consistency and guarantee ordering. Kyoto Tycoon is an open source project, and in the spirit of the holidays, we’re contributing our internal changes back to the open source project.
 CC BY-ND 2.0 image by Moyan Brenn
CC BY-ND 2.0 image by Moyan Brenn
CloudFlare uses Kyoto Tycoon to replicate data from a Postgres Database to our 30 data centers around the world. In practice, it takes around 3 seconds for full propagation in normal conditions. This is our pipeline for distributing sensitive data like our session ticket keys and DNS data to the CloudFlare edge.
Protecting data in transit
If the Internet is not a dangerous place, it at least has dangerous neighborhoods. To move from one datacenter to another, data has to pass through the public Internet. Data could end up going though some network with a wire-tap in place, or through a network with an unscrupulous network operator.
Datacenter-to-datacenter encryption has been brought into the international spotlight since the surveillance revelations. One of the leaked slides contained the expression “SSL added Continue reading
Fabric visibility with Cumulus Linux
A leaf and spine fabric is challenging to monitor. The fabric spreads traffic across all the switches and links in order to maximize bandwidth. Unlike traditional hierarchical network designs, where a small number of links can be monitored to provide visibility, a leaf and spine network has no special links or switches where running CLI commands or attaching a probe would provide visibility. Even if it were possible to attach probes, the effective bandwidth of a leaf and spine network can be as high as a Petabit/second, well beyond the capabilities of current generation monitoring tools.The 2 minute video provides an overview of some of the performance challenges with leaf and spine fabrics and demonstrates Fabric View - a monitoring solution that leverages industry standard sFlow instrumentation in commodity data center switches to provide real-time visibility into fabric performance.
Fabric View is free to try, just register at http://www.myinmon.com/ and request an evaluation. The software requires an accurate network topology in order to characterize performance and this article will describe how to obtain the topology from a Cumulus Networks fabric.
Complex Topology and Wiring Validation in Data Centers describes how Cumulus Networks' prescriptive topology manager (PTM) provides Continue reading
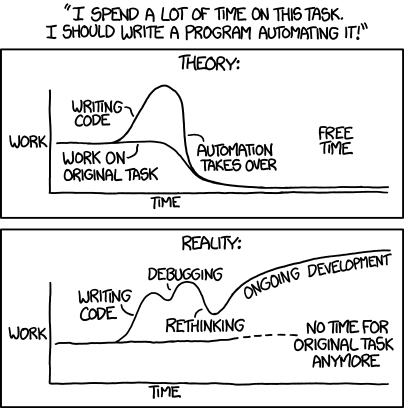
Automation Isn’t Just About Speed
In talking with folks about automation, the conversation almost always come around to “speed, speed, speed”. It’s easy to see why this is the first benefit that pops into mind – we’ve all spent gratuitous amounts of time doing repetitive, time-consuming tasks. It’s obvious why the prospect of automating these tasks and getting the time back is such an attractive one, even though most of us that have tried know that this is an absolute reality:
All kidding (but some…..seriousing?) aside, is speed the only benefit? In the realm of IT infrastructure, should we pursue automation only when this other piece of brilliance tells us it’s worth it?
Consider a small deployment of a few switches, a router, maybe some servers. Using manual methods to configure the relatively small amount of infrastructure isn’t really sexy, but it’s also not a huge time suck either. There’s just not a lot of infrastructure in these small deployments, and manual configuration doesn’t really impact the rate of change.
As a result, when discussing automation concepts with small, and even medium-size shops, I’m usually met with understandable skepticism. There’s a huge part of IT industry that assumes that all of our Continue reading