TL002: The Philosophical Roots of Leadership
On this episode of Technically Leadership, we talk about the philosophical underpinnings of leadership. We discuss what it means to hold and drive a vision for a technical organization, how to build a strong team culture, handling layoffs and letting people go, and exploring what philosophy can teach us about leadership. Guest Matt Butcher, CEO... Read more »Common Services VRF with EVPN Control Plane
After discovering that some EVPN implementations support multiple transit VNI values in a single VRF, I had to check whether I could implement a common services L3VPN with EVPN.
TL&DR: It works (on Arista cEOS)1.
Here are the relevant parts of a netlab lab topology I used in my test (you can find the complete lab topology in netlab-examples GitHub repository):
NAN072: Exploring Internet2’s Network Automation for University and Research Networks
On today’s episode we delve into Internet2’s mission to advance research and education through high-speed connectivity. University and research networks may have more complicated designs, requirements, and restrictions than you’d expect. We talk about these challenges, along with innovative network automation solutions. The discussion emphasizes the collaborative, member-driven approach of Internet2 and its commitment to... Read more »Not All OSPF Inter-area Traffic Traverses Interfaces In Area 0
Everyone knows that OSPF is a link state protocol. Those that study also discover that OSPF behaves like distance vector between areas as Type-1- and Type-2 LSAs are not flooded between areas, but rather summarized in Type-3 LSAs. This means that OSPF is a logical star, or hub with spokes, where Area 0 is the backbone and all other areas must connect to Area 0. This is shown below:

With this topology, since all the areas only connect to the backbone area, traffic between areas must traverse the backbone:

We learn about this behavior in literature where there is a very straight forward topology where each ABR is only attached to one area beyond the backbone. Such a topology is shown below:

In such a topology, traffic between RT04 and RT05 has to traverse the backbone. This is shown below:

However, what if you have a topology which is not as clear cut? Where an ABR attaches to multiple areas? This is what we will explore in this post. We’ll be using the topology below:

In this topology, RT02 and RT03 are ABRs. RT02 is attached to both Area 1 and Area 2 in addition to the backbone, while RT03 Continue reading
PP028: Can SecOps and NetOps Work Together?
IT tends to divide itself by job function and technological specialization, especially as technology gets more complex. However, each IT domain is part of a larger system, and these systems require coordination and cooperation to operate effectively. On today’s Packet Protector we look at how and why Security Operations (SecOps) and Network Operations (NetOps) should... Read more »HS081: What’s Your Strategic Plan for AI Infrastructure?
AI seems to be changing everything, including your IT infrastructure. Do you have a strategic plan for your AI infrastructure? Today we discuss the merits and challenges of cloud computing, on-premises solutions, hybrid models, and edge computing along with the importance of low latency for real-time AI applications and the potential of edge computing in... Read more »Multivendor EVPN Just Works
Shipping netlab release 1.9.0 included running 36 hours of integration tests, including fifteen VXLAN/EVPN tests covering:
- Bridging multiple VLANs
- Asymmetric IRB, symmetric IRB, central routing, and running OSPF within an IRB VRF.
- Layer-3 only VPN, including routing protocols (OSPF and BGP) between PE-router and CE-routers
- All designs evangelized by the vendors: IBGP+OSPF, EBGP-only (including reusing BGP AS number on leaves), EBGP over the interface (unnumbered) BGP sessions, IBGP-over-EBGP, and EBGP-over-EBGP.
All tests included one or two devices under test and one or more FRR containers1 running EVPN/VXLAN with the devices under test. The results were phenomenal; apart from a few exceptions, everything Just Worked™️.
HN746: Going Deep on OSPF Route Filtering
On today’s episode we delve into OSPF filtering. That is, how to filter routes from a device’s routing table in an OSPF environment. This is a tricky business, because OSPF requires an identical database on every device in an OSPF area. That means you can’t stop announcing a route from one OSPF router because you... Read more »NB492: AMD Spends Big For Engineering Talent; FCC Cracks Down on AI-Faked Robocalls
Take a Network Break! A US appeals court will let a privacy lawsuit against Google go forward, striking telecom workers are a reminder to test your resiliency planning, and AMD spends nearly $5 billion to acquire systems engineering talent from ZT Systems. Juniper Networks offers deep discounts and other enticements to get network engineers to... Read more »Tech Bytes: Why It’s Time To Say Goodbye To NFS (Sponsored)
Today on the Tech Bytes podcast we talk cloud storage. More specifically, we dive into why it’s time for NFS to sail off into the sunset, particularly for cloud datasets. Our guest is Tom Lyon, an industry legend who has delivered a talk entitled “NFS Must Die.” We talk with Tom about the strengths and weaknesses of NFS, the... Read more »August Rule 11 Academy Update
I’ve been working on new material over at Rule 11 Academy. This month’s posts are:
- BGP Route Reflector Lab
- The Clos Fabric (history)
- The Default Free Zone
- Network Addresses
- BGP Policy Entrance Selection (2)
- Interview Rubric Sample
- BGP Policy Entrance Select (1)
- Interviewing Background
This brings us up to a total of 39 lessons. Each lesson should be about 15 minutes, so about 10 hours of material so far. The trial membership will take you through the end of the year. After the first of the year, the trial membership will last 2 months.
Repost: The Benefits of SRv6
I love bashing SRv6, so it’s only fair to post a (technical) counterview, this time coming as a comment from Henk Smit.
There are several benefits of SRv6 that I’ve heard of.
Network CI/CD Pipeline – What’s the Point?

Hi all, welcome to the 'Network CI/CD' blog series. To kick things off, let's ask the question, "Why do we even need a CI/CD pipeline for networks?" Instead of diving straight into technical definitions or showing you how to build a CI/CD pipeline, which might make you lose interest, we’ll focus on the reasons behind it. Why should network teams even consider implementing CI/CD?
In this post, we’ll talk about the benefits and the problems it solves, so you can see why it's worth learning. Let's get to it.
Making Network Changes - The Traditional Way
Even though I call it the “traditional way,” most of us (myself included) still make changes via the CLI. So, let’s imagine you and two colleagues are managing a campus network with 10 access switches. One of your tasks is to configure VLANs on all of Continue reading
Hedge 240: Build or Buy?
Many network operators think the idea of building rather than buying is something that’s out of reach–but is it? Join Steve Dodd, Eyvonne, Tom, and Russ as we discuss the positive and negative aspects of build versus buy, what operators get wrong, and what operators don’t often expect.
TNO001: Your Team Matters as Much as Your Tech and Tools
Your team is just as important as your tech and tools in any environment, including NetOps. Garrett Nowak, Senior Director of Network Architecture at 11:11 Systems shares his journey from tier one help desk to a leadership role. He discusses the importance of teamwork, community, and effective leadership in network operations and how he works... Read more »Delegation And You

I once again loved this episode of the Art of Network Engineering featuring Mike Bushong. He is a very astute judge of character as well as how to apply social skills to your tech role. Definitely listen to the above episode if you’re interested in countering cognitive biases.
In the episode, he told a great story of how he had a pivotal career moment with one of his managers that led to some important introspection. I won’t tell his story but the summary is that he had taken on way too much work and way too many roles and he blew up at his manager because of the stress. She leveled him with a quote that rang true for me:
“No one knows everything you’re working on. They just see that the thing that’s important to them is late.”
That’s not the verbatim quote but that’s how I remember it. It’s definitely something that I’ve been thinking about since the previous episode when he mentioned it the first time.
Load Bearing and Busting
The odds are good that we’re all doing way too many things right now. Whether it’s doing more work in our role or taking on way Continue reading
Exploring Internet and security trends during the 2024 U.S. Democratic National Convention
The 2024 Democratic National Convention (DNC) wrapped up on Thursday, August 22, in Chicago, Illinois. Since our blog post about Internet trends during the first presidential debate between President Joe Biden and former President Donald Trump on June 27, the presidential race has fundamentally changed. We experienced the attempted assassination of Trump, the Republican National Convention (RNC), Biden’s late July withdrawal from the race, and Vice President Kamala Harris being selected as the Democratic nominee and participating in her party’s convention this week. Here, we’ll examine trends more focused on DNS traffic to news and candidate-related sites, cyberattacks targeting politically-related organizations, and spam and malicious emails mentioning the candidates’ names.
Over 60 more national elections are scheduled to take place across the world this year, and we have been monitoring them as they occur. Our goal is to provide a neutral analysis of their impact on Internet behavior, which often mirrors human activities. Significant events, such as the total eclipse in Mexico, the United States, and Canada, and the Paris 2024 Olympics, have had an impact on Internet traffic. Our ongoing election report on Cloudflare Radar includes updates from recent elections in the European Union, France, Continue reading
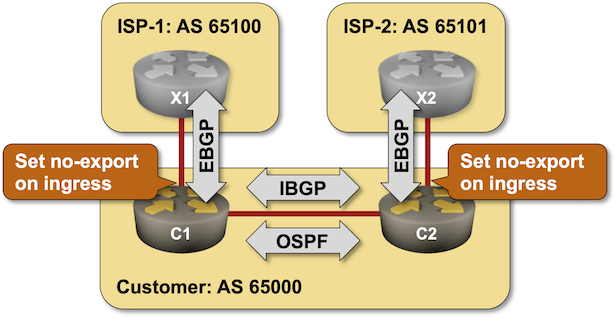
Using No-Export Community to Filter Transit Routes
The very first BGP Communities RFC included an interesting idea: let’s tag paths we don’t want to propagate to other autonomous systems. For example, the prefixes received from one upstream ISP should not be propagated to another upstream ISP (sadly, things don’t work that way in reality).
Want to try out that concept? Start the Using No-Export Community to Filter Transit Routes lab in GitHub Codespaces.