Cloudflare’s WAF is recognized as customers’ choice for 2021
The team at Cloudflare building our Web Application Firewall (WAF) has continued to innovate over the past year. Today, we received public recognition of our work.
The ease of use, scale, and innovative controls provided by the Cloudflare WAF has translated into positive customer reviews, earning us the Gartner Peer Insights Customers' Choice Distinction for WAF for 2021. You can download a complimentary copy of the report here.

Gartner Peer Insights Customers’ Choice distinctions recognize vendors and products that are highly rated by their customers. The data collected represents a top-level synthesis of vendor software products most valued by IT Enterprise professionals.
The positive feedback we have received is consistent and leads back to Cloudflare’s product principles. Customers find that Cloudflare’s WAF is:
- “An excellent hosted WAF, and a company that acts more like a partner than a vendor” — Principal Site Reliability Architect in the Services Industry [Full Review];
- “A straightforward yet highly effective WAF solution” — VP in the Finance Industry [Full Review];
- “Easy and Powerful with Outstanding Support” — VP Technology in the Retail Industry [Full Review];
- “Secure, Intuitive and a Delight for web security and accelerations” — Sr Director-Technical Product Continue reading
Build Zero Trust rules with managed devices


Starting today, your team can use Cloudflare Access to build rules that only allow users to connect to applications from a device that your enterprise manages. You can combine this requirement with any other rule in Cloudflare’s Zero Trust platform, including identity, multifactor method, and geography.
As more organizations adopt a Zero Trust security model with Cloudflare Access, we hear from customers who want to prevent connections from devices they do not own or manage. For some businesses, a fully remote workforce increases the risk of data loss when any user can login to sensitive applications from an unmanaged tablet. Other enterprises need to meet new compliance requirements that restrict work to corporate devices.
We’re excited to help teams of any size apply this security model, even if your organization does not have a device management platform or mobile device manager (MDM) today. Keep reading to learn how Cloudflare Access solves this problem and how you can get started.
The challenge of unmanaged devices
An enterprise that owns corporate devices has some level of control over them. Administrators can assign, revoke, inspect and manage devices in their inventory. Whether teams rely on management platforms or a simple spreadsheet, businesses can Continue reading
Inside Cloudflare: Preventing Account Takeovers


Over the last week, Cloudflare has published blog posts on products created to secure our customers from credential stuffing bots, detect users with compromised credentials, and block users from proxy services. But what do we do inside Cloudflare to prevent account takeovers on our own applications? The Security Team uses Cloudflare products to proactively prevent account compromises. In addition, we build detections and automations as a second layer to alert us if an employee account is compromised. This ensures we can catch suspicious behavior, investigate it, and quickly remediate.
Our goal is to prevent automated and targeted attackers regardless of the account takeover technique: brute force attack, credential stuffing, botnets, social engineering, or phishing.
Classic Account Takeover Lifecycle
First, let's walk through a common lifecycle for a compromised account.
In a typical scenario, a set of passwords and email addresses have been breached. These credentials are reused through credential stuffing in an attempt to gain access to any account (on any platform) where the user may have reused that combination. Once the attacker has initial access, which means the combination worked, they can gain information on that system and pivot to other systems through methods. This is classified Continue reading
End User Security: Account Takeover Protections with Cloudflare


End user account security is always a top priority, but a hard problem to solve. To make matters worse, authenticating users is hard. With datasets of breached credentials becoming commonplace, and more advanced bots crawling the web attempting credential stuffing attacks, protecting and monitoring authentication endpoints becomes a challenge for security focused teams. On top of this, many authentication endpoints still rely just on providing a correct username and password making undetected credential stuffing lead to account takeover by malicious actors.
Many features of the Cloudflare platform can help with implementing account takeover protections. In this post we will go over several examples as well as announce a number of new features. These include:
- Open Proxy managed list (NEW): ensure authentication attempts to your app are not coming from proxy services;
- Super Bot Fight Mode (NEW): keep automated traffic away from your authentication endpoints;
- Exposed Credential Checks (NEW): get a warning whenever a user is logging in with compromised credentials. This can be used to initiate a two factor authentication flow or password reset;
- Cloudflare Access: add an additional authentication layer by easily integrating with third party OATH services, soon with optional enforcement of managed devices (NEW);
- Rate Limiting Continue reading
A new Cloudflare Web Application Firewall
The Cloudflare Web Application Firewall (WAF) blocks more than 57 billion cyber threats per day. That is 650k blocked HTTP requests per second. The original code that filters this traffic was written by Cloudflare’s now CTO and the WAF has since received many accolades including the highest score for ability to execute in the 2020 Gartner Magic Quadrant for WAF.
Because we value replacing code when it is no longer as maintainable, performant, or scalable as it once was, we regularly rewrite key parts of the Cloudflare stack. That’s necessary as our enormous growth makes yesterday’s solutions unworkable. For some time, we have been working on replacing that original LuaJIT code John wrote with new code, written in Rust, along with an improved UI.
We are now excited to announce a new Cloudflare Web Application Firewall.
Starting today, 10% of newly created accounts on Cloudflare will be given access to the new WAF whenever a Pro plan zone or above is added. This percentage will increase to 100% of new accounts over the month of April, after which migration efforts will commence for existing customers. Enterprise customers may migrate early by contacting their account team.
What’s changing
The Web Application Continue reading
Keyless SSL now supports FIPS 140-2 L3 hardware security module (HSM) offerings from all major cloud providers
Private encryption keys stored in hardware security module offerings from all major cloud providers can now be used to secure HTTPS connections at Cloudflare’s global edge.
Cloudflare generates, protects, and manages more SSL/TLS private keys than perhaps any organization in the world. Private keys must be carefully protected, as an attacker in possession of one can impersonate legitimate sites and decrypt HTTPS requests. To mitigate this risk, Cloudflare has strict key handling procedures and layers of isolation at the edge that are designed to safeguard keys at all costs. But for a small minority of customers with information security policies dictating where they can (or cannot) custody their keys, these protections do not meet their requirements.
It was for these customers that we first released Keyless SSL in 2014, a protocol we use extensively inside our network: all of the TLS handshakes per day established at the Cloudflare edge that take place in a process that has no access to our customers’ private keys. The data required to establish the session is instead sent to a separate system, where the necessary cryptographic signing operation is performed. For keys uploaded to or generated by Cloudflare, we manage this other system, Continue reading
Heartbleed Revisited


In 2014, a bug was found in OpenSSL, a popular encryption library used to secure the majority of servers on the Internet. This bug allowed attackers to abuse an obscure feature called TLS heartbeats to read memory from affected servers. Heartbleed was big news because it allowed attackers to extract the most important secret on a server: its TLS/SSL certificate private key. After confirming that the bug was easy to exploit, we revoked and reissued over 100,000 certificates, which highlighted some major issues with how the Internet is secured.
As much as Heartbleed and other key compromise events were painful for security and operations teams around the world, they also provided a learning opportunity for the industry. Over the past seven years, Cloudflare has taken the lessons of Heartbleed and applied them to improve the design of our systems and the resiliency of the Internet overall. Read on to learn how using Cloudflare reduces the risk of key compromise and reduces the cost of recovery if it happens.
Keeping keys safe
An important tenet of security system design is defense-in-depth. Important things should be protected with multiple layers of defense. This is why security-conscious people keep spare house Continue reading
Introducing: Advanced Certificate Manager
In 2016, we launched Dedicated Certificates. Today, we are excited to announce that dedicated certs are getting an upgrade… and a new name… introducing Advanced Certificate Manager! Advanced Certificate Manager is a flexible and customizable way to manage your certificates on Cloudflare.
Certificates
TLS Certificates are the reason you can safely browse the Internet, securely transfer money online, and keep your passwords private. They do that by encrypting your sensitive messages using public-key cryptography that is cryptographically linked to the certificate itself. But beyond that, TLS certificates are used to make an assertion about identity — verifying that the server is who they claim to be. Server Certificates — used by every website — include the website's name on the certificate and is issued by a third-party certificate authority (CA) who verifies that the certificate's information is correct and accurate.
Browsers only let you visit a website when it's encrypted using TLS after it has successfully validated the certificate presented by the server — much like how security checks your ID to board a plane.
We are focusing on securing the Internet now more than ever. We want to make it as easy as possible for any customer to be Continue reading
Introducing Super Bot Fight Mode
Almost half of the Internet’s traffic is powered by bots. Bots have scoured the net for years, relentlessly hacking into bank accounts, scooping up Bruno Mars tickets, and scraping websites for data. The problem is so widespread that we launched Bot Fight Mode in 2019 to fight back. Since then, over 150,000 individuals and small businesses have used the product, and we’ve received countless requests for more functionality. More analytics, more detections, and more controls.
Introducing Super Bot Fight Mode.
Beginning immediately, any Cloudflare user with a Pro or Business site can take new action against bots. We’ve added advanced features in the dashboard and some exciting updates to analytics. Free customers will retain all the benefits they've enjoyed with Bot Fight Mode, and our Enterprise Bot Management product will continue to push the needle on innovation.
In the Dashboard
Our bot solutions have a new home. The features we discuss in this blog post go beyond a single toggle, so we created a hub for bot protection. Head to the Firewall app and select the “Bots” subtab to get started.
The new hub is live for all users, including those with Enterprise Bot Management.
Pro Plan Features
First up: Continue reading
Mitigating Bot Attacks against Cloudflare
The word “bots” on the Internet is a fairly loaded one. My earliest ‘bot’ experience was on IRC, where bots were quite helpful in making sure your favorite channel didn’t get taken over by malicious users and allowed for fun games of trivia. Around five years ago, “bots” were often referencing text chats in combination with AI and messaging platforms/apps as a new way to interact with customers. Today most of the connotations around bots on the Internet, particularly in the security space, are negative and we have a number of vendors offering new ways to detect and block bots.
In its most simple form, a bot is an automated piece of software that replaces human interaction. In the examples above, this is done so we can scale a process to be faster or more extensive than a single manual action. Search Engine bots exist because it is impossible (or at the very least, impractical) to crawl the Internet one curl at a time. The benefit of scale can be used for both good and for bad, by attacking a property on the Internet. Bots are used for attacks at scale — they can be deployed to attack an Continue reading
Announcing API Abuse Detection


APIs are incredibly important. Throughout the 2000s, they formed the backbone of popular web services, helping the Internet become more useful and accessible. In the 2010s, APIs played a larger role in our lives, allowing personal devices to communicate with the digital world. Many of our daily activities, like using rideshare services and paying for lattes, are dependent on this form of modern communication. Now we are approaching a post-pandemic world in which APIs will be more important than ever.
Unfortunately, as any technology grows, so does its surface area for abuse. APIs are no exception. Competing rideshare services might monitor each other’s prices via API, spawning a price war and a waste of digital resources. Or a coffee drinker might manipulate an API for a latte discount. Some companies have thousands of APIs — including ones that they don’t even know about. Cloudflare can help solve these problems.
Today, we are announcing early access to API Discovery and API Abuse Detection.
Background
Before going further, it’s important to explain why we need a solution for APIs. Traditional security tools, including Rate Limiting and DDoS Protection, can be wonderfully useful. But these approaches were not built to act Continue reading
Page Shield: Protect User Data In-Browser


Today we're excited to introduce Page Shield, a client-side security product customers can use to detect attacks in end-user browsers.
Starting in 2015, a hacker group named Magecart stole payment credentials from online stores by infecting third-party dependencies with malicious code. The infected code would be requested by end-user browsers, where it would execute and access user information on the web page. After grabbing the information, the infected code would send it to the hackers, where it would be resold or used to launch additional attacks such as credit card fraud and identity theft.
Since then, other targets of such supply chain attacks have included Ticketmaster, Newegg, British Airways, and more. The British Airways attack stemmed from the compromise of one of their self-hosted JavaScript files, exposing nearly 500,000 customers’ data to hackers. The attack resulted in GDPR fines and the largest class-action privacy suit in UK history. In total, millions of users have been affected by these attacks.
Writing secure code within an organization is challenging enough without having to worry about third-party vendors. Many SaaS platforms serve third-party code to millions of sites, meaning a single compromise could have devastating results. Page Shield helps customers monitor these potential Continue reading
Protecting Cloudflare Customers from BGP Insecurity with Route Leak Detection
Border Gateway Protocol (BGP) route leaks and hijacks can ruin your day — BGP is insecure by design, and incorrect routing information spreading across the Internet can be incredibly disruptive and dangerous to the normal functioning of customer networks, and the Internet at large. Today, we're excited to announce Route Leak Detection, a new network alerting feature that tells customers when a prefix they own that is onboarded to Cloudflare is being leaked, i.e., advertised by an unauthorized party. Route Leak Detection helps protect your routes on the Internet: it tells you when your traffic is going places it’s not supposed to go, which is an indicator of a possible attack, and reduces time to mitigate leaks by arming you with timely information.
In this blog, we will explain what route leaks are, how Cloudflare Route Leak Detection works, and what we are doing to help protect the Internet from route leaks.
What are route leaks and why should I care?
A route leak occurs when a network on the Internet tells the rest of the world to route traffic through their network, when the traffic isn’t supposed to go there normally. A great example of this Continue reading
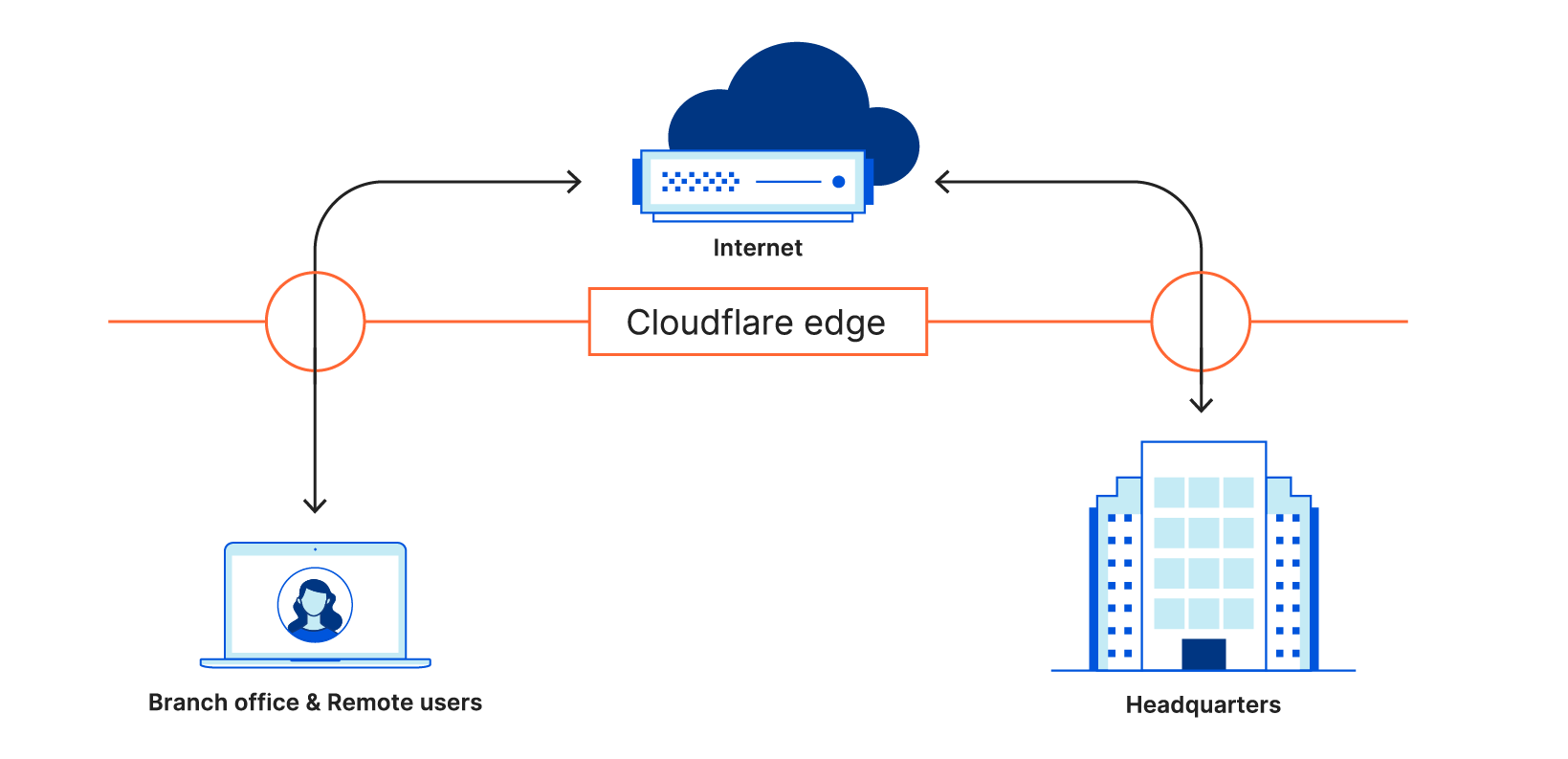
Cloudflare’s New Magic WAN Is A Familiar Trick
Cloudflare is building out its network and security services offerings to compete with SASE and CASB providers. The new Magic WAN and Magic Firewall offerings let customers direct traffic from branch offices, remote workers, and data centers to Cloudlfare's infrastructure for WAN transport and security inspection.
The post Cloudflare’s New Magic WAN Is A Familiar Trick appeared first on Packet Pushers.
Announcing Cloudflare’s Data Loss Prevention platform

Today, we’re excited to announce that your team can use Cloudflare’s network to build Zero Trust controls over the data in your enterprise - wherever it lives and however it moves.
Stopping data loss is difficult for any team and that challenge has become harder as users have left offices and data has left on-premise storage centers. Enterprises can no longer build a simple castle-and-moat around their data. Users now connect from any location on the planet to applications that live in environments outside of that enterprise’s control.
We have talked to hundreds of customers who have resorted to applying stopgap measures to try and maintain that castle-and-moat model in some form, but each of those band-aids slow down their users or drive up costs - or both. Almost all of the short-term options available combine point solutions that ultimately force traffic to backhaul through a central location.

Part of Cloudflare One, Cloudflare’s approach to data loss prevention relies on the same infrastructure and global network that accelerates user traffic to the Internet to also perform inline inspection against all traffic regardless of how it arrives on our network.
We also know that enterprises need more than just scanning Continue reading
Using Cloudflare for Data Loss Prevention


Data exfiltration, or data loss, can be a very time-consuming and expensive ordeal causing financial loss, negative brand association, and penalties from privacy focused laws. Take for example, an incident where sensitive smart grid and metering R&D knowledge information from an industrial control system of a North American electric utility was exfiltrated through an attack that was suspected to have originated from inside the network. Unauthorized access to data from a utilities company can result in a compromised smart grid or power outages.
In another example, a security researcher found exposed and unknown (undocumented) API endpoints for Tesla’s Backup Gateway that could have been used to export data or make unauthorized changes. This would have had very real physical consequences had the unauthenticated API endpoint been used by an attacker to damage the battery or the connected electric grid.

Both these examples emphasize the importance of considering internal and external threats when thinking about how to protect a network from data exfiltration. An insider threat isn’t necessarily a user willfully causing harm: according to Fortinet’s 2019 Insider Threat Report, from the organizations surveyed 71% were concerned about a careless user causing an accidental Continue reading
Protecting your APIs from abuse and data exfiltration


API traffic is growing fast. Last year alone it grew 300% faster at our edge than web traffic. Because APIs power mobile and web applications, transmitting instructions as diverse as “order a pizza from my favourite restaurant using this credit card” or “place a cryptocurrency trade and these are my personal details”, they are ripe for data theft and abuse. Data exposure is listed as one of the top threats for API traffic by OWASP; this includes data leaks and exfiltration from origin responses (API Security TOP 10 threats 2019). The increase in API traffic and more frequent data attacks call for new security solutions.
Cloudflare’s security toolkit had always been designed to protect web and API traffic. However, after talking to hundreds of customers we realised that there is a need for easily deployed and configured security tools for API traffic in a single interface. To meet this demand, in October 2020 we launched API ShieldTM, a new product aimed at bringing together all security solutions designed for API traffic. We started by providing mTLS authentication to all Cloudflare users free of charge, gRPC support and Schema Validation in Beta. During the launch we laid Continue reading
Browser Isolation for teams of all sizes

Every Internet-connected organization relies on web browsers to operate: accepting transactions, engaging with customers, or working with sensitive data. The very act of clicking a link triggers your web browser to download and execute a large bundle of unknown code on your local device.

IT organizations have always been on the back foot while defending themselves from security threats. It is not a question of ‘if’, but ‘when’ the next zero-day vulnerability will compromise a web browser. How can IT organizations protect their users and data from unknown threats without over-blocking every potential risk? The solution is to shift the burden of executing untrusted code from the user’s device to a remote isolated browser.
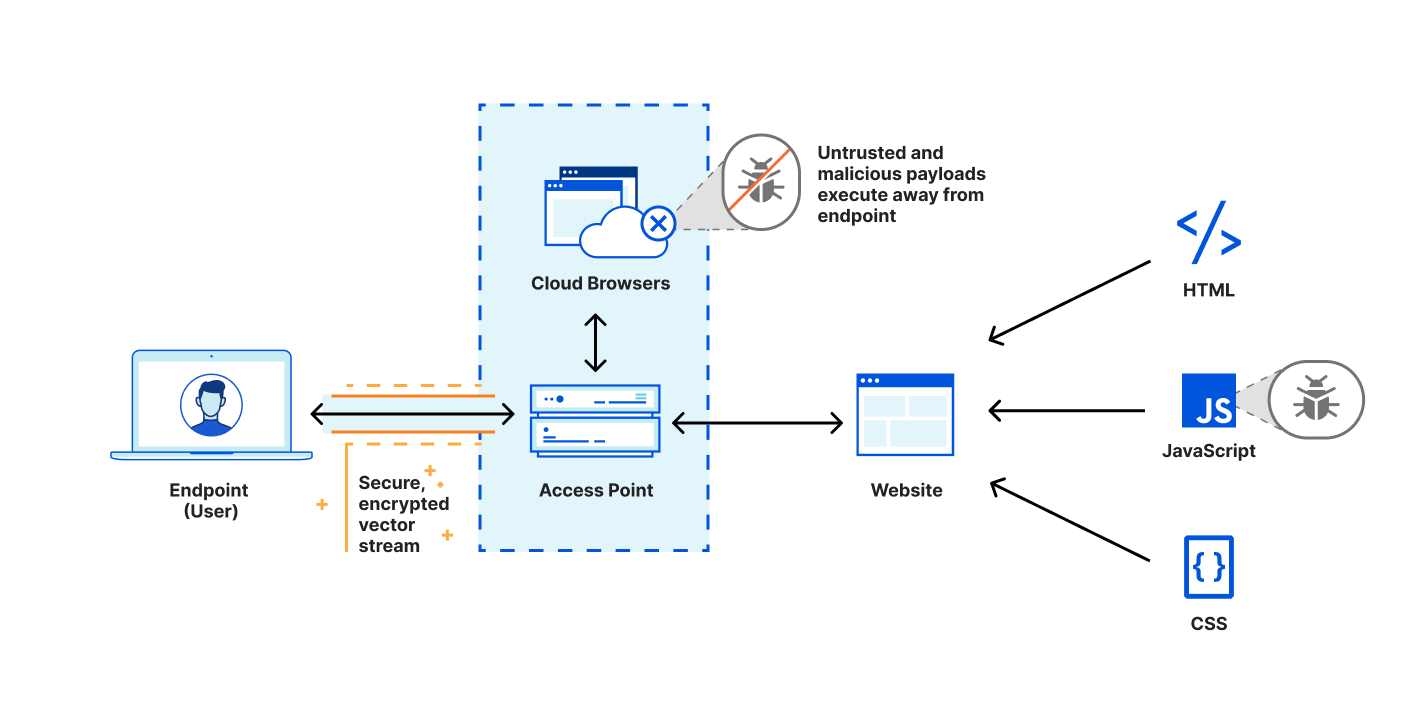
Bringing Remote Browser Isolation to teams of any size
Today we are excited to announce that Cloudflare Browser Isolation is now available within Cloudflare for Teams suite of zero trust security and secure web browsing services as an add-on. Teams of any size from startups to large enterprises can benefit from reliable and safe browsing without changing their preferred web browser or setting up complex network topologies.
Remote Browsers must be reliable
Running sensitive workloads in secure environments is nothing new, and Remote Browser Isolation (RBI) Continue reading
Anatomy of a Targeted Ransomware Attack
Imagine your most critical systems suddenly stop operating, bringing your entire business to a screeching halt. And then someone demands a ransom to get your systems working again. Or someone launches a DDoS against you and demands ransom to make it stop. That’s the world of ransomware and ransom DDoS.
So what exactly is ransomware? It is malicious software that encrypts files on computers making them useless until they are decrypted. In some cases, ransomware could even corrupt and destroy data. A ransom note is then placed on compromised systems with instructions to pay a ransom in exchange for a decryption utility that can be used to restore encrypted files. Payment is often in the form of Bitcoin or other cryptocurrency.
Recently, Cloudflare onboarded and protected a Fortune 500 customer from a targeted Ransom DDoS (RDDoS) attack -- a different type of extortion attack.
Prior to joining Cloudflare, I responded to and investigated a large number of data breaches and ransomware attacks for clients across various industries, including healthcare, financial, and education, to name a few. I’ve been in the trenches analyzing these types of attacks and working closely with clients to help them recover from the aftermath.
In this Continue reading
Announcing antivirus in Cloudflare Gateway

Today we’re announcing support for malware detection and prevention directly from the Cloudflare edge, giving Gateway users an additional line of defense against security threats.
Cloudflare Gateway protects employees and data from threats on the Internet, and it does so without sacrificing performance for security. Instead of backhauling traffic to a central location, Gateway customers connect to one of Cloudflare’s data centers in 200 cities around the world where our network can apply content and security policies to protect their Internet-bound traffic.
Last year, Gateway expanded from a secure DNS filtering solution to a full Secure Web Gateway capable of protecting every user’s HTTP traffic as well. This enables admins to detect and block not only threats at the DNS layer, but malicious URLs and undesired file types as well. Moreover, admins now have the ability to create high-impact, company-wide policies that protect all users with one click, or they can create more granular rules based on user identity.
Earlier this month, we launched application policies in Cloudflare Gateway to make it easier for administrators to block specific web applications. With this feature, administrators can block those applications commonly used to distribute malware, such as public cloud file storage.
These Continue reading