Post-quantum cryptography goes GA
Over the last twelve months, we have been talking about the new baseline of encryption on the Internet: post-quantum cryptography. During Birthday Week last year we announced that our beta of Kyber was available for testing, and that Cloudflare Tunnel could be enabled with post-quantum cryptography. Earlier this year, we made our stance clear that this foundational technology should be available to everyone for free, forever.
Today, we have hit a milestone after six years and 31 blog posts in the making: we’re starting to roll out General Availability1 of post-quantum cryptography support to our customers, services, and internal systems as described more fully below. This includes products like Pingora for origin connectivity, 1.1.1.1, R2, Argo Smart Routing, Snippets, and so many more.
This is a milestone for the Internet. We don't yet know when quantum computers will have enough scale to break today's cryptography, but the benefits of upgrading to post-quantum cryptography now are clear. Fast connections and future-proofed security are all possible today because of the advances made by Cloudflare, Google, Mozilla, the National Institutes of Standards and Technology in the United States, the Internet Engineering Task Force, and numerous academic institutions
What does Continue reading
Easily manage AI crawlers with our new bot categories
Today, we’re excited to announce that any Cloudflare user, on any plan, can choose specific categories of bots that they want to allow or block, including AI crawlers.
As the popularity of generative AI has grown, content creators and policymakers around the world have started to ask questions about what data AI companies are using to train their models without permission. As with all new innovative technologies, laws will likely need to evolve to address different parties' interests and what’s best for society at large. While we don’t know how it will shake out, we believe that website operators should have an easy way to block unwanted AI crawlers and to also let AI bots know when they are permitted to crawl their websites.
The good news is that Cloudflare already automatically stops scraper bots today. But we want to make it even easier for customers to be sure they are protected, see how frequently AI scrapers might be visiting their sites, and respond to them in more targeted ways. We also recognize that not all AI crawlers are the same and that some AI companies are looking for clear instructions for when they should not crawl a public website.
Continue reading
Cloudflare is free of CAPTCHAs; Turnstile is free for everyone


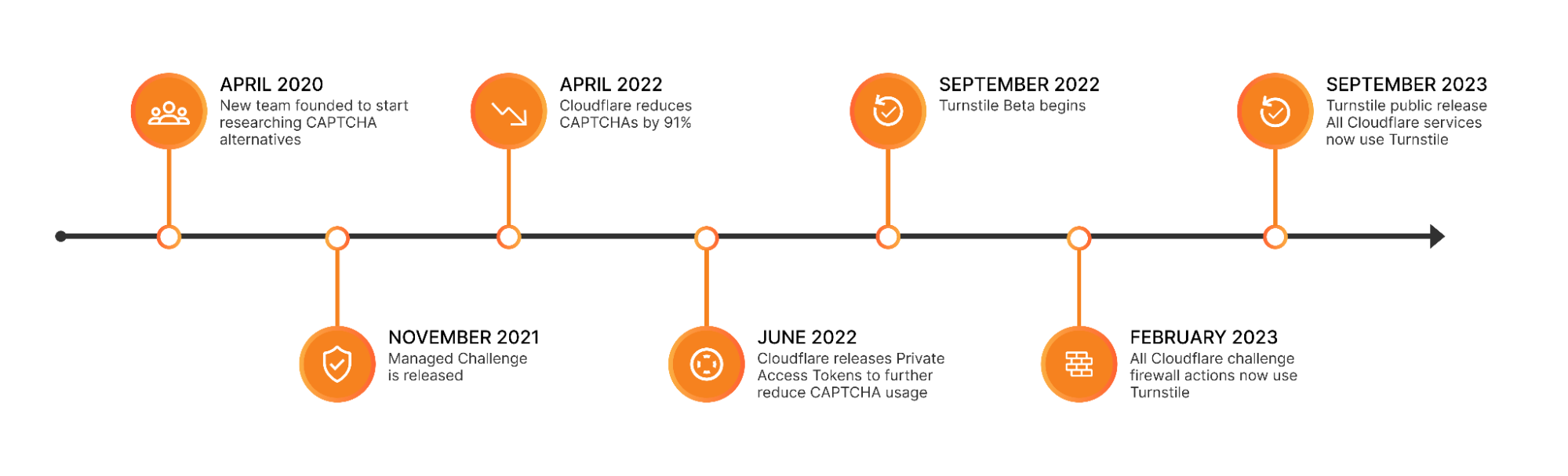
For years, we’ve written that CAPTCHAs drive us crazy. Humans give up on CAPTCHA puzzles approximately 15% of the time and, maddeningly, CAPTCHAs are significantly easier for bots to solve than they are for humans. We’ve spent the past three and a half years working to build a better experience for humans that’s just as effective at stopping bots. As of this month, we’ve finished replacing every CAPTCHA issued by Cloudflare with Turnstile, our new CAPTCHA replacement (pictured below). Cloudflare will never issue another visual puzzle to anyone, for any reason.
Now that we’ve eliminated CAPTCHAs at Cloudflare, we want to make it easy for anyone to do the same, even if they don’t use other Cloudflare services. We’ve decoupled Turnstile from our platform so that any website operator on any platform can use it just by adding a few lines of code. We’re thrilled to announce that Turnstile is now generally available, and Turnstile’s ‘Managed’ mode is now completely free to everyone for unlimited use.
Easy on humans, hard on bots, private for everyone
There’s a lot that goes into Turnstile’s simple checkbox to ensure that it’s easy for everyone, preserves user privacy, and does its job stopping bots. Continue reading
클라우드, 네트워크, 애플리케이션 및 사용자를 연결하고 보호하는 현대적인 방법인 클라우드 연결성으로 여러분을 모십니다
우리가 근무하면서 가장 좋아하는 부분은 Cloudflare 고객과 대화하는 시간입니다. 고객의 IT 및 보안 문제에 대하여 항상 새롭고 흥미로운 사실을 알게 됩니다.
최근 이러한 대화에 변화가 있었습니다. 고객이 언급하는 가장 큰 문제를 쉽게 정의할 수 없는 경우가 점점 더 많아집니다. 그리고 이러한 문제는 개별 제품이나 주요 기능으로 대처할 수 없는 것입니다.
더 정확히 말하면 IT 및 보안 팀에서는 디지털 환경에 대한 제어 능력을 잃고 있다고 이야기합니다.
제어 능력 상실은 다양한 형태를 띱니다. 고객은 호환성이 걱정되므로 필요성은 알지만 새로운 기능을 채택하는 것을 꺼리는 모습을 보일 수 있습니다. 아니면 비교적 단순한 변경 사항을 적용하는 데 시간과 노력이 많이 들며, 이러한 변경 사항 때문에 더 큰 영향력이 있을 작업에 투입할 시간을 빼앗기고 있다고 언급할 수도 있습니다. 고객이 느끼는 감정을 요약하자면 "팀이나 예산의 규모가 아무리 크더라도 비즈니스를 완벽하게 연결하고 보호하는 데는 절대 충분하지 않다"는 것입니다.
익숙하게 느껴지는 부분이 있으신가요? 그런 부분이 있다 해도 여러분 혼자 그렇게 느끼는 건 아닙니다.
제어 능력을 상실하는 이유
IT 및 보안이 바뀌는 속도는 빨라지고 있으며 무섭도록 복잡해지고 있습니다. IT 및 보안 팀에서는 과거에 비해 더 다양한 기술 도메인을 책임지고 있습니다. 최근 Forrester 연구에서 확인된 변화에 따르면 사내, 원격, 하이브리드 근무자를 보호할 책임이 있는 팀의 52%만이 지난 5년 동안 이러한 책임을 맡았습니다. 한편 46%는 해당 기간 동안 퍼블릭 클라우드 애플리케이션을 Continue reading
Descubre qué amenazas acechan tu buzón de correo de Office 365 con Cloudflare Email Retro Scan

Ahora los clientes de Cloudflare pueden analizar viejos mensajes de sus bandejas de entrada de Office 365 en busca de amenazas. Retro Scan te permitirá observar qué amenazas ha pasado por alto tu actual herramienta de seguridad del correo electrónico en los últimos siete días.
Por qué ejecutar Retro Scan
Al hablar con los clientes, solemos escuchar que no conocen el estado de los buzones de correo de sus organizaciones. Las organizaciones tienen una herramienta de seguridad para correo electrónico o usan la protección integrada de Microsoft, pero no entienden qué nivel de efectividad tiene la actual solución. A menudo, descubrimos que estas herramientas permiten el paso de correos electrónicos maliciosos a través de sus filtros, lo que aumenta el riesgo en la empresa.
En nuestra búsqueda de ayudar a crear un mejor servicio de Internet, permitimos a los clientes de Cloudflare el uso de Retro Scan para analizar mensajes en sus buzones de entrada con nuestros modelos de aprendizaje automático avanzados, ¡gratis! Nuestro Retro Scan detecta y resalta las amenazas que encontramos para que los clientes puedan limpiar sus buzones de entrada y gestionarlas dentro de sus cuentas de correo electrónico. Con esta información, los clientes también pueden implementar Continue reading
Veja quais ameaças estão escondidas no seu Office 365 com o Cloudflare Email Retro Scan

Agora anunciamos a possibilidade de os clientes da Cloudflare verificarem mensagens antigas em suas caixas de entrada do Office 365 em busca de ameaças. Este Retro Scan permitirá que você analise sete dias atrás e veja quais ameaças sua ferramenta de segurança de e-mail atual deixou passar.
Por que executar um Retro Scan
Conversando com os clientes, ouvimos frequentemente que eles não sabem o estado das caixas de entrada de suas organizações. As organizações possuem uma ferramenta de segurança de e-mail ou usam a proteção integrada da Microsoft, mas não entendem a eficácia de sua solução atual. Descobrimos que essas ferramentas muitas vezes permitem que e-mails maliciosos passem por seus filtros, aumentando o risco de comprometimento dentro da empresa.
Em nossa busca para ajudar a construir uma internet melhor, disponibilizamos para os clientes da Cloudflare o uso do Retro Scan para verificar mensagens em suas caixas de entrada usando nossos modelos avançados de aprendizado de máquina gratuitamente. Nosso Retro Scan detecta e destaca quaisquer ameaças que encontrarmos, assim os clientes podem limpar suas caixas de entrada tratando-as em suas contas de e-mail. Com essas informações, os clientes também podem implementar controles adicionais, como usar a Cloudflare ou sua solução preferida, Continue reading
Sehen Sie, welche Bedrohungen in Ihrem Office 365 lauern – mit dem Retro Scan von Cloudflare für E-Mails

Ab sofort können Cloudflare-Kunden alte Nachrichten in ihren Office 365-Postfächern auf Bedrohungen hin scannen. Mit dem Retro Scan können Sie jeweils die vergangenen sieben Tage überprüfen, um zu sehen, welche Bedrohungen Ihrem aktuellen E-Mail-Sicherheitstool entgangen sind.
Gründe für den Einsatz eines Retro Scan
Kunden berichten uns oft, dass sie nicht wissen, in welchem Zustand die E-Mail-Postfächer ihrer Unternehmen sind. Firmen nutzen ein E-Mail-Sicherheitstool oder den bei Microsoft integrierten Schutz. Oft ist wissen sie aber nicht, wie effektiv ihre aktuelle Lösung tatsächlich arbeitet. Wir haben festgestellt, dass schädliche E-Mails von diesen Werkzeugen oft nicht herausgefiltert werden, wodurch sich das Risiko einer Kompromittierung innerhalb des Unternehmens erhöht.
Im Rahmen unserer Bemühungen, ein besseres Internet zu schaffen, stellen wir Cloudflare-Kunden nun einen Retro Scan zur Verfügung. Mit diesem können sie Nachrichten in ihren Postfächern unter Einsatz fortschrittlicher Machine Learning-Modelle kostenlos scannen. Unser Retro Scan erkennt Bedrohungen und weist auf diese hin, sodass Kunden ihre Postfächer durch eine Behebung innerhalb ihrer E-Mail-Konten bereinigen können. Mit diesen Informationen sind sie außerdem in der Lage, herkömmliche Kontrollen zu implementieren. Sie können also Cloudflare oder ihre bevorzugte Lösung einsetzen, um vergleichbare Bedrohungen in Zukunft daran zu hindern, ihre Postfach überhaupt erst zu erreichen.
Einsatz des Retro Scan
Découvrez les menaces qui se dissimulent dans votre boîte aux lettres Office 365 avec Cloudflare Email Retro Scan

Nous annonçons maintenant la possibilité pour les clients de Cloudflare d'analyser les anciens messages dans leurs boîtes de réception Office 365 afin de détecter les menaces. Le service Retro Scan vous permet de revenir sept jours en arrière, afin d'identifier les menaces qui n'ont pas été détectées par votre outil de sécurité actuel.
Pourquoi exécuter le service Retro Scan
Lorsque nous échangeons avec nos clients, ces derniers nous apprennent souvent qu'ils n'ont pas connaissance de l'état des boîtes aux lettres de leur entreprise. Les entreprises disposent d'un outil de sécurité des e-mails, ou elles utilisent la protection intégrée de Microsoft, mais elles ne sont pas en mesure de comprendre l'efficacité de leur solution actuelle. Nous constatons que les filtres de ces outils laissent souvent passer des e-mails malveillants, augmentant le risque de compromission de données au sein des entreprises.
Conformément à notre engagement de contribuer à bâtir un Internet meilleur, nous permettons désormais aux clients de Cloudflare d'utiliser Retro Scan pour analyser les messages dans leurs boîtes de réception à l'aide de nos modèles d'apprentissage automatique avancés – et ce, gratuitement. Notre service Retro Scan détectera et mettra en évidence toutes les menaces que nous identifions, afin de permettre aux Continue reading
Hyperdrive: making databases feel like they’re global


Hyperdrive makes accessing your existing databases from Cloudflare Workers, wherever they are running, hyper fast. You connect Hyperdrive to your database, change one line of code to connect through Hyperdrive, and voilà: connections and queries get faster (and spoiler: you can use it today).
In a nutshell, Hyperdrive uses our global network to speed up queries to your existing databases, whether they’re in a legacy cloud provider or with your favorite serverless database provider; dramatically reduces the latency incurred from repeatedly setting up new database connections; and caches the most popular read queries against your database, often avoiding the need to go back to your database at all.
Without Hyperdrive, that core database — the one with your user profiles, product inventory, or running your critical web app — sitting in the us-east1 region of a legacy cloud provider is going to be really slow to access for users in Paris, Singapore and Dubai and slower than it should be for users in Los Angeles or Vancouver. With each round trip taking up to 200ms, it’s easy to burn up to a second (or more!) on the multiple round-trips needed just to set up a connection, before you’ve Continue reading
Hyperdrive: 데이터베이스를 글로벌하다고 느껴지게 만들기

Hyperdrive는 어디에서 실행되는 Cloudflare Workers에서 기존 데이터베이스에 액세스하는 것을 매우 빠르게 만듭니다. Hyperdrive를 데이터베이스와 연결하고 Hyperdrive로 연결하기 위해 단 한 줄의 코드를 바꾸면 연결과 쿼리가 마법처럼 빨라집니다(오늘 바로 사용할 수 있습니다).
요약하자면, Hyperdrive는 Cloudflare의 전역 네트워크를 사용하므로 기존 데이터베이스에 대한 쿼리 속도가 단축됩니다. 데이터베이스가 레거시 클라우드 공급자에 있든, 여러분이 좋아하는 서버리스 데이터베이스 공급자에 있든 구애받지 않습니다. Hyperdrive를 사용하면 반복적으로 새로운 데이터베이스 연결을 설정할 때 발생하는 대기 시간이 대폭 단축되고, 데이터베이스에 대한 가장 인기 있는 읽기 쿼리가 캐시되어 데이터베이스에 돌아갈 필요가 없어지는 경우가 많습니다.
Hyperdrive가 없으면 기존 클라우드 공급자의 미국 동부1 지역에 있는 핵심 데이터베이스(사용자 프로필, 제품 인벤토리, 중요한 웹 앱을 실행하는 데이터베이스)는 파리, 싱가포르, 두바이에 있는 사용자가 액세스하는 속도가 매우 느려질 수 있습니다. 로스앤젤레스나 밴쿠버에 있는 사용자에게도 예상보다 느려질 것입니다. 각 왕복 시간이 최대 200ms이므로 연결을 설정하는 데 필요한 몇 번의 왕복 자체만으로도 최대 1초(또는 그 이상!)가 걸리기 쉽습니다. 데이터를 위해 쿼리를 작성하기도 전에도 말입니다. Hyperdrive는 이러한 현상을 해결하기 위해 설계되었습니다.
Hyperdrive의 성능을 선보이기 위해 Cloudflare에서는 데모 애플리케이션을 구축했습니다. 이는 Hyperdrive를 사용한 채로 그리고 사용하지 않은 채로 (바로) 동일한 데이터베이스에 대해 연속되는 쿼리를 작성합니다. 이 앱은 주변 대륙에 있는 데이터베이스를 선택합니다. 여러분이 유럽에 있다면 이는 미국에 있는 데이터베이스를 선택합니다. 많은 유럽 인터넷 사용자가 흔히 겪는 상황입니다. Continue reading
Hyperdrive:データベースをあたかもグローバルであるかのように感じさせる

Hyperdriveは、実行されている場所を問わず、Cloudflare Workersから既存のデータベースへのアクセスを超高速にします。Hyperdriveをデータベースに接続し、Hyperdriveを経由して接続するようにコードを1行変更するだけで、接続とクエリーが高速化されます(秘密:本日から 使えます ) 。
一言で言えば、Hyperdriveは当社のグローバルネットワークを使用して、レガシーなクラウドプロバイダーであろうとお気に入りのサーバーレスデータベースプロバイダーであろうと、既存のデータベースへのクエリーを高速化し、新しいデータベース接続を繰り返し設定することで発生する遅延を劇的に短縮し、データベースに対して最も一般的な読取りクエリーをキャッシュします。これにより、データベースに戻る必要がなくなります。
Hyperdriveがなければ、レガシークラウドプロバイダーのus-east1リージョンにあるコアデータベース(ユーザープロファイル、製品在庫、または重要なWebアプリを実行しているデータベース)へのアクセスは、パリ、シンガポール、ドバイのユーザーにとっては非常に遅くなり、ロサンゼルスやバンクーバーのユーザーにとっては必要以上に遅くなります。各ラウンドトリップに最大200msかかるため、データのクエリーを行う前に、接続をセットアップするためだけに何度もラウンドトリップすることになり、1秒(またはそれ以上)も費やしてしまうことになります。Hyperdrive はこれを解決するために設計されています。
Hyperdriveのパフォーマンスを実証するため、 Hyperdriveを使用した場合とHyperdriveを使用しない場合(直接)の両方で、同じデータベースに対して連続してクエリーを実行するデモアプリケーションを作成しました。このアプリケーションは、近隣の大陸のデータベースを選択します。ヨーロッパにいる場合は米国のデータベースを選択します。これは、多くのヨーロッパのインターネットユーザーにとって非常に一般的です。アフリカにいる場合はヨーロッパのデータベースを選択します(以下同様)。このクエリーは、厳選された平均値や厳選された指標を使用せず、単純な`SELECT`クエリーから生の結果を返します。
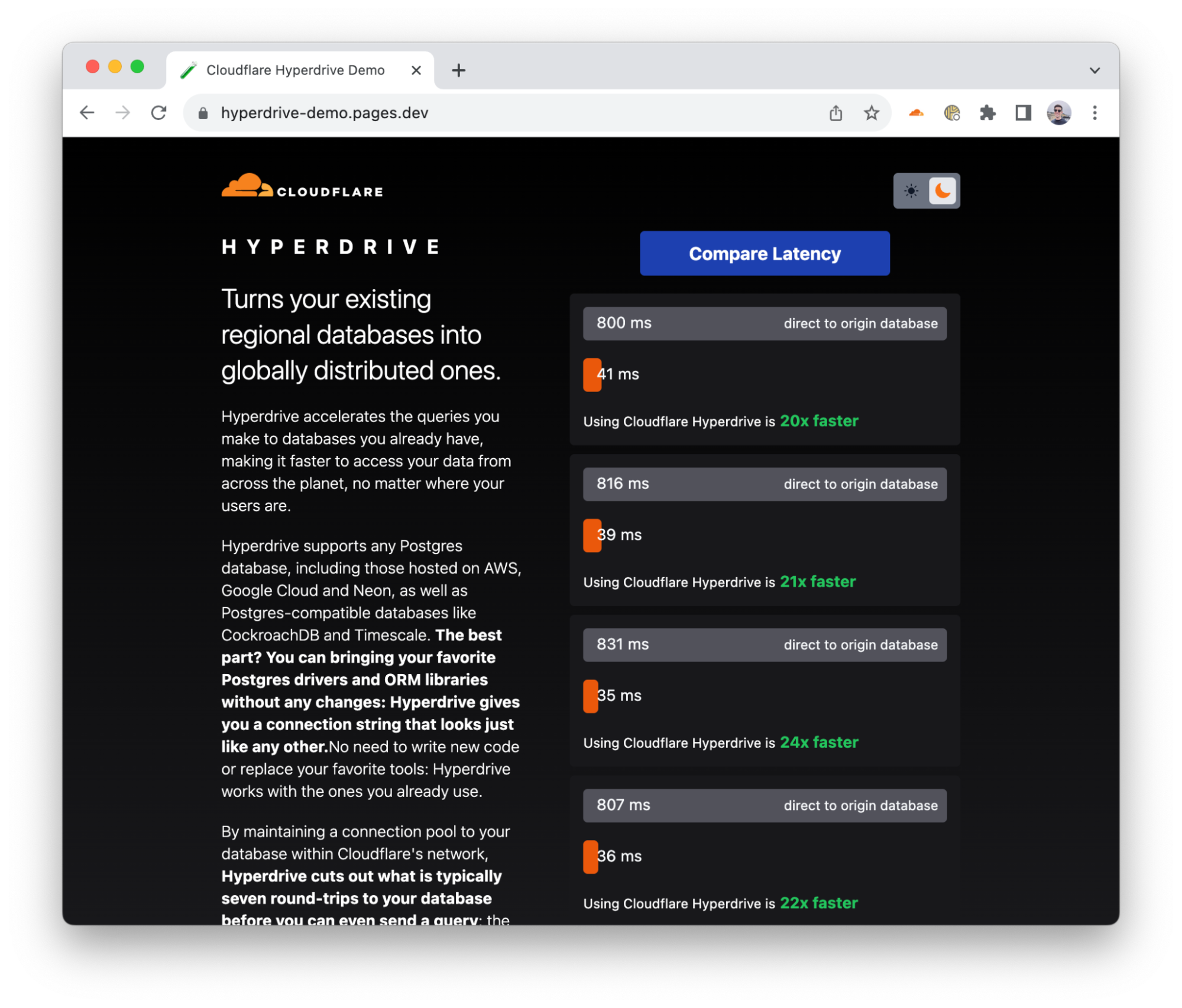
社内テスト、初期ユーザーレポート、およびベンチマークでの複数回の実行を通じて、Hyperdriveは、キャッシュされたクエリーではデータベースに直接アクセスする場合と比較して17~25倍、キャッシュされていないクエリーおよび書き込みでは6~8倍のパフォーマンス向上を実現しています。キャッシュされた遅延は驚くことではないかもしれませんが、キャッシュされていないクエリーで6~8倍速くなることは、お客様のご意見を「Cloudflare Workersから集中管理されたデータベースにクエリーできない」を「非常に有用な機能だ!」に変えると私たちは考えています。また、パフォーマンスの改善にも引き続き取り組んでいます。すでに、さらなる遅延の低減を確認しており、今後数週間のうちに、その低減分を推進していく予定です。
一番の魅力は?Workersの有料プランにお申込みいただいている開発者は、すぐにHyperdriveオープンベータを使い始めることができます。待機リストや専用の登録フォームへの登録は不要です。
Hyperdriveを聞いたことがありませんか?
私たちはしばらくの間、Hyperdriveに秘密裏に取り組んできました。ですが、開発者がすでに持っているデータベース(既存のデータ、クエリー、ツール)に接続できるようにすることは、かなり以前から考えていたことでした。
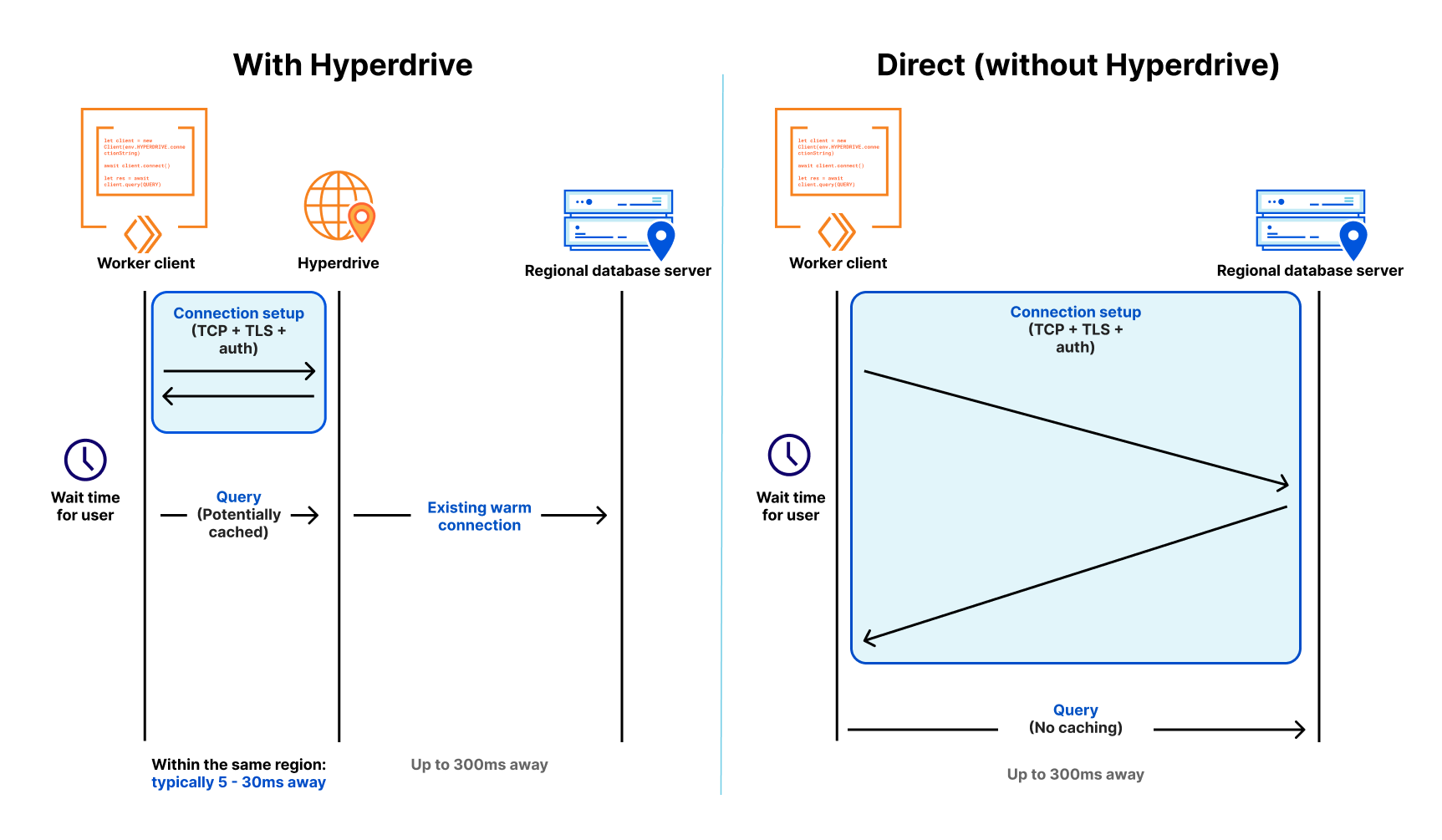
Workersのような最新の分散型クラウド環境では、コンピューティングはグローバルに分散され(そのためユーザーの近くにある)、関数は短時間で終了する(そのため必要以上の課金はされない)ため、従来のデータベースへの接続は遅くて拡張性がありませんでした。遅いというのは、接続を確立するのに7往復(TCPハンドシェイク、TLSネゴシエーション、認証)以上かかるためであり、拡張性がないというのは、PostgreSQLのようなデータベースは接続あたりのリソースコストが高いためです。データベースへの数百の接続でさえ、クエリーに必要なメモリとは別に、無視できないメモリを消費します。
Neon(人気のあるサーバーレスPostgresプロバイダー)の友人たちはこのことについて書いており、接続のオーバーヘッドを減らすためのWebSocketプロキシとドライバまでリリースしていますが、それでもまだ力戦奮闘しています。カスタムドライバを使うと4往復まで減らすことができますが、それでもそれぞれに50~200ミリ秒以上かかる可能性があります。これらの接続が長寿命であれば、それは問題ありません。しかし、接続が個々の関数呼び出しにスコープ化され、せいぜい数ミリ秒から数分しか役に立たない場合、コードはより多くの待ち時間を費やすことになります。これは事実上、別の種類のコールドスタートです。クエリーを実行する前にデータベースへの新しい接続を開始する必要があるため、分散環境やサーバーレス環境で従来のデータベースを使用するのは(控えめに言っても)本当に遅いのです。
これに対抗するため、Hyperdriveは2つのことを行います。
第一に、Cloudflare WorkerはCloudflareのネットワーク全体にわたる地域データベース接続プールのセットを維持するので、リクエストごとにデータベースへの新規接続を行う必要がありません。その代わりに、WorkerはHyperdriveへの接続を(高速で)確立し、Hyperdriveはデータベースへの接続プールを維持します。データベースは1回のラウンドトリップで30msから300msとなることがあるため (新しい接続に必要な7回以上の接続は別として)、利用可能な接続のプールを持つことで、短時間の接続が被る遅延の問題を劇的に減らすことができます。
第二に、読み取り(non-mutating)クエリーと書き込み(mutating)クエリーとトランザクションの違いを理解し、最もよく使われる読み取りクエリーを自動的にキャッシュすることができます。このクエリーは、一般的なWebアプリのデータベースに対して行われるクエリーの80%以上を占めます。何万人ものユーザーが毎時間訪れる商品一覧ページ、大手求人サイトの求人情報、あるいは時折変更される設定データに対するクエリーなど、クエリーされる内容の膨大な部分は頻繁に変更されるものではないため、ユーザーがクエリーを実行する場所の近くにキャッシュすることで、次の1万人のユーザーのデータへのアクセスを劇的に高速化することができます。安全にキャッシュすることができない書き込みクエリーは、Hyperdriveの接続プールとCloudflareのグローバルネットワークの両方から恩恵を受けることができます。つまり、バックボーンを介してインターネット上で最も早い経路をとることができれば、そこでの待ち時間も短縮できるのです。
Hyperdriveは、Neon、GoogleクラウドSQL、AWS RDS、 TimescaleなどのPostgreSQLデータベースだけでなく、 Materialize(強力なストリーム処理データベース)、CockroachDB(主要な分散データベース)、GoogleクラウドのAlloyDB、AWS Aurora PostgresなどのPostgreSQL互換データベースでも動作します。
また、PlanetScaleのようなプロバイダーも含め、MySQLのサポートを年内に実現するよう取り組んでおり、将来的にはさらに多くのデータベースエンジンをサポートする予定です。
接続用のマジック文字列
Hyperdriveの主要な設計目標の1つは、開発者が既存のドライバ、クエリービルダー、ORM(Object-Relational Mapper)ライブラリを使い続ける必要性でした。Hyperdriveのパフォーマンスの恩恵を受けるために、お気に入りのORMからの移行や、数百行(またはそれ以上)のコードの書き換えが必要であれば、Hyperdriveがどれほど高速であるかは重要ではなかったでしょう。
これを達成するために、私たちはnode-postgresやPostgres.jsを含む人気のあるオープンソースドライバのメンテナーと協力し、標準化プロセスを経ているWorkerの新しいTCPソケットAPIをライブラリがサポートできるように支援しました。そして、Node.js、Deno、Bunに対するサポートも拡充予定です。
地味なデータベース接続文字列は、データベースドライバの共有言語であり、通常、次の形式をとります。
postgres://user:[email protected]:5432/postgres
Hyperdriveの魔法は、接続文字列をHyperdriveが生成するものに置き換えるだけで、既存のWorkersアプリで、既存のクエリーで、Hyperdriveを使い始めることができるということです。
Hyperdriveの作成
既存のデータベース(この例では、NeonのPostgresデータベースを使用)が準備できていれば、Hyperdriveを起動させるのに1分もかかりません(実際、時間を計測しました)。
既存のCloudflare Workersプロジェクトがない場合は、すぐに作成できます。
$ npm create cloudflare@latest
# Call the application "hyperdrive-demo"
# Choose "Hello World Worker" as your template
ここからは、データベースの接続文字列と、 Hyperdriveに接続させるための簡単な Wrangler コマンドライン 呼び出しが必要です。
# Using wrangler v3.10.0 or above
wrangler hyperdrive create a-faster-database --connection-string="postgres://user:[email protected]:5432/neondb"
# This will return an ID: we'll use this in the next step
Workerのwrangler.toml構成ファイルにHyperdriveを追加:
[[hyperdrive]]
name = "HYPERDRIVE"
id = "cdb28782-0dfc-4aca-a445-a2c318fb26fd"
これで、Workerを書く、あるいは既存のWorkerスクリプトを利用し、Hyperdriveを使って既存のデータベースへの接続とクエリーを高速化することができます。ここで、node-postgresを使用していますが、単純にDrizzle ORMを使うこともできます。
import { Client } from 'pg';
export interface Env {
HYPERDRIVE: Hyperdrive;
}
export default {
async fetch(request: Request, env: Env, ctx: ExecutionContext) {
console.log(JSON.stringify(env));
// Create a database client that connects to our database via Hyperdrive
//
// Hyperdrive generates a unique connection string you Continue readingHyperdrive: cómo hacer que las bases de datos parezcan globales

Hyperdrive te permite un acceso ultrarrápido a tus bases de datos existentes desde Cloudflare Workers, dondequiera que se ejecuten. Conectas Hyperdrive a tu base de datos, modificas una línea de código para conectarte a través de Hyperdrive, y listo: las conexiones y las consultas son más rápidas (spoiler: puedes utilizarlo hoy mismo).
En pocas palabras, Hyperdrive utiliza nuestra red global para acelerar las consultas a tus bases de datos existentes, tanto si se encuentran en un proveedor de nube heredado como en tu proveedor favorito de bases de datos sin servidor; reduce drásticamente la latencia que implica configurar repetidamente nuevas conexiones a la base de datos; y almacena en caché las consultas de lectura a tu base de datos más populares, lo que a menudo evita incluso la necesidad de volver a tu base de datos.
Sin Hyperdrive, esa base de datos principal (la que contiene tus perfiles de usuario, tu inventario de productos o que ejecuta tus aplicaciones web críticas), ubicada en la región us-east1 de tu proveedor de nube heredado, ofrecerá un acceso muy lento a los usuarios en París, Singapur y Dubái, y más lento de lo que debería ser para los usuarios en Los Ángeles Continue reading
Hyperdrive: Damit Datenbanken global wirken

Hyperdrive macht den Zugriff auf Ihre bestehenden Datenbanken von Cloudflare Workers aus hyperschnell, egal wo sie laufen. Sie verbinden Hyperdrive mit Ihrer Datenbank, ändern eine Codezeile, um eine Verbindung über Hyperdrive herzustellen, und voilà: Verbindungen und Abfragen werden schneller (und Spoiler: Sie können es schon heute nutzen).
Kurz gesagt: Hyperdrive nutzt unser globales Netzwerk, um Abfragen an Ihre bestehenden Datenbanken zu beschleunigen, unabhängig davon, ob sich diese bei einem alten Cloud-Provider oder bei Ihrem bevorzugten Provider für Serverless-Datenbanken befinden. Die Latenz, die durch das wiederholte Einrichten neuer Datenbankverbindungen entsteht, wird drastisch reduziert, und die beliebtesten Leseabfragen an Ihre Datenbank werden zwischengespeichert, sodass Sie oft gar nicht mehr zu Ihrer Datenbank zurückkehren müssen.
Wenn Ihre Kerndatenbank – mit Ihren Nutzerprofilen, Ihrem Produktbestand oder Ihrer wichtigen Web-App – in der us-east1-Region eines veralteten Cloud-Anbieters angesiedelt ist, wird der Zugriff für Nutzende in Paris, Singapur und Dubai ohne Hyperdrive sehr langsam sein und selbst für Nutzende in Los Angeles oder Vancouver langsamer, als er sein sollte. Da jeder Roundtrip bis zu 200 ms dauert, können die mehrfachen Roundtrips, die allein für den Verbindungsaufbau erforderlich sind, leicht bis zu einer Sekunde (oder mehr!) in Anspruch nehmen; und das, bevor Sie überhaupt eine Continue reading
Hyperdrive : donner aux bases de données l'impression d'être mondiales

Hyperdrive vous permet d'accéder très rapidement à vos bases de données existantes à partir de Cloudflare Workers, quel que soit leur lieu d'exécution. Il vous suffit de connecter Hyperdrive à votre base de données, de modifier une ligne de code pour vous connecter via Hyperdrive, et voilà : les connexions et les requêtes sont accélérées (et spoiler : vous pouvez l'utiliser dès aujourd'hui).
En un mot, Hyperdrive s'appuie sur notre réseau mondial pour accélérer les requêtes vers vos bases de données existantes, qu'elles se situent chez un fournisseur de cloud traditionnel ou chez votre fournisseur de base de données serverless préféré. La solution réduit considérablement la latence induite par l'établissement répété de nouvelles connexions avec la base de données. En outre, elle met en cache les requêtes de lecture les plus populaires adressées à votre base de données, une opération qui évite souvent d'avoir à s'adresser à nouveau à votre base de données.
Sans Hyperdrive, l'accès à votre base de données principale (celle qui contient les profils de vos utilisateurs, votre stock de produits ou qui exécute votre application web essentielle) hébergée dans la région us-east1 d'un fournisseur de cloud traditionnel se révèlera très lent pour les utilisateurs situés Continue reading
Race ahead with Cloudflare Pages build caching


Today, we are thrilled to release a beta of Cloudflare Pages support for build caching! With build caching, we are offering a supercharged Pages experience by helping you cache parts of your project to save time on subsequent builds.
For developers, time is not just money – it’s innovation and progress. When every second counts in crunch time before a new launch, the “need for speed” becomes critical. With Cloudflare Pages’ built-in continuous integration and continuous deployment (CI/CD), developers count on us to drive fast. We’ve already taken great strides in making sure we’re enabling quick development iterations for our users by making solid improvements on the stability and efficiency of our build infrastructure. But we always knew there was more to our build story.
Quick pit stops
Build times can feel like a developer's equivalent of a time-out, a forced pause in the creative process—the inevitable pit stop in a high-speed formula race.
Long build times not only breaks the flow of individual developers, but it can also create a ripple effect across the team. It can slow down iterations and push back deployments. In the fast-paced world of CI/CD, these delays can drastically impact productivity and the delivery Continue reading
Re-introducing the Cloudflare Workers Playground

Since the very initial announcement of Cloudflare Workers, we’ve provided a playground. The motivation behind that being a belief that users should have a convenient, low-commitment way to play around with and learn more about Workers.
Over the last few years, while Cloudflare Workers and our Developer Platform have changed and grown, the original playground has not. Today, we’re proud to announce a revamp of the playground that demonstrates the power of Workers, along with new development tooling, and the ability to share your playground code and deploy instantly to Cloudflare’s global network.
A focus on origin Workers
When Workers was first introduced, many of the examples and use-cases centered around middleware, where a Worker intercepts a request to an origin and does something before returning a response. This includes things like: modifying headers, redirecting traffic, helping with A/B testing, or caching. Ultimately the Worker isn’t acting as an origin in these cases, it sits between the user and the destination.
While Workers are still great for these types of tasks, for the updated playground, we decided to focus on the Worker-as-origin use-case. This is where the Worker receives a request and is responsible for returning the full response. In Continue reading
Running Serverless Puppeteer with Workers and Durable Objects

Last year, we announced the Browser Rendering API – letting users running Puppeteer, a browser automation library, directly in Workers. Puppeteer is one of the most popular libraries used to interact with a headless browser instance to accomplish tasks like taking screenshots, generating PDFs, crawling web pages, and testing web applications. We’ve heard from developers that configuring and maintaining their own serverless browser automation systems can be quite painful.
The Workers Browser Rendering API solves this. It makes the Puppeteer library available directly in your Worker, connected to a real web browser, without the need to configure and manage infrastructure or keep browser sessions warm yourself. You can use @cloudflare/puppeteer to run the full Puppeteer API directly on Workers!
We’ve seen so much interest from the developer community since launching last year. While the Browser Rendering API is still in beta (sign up to our waitlist to get access), we wanted to share a way to get more out of our current limits by using the Browser Rendering API with Durable Objects. We’ll also be sharing pricing for the Rendering API, so you can build knowing exactly what you’ll pay for.
Building a responsive web design testing tool with the Continue reading
A Socket API that works across JavaScript runtimes — announcing a WinterCG spec and Node.js implementation of connect()


Earlier this year, we announced a new API for creating outbound TCP sockets — connect(). From day one, we’ve been working with the Web-interoperable Runtimes Community Group (WinterCG) community to chart a course toward making this API a standard, available across all runtimes and platforms — including Node.js.
Today, we’re sharing that we’ve reached a new milestone in the path to making this API available across runtimes — engineers from Cloudflare and Vercel have published a draft specification of the connect() sockets API for review by the community, along with a Node.js compatible implementation of the connect() API that developers can start using today.
This implementation helps both application developers and maintainers of libraries and frameworks:
- Maintainers of existing libraries that use the node:net and node:tls APIs can use it to more easily add support for runtimes where node:net and node:tls are not available.
- JavaScript frameworks can use it to make connect() available in local development, making it easier for application developers to target runtimes that provide connect().
Why create a new standard? Why connect()?
As we described when we first announced connect(), to-date there has not been a standard API across JavaScript runtimes for creating and Continue reading
Cloudflare Integrations Marketplace introduces three new partners: Sentry, Momento and Turso
Building modern full-stack applications requires connecting to many hosted third party services, from observability platforms to databases and more. All too often, this means spending time doing busywork, managing credentials and writing glue code just to get started. This is why we’re building out the Cloudflare Integrations Marketplace to allow developers to easily discover, configure and deploy products to use with Workers.
Earlier this year, we introduced integrations with Supabase, PlanetScale, Neon and Upstash. Today, we are thrilled to introduce our newest additions to Cloudflare’s Integrations Marketplace – Sentry, Turso and Momento.
Let's take a closer look at some of the exciting integration providers that are now part of the Workers Integration Marketplace.
Improve performance and reliability by connecting Workers to Sentry
When your Worker encounters an error you want to know what happened and exactly what line of code triggered it. Sentry is an application monitoring platform that helps developers identify and resolve issues in real-time.
The Workers and Sentry integration automatically sends errors, exceptions and console.log() messages from your Worker to Sentry with no code changes required. Here’s how it works:
- You enable the integration from the Cloudflare Dashboard.
- The credentials from the Sentry project of Continue reading
Cloudflare is now powering Microsoft Edge Secure Network


Between third-party cookies that track your activity across websites, to highly targeted advertising based on your IP address and browsing data, it's no secret that today’s Internet browsing experience isn’t as private as it should be. Here at Cloudflare, we believe everyone should be able to browse the Internet free of persistent tracking and prying eyes.
That’s why we’re excited to announce that we’ve partnered with Microsoft Edge to provide a fast and secure VPN, right in the browser. Users don’t have to install anything new or understand complex concepts to get the latest in network-level privacy: Edge Secure Network VPN is available on the latest consumer version of Microsoft Edge in most markets, and automatically comes with 5 GB of data. Just enable the feature by going to [Microsoft Edge Settings & more (…) > Browser essentials, and click Get VPN for free]. See Microsoft’s Edge Secure Network page for more details.
Cloudflare’s Privacy Proxy platform isn’t your typical VPN
To take a step back: a VPN is a way in which the Internet traffic leaving your device is tunneled through an intermediary server operated by a provider – in this case, Cloudflare! There are many important pieces that Continue reading