Day Two Cloud 018: “I’m Not As Terrified As I Was” – Making The Transition To Cloud And DevOps
Today's Day Two Cloud podcast explores the struggle of transitioning from traditional infrastructure ops to the public cloud using DevOps principles and new tools. My guest is Aaron Strong, a cloud architect. We talk about how to skill up quickly, where to start, when and where to ask for help, and more.
The post Day Two Cloud 018: “I’m Not As Terrified As I Was” – Making The Transition To Cloud And DevOps appeared first on Packet Pushers.
Day Two Cloud 018: “I’m Not As Terrified As I Was” – Making The Transition To Cloud And DevOps
Today's Day Two Cloud podcast explores the struggle of transitioning from traditional infrastructure ops to the public cloud using DevOps principles and new tools. My guest is Aaron Strong, a cloud architect. We talk about how to skill up quickly, where to start, when and where to ask for help, and more.Cloudflare’s Approach to Research


Cloudflare’s mission is to help build a better Internet. One of the tools used in pursuit of this goal is computer science research. We’ve learned that some of the difficult problems to solve are best approached through research and experimentation to understand the solution before engineering it at scale. This research-focused approach to solving the big problems of the Internet is exemplified by the work of the Cryptography Research team, which leverages research to help build a safer, more secure and more performant Internet. Over the years, the team has worked on more than just cryptography, so we’re taking the model we’ve developed and expanding the scope of the team to include more areas of computer science research. Cryptography Research at Cloudflare is now Cloudflare Research. I am excited to share some of the insights we’ve learned over the years in this blog post.
Cloudflare’s research model
| Principle | Description |
|---|---|
| Team structure | Hybrid approach. We have a program that allows research engineers to be embedded into product and operations teams for temporary assignments. This gives people direct exposure to practical problems. |
| Problem philosophy | Impact-focused. We use our expertise and the expertise of partners in industry and academia to select projects that Continue reading |
Testing at Juniper NXTWORK
Earlier this week I did a post on Juniper NXTWORK and talked about the event. There is a lot going …
The post Testing at Juniper NXTWORK appeared first on Fryguy's Blog.
DC 14. Real case of using ZTP to setup Mellanox SN 2010 with Cumulus Linux.
Hello my friend,
Earlier in this year we’ve discussed zero touch provisioning using the Data Centre Fabric Enabler Infrastructure. As always in my articles, I’ve used wonderful VM images, which are freely available on the Internet. Nevertheless, when you deal with real boxes, various caveats might arise. Today we’ll review how to bring Mellanox switch SN 2010 to the operational state running Cumulus Linux using the ZTP framework I’ve already created.

2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Thanks
Special thanks for Avi Alkobi from Mellanox and Pete Crocker and Attilla de Groot from Cumulus for providing me the Mellanox switch and Cumulus license for the tests.
Disclaimer
It is always exciting to do something for the first time. I have never written about any particular network device. Mostly because I always separate, as far as it is possible, the relationship between my current employer, which is The Hut Group as of today, and my blog. And this is the justification, why Continue reading
Worth Reading: TCP MSS Values in the Wild
In Never-Ending Story of IP Fragmentation I described how you could use TCP Maximum Segment Size to minimize the impact of IP fragmentation and PMTUD blackholes (more details on TCP MSS clamping)… but one has to wonder how people use TCP MSS in the wild and what values you might see.
As is often the case, Geoff Houston found a way to measure them, and published the answer: TCP MSS Values
AT&T CEO Downplays Threat From Activist Investor Group
AT&T CEO Randall Stephenson described the series of demands made by an activist investor...
GitLab Inhales $268M Series E, Valuation Hits $2.75B
The new valuation inches the company closer to the $7.5 billion Microsoft spent to acquire rival...
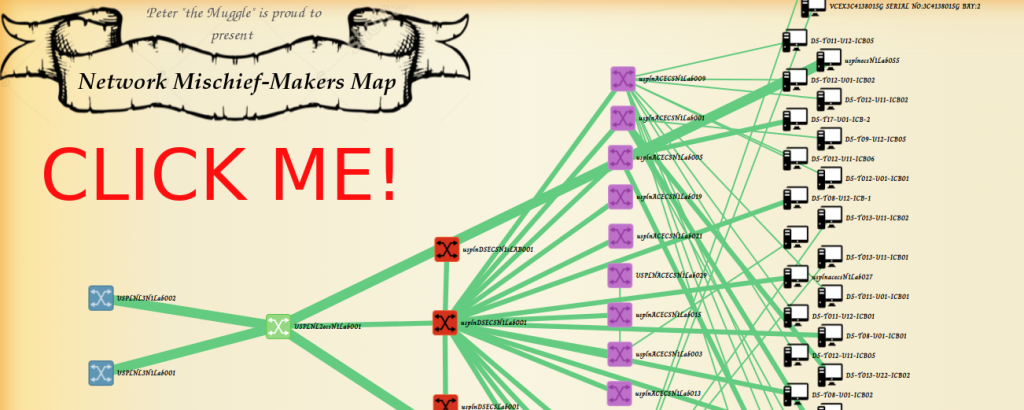
[mini-update] Network Topology Visualization #2 – Using SNMP as data source and enhanced visuals
After a longer break, I managed to get back to my small visualization experiment from last time, and improve it a little. Firstly, the NETCONF interface was switched for a more standard SNMP one, even if that is not as cutting edge anymore.
So without keeping you waiting, here is firs the visualization example, as you can see I was playing here a little and got inspired by the Mischief-makers map from Harry Potter. Of course if you do not like the visuals just re-do the CSS to get rid of it.
Also, this time I made the code public using the much more common github.com here.
Usage/Tutorial
Once you download this project from github, you will find several files in the directory, your starting point are the two configuration files called:
- config.ini – holds SNMP configuration like community string and a list of IPs for each network device to be SNMP queried
- pyconfig.py – holds low level configuration on how to visualize the data recieved and how to order the devices detected into layers
Lets start with the config.ini, which is much smaller. Here is an example.
[DEFAULT] SnmpVersion = 2c SnmpCommunityString Continue reading
VMworld US 2019: Networking and Security Recap
VMworld US 2019 has come to a close. If you didn’t attend, don’t worry as we still have VMworld Europe right around the corner. Join us November 4-7, 2019 to hear experts discuss cloud, networking and security, digital workspace, digital trends and more! Register for VMworld Europe now.
Below is a quick recap and resources to check out from VMworld US 2019.
Stats from VMworld US 2019
- For networking and security we delivered 91 Breakout Sessions + 2 Showcase Keynotes
- VMware NSX-T – Getting Started was the second most played video post-VMworld!
- VMware NSX was the #1 attended Hands-On-Lab (HOL), and there was a total of 1,922 labs taken on NSX
- 17,277 NSX networks were created at HOL
- VMware NSX Intelligence won TechTarget’s Best of Show award – Judge’s Choice for Disruptive Technology

Congratulations to our NSX Intelligence team: Anirban Sengupta, Umesh Mahajan, Farzad Ghannadian, Kausum Kumar, Catherine Fan and Ray Budavari.

Surprise guest Michael Dell stopped by the Solutions Exchange to check out demos of what’s new from the networking and security business unit demoed by Chris McCain.
Technical Networking and Security Sessions from VMworld US 2019
Below is a list of sessions that jump into the NSX Continue reading
VMware Adds Oracle to Its Growing Cloud Harem
This means VMware’s software stack will now run on all major public clouds including AWS, Azure,...
Cloudian Welcomes New Edgy Unit, Edgematrix
Cloudian announced the launch of Edgematrix, its edge analytics platform that will use HyperStore...
Arista Updates CloudVision, Integrates With Red Hat Ansible
Arista announced a bevy of upgrades to the company's management plane software, including support...
SK Telecom Boasts 5G Standalone First in South Korea
The operator is no stranger to early adoption — it previously laid claim to the world’s first...