The Serverlist Newsletter 2nd Edition: Available Now

Check out our second edition of The Serverlist below. Get the latest scoop on the serverless space, get your hands dirty with new developer tutorials, engage in conversations with other serverless developers, and find upcoming meetups and conferences to attend.
Sign up below to have The Serverlist sent directly to your mailbox.
Unpacking the Stack and Addressing Complaints about Content


Although we are focused on protecting and optimizing the operation of the Internet, Cloudflare is sometimes the target of complaints or criticism about the content of a very small percentage of the more than thirteen million websites that use our service. Our termination of services to the Daily Stormer website a year and a half ago drew significant attention to our approach to these issues and prompted a lot of thinking on our part.
At the time, Matthew wrote that calls for service providers to reject some online content should start with a consideration of how the Internet works and how the services at issue up and down the stack interact with that content. He tasked Cloudflare’s policy team with engaging broadly to try and find an answer. With some time having passed, we want to take stock of what we’ve learned and where we stand in addressing problematic content online.
The aftermath of the Daily Stormer decision
The weeks immediately following the decision in August 2017 were filled with conversations. Matthew made sure the Cloudflare team accepted every single invitation to talk about these issues; we didn’t simply put out a press release or “no comment” anyone. Continue reading
Cloudflare Signs European Commission Declaration on Gender Balanced Company Culture

Last week Cloudflare attended a roundtable meeting in Brussels convened by the European Commissioner for Digital Economy and Society, Mariya Gabriel, with all signatories of the Tech Leaders’ Declaration on Gender Balanced Company Culture. Cloudflare joined this European Commission initiative late last year and, along with other companies, we are committed to taking a hands-on approach to close the digital gender divide in skills, inception of technologies, access and career opportunities.
In particular, we have all committed to implementing, promoting and spreading five specific actions to achieve equality of opportunities for women in our companies and in the digital sector at large:
- Instil an inclusive, open, female-friendly company culture
- Recruit and invest in diversity
- Give women in tech their voice and visibility
- Create the leaders of the future
- Become an advocate for change
The project, spearheaded by the Digital Commissioner as part of a range of actions to promote gender balance in the digital industry, allows for the exchange of ideas and best practices among companies, with opportunities to chart progress and also to discuss the challenges we face. Many companies around the table shared their inspiring stories of steps taken at company level to encourage diversity, push back against Continue reading
Logpush: the Easy Way to Get Your Logs to Your Cloud Storage
Introducing Logpush

Today, we’re excited to announce a new way to get your logs: Logpush, a tool for uploading your logs to your cloud storage provider, such as Amazon S3 or Google Cloud Storage. It’s now available in Early Access for Enterprise domains.
We first explained Cloudflare’s logging functionality almost six years ago. Since then, the number of domains on our network has grown by ten times. We’ve continued giving our Enterprise customers the ability to download logs using a REST API, which has gotten a large number of functional and technical updates. We’ve also been paying attention to how our customers’ needs have evolved, especially as we protect and accelerate increasingly larger domains. This led to the development of Logpush.
The Value of Logs
Cloudflare works by being an intermediary between our customers’ websites, applications, and devices, and their end-users or potential attackers. As part of providing our service, we create a record of each request that goes through our network. These records (or request logs) have detailed information regarding the connecting client, our actions—including whether the request was served by the cache or blocked by our firewall—and the response from the origin web server. For Enterprise customers Continue reading
Cloudflare Transparency Update: Joining Cloudflare’s Flock of (Warrant) Canaries


Today, Cloudflare is releasing its transparency report for the second half of 2018. We have been publishing biannual Transparency Reports since 2013.
We believe an essential part of earning the trust of our customers is being transparent about our features and services, what we do – and do not do – with our users’ data, and generally how we conduct ourselves in our engagement with third parties such as law enforcement authorities. We also think that an important part of being fully transparent is being rigorously consistent and anticipating future circumstances, so our users not only know how we have behaved in the past, but are able to anticipate with reasonable certainty how we will act in the future, even in difficult cases.
As part of that effort, we have set forth certain ‘warrant canaries’ – statements of things we have never done as a company. As described in greater detail below, the report published today adds three new ‘warrant canaries’, which is the first time we’ve added to that list since 2013. The transparency report is also distinguished because it adds new reporting on requests for user information from foreign law enforcement, and requests for user information that we Continue reading
Cloudflare’s RPKI Toolkit

A few months ago, we made a first then a second announcement about Cloudflare’s involvement in Resource Public Key Infrastructure (RPKI), and our desire to make BGP Internet routing more secure. Our mission is to build a safer Internet. We want to make it easier for network operators to deploy RPKI.
Today’s article is going to cover our experience and the tools we are using. As a brief reminder, RPKI is a framework that allows networks to deploy route filtering using cryptography-validated information. Picture TLS certificates for IP addresses and Autonomous System Numbers (ASNs)
What it means for you:
We validate our IP routes. This means, as a 1.1.1.1 DNS resolver user, you are less likely to be victim of cache poisoning. We signed our IP routes. This means a user browsing the websites on Cloudflare’s network are unlikely to experience route hijacks.
All our Points of Presence which have a router compatible with The Resource Public Key Infrastructure (RPKI) to Router Protocol (RTR protocol) are connected to our custom software called GoRTR and are now filtering invalid routes. The deployment amounts to around 70% of our network.
We received many questions regarding the amount of invalid Continue reading
My Cloudflaraversery: Things I’ve Learned Along the Way


A year ago, I joined the marketing team at Cloudflare.
I was first attracted to Cloudflare by its audacious mission: to help build a better Internet. As someone who’s spent most of my professional life working on programs — in marketing, policy, communications, and advocacy — that build trust and confidence in the Internet, Cloudflare’s mission resonated with me.
But it wasn’t just the mission — it was the product too. Over its eight years, the company has developed a growing platform of products and solutions that help millions of online properties — from nonprofits and hobbyists to small businesses and large enterprises — protect and accelerate anything connected to the Internet. For me, joining the Cloudflare team was an opportunity to help advance a mission and a product that is doing good in the world.
It’s been an exciting year and I want to take the opportunity to reflect on a few things I’ve learned along the way.
First, trust is everything
During my first few months at Cloudflare, I spoke with dozens and dozens of customers. I wanted to understand Cloudflare from their perspective. What challenges do they face? What progress are Continue reading
Cloudflare Registrar at three months


We announced Cloudflare Registrar in September. We launched the product by making it available in waves to our existing customers. During that time we gathered feedback and continued making improvements to the product while also adding more TLDs.
Staring today, we’re excited to make Cloudflare Registrar available to all of our customers. Cloudflare Registrar only charges you what we pay to the registry for your domain and any user can now rely on that at-cost pricing to manage their domain. As part of this announcement, we’d like to share some insights and data about domain registration that we learned during the early access period.
One-click DNS security makes a difference
When you launch your domain to the world, you rely on the Domain Name System (DNS) to direct your users to the address for your site. However, DNS cannot guarantee that your visitors reach your content because DNS, in its basic form, lacks authentication. If someone was able to poison the DNS responses for your site, they could hijack your visitors' DNS requests.
The Domain Name System Security Extensions (DNSSEC) can help prevent that type of attack by adding a chain of trust to DNS queries. When you enable DNSSEC Continue reading
Cloudflare Access now supports RDP
Last fall, the United States FBI warned organizations of an increase in attacks that exploit vulnerabilities in the Remote Desktop Protocol (RDP). Attackers stole sensitive data and compromised networks by taking advantage of desktops left unprotected. Like legacy VPNs, RDP configurations made work outside of the office corporate network possible by opening a hole in it.
Starting today, you can use Cloudflare Access to connect over RDP without sacrificing security or performance. Access enables your team to lock down remote desktops like you do physical ones while using your SSO credentials to authenticate each connection request.
Stronger passwords with identity provider integration
The FBI cited weak passwords and unrestricted port access to RDP ports as serious risks that led to the rise in RDP-based attacks. Cloudflare Access addresses those vulnerabilities by removing them altogether.
When users connect over RDP, they enter a local password to login to the target machine. However, organizations rarely manage these credentials. Instead, users set and save these passwords on an ad-hoc basis outside of the single sign-on credentials used for other services. That oversight leads to outdated, reused, and ultimately weak passwords.
Cloudflare Access integrates with the identity credentials your team already uses. Whether your Continue reading
Join us for 5 serverless events in SF Bay Area this week
Developer Week Bay Area is happening this week and Cloudflare engineers and developer relations team members are delivering several talks around the Bay. Join us in San Francisco and Oakland for the following talks. We’ll hope to see you soon.

WebAssembly on the Server, npm & genomics tools @ Cloudflare
We've partnered with the WebAssembly SF meetup group to curate three talks from Zack Bloom of Cloudflare, Laurie Voss of npm, and Robert Aboukhalil of Invitae.
Event Type: Meetup
Location: Cloudflare HQ, San Francisco, CA
Date: February 20, 2019
View Event Details & Register Here »

Serverless: An Inside Look
Cloudflare engineers are delivering three serverless talks in downtown Oakland: How Workers Work, Security: the Serverless Future, and Building a Serverless World (Map) with IoT and Workers.
Event Type: Meetup
Location: At My Sphere, Oakland, CA
Date: February 21, 2019
View Event Details & Register Here »

Developer Week Bay Area
Cloudflare will be at Developer Week Bay Area. Be sure to check out Single-Process Serverless, Building an Iot World (Map) with Serverless, and Make Your Existing Application Serverless talks.
Event Type: Conference
Location: Oakland Convention Center, Oakland, CA
Date: February 20-24, 2019
Stop the Bots: Practical Lessons in Machine Learning

Bot-powered credential stuffing is a scourge on the modern Internet. These attacks attempt to log into and take over a user’s account by assaulting password forms with a barrage of dictionary words and previously stolen account credentials, with the aim of performing fraudulent transactions, stealing sensitive data, and compromising personal information.
At Cloudflare we’ve built a suite of technologies to combat bots, many of them grounded in Machine Learning. ML is a hot topic these days, but the literature tends to focus on improving the core technology — and not how these learning machines are incorporated into real-world organizations.
Given how much experience we have with ML (which we employ for many security and performance products, in addition to bot management), we wanted to share some lessons learned with regard to how this technology manifests in actual products.

There tend to be three stages every company goes through in the life cycle of infusing machine learning into their DNA. They are:
- Business Intelligence
- Standalone Machine Learning
- Machine Learning Productization
These concepts are a little abstract — so let’s walk through how they might apply to a tangible field we all know and love: dental insurance.
Business Intelligence
Many companies already Continue reading
Announcing workers.dev
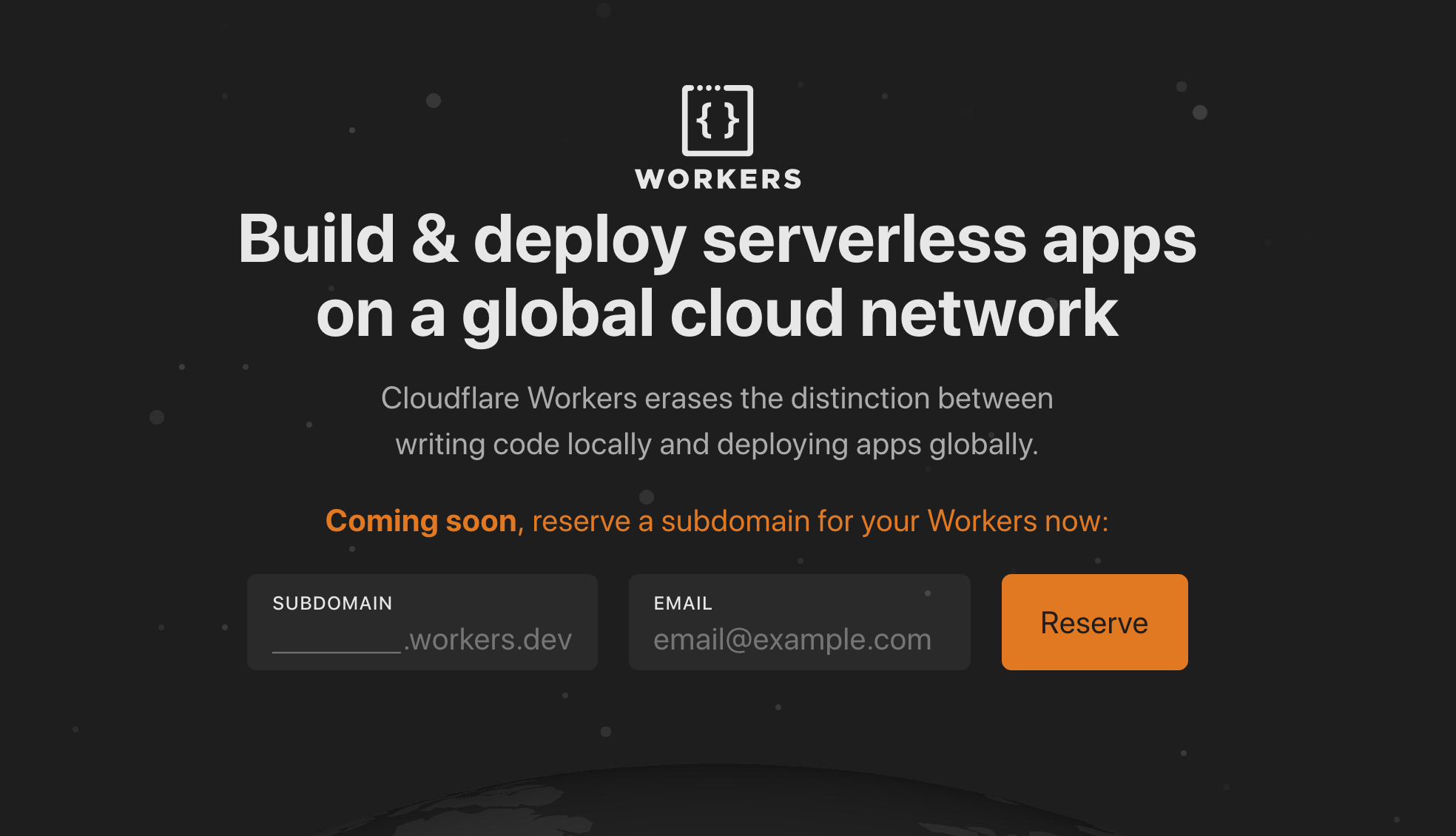
We are working really hard to allow you to deploy Workers without having a Cloudflare domain. You will soon be able to deploy your Cloudflare Workers to a subdomain-of-your-choice.workers.dev, which you can go claim now on workers.dev!
Why are we doing this?
You may have read the announcement blog post for Workers (or one of the many tutorials and guest posts), and thought “let me give this a try!”. If you’re an existing Cloudflare customer, you logged into the dashboard, and found a new icon called “Workers”, paid $5 and were on your way. If you’re not, you clicked “Sign Up”, but instead of getting to create and deploy a Worker, we asked you for your domain (if you didn’t have one, we had you register one), and move your nameservers.
Since launch, we have had tons of people who wanted to build a new serverless project from scratch or just try Workers out, but found it difficult to get started. We want to make it easier for anyone to get started building and deploying serverless applications.
How did we get here?
The way you get started on Workers today reflects our journey as a company. Continue reading
SOCKMAP – TCP splicing of the future

Recently we stumbled upon the holy grail for reverse proxies - a TCP socket splicing API. This caught our attention because, as you may know, we run a global network of reverse proxy services. Proper TCP socket splicing reduces the load on userspace processes and enables more efficient data forwarding. We realized that Linux Kernel's SOCKMAP infrastructure can be reused for this purpose. SOCKMAP is a very promising API and is likely to cause a tectonic shift in the architecture of data-heavy applications like software proxies.

But let’s rewind a bit.
Birthing pains of L7 proxies
Transmitting large amounts of data from userspace is inefficient. Linux provides a couple of specialized syscalls that aim to address this problem. For example, the sendfile(2) syscall (which Linus doesn't like) can be used to speed up transferring large files from disk to a socket. Then there is splice(2) which traditional proxies use to forward data between two TCP sockets. Finally, vmsplice can be used to stick memory buffer into a pipe without copying, but is very hard to use correctly.
Sadly, sendfile, splice and vmsplice are very specialized, synchronous and solve only one part Continue reading
Introducing Cf-Terraforming
Ever since we implemented support for configuring Cloudflare via Terraform, we’ve been steadily expanding the set of features and services you can manage via this popular open-source tool.
If you're unfamiliar with how Terraform works with Cloudflare, check out our developer docs.
We are Terraform users ourselves, and we believe in the stability and reproducibility that can be achieved by defining your infrastructure as code.
What is Terraform?
Terraform is an open-source tool that allows you to describe your infrastructure and cloud services (think virtual machines, servers, databases, network configurations, Cloudflare API resources, and more) as human-readable configurations.
Once you’ve done this, you can run the Terraform command-line tool and it will figure out the difference between your desired state and your current state, and make the API calls in the background necessary to reconcile the two.
Unlike other solutions, Terraform does not require you to run software on your hosts, and instead of spending time manually configuring machines, creating DNS records, and specifying Page Rules, you can simply run:
terraform apply
and the state described in your configuration files will be built for you.
Enter Cloudflare Terraforming
Terraform is a tremendous time-saver once you have your configuration files Continue reading
SEO Best Practices with Cloudflare Workers, Part 2: Implementing Subdomains
Recap
In Part 1, the merits and tradeoffs of subdirectories and subdomains were discussed. The subdirectory strategy is typically superior to subdomains because subdomains suffer from keyword and backlink dilution. The subdirectory strategy more effectively boosts a site's search rankings by ensuring that every keyword is attributed to the root domain instead of diluting across subdomains.
Subdirectory Strategy without the NGINX
In the first part, our friend Bob set up a hosted Ghost blog at bobtopia.coolghosthost.com that he connected to blog.bobtopia.com using a CNAME DNS record. But what if he wanted his blog to live at bobtopia.com/blog to gain the SEO advantages of subdirectories?
A reverse proxy like NGINX is normally needed to route traffic from subdirectories to remotely hosted services. We'll demonstrate how to implement the subdirectory strategy with Cloudflare Workers and eliminate our dependency on NGINX. (Cloudflare Workers are serverless functions that run on the Cloudflare global network.)
Back to Bobtopia
Let's write a Worker that proxies traffic from a subdirectory – bobtopia.com/blog – to a remotely hosted platform – bobtopia.coolghosthost.com. This means that if I go to bobtopia.com/blog, I should see the content of Continue reading
SEO Best Practices with Cloudflare Workers, Part 1: Subdomain vs. Subdirectory
Subdomain vs. Subdirectory: 2 Different SEO Strategies

Alice and Bob are budding blogger buddies who met up at a meetup and purchased some root domains to start writing. Alice bought aliceblogs.com and Bob scooped up bobtopia.com.
Alice and Bob decided against WordPress because its what their parents use and purchased subscriptions to a popular cloud-based Ghost blogging platform instead.
Bob decides his blog should live at at blog.bobtopia.com – a subdomain of bobtopia.com. Alice keeps it old school and builds hers at aliceblogs.com/blog – a subdirectory of aliceblogs.com.

Subdomains and subdirectories are different strategies for instrumenting root domains with new features (think a blog or a storefront). Alice and Bob chose their strategies on a whim, but which strategy is technically better? The short answer is, it depends. But the long answer can actually improve your SEO. In this article, we'll review the merits and tradeoffs of each. In Part 2, we'll show you how to convert subdomains to subdirectories using Cloudflare Workers.
Setting Up Subdomains and Subdirectories
Setting up subdirectories is trivial on basic websites. A web server treats its subdirectories (aka subfolders) the same as regular old folders in a Continue reading
Solving Problems with Serverless – The Cloudflare LED Data Center Board, Part I
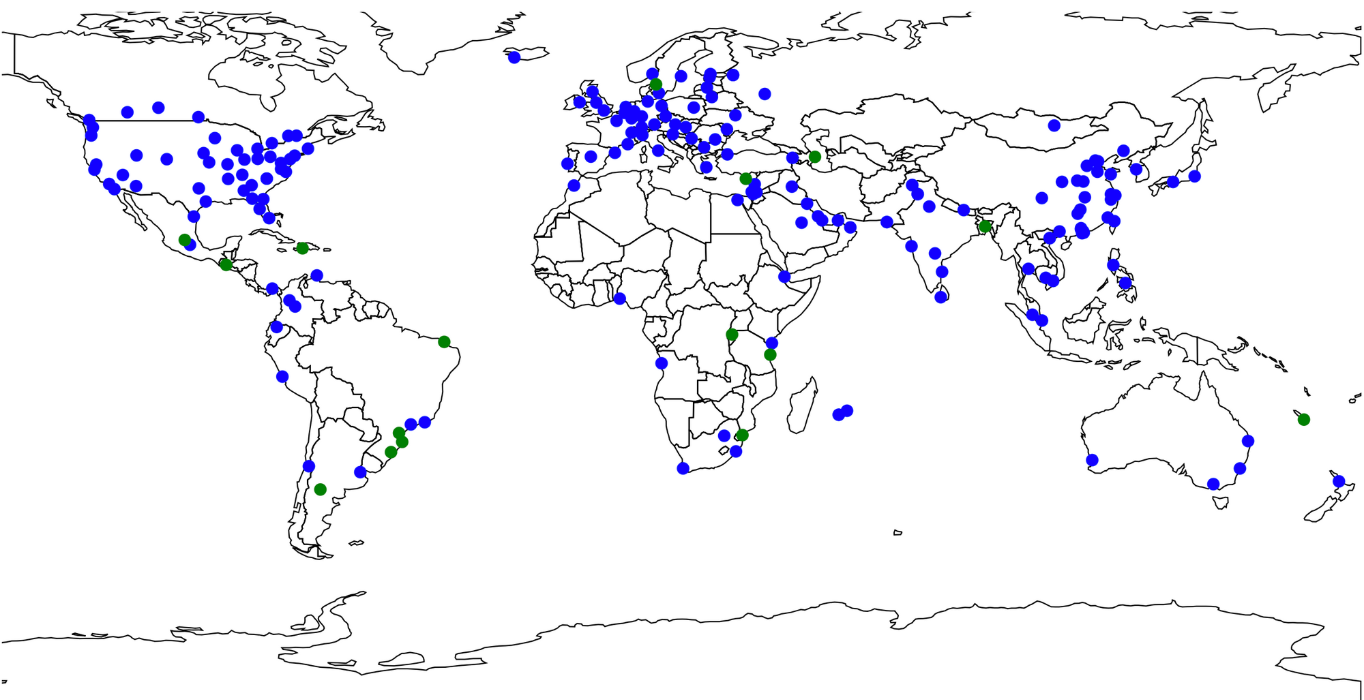
You know you have a cool job when your first project lets you bring your hobby into the office.
That’s what happened to me just a few short weeks ago when I joined Cloudflare. The task: to create a light-up version of our Data Center map – we’re talking more than a hundred LEDs tied to the deployment state of each and every Cloudflare data center. This map will be a part of our booths, so it has to be able to travel; meaning we have to consider physical shipping and the ability to update the data when the map is away from the office. And the fun part – we are debuting it at SF Developer Week in late February (I even get to give a talk about it!) That gave me one week of software time in our San Francisco office, and a little over two and a half in the Austin office with the physical materials.
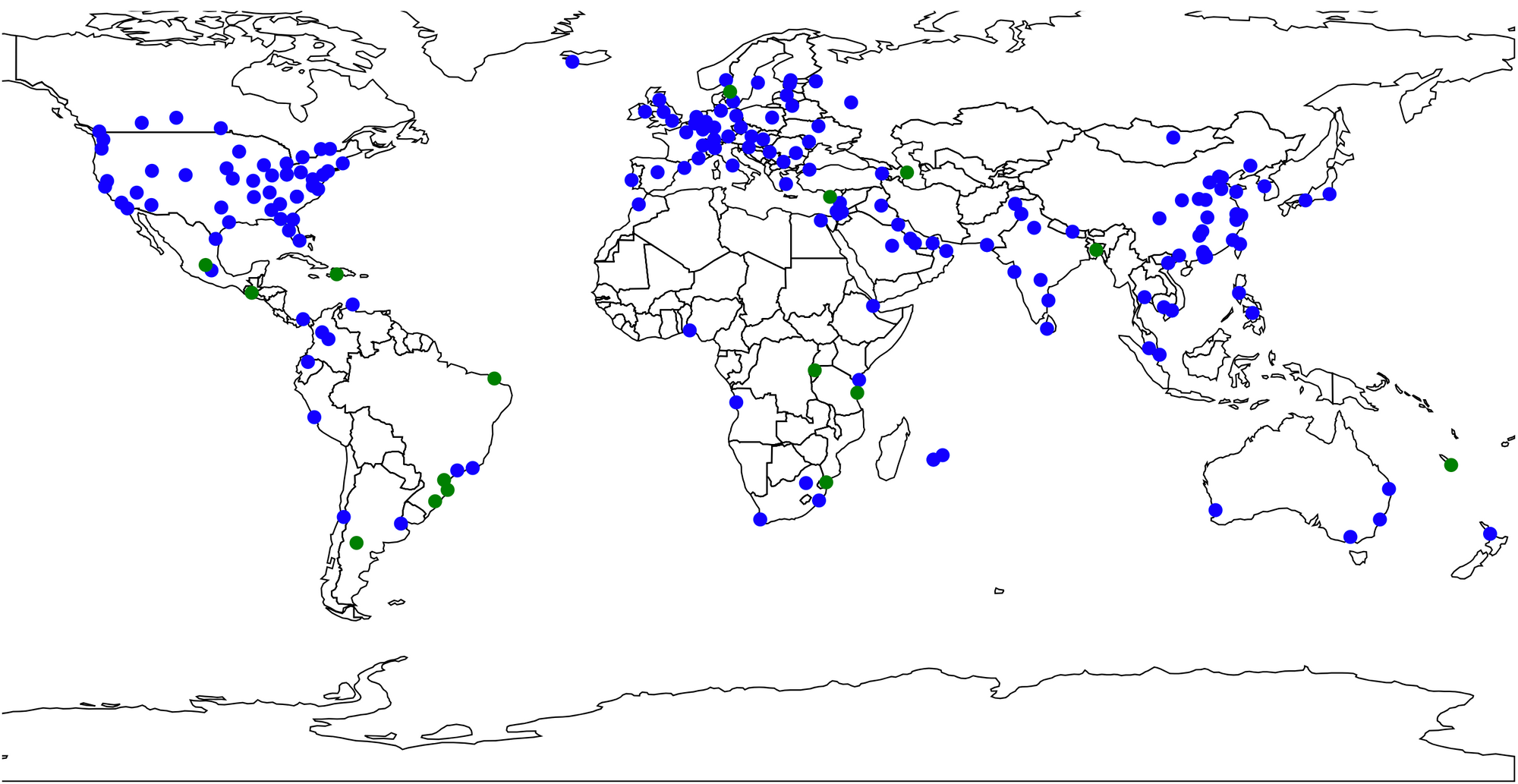
So what does this have to do with Serverless? Well, let’s think about where and how this map will need to operate: This will be going to Continue reading
Winning the Blackbird Battle


Frequent readers of the Cloudflare blog are aware of the efforts we’ve undertaken in response to our first encounter with a patent troll. We’re happy to report that on Wednesday, the U.S. Court of Appeals for the Federal Circuit issued an opinion affirming a lower court decision dismissing the case brought by Blackbird Tech. This is the last step in the process 1, we’ve won.

In addition to vigorously opposing this case in court, we created and sponsored Project Jengo to push back against the incentives that empower patent trolls like Blackbird Tech. Now that the case is over, we will be wrapping up Project Jengo and will report back with a summary of the Project’s successes in the near future.
But before we move on from the litigation, I want to share a few reflections on this case.
We noted from the very beginning: “The infringement claim is not a close one … if the ‘335 patent is read broadly enough to cover our system (which shouldn’t happen), it would also cover any system where electronic communications are examined and redacted or modified.”

Our initial observation, which we Continue reading
The Curious Case of the Garden State Imposter


Dealing with abuse complaints isn’t easy, for any Internet company. The variety of subject matters at issue, the various legal and regulatory requirements, and the uncertain intentions of complaining parties combine to create a ridiculously complex situation. We often suggest to those who propose easy answers to this challenge that they spend a few hours tracking the terminal of a member of our Trust & Safety team to get a feel for how difficult it can be. Yet even we were a bit surprised by an unusual abuse report we’ve been dealing with recently.
Last week, we received what looked like a notable law enforcement request: a complaint from an entity that identified itself as the “New Jersey Office of the Attorney General” and claimed to be a notice Cloudflare was “serving files consisting of 3D printable firearms in violation of NJ Stat. Ann. § 2C:39-9 3(I)(2).” The complaint further asked us to “delete all files described within 24 hours” and threatened “to press charges in order to preserve the safety of the citizens of New Jersey.”
Because we are generally not the host of information, and are unable to remove content from the Internet that we don’t Continue reading
Introducing The Serverlist: Cloudflare’s New Serverless Newsletter

At Cloudflare, we've been digging our heels into serverless, so we created The Serverlist newsletter, enabling us to share interesting content in the serverless space with the developer community. The Serverlist newsletter highlights all things serverless, with content that covers news from the serverless world, tutorials to learn how to get involved yourself, and different events you can attend.
Check out our first edition of The Serverlist below and sign up here to have this newsletter delivered to your inbox.