Edinburgh: 139th Cloudflare city


Our newest data center in Edinburgh expands our current total to 139 cities globally with a Cloudflare deployment. It also brings our UK total to 3 cities, after London and Manchester.
The city
Edinburgh is the capital of Scotland, located in the Lothian region. It has been recognised as the capital since the 15th century, and is the home of the Scottish government, parliament and supreme courts. It is a city of many hills, with important landmarks such as Edinburgh Castle being built at the top of a hill.
Photo by Nicola Gadler / Unsplash
Culture
One of the most famous events held each year in Edinburgh is the Fringe Festival, which is reported to be the world's largest arts festival. Many famous comedians have made their big break at this very festival.
Building a community
The internet community in the UK is very well established, but mostly concentrated on London and Manchester, with a heavy emphasis on London. By deploying in Edinburgh we're encouraging ISPs to regionalise their traffic, away from just London. We're connected to IXScotland, and are actively seeking to peer with other connected networks, to help build the peering community.
Regional expansion
Can Continue reading
Cebu City, Philippines: Cloudflare’s 138th Data Center


Cebu City, the second most populous metro area, but oldest city in the Philippines is the home of Cloudflare’s newest Data Center.
Located centrally in the Philippines, Cebu has had a long standing tradition of trade and business activity, the word itself “Cebu” meaning trade. It’s central location brings excellent coverage to central and southern Philippines, while our existing location in Manila, serving the Manila Metro and northern Philippines.
Photo by Zany Jadraque / Unsplash
Cebu’s history covers hundreds of years, with rich local culture and international influence dating back from the first Spanish visitors to modern trade and shipping. One of the more popular dishes is Lechon.
Cebu has infamous white sand beaches, in-between making millions of websites and applications faster and more secure for the Philippine internet users, we hope our servers can get some excellent R&R on the famous beaches.
Data-driven development with Cloudflare Mobile SDK


If your app loads critical resources over the network, it's relying on your user's mobile network connection to deliver an engaging experience. Network errors occur in 3 to 12% of app sessions depending on infrastructure reliability and user geography.
How much engagement are you losing in your app to network errors? Chances are, you don't know.
We didn't either, until we built a free tool that helps Android and iOS developers visualize and understand their mobile app's network utilization.
Introducing Cloudflare Mobile SDK
Our SDK helps you identify slowdowns caused by balky or too frequent network calls, so you can focus your development effort on optimizing the lowest-hanging fruit.
Modern app developers already heavily instrument their apps to identify UX impacting events: they measure and collect launch time, session length, crash rates, conversion events, and lots more, using a multitude of different metrics packages and services.
Web developers look at similar data. They also pay tons of attention to their resource waterfall, mapping their critical rendering path, and understanding which resource loads are synchronous, which are not, and which block rendering. JavaScript even exposes an API to collect waterfalls in the browser programmatically.
It's time to bring the same visibility Continue reading
Cloudflare Global Network Spans 137 Cities: Launching Durban and Port Louis Data Centers


Our newest data centers in Durban (South Africa) and Port Louis (Mauritius) expand the Cloudflare network to 137 cities globally. We are delighted to reach this special milestone, and even more excited to help improve the performance and security of over 7 million Internet properties (and growing!) across 69 countries.
Just in March, so far, we've launched new data centers across Beirut, Phnom Penh, Kathmandu, Istanbul, Reykjavík, Riyadh, Macau, Baghdad, Houston, Indianapolis, Montgomery, Pittsburgh, Sacramento, Mexico City and Tel Aviv!
Growing Africa network
Just three years (and about 100 cities ago!), we launched our very first Africa deployment in Johannesburg (South Africa). It was an exciting day for members of our team to facilitate an especially substantial latency improvement for our customers.
Since then, we’ve turned up additional deployments in Cairo (Egypt), Cape Town (South Africa), Djibouti (Djibouti), Luanda (Angola), and Mombasa (Kenya).
Durban is our third deployment in South Africa, where mobile adoption continues to drive traffic growth amongst 20 million Internet users. Other countries with three (or more) Cloudflare data centers are Australia, Canada, China, Germany and United States (with two European states joining this list very Continue reading
IBM Cloud Security Beefs Up Protection for Apps, Containers
 IBM partnered with Cloudflare to offer cloud-based security services.
IBM partnered with Cloudflare to offer cloud-based security services.
Tel Aviv, Israel: Cloudflare’s 135th Data Center Now Live!


Our newest data center is now live in Tel Aviv, Israel! This expands our global network even further to span 135 cities across 68 countries.
High-Tech in Israel
Although Israel will only be turning 70 this year, it has a history so rich we’ll leave it to the textbooks. Despite its small size, and young age, Israel is home to one of the largest tech scenes, often referred to as Start-up Nation.
Haifa’s Matam technology park houses a few tech giants’ offices including Intel, Apple, Elbit, Google, IBM, Microsoft, Yahoo, Philips and more. Meanwhile, Tel Aviv serves a true hipster capital, with a high concentration of great coffee shops to serve its many startup employees and founders.
Some brag-worthy Israeli inventions include flash drives, Waze and cherry tomatoes. This is due to Israel’s excellent education. Israel is home of the top universities in the world, bringing Israel to be one of the top five nations in scientific publication per capita output. Israel also has one of the highest PhD and MD degrees per capita, and among of the highest nobel laureates per capita as well. Israeli mothers, your nagging has paid off.
CC BY-SA 4.0 image by Rita Kozlov Continue reading
Mexico City, Mexico: Cloudflare Data Center #134


¡Mexicanos! ¡Viva México! ¡Viva México! ¡Viva México! No, no es el 16 de septiembre (Día de la Independencia de México). Sin embargo aquí en Cloudflare celebramos la introducción de nuestro Datacenter #134 en la Ciudad De México. Este Datacenter marca nuestra entrada en la nación Azteca. Anteriormente el tráfico de México era servido desde algunos de nuestros otros Datacenters (principalmente McAllen, TX, Dallas, TX y Los Angeles, CA).
Mexicans! Long Live Mexico! Long Live Mexico! Long Live Mexico! No, its not the 16th of September (Mexico Independence Day). However at Cloudflare we are proud to introduce our Datacenter #134 located in Mexico City Mexico. This data center marks our entrance into the Aztec Nation. Prior to this, traffic to Mexico was served from some of our other datacenters (Primarily Mcallen, TX, Dallas, TX and Los Angeles, CA).
El área metropolitana de México cuenta con mas de 21 millones de habitantes quienes desde hoy podrán difrutar más rápido acesso a más de 7 millones de Sitios y aplicaciones en Internet servidos por Cloudflare. Este sera nuestro décimo centro de datos en la region de América Latina y El Caribe.
The Mexico City Metropolitan Areas have Continue reading
Five new Cloudflare data centers across the United States
When Cloudflare launched, three of the original five cities in our network - Chicago, Ashburn and San Jose - were located in the United States. Since then, we have grown the breadth of the global network considerably to span 66 countries, and even added expanded the US footprint to twenty five locations. Even as a highly international business, the United States continues to be home to a number of our customers and the majority of Cloudflare employees.
Today, we expand our network in the United States even further by adding five new locations: Houston (Texas), Indianapolis (Indiana), Montgomery (Alabama), Pittsburgh (Pennsylvania) and Sacramento (California) as our 129th, 130th, 131st, 132nd and 133rd data centers respectively. They represent states that collectively span nearly 100 million people. In North America alone, the Cloudflare network now spans 37 cities, including thirty in the US.
In each of these new locations, we connect with at least one major local Internet service provider and also openly peer using at least one major Internet exchange. We are participants at CyrusOne IX Houston, Midwest IX Indianapolis, Montgomery IX, Pittsburgh IX, and the upcoming Sacramento IX.
These deployments improves performance, security and reliability Continue reading
Baghdad, Iraq: Cloudflare’s 128th Data Center


Cloudflare's newest data center is located in Baghdad, Iraq, in the region often known as the cradle of civilization. This expands our growing Middle East presence, while serving as our 45th data center in Asia, and 128th data center globally.
Even while accelerating over 7 million Internet properties, this deployment helps our effort to be closer to every Internet user. Previous, ISPs such as Earthlink were served from our Frankfurt data center. Nearly 40 million people live in Iraq.
Rich Cuisine
One of the world's largest producers of the sweet date palm, Iraq's cuisine dates back over 10,000 years and includes favorites such as,
- Kleicha: Date-filled cookies flavored with cardamom, saffron and rose water
- Mezza: a selection of appetizers to begin the meal
- Iraqi Dolma: stuffed vegetables with a tangy sauce
- Iraqi Biryani: cooked rice with spices, beans, grilled nuts and meat / vegetables
- Masgouf: whole baked fish marinated in oil, salt, pepper, turmeric and tamarind
New data centers
Baghdad is the first of eight deployments joining the Cloudflare global network just this week. Stay tuned!
The Cloudflare Global Anycast Network
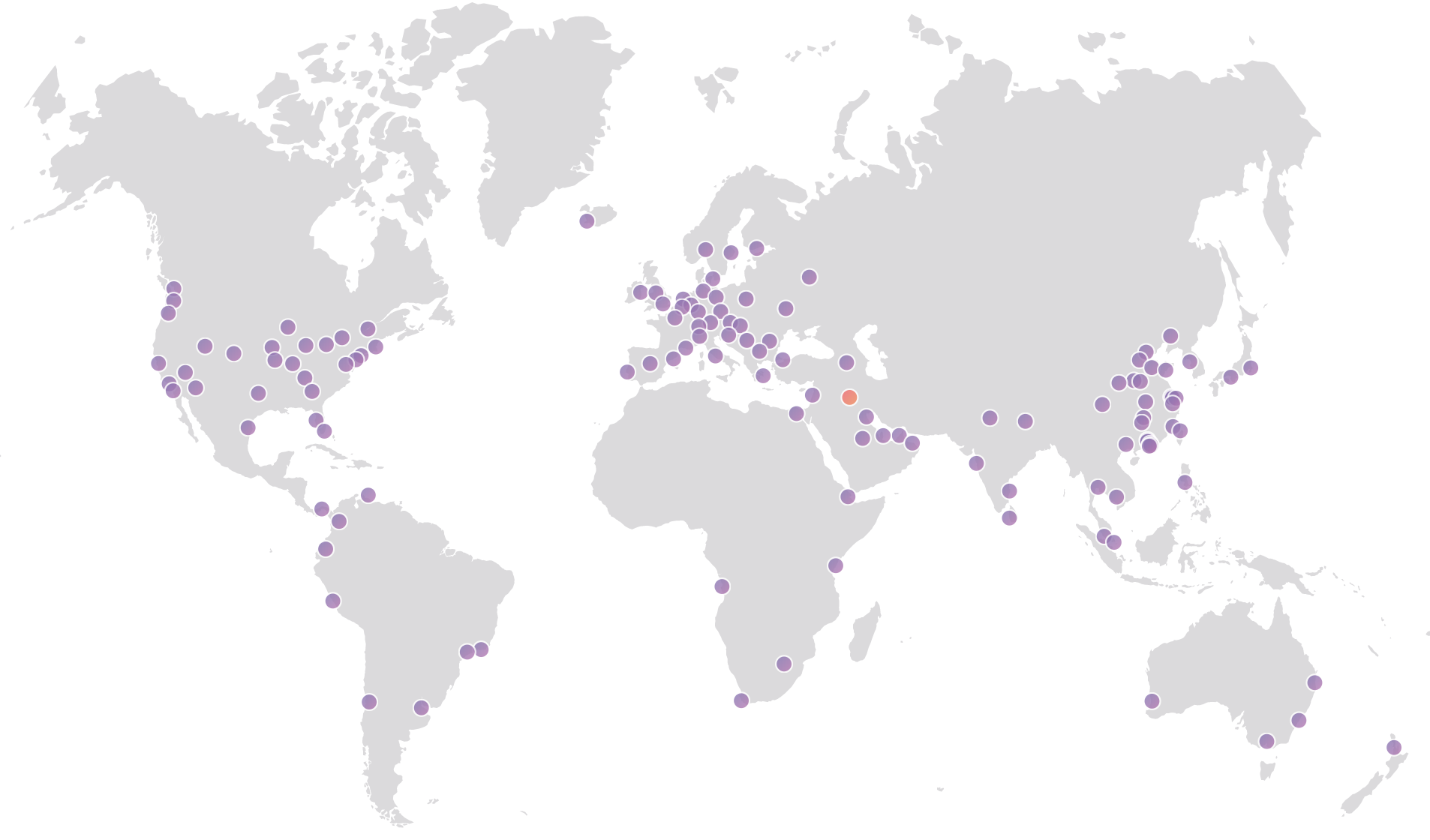
This map reflects the network as of the publish date of this blog Continue reading
IBM Cloud, Now Powered by Cloudflare

A Tale of Two New Relationships
Late last spring, we were seeking to expand our connections inside of IBM. IBM had first become a direct Cloudflare customer in 2016, when its X-force Exchange business selected Cloudflare, instead of traditional scrubbing center solutions, for DDoS protection, WAF, and Load Balancing. We had friendly relationships with several people inside of IBM’s Softlayer business. We learned that the IBM “Networking Tribe” was evaluating various solutions to fill product gaps that their cloud customers were experiencing for DDoS, DNS, WAF, and load balancing.
In trying to engage with the people leading the effort, I made a casual phone call late on a Friday afternoon to one of the IBMers based in Raleigh, NC. When he understood that I was from Cloudflare, he replied, “Oh, I know Cloudflare. You guys do DDoS protection, right?” I replied, “Well, yes, we do offer DDoS protection, but we also offer a number of other security and performance services.” He indicated that he would be in the Bay Area two weeks later, and that he would bring his team to our office if we could make the time.
Also late last spring, my wife delivered our baby Continue reading
Everyone can now run JavaScript on Cloudflare with Workers
Exactly one year ago today, Cloudflare gave me a mission: Make it so people can run code on Cloudflare's edge. At the time, we didn't yet know what that would mean. Would it be container-based? A new Turing-incomplete domain-specific language? Lua? "Functions"? There were lots of ideas.
Eventually, we settled on what now seems the obvious choice: JavaScript, using the standard Service Workers API, running in a new environment built on V8. Five months ago, we gave you a preview of what we were building, and started the beta.
Today, with thousands of scripts deployed and many billions of requests served, Cloudflare Workers is now ready for everyone.
"Moving away from VCL and adopting Cloudflare Workers will allow us to do some creative routing that will let us deliver JavaScript to npm's millions of users even faster than we do now. We will be building our next generation of services on Cloudflare's platform and we get to do it in JavaScript!"
— CJ Silverio, CTO, npm, Inc.
What is the Cloud, really?
Historically, web application code has been split between servers and browsers. Between them lies a vast but fundamentally dumb network which merely ferries data from point to Continue reading
Deprecating TLS 1.0 and 1.1 on api.cloudflare.com
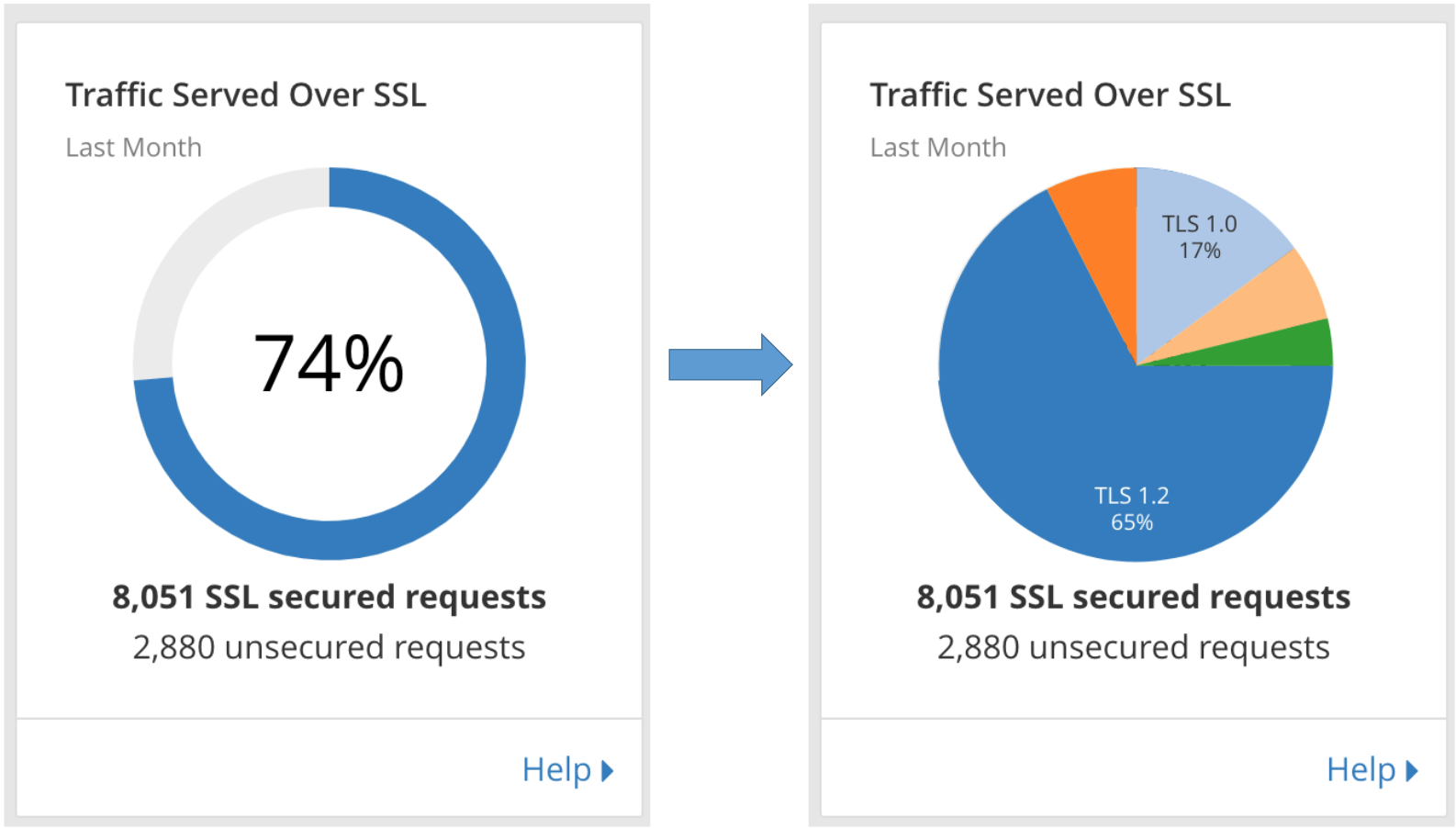
On June 4, Cloudflare will be dropping support for TLS 1.0 and 1.1 on api.cloudflare.com. Additionally, the dashboard will be moved from www.cloudflare.com/a to dash.cloudflare.com and will require a browser that supports TLS 1.2 or higher.
No changes will be made to customer traffic that is proxied through our network, though you may decide to enforce a minimum version for your own traffic. We will soon expose TLS analytics that indicate the percent of connections to your sites using TLS 1.0-1.3, and controls to set a specific minimum version. Currently, you may enforce version 1.2 or higher using the Require Modern TLS setting.
Prior to June 4, API calls made with TLS 1.0 or 1.1 will have warning messages inserted into responses and dashboard users will see a banner encouraging you to upgrade your browser. Additional details on these changes, and a complete schedule of planned events can be found in the timeline below.
Background
Transport Layer Security (TLS) is the protocol used on the web today to encrypt HTTPS connections. Version 1.0 was standardized almost 20 years ago as the successor to SSL Continue reading
Macau: Cloudflare Data Center 127


Cloudflare's 127th data center is now live in Macau, helping make over 7 million Internet facing applications safer and faster. This is our 44th data center in Asia.
Cloudflare 將在澳門啟用全球第127個數據中心, 幫助超過 7,000,000 客戶的互聯網資產運行得更快、更安全。澳門也是我們在亞洲的第44個數據中心。
O 127º centro de dados da Cloudflare agora está em funcionamento em Macau, ajudando a tornar mais de 7 milhões de aplicações voltadas para a Internet de forma mais segura e rápida. Estamos felizes em compartilhar que este é o nosso 44º centro de dados na Ásia.

CC BY-NC-ND 2.0 image by kidchen915
Blending Chinese and Portuguese culture, just last year, Macau welcomed over 30 million visitors. Visit Macau to experience its unique and extravagant entertainment scene, see scenic spots such as the Ruins of St Paul, Senado Square, attempt the world's highest bungy jump from Macau Tower, or enjoy the foodie paradise Macau delivers!
有著與眾不同的中國及葡萄牙文化融合景觀,澳門至去年為止已經吸引了三千萬遊客來一睹她的風采。你可以拜訪著名的娛樂景觀,像是聖保祿大教堂遺址,議事亭廣場,挑戰澳門的美食,亦可以選擇從全世界最高的高空彈跳地點ㄧ澳門旅遊塔上一躍而下。
Combinando cultura chinesa e portuguesa, o ano passado, Macau recebeu mais de 30 milhões de visitantes. Recomendamos que visite Macau para experimentar a cena de entretenimento única e extravagante, explore os pontos cénica, como ruínas de São Paulo, Praça do Senado, e ainda, tente o "bungee jumping" mais alto do mundo deste da Torre de Macau, ou aproveite Continue reading
Riyadh, Saudi Arabia: Cloudflare Data Center #126


We are very excited to announce Cloudflare’s 126th data center in Riyadh, Saudi Arabia (only hours after launching in Reykjavík!). This joins our existing Middle East facilities to provide even stronger coverage and resilience for over 7 million Internet properties across the region.
Our newest deployment was made possible in partnership with Zain, which now experiences reduced latency for every Internet user accessing every Internet facing application using Cloudflare. At least four additional Middle East deployments are already in the works.
Saudi Arabia
Photo by Mohammed Alamri / Unsplash
Over 30 million people live in Saudi Arabia, which is also the 13th largest country by area at over 830,000 square miles. In 2020, alongside the launch of entirely new “economic cities”, we might witness the opening of the world’s tallest skyscraper at a staggering 1,000m height, located in Jeddah. More modestly, but in much less than two years from now, we also expect to place a Cloudflare data center there.
Saudi Arabia has an incredibly young demographic, as over half of the population is less than 25. Additional 4G LTE deployments, while also paving the way for 5G, should drive increased Internet usage.
Stay tuned as Continue reading
Reykjavík, Cloudflare’s northernmost location

Iceland is a small country in Northern Europe, a land of active volcanoes and boiling hot geysers. The geology and climate creates unique conditions for running compute power. With an abundance of green electricity and natural cooling, many companies are placing high power machines in Iceland to run power intensive, heat generating operations. Reykjavík is our 125th location globally.

Connecting to the rest of the world
A unique aspect about Iceland relates to how it connects to the Internet, being situated on the Mid-Atlantic Ridge means submarine cables are necessary to reach networks in other countries. Iceland has three active fibre optic submarine cables that land on its shores: FARICE-1, DANICE and Greenland Connect. Due to the distance, latency to the nearest Cloudflare locations in London and Copenhagen starts at 35 milliseconds. By deploying in Reykjavík, we're able to drive down latency even further to a minimum of under 1 millisecond.
Iceland is unique in many ways, but is no different from other countries when it comes to exchanging internet traffic. ISNIC, Iceland's Network Information Centre runs RIX, the Reykjavík Internet Exchange. Cloudflare is the only CDN network connected to RIX, allowing traffic to flow directly to Continue reading
HTTP Analytics for 6M requests per second using ClickHouse
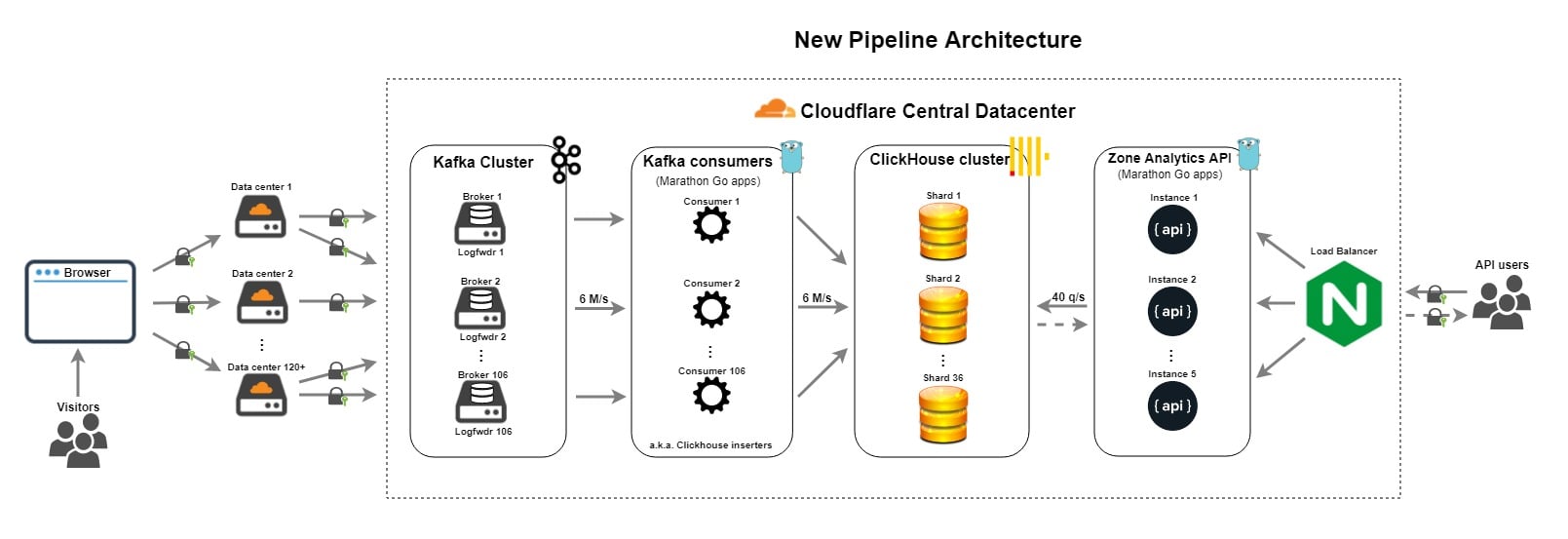
One of our large scale data infrastructure challenges here at Cloudflare is around providing HTTP traffic analytics to our customers. HTTP Analytics is available to all our customers via two options:
- Analytics tab in Cloudflare dashboard
- Zone Analytics API with 2 endpoints
- Dashboard endpoint
- Co-locations endpoint (Enterprise plan only)
In this blog post I'm going to talk about the exciting evolution of the Cloudflare analytics pipeline over the last year. I'll start with a description of the old pipeline and the challenges that we experienced with it. Then, I'll describe how we leveraged ClickHouse to form the basis of a new and improved pipeline. In the process, I'll share details about how we went about schema design and performance tuning for ClickHouse. Finally, I'll look forward to what the Data team is thinking of providing in the future.
Let's start with the old data pipeline.
Old data pipeline
The previous pipeline was built in 2014. It has been mentioned previously in Scaling out PostgreSQL for CloudFlare Analytics using CitusDB and More data, more data blog posts from the Data team.
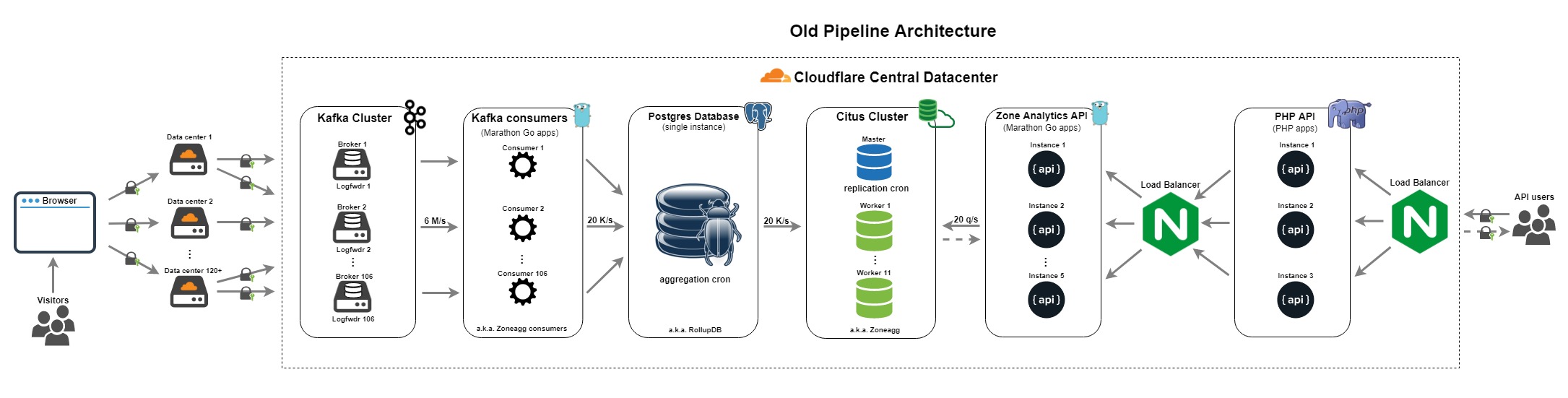
It had following components:
- Log forwarder - collected Cap'n Proto formatted logs from the edge, notably DNS and Nginx logs, Continue reading
NAT To Be Missed At SXSW

We’re at the EDGE of our seats, about to LANd in Austin, Texas in route for SXSW. (TKIP, hip, hooray!)
ARP you going to be there? We R going to have three epoch sessions by Cloudflare speakers. Ifdown, seems apt you could SELECT to JOIN. Cat make it? Not a bg deal, wget it (though it mega hertz we won’t C you). All the audio from the three sessions will be recorded, you can listen to the cd.
WPS! I almost forgot to tel(net) you whois going to be there, and WAN and where to go.
On Friday, March 9, I’m moderating a panel with Emily Schechter from Google, Aaron DeVera from Deloitte and Gabe Kassel from eero about how Wi-Fi networks work and WEP happens when attackers coax people into joining insecure networks. It’s at Salon K in the Hilton at 3:30PM.
On Sunday the 11th, Nitin Rao is on a panel with Heather West from Mozilla, Stefan Lederer from Bitmovin and Fred Benenson from Unlimited Liability Corporation LLC about the impact of the recent revocation of Net Neutrality rules on online video streaming. It’s at 11AM at Salon J in the Continue reading
The real cause of large DDoS – IP Spoofing
A week ago we published a story about new amplification attacks using memcached protocol on UDP port 11211. A few things happened since then:
- Github announced it was a target of 1.3Tbps memcached attack.
- OVH and Arbor reported similar large attacks with the peak reported at 1.7Tbps.
Let's take a deep breath and discuss why such large DDoS attacks are even possible on the modern internet.
Large attacks use IP spoofing

CC BY-SA 2.0 image by DaPuglet
All the gigantic headline-grabbing attacks are what we call "L3" (Layer 3 OSI[1]). This kind of attack has a common trait - the malicious software sends as many packets as possible onto the network. For greater speed these packets are hand crafted by attackers - they are not generated using high-level, well-behaved libraries. Packets are mashed together as a series of bytes and fired onto the network to inflict the greatest damage.
L3 attacks can be divided into two categories, depending on where the attacker directs their traffic:
-
Direct: where the traffic is sent directly against a victim IP. A SYN flood is a common attack of this type.
-
Amplification: the traffic is sent to vulnerable Continue reading
Istanbul (not Constantinople): Cloudflare’s 124th Data Center


Cloudflare is excited to turn up our newest data center in Istanbul, Turkey. This is our 124th data center globally (and 62nd country), and it is throwing a curveball in our data center by continent tracking. Istanbul is one of the only cities in the world to span two continents: Europe and Asia. Technically, we’ll specify this is our 34th data center in Europe. In the coming weeks, we’ll continue to attract more traffic to this deployment as more networks interconnect with us locally.
March 2018 is a big month for us, as we’ll be announcing (on average) nearly one new Cloudflare data center per day. Stay tuned as we continue to meaningfully expand our geographic coverage and capacity.
Turkish Internet
The Hagia Sophia - Photo by Blaque X / Unsplash
Istanbul itself is home to more than 16 million people, and Turkey is home to over 80 million people. For reference, Turkey’s population is comparable to Germany’s, where Cloudflare turned up its 11th, 31st, 44th, 72nd and 110th data centers in Frankfurt, Düsseldorf, Berlin, Hamburg and Munich. Internet usage in Turkey is approaching 70%, while the rate of Turkish households with access to Internet now exceeds Continue reading
Squeezing the firehose: getting the most from Kafka compression

We at Cloudflare are long time Kafka users, first mentions of it date back to beginning of 2014 when the most recent version was 0.8.0. We use Kafka as a log to power analytics (both HTTP and DNS), DDOS mitigation, logging and metrics.
 Firehose CC BY 2.0 image by RSLab
Firehose CC BY 2.0 image by RSLab
While the idea of unifying abstraction of the log remained the same since then (read this classic blog post from Jay Kreps if you haven't), Kafka evolved in other areas since then. One of these improved areas was compression support. Back in the old days we've tried enabling it a few times and ultimately gave up on the idea because of unresolved issues in the protocol.
Kafka compression overview
Just last year Kafka 0.11.0 came out with the new improved protocol and log format.
The naive approach to compression would be to compress messages in the log individually:

Edit: originally we said this is how Kafka worked before 0.11.0, but that appears to be false.
Compression algorithms work best if they have more data, so in the new log format messages (now called records) are packed back to back and compressed in Continue reading





