Setting Up Addressing and Routing: FTDv Fun
In my previous blog (Fun in the Lab: FTDv & FMC – Install and Deploy) we deployed a FMC VM and a FTDv VM and ended the blog with the FTDv successfully added to the FMC.
Now? Now let’s add IP addressing for the FTDv and also set up routing protocol neighbor relationships. I learned what I am about to show you from my co-worker and friend, Keith Brister. So don’t thank me, thank Keith. 
I tossed together a ~29 minute YouTube. Obviously you can watch the entire thing. Or… here you go for the big sections.
- Overview – Start to 2:17 minutes
- Physical/Logical Mapping Overview – 2:18 to 9:25
- vSwitches, vmNICs and More in VMware – 9:26 to 16:20
- FTDv Configuring IP Adresses via FMC – 16:21 to 23:18
- FTDv Configuring IP Routing via FMC – 23:19 to 29:29
Done and Done. Easy Peasy!
Fun in the Lab: FTDv & FMC – Install and Deploy
This is my Stealthwatch playground…. errrr… I mean … ahem… “work environment” for a Technical Solution Workshop I am working on for Stealthwatch.
Going to set up FTDv and FMC today. A co-worker and friend, Scott Barasch, helped me get jump started… so figure I’ll pass on what I just learned to you. 
What this blog will cover is
- DEPLOY
- Deploying the OVF for FTDv
- Deploying the OVF for FMC
- VMware settings
- Tweak for FTDv
- Tweak for FMC
- Prepping to Power On
- Snapshot Both Before Power On
- Power Both On
- Setup via Console
- FMC – console in and setup IP address
- FTDv – console in and step thru the prompts
- Test IP Connectivity
- Ping FMC and FTDv from the PC
- Notice Can’t ping FTDv
- Fix
- Ping
- Browse into FMC
- Change password
- Setup DNS
- Setup NTP
- Accept EULA
- Apply
- LICENSING
- License FMC
- FMC/FTDv: Make the Connection
- FTDv – Point FTDv to FMC
- FMC – bring the FTDv into the fold.

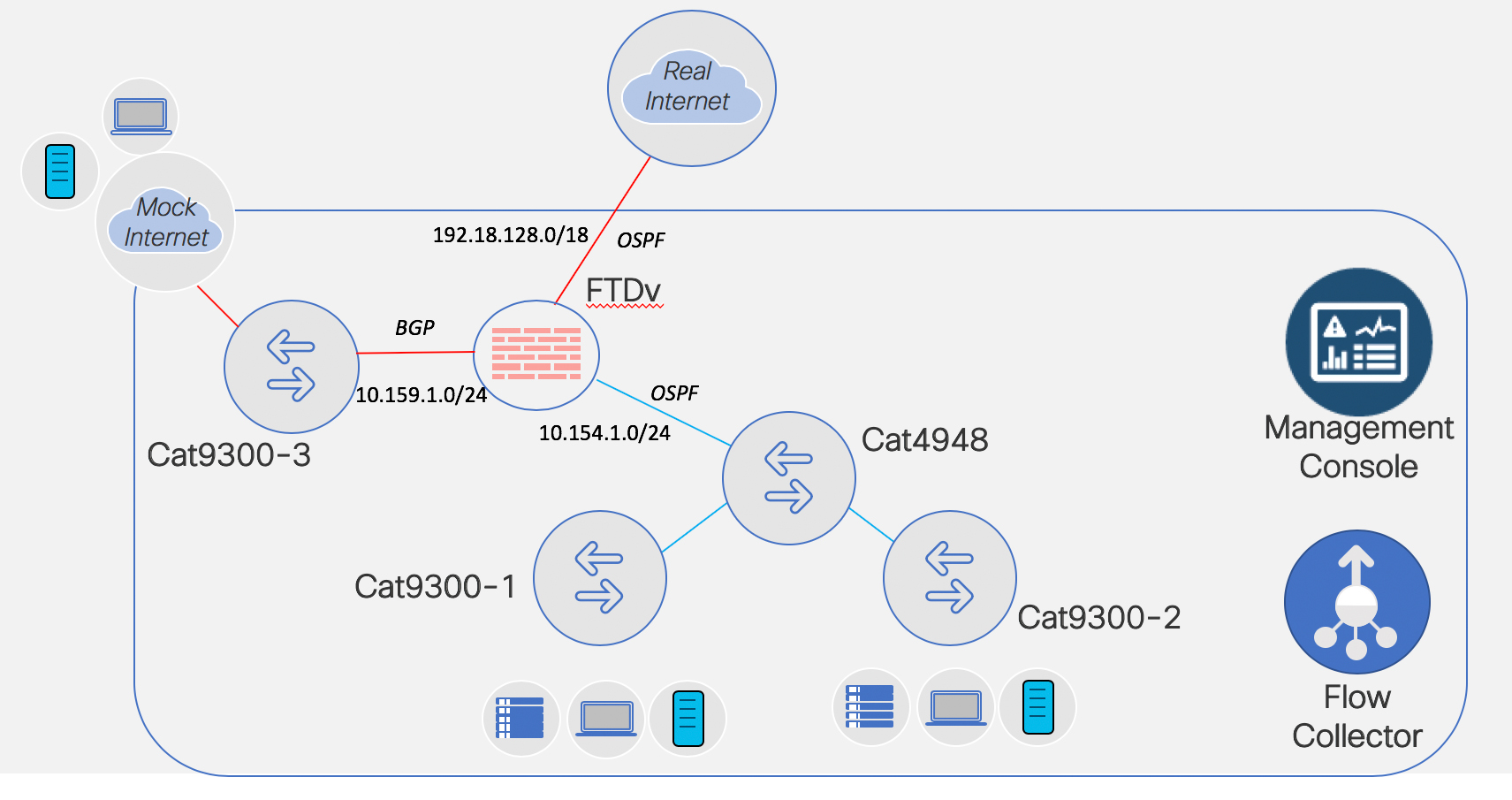
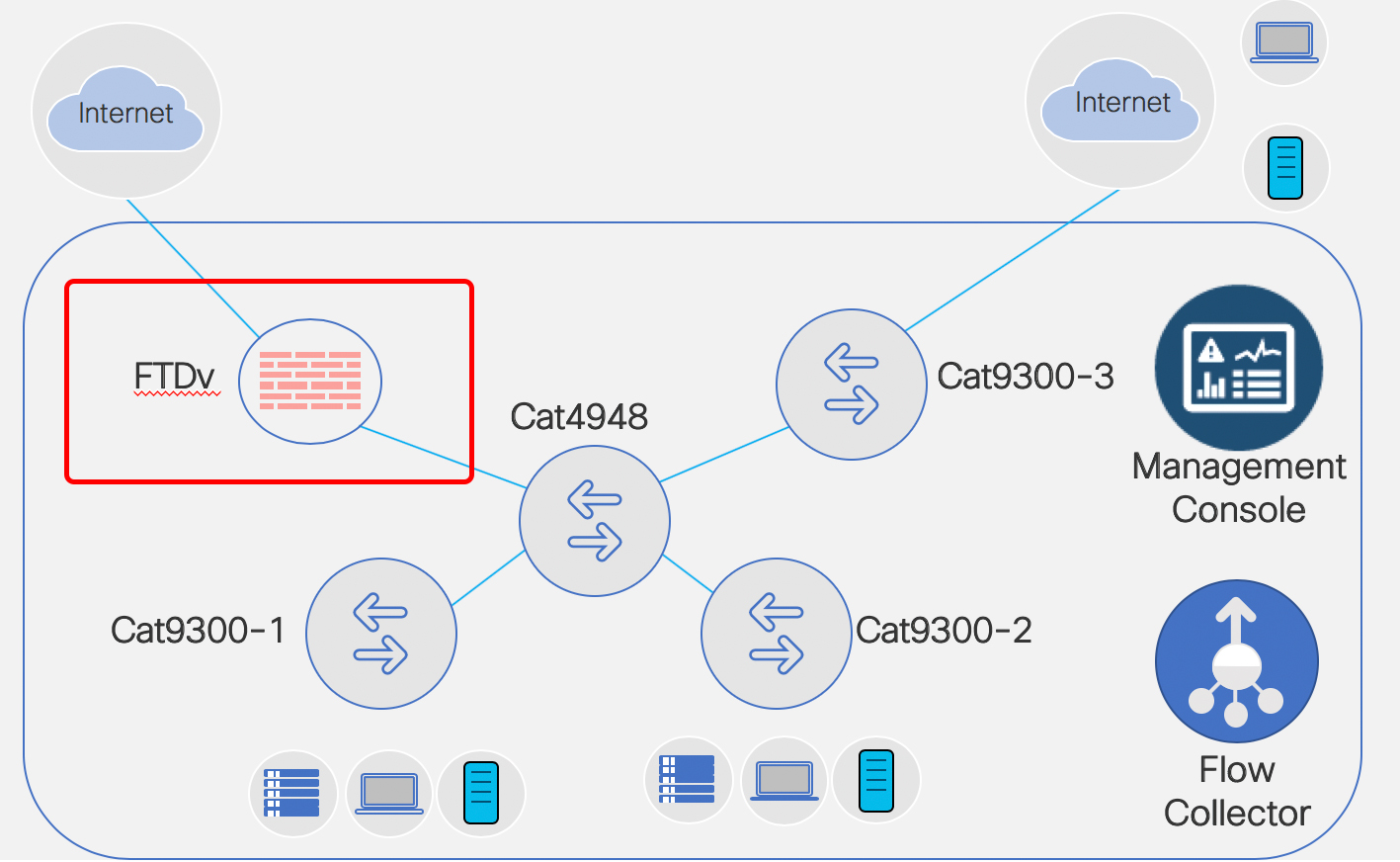
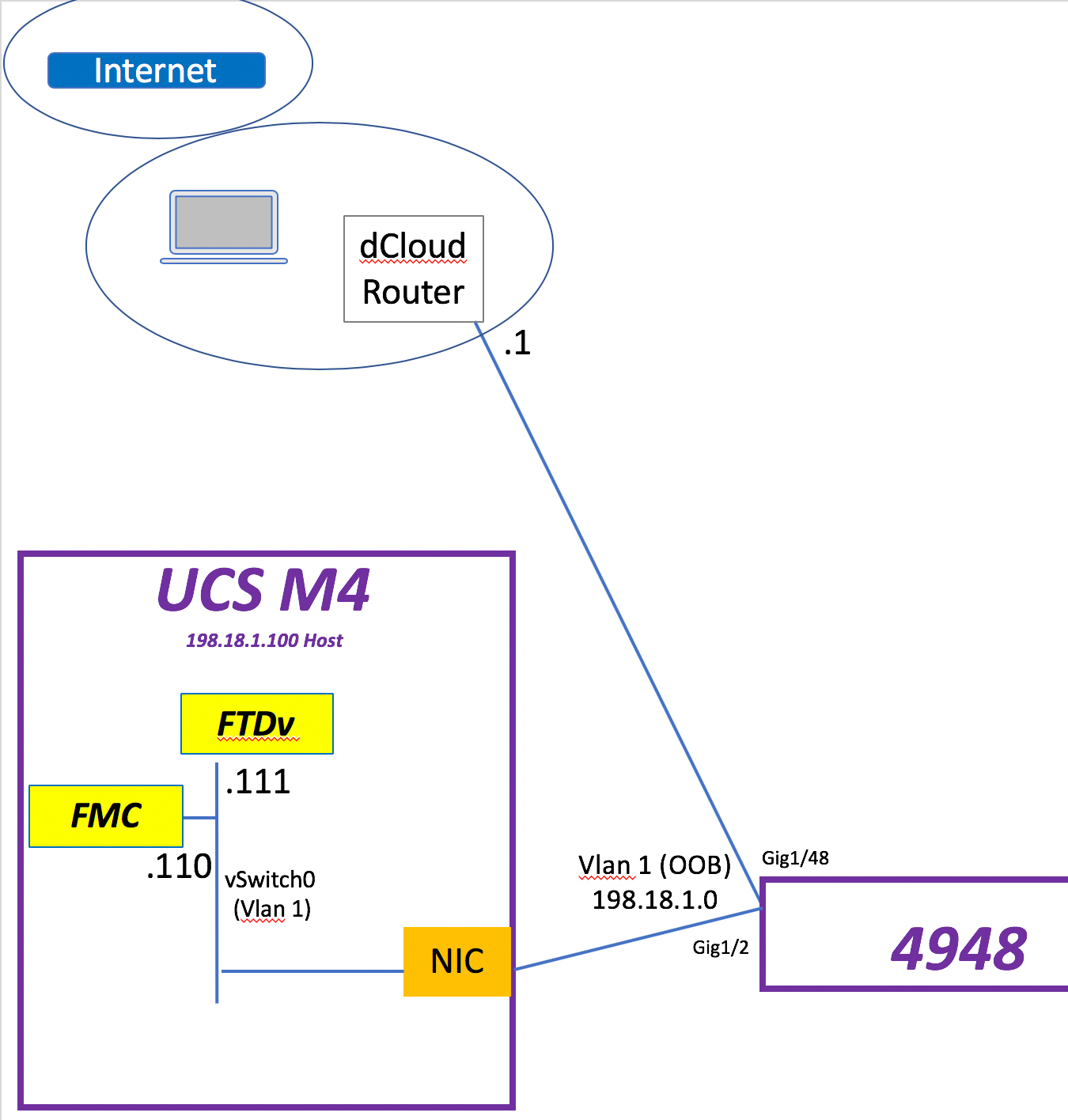
So let’s begin. What I have to host my FMC & FTDv VMs is a UCS M4 with a NIC connected to a Cat4948 in vlan 1. That NIC is tied to vSwitch0 in the UCS. Continue reading
Hello There! :) Update from the FishBowl
June 28th… wow…. lol… my last blog out here was June 28th! Too funny! So where have I been and what have I been doing?
Well June was CiscoLive in the beginning and then SharkFest at the end. I think i hit some “being social” limit and became a hermit for most of July and August. Then 2 weeks of vacation for the first 2 weeks of September. Two full weeks. It was AWESOME! Then Florence came to visit…  She hung around for a little while. Like one of those visitors who come stay with you at your house and just won’t leave. Oh.. and then breaking a finger September 15th and struggling to type for the rest of the month.
She hung around for a little while. Like one of those visitors who come stay with you at your house and just won’t leave. Oh.. and then breaking a finger September 15th and struggling to type for the rest of the month.
Hello! I’m BACK!
And I have REALLY missed being here! At the same time… that break was REALLY needed!  Awesome summer with the wife and family! Woot woot! Work hard… play hard!
Awesome summer with the wife and family! Woot woot! Work hard… play hard!
So what am I up to? Stealthwatch Baby! Woot woot! Been with Cisco for 22 years and I have NEVER loved a product and a GUI so Continue reading
Techniques of a Network Detective: A New Series
Put your detective hat on your head and your Network Detective badge on your lapel. Introducing a new blog series – Techniques of a Network Detective. This series will focus on the detective work (troubleshooting side) of our jobs as network engineers.
For over 30 years I’ve been playing in the “world of IT”. During those years there have been a lot of changes in our world. But through all that change, there has been a thread, for me, that has always remained constant. A thread and a passion that always seemed to be with me in every job over all these years.
Troubleshooting!
Being a “Network Detective” is much the same as being a regular detective in many ways. As a Network Detective we get put on a “case” – the “Case of the Missing Packets” maybe. We go to the crime scene and try to find answers so we can solve the “who done it”
When a “crime” happens you need to be right there interviewing the suspects, surveying the crime scene, asking the right questions. Trying to quickly figure out what is happening, where it is happening, and why it Continue reading
SharkFest 2018!! Woot woot! So Excited!
On Saturday I leave North Carolina to head to Sunnyvale, California for…… (insert drumroll here)… SharkFest! I’m am so pumped and excited! I have wanted to attend SharkFest since 2009 when I first learned about it! I’m finally going! Woot woot!
It is not uncommon that I find myself having to explain what SharkFest is… even to diehard WireShark users and enthusiasts. So let me take a step back and explain what SharkFest is.
What is SharkFest?
SharkFest
, launched in 2008, is a series of annual educational conferences staged in various parts of the globe and focused on sharing knowledge, experience and best practices among the Wireshark® developer and user communities.
SharkFest attendees hone their skills in the art of packet analysis by attending lecture and lab-based sessions delivered by the most seasoned experts in the industry. Wireshark core code contributors also gather during the conference days to enrich and evolve the tool to maintain its relevance in ensuring the productivity of modern networks.
https://sharkfestus.wireshark.org/about
Teehee. So basically it is a major WireShark geek fest!!!! And I am STOKED! Who wouldn’t be? Just look at the classes I’ve Continue reading
Network Detective Ride-Along: Troubleshooting Multicast
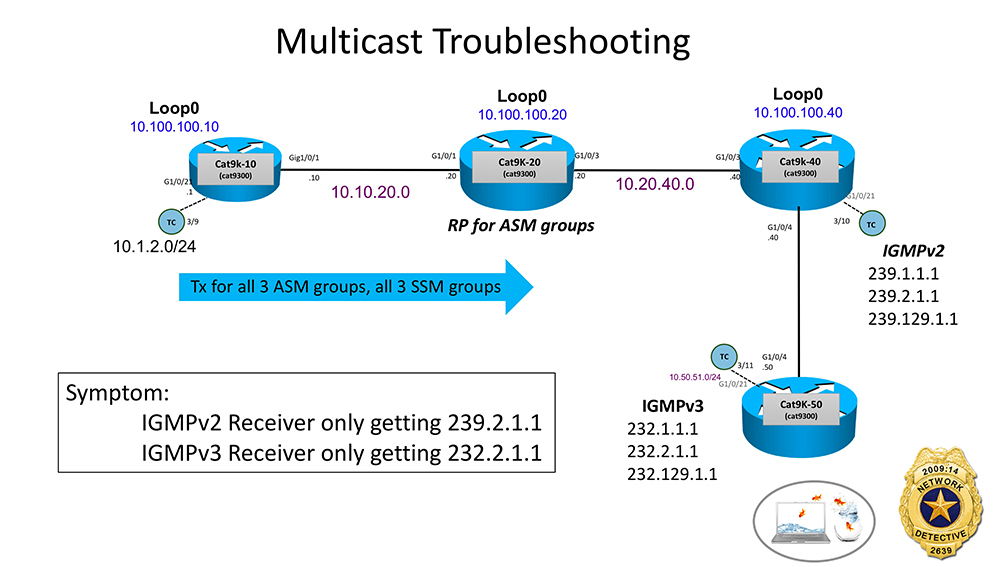
Grab your Network Detective badge! It’s time for another Network Detective ride-along.  Multicast this time.
Multicast this time.
We need to solve the case of the missing Multicast streams. ONLY 2 multicast streams (232.2.1.1 and 239.2.1.1) are getting thru to the hosts who requested them. The other 4 streams the same hosts requested are NOT getting thru. Let’s go to the crime scene and review the facts.
Fact #1 – Host off of Cat9K-40 is sending IGMPv2 membership reports to join ASM groups 239.1.1.1, 239.2.1.1 and 239.129.1.1
Fact #2 – Host off of Cat9K-50 is sending IGMPv3 membership reports to join SSM groups 232.1.1.1, 232.2.1.1 and 232.129.1.1
Fact #3 – All multicast sources are off of Cat9k-10 in subnet 10.1.2.0/24. They are sending the mcast for all 3 SSM groups and all 3 ASM groups
Fact #4 – Cat9K-20 is the Rendezvous Point (RP) for all 3 ASM groups
Any thoughts at first glance? Time to go to the YouTube ride-along ~11 minute video! Good luck! Have fun!
Networking With Fish: YouTube Channel
Blogging, originally, was my go to and preferred method for sharing information to others – teaching, sharing, etc. For a few corner case type things I found video (YouTube) to be a better tool for those specific items. Recently, however, I am finding about half of my ideas of things I want to “pass on” to others… would be best (in my opinion) via video.
I’ve been trying to figure out and think about how best to have the two sharing tools – this blog site and the YouTube channel – best compliment each other. So I have been experimenting with this. What I have come up with that I like and works for me is the following…..
- “Standalone Video” – If the YouTube is really a “standalone” and blogging with additional text around it here doesn’t “help” communicate what I’m trying to get across… then I won’t be blogging about it here.
- “Video Series” – There will be series that will be building on each other – like the videos in the playlist “BGP Show and Tell: Beginners” and the playlist “Label Swapping Fun”. Video series, I believe, would definitely benefit from larger big Continue reading
CiscoLive 2018: ‘Summer Camp for Geeks’
Are you ready for CiscoLive US 2018? Ready for Summer Camp for Geeks?! I think it is hard to truly be completely ready for the experience nowadays. Why? Because CiscoLive US is just huge with so many options of things to experience as an attendee…. more options than you have time for. If you have been to CiscoLive US before… you KNOW this is true. And every year more and more …. and more and more … get added. For 2018 my favorite CiscoLive add is the new ‘Content Cafe’ session type (30 minutes). Other favorites of mine are the ‘Flip Sessions’ and the “Beers with Engineers”. ?
Deciding where to spend your time and energy during #CLUS can be overwhelming and daunting.
What is my absolute #1 suggestion to anyone going to a CiscoLive event? Easy – “Begin with the End in Mind“. Know what your priorities are and then schedule your week accordingly.
STEP #1: Create Your Cisco Live 2018 Priority List
Take your goals and translate them into a priority list.
STEP #2: Learn from the Past
If you have been to CiscoLive before… Continue reading
Resumes: “Begin with the End in Mind” – Musings from the FishBowl
I feel like I should go to some “Resume PTSD” meetings.. are there such things? LOL. I can imagine a dark room like they have in the movies for 12 step meetings. Some podium up in the front where everyone has to tell their story. The lead nods to me that it is my turn and I go up to the podium….
“Hello, my name is Fish, and I have Resume PTSD. It all started for me one evening when I was 16 years old. I remember was in the family room of our house in Princeton, New Jersey… it was deep winter out so we had the fire in the fireplace going. Dad walked across the room to sit by the fire… he put before him 2 stacks of resumes – one stack for people applying to be a Vice President and another stack for people applying to be a Lobby Ambassador and Admin. I watched in appropriate 16 year old horror as he glanced at each piece of paper and within 5-10 seconds he decided if it went in the pile for definitely interview, or the pile for review resume again Continue reading
Woot Woot! 16 Weeks of Security Learning!! — SECURITY ZERO-TO-HERO
Just signed up last week for the Micronic’s “Security Zero-to-Hero” class. I am beyond stoked and excited! I have been searching for awhile now for a class to take to help me really “go to the next level” in Security. But I just wasn’t finding the kind of class I was looking for. Every class I saw offered was either focused on one narrow aspect of the security landscape OR focused on helping people pass the CCIE Security. Neither or which matched what I was searching for.
The class I was hoping to find would be structured more like a semester long college class with real world production discussions and also hands on labs. A class where … over weeks of learning and labbing in my personal time… the learning would just continue to seep deeper and deeper and the “aha” moments would just keep coming. There were lots of one week classes to choose from. But, for me, I just don’t see a one week class as a great “immersive” experience into the complex landscape of the world of Security. There is a “learning limit”, for me, as to how much my brain can retain Continue reading
Casting Call: Angling for Good Tech and Good Conversation – Coming to YouTube SOON!
The idea started forming in my head 3 years ago at CiscoLive Europe 2018 in Barcelona. I was asked to be a roving reporter for the event. I had never done anything like that before…. so to say I was... Read More ›
The post Casting Call: Angling for Good Tech and Good Conversation – Coming to YouTube SOON! appeared first on Networking with FISH.
The “Case of the Broken MPLS L3VPN” – Time to Troubleshoot!
In the last blog – “MPLS L3VPN: Label Following Fun with Fish” and its corresponding YouTube show and tell we basically set the stage for this blog and YouTube. ? Last we left our environment, we saw a successful ping... Read More ›
The post The “Case of the Broken MPLS L3VPN” – Time to Troubleshoot! appeared first on Networking with FISH.
MPLS L3VPN: Label Following Fun with Fish
I have to admit I LOVE MPLS. I admit, I didn’t love it so much when I was first learning. I found it kinda hard at first. But then I absolutely loved it once I “saw” it. Newer to MPLS... Read More ›
The post MPLS L3VPN: Label Following Fun with Fish appeared first on Networking with FISH.
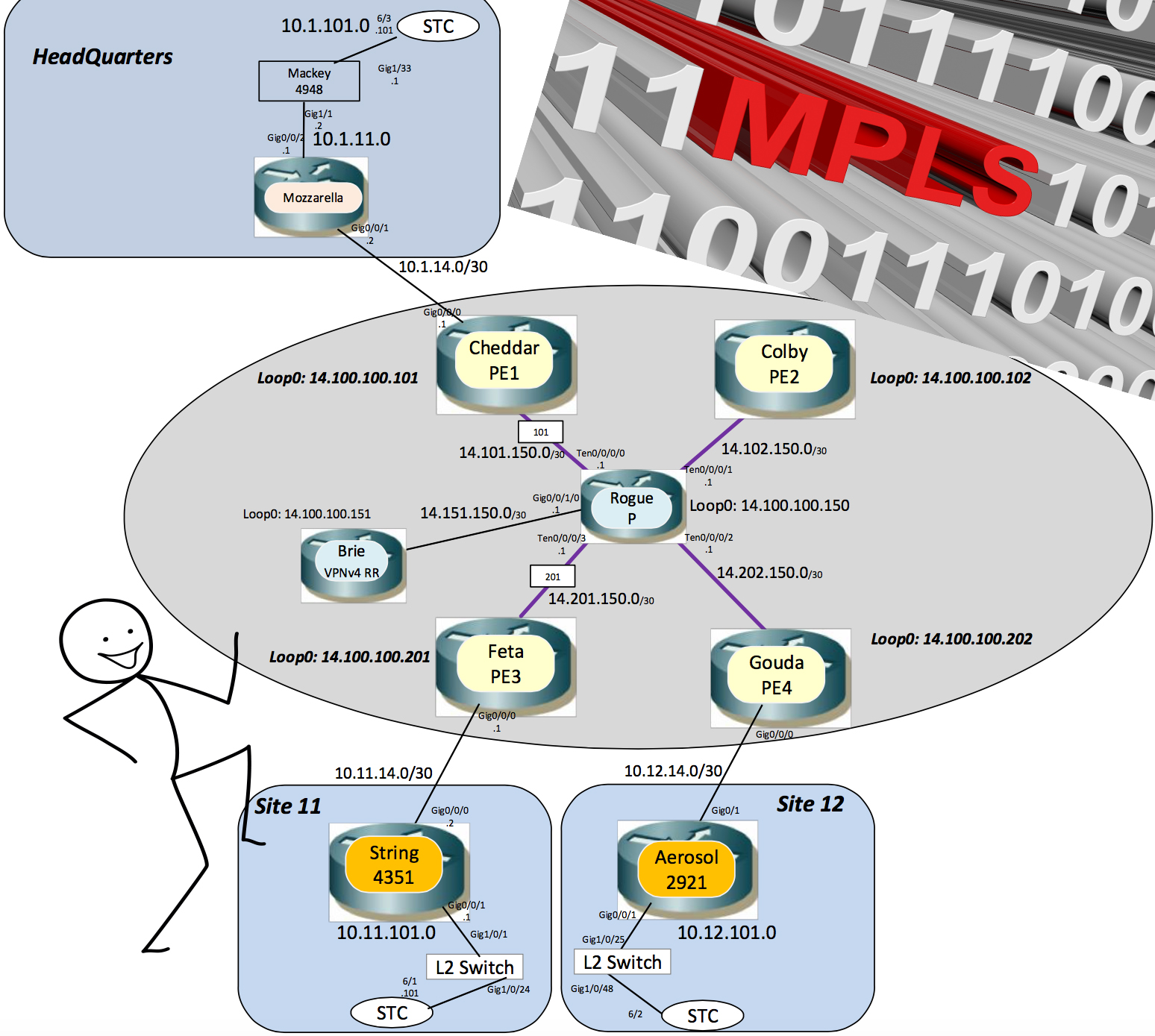
MPLS, L3VPN, Multicast, and mVPN Fun in the Lab: Building a MPLS L3VPN Unicast and Multicast Cloud (6 Part Blog Series)
I needed to build a MPLS cloud for something. Thought I’d invite you along for the fun in the lab. Party on!**
Ultimately what I want to do is have a multicast source up in the upper left in Headquarters and multicast receivers down in Site11 and Site 12 joining those groups.
For this blog series that will mean 6 blogs, plus zip files of the varying configs as we build them, plus sniffer traces for you to download and refer to.
MPLS Fun in the Lab: Building the MPLS Cloud – Part 1 of 6
Create the MPLS cloud and prep it for MPLS L3VPN Unicast for One L3VPN Customer
- OSPF area 0
- MPLS LDP neighbors between the PEs and the P
- BGP VPNv4 peers from all PEs to the VPNv4 Route Reflector
MPLS Fun in the Lab: Connect a Customer – Part 2 of 6
- Create a VRF in each PE.
- Apply the VRF and IP addresses on the interfaces in each PE towards the CEs.
- Create the BGP neighbors in the PEs towards the CEs.
- Ping from HQ to Site 11
- Look at the sniffer trace of the above Ping
MPLS Fun in the Continue reading
Understanding IPv6 – The 7 Part Blog Series and the 28 minute CHI-NOG Snippet
New to IPv6 or know someone who is? Below you will find my 7 part blog series of my lessons learned during my IPv6 journey and how I now teach IPv6 to others newer to it. Prefer a YouTube instead? At the end you will find the very rapid paced .. 28 minute… presentation I did of this for CHI-NOG in 2016.
 Understanding IPv6: The Journey Begins (Part 1 of 7)
Understanding IPv6: The Journey Begins (Part 1 of 7)
 Understanding IPv6: Link-Local ‘Magic’ (Part 2 of 7)
Understanding IPv6: Link-Local ‘Magic’ (Part 2 of 7)
 Understanding IPv6: A Sniffer Full Of 3s (Part 3 of 7)
Understanding IPv6: A Sniffer Full Of 3s (Part 3 of 7)
 Understanding IPv6: What Is Solicited-Node Multicast? (Part 4 of 7)
Understanding IPv6: What Is Solicited-Node Multicast? (Part 4 of 7)
 Understanding IPv6: Prepping For Solicited-Node Multicast (Part 5 of 7)
Understanding IPv6: Prepping For Solicited-Node Multicast (Part 5 of 7)
 Understanding IPv6: The Ping Before Solicited-Node Multicast (Part 6 of 7)
Understanding IPv6: The Ping Before Solicited-Node Multicast (Part 6 of 7)
 Understanding IPv6: Solicited-Node Multicast In Action (Part 7 of 7)
Understanding IPv6: Solicited-Node Multicast In Action (Part 7 of 7)
Understanding IPv6: Solicited-Node Multicast In Action (Part 7 of 7)
The last few blogs in my series on IPv6 have focused on solicited-node multicast, which provides the functionality for Neighbor Discovery in IPv6 addressing. We ended the last blog with a cliffhanger, asking, “In IPv6, how do we find the Layer 2 MAC address associated with a Layer 3 IPv6 address?”
Time to put the pieces together
In this series of blogs, I have laid out all the varying puzzle pieces needed to answer this question. Let’s start putting those puzzle pieces together.
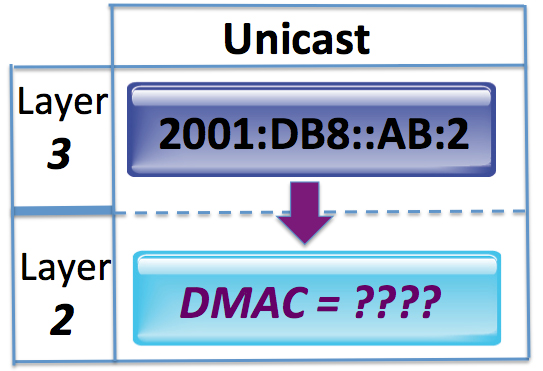
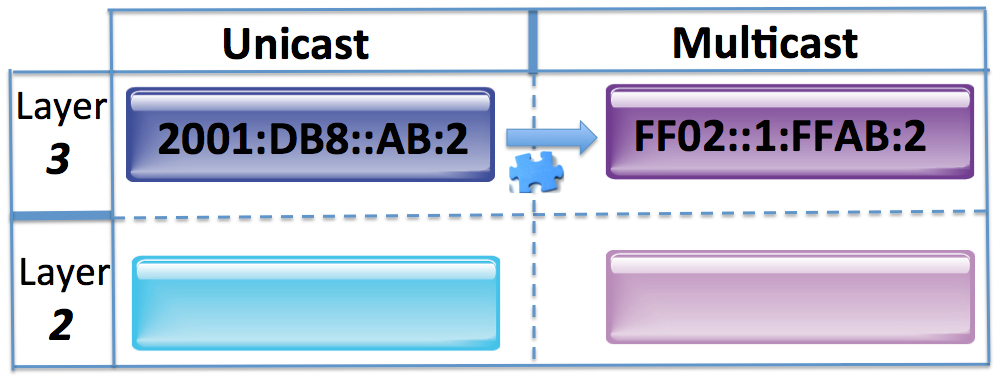
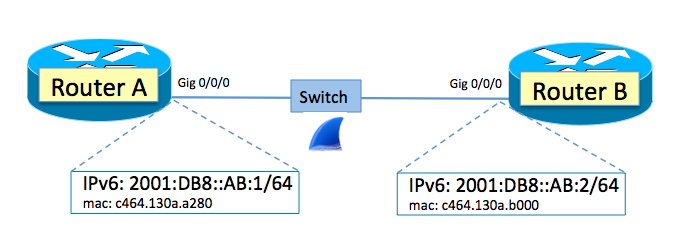
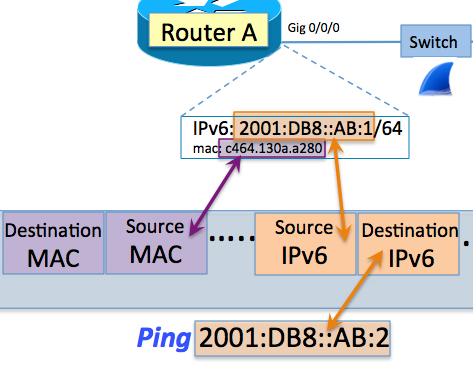
In this blog, we learned that, if a device has an IPv6 global address of 2001:DB8::AB:1/64, then, according to RFC 4291, it must also “compute and join” the IPv6 solicited-node multicast address FF02::1:FFAB:1.
By the same logic, that means the node associated with the IPv6 address of 2001:DB8::AB:2 must “compute and join” the IPv6 solicited-node multicast address FF02::1:FFAB:2.
So our first puzzle piece gets us to here:
But so what? How does that get us any closer to getting the DMAC associated with Router B’s IPv6 global unicast address? All it did was give us a multicast address that this IPv6 unicast address must join.
Let’s add another piece of the puzzle. From this Continue reading
Understanding IPv6: The Ping Before Solicited-Node Multicast (Part 6 of 7)
In a previous blog, we looked at the basics of IPv6 solicited-node multicast. Going back to our Router A and Router B environment, if we sniff the wire while pinging from Router A’s IPv6 address to Router B’s IPv6 address, what will we see? Spoilers! Suffice it to say we will see some IPv6 solicited-node multicast very much in action.
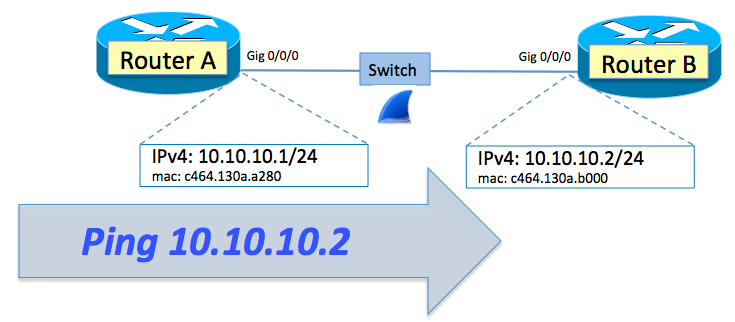
Ping in IPv4
Before we jump into IPv6, let’s first do an IPv4 ping from Router A to Router B. When we sniff the wire we can review the mechanisms of how IPv4 does all of this on the wire.
When ping 10.10.10.2 is entered on Router A, the router knows it is being asked to build an ICMP echo request message and put it “out on the wire” with a destination IP address of 10.10.10.2. But in order to make the request “ready” to put out on the wire to get to 10.10.10.2, Router A needs more than simply the destination IPv4 address.
For the purposes of this post, we will look at four things the router needs before sending the ICMP echo request out on the wire. These Continue reading
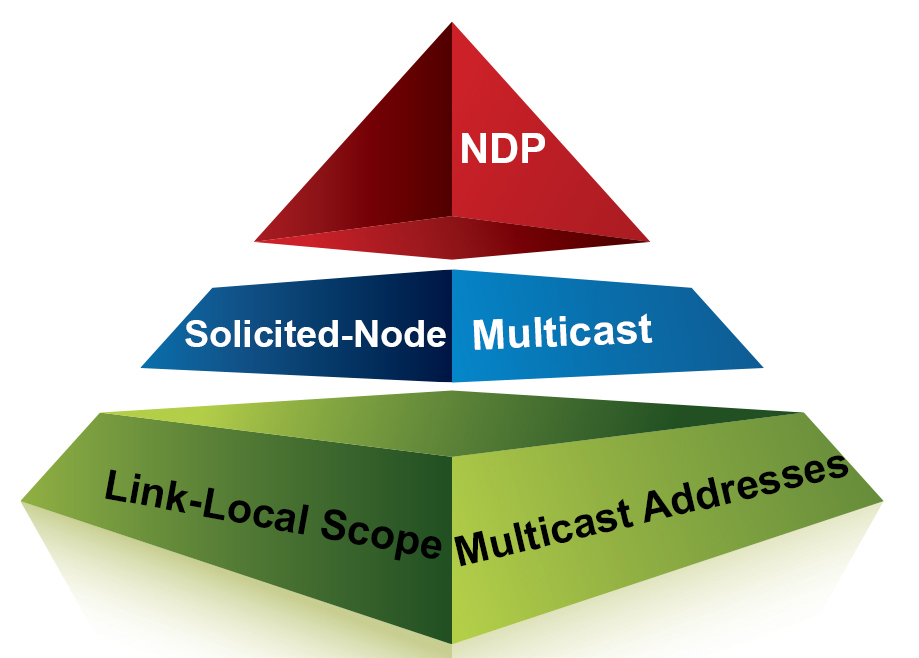
Understanding IPv6: Prepping For Solicited-Node Multicast (Part 5 of 7)
Solicited-node multicast: I stumbled and tripped a bunch over this one in the beginning. Well, that isn’t 100% true. Admittedly, at first, I really just ignored it, which really got in the way of my understanding some of the fundamentals of Neighbor Discovery Protocol (NDP).
But before we jump into solicited-node multicast, let’s review link-local scope multicast addresses.
Multicast is all around you
Multicast is all around your current IPv4 network. You might not think so if you haven’t enabled IP multicast routing and PIM, but it’s there. Pretty much everywhere you turn, it’s there.
Let’s return to our RouterA/RouterB environment. But let’s have IPv4 only running right now, like probably a lot of your routers in your environment.
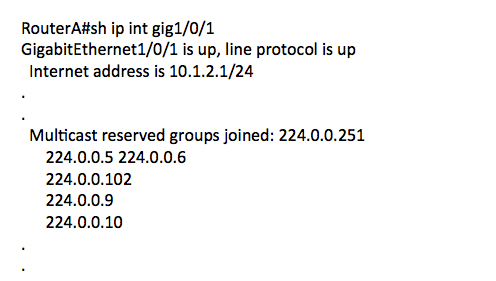
Show IP interface
This is often an overlooked command, which is a shame because there is a great deal of very useful information that is given in the output. For now, we’re going to focus on the line “multicast reserved groups joined” and ignore all the other lines.
See? Lots and lots of multicast! To be specific, lots of “Local Network Control Block (224.0.0.0 – 224.0.0.255 (224.0.0/24),” according to the Internet Continue reading
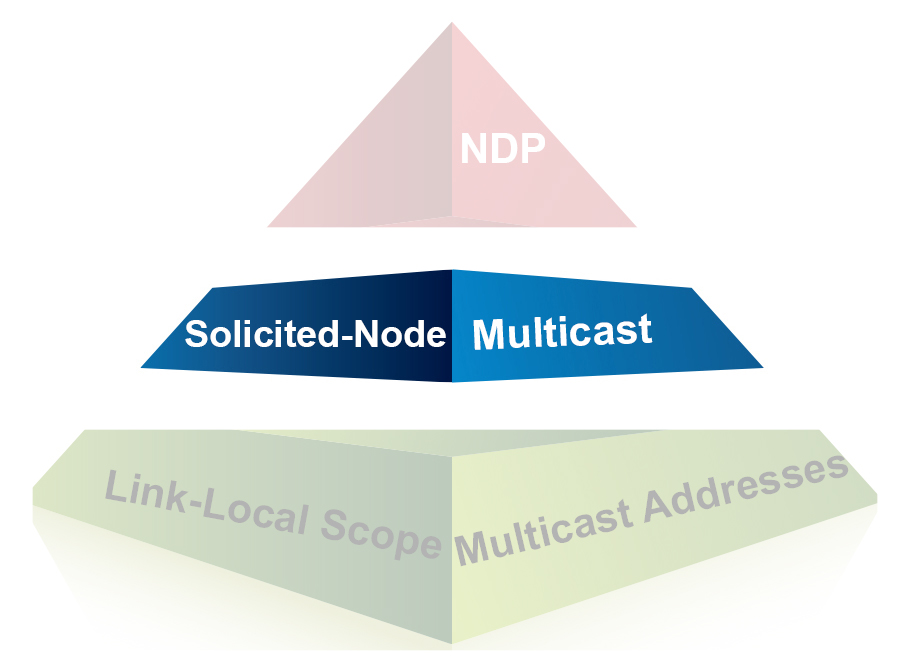
Understanding IPv6: What Is Solicited-Node Multicast? (Part 4 of 7)
IPv6 solicited-node multicast somtimes seems to confuse those new to IPv6 in the beginning. I think this is because it seems so foreign and new. In this post, we will explore exactly what IPv6’s solicited-node multicast is and the rules of creating such an address as told to us by RFC 4291.
However, before we start on what’s new and different, let’s look at what solicited-node multicast has in common with IPv4 and IPv6 constructs that we already know.
In this blog post, we looked at IPv6 link-local scope multicast addresses. One of the examples was FF02::A. This address is for all devices on a wire that want to “talk” EIGRP with one another.
Focusing specifically on FF02::A and how routers join it, we can see and say three things:
- Local: FF02::A is local to the wire.
- Join: Each device “joins” FF02::A by just “deciding to listen” to the IPv6 link-local scope multicast address FF02::A. Then, by extension, it listens to the corresponding MAC address for that multicast IPv6 address (33:33:00:00:00:0A).
- Common interest: As we can see, these varying groups have something in common that they would all like to hear about. For FF02::A, the common interest — the “connection” Continue reading
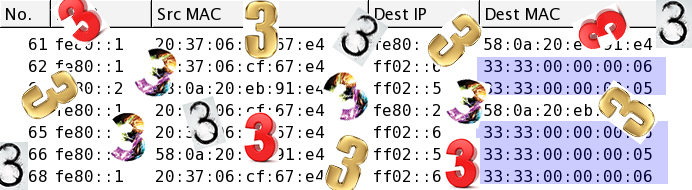
Understanding IPv6: A Sniffer Full Of 3s (Part 3 of 7)
“What the heck?” Yup, that pretty much summed up my confusion the first time I saw it. A sniffer trace full of threes.
The first thing it reminded me of was my days with Token Ring and locally administered addresses (LAAs). This was for two reasons:
- I could only see these MAC addresses being used as destination MACs, not as source MACs. This was the same with my experience with LAAs in token ring
- The MAC addresses seemed so pretty and clean, like the Token Ring LAA typically used for a 3745 IBM front-end process — 4000.3745.0001. Just look at them. Four threes, followed by a bunch of zeros, and then just one little number.
Help from Wireshark
I hope you are familiar with Wireshark; I use it all the time. It shows “reality” on the wire, which is crucial if you are a network detective trying to solve a whodunit.
If you are familiar with Wireshark then you might know that I can configure how the MAC addresses are displayed in the columns via the Wireshark preferences. As you can see below, I have set the preferences to not resolve the MAC addresses for me, Continue reading