Advancing Threat Intelligence: JA4 fingerprints and inter-request signals

For many years, Cloudflare has used advanced fingerprinting techniques to help block online threats, in products like our DDoS engine, our WAF, and Bot Management. For the purposes of Bot Management, fingerprinting characteristic elements of client software help us quickly identify what kind of software is making an HTTP request. It’s an efficient and accurate way to differentiate a browser from a Python script, while preserving user privacy. These fingerprints are used on their own for simple rules, and they underpin complex machine learning models as well.
Making sure our fingerprints keep pace with the pace of change on the Internet is a constant and critical task. Bots will always adapt to try and look more browser-like. Less frequently, browsers will introduce major changes to their behavior and affect the entire Internet landscape. Last year, Google did exactly that, making older TLS fingerprints almost useless for identifying the latest version of Chrome.
Cloudflare network fingerprinting techniques
These methods are instrumental in accurately scoring and classifying bots, enhancing security measures, and enriching data analytics capabilities. Below are some examples of the fingerprinting techniques we have implemented over the years:
HTTP Signature: The HTTP Signature technique involves analyzing HTTP Continue reading
Response: The Usability of VXLAN
Wes made an interesting comment to the Migrating a Data Center Fabric to VXLAN blog post:
The benefit of VXLAN is mostly scalability, so if your enterprise network is not scaling… just don’t. The migration path from VLANs is to just keep using VLANs. The (vendor-driven) networking industry has a huge blind spot about this.
Paraphrasing the famous Dinesh Dutt’s Autocon1 remark: I couldn’t disagree with you more.
How Walking Improved My Daily Productivity?

Recently, walking has become a habit for me, and I absolutely love taking short walks while listening to music or podcasts. It helps me rest and recover mentally, emotionally, and physically. Walking clears my mind and helps me process my emotions and thoughts. In this post, I will cover the benefits I experience from walking and how it improves my productivity.
Taking a Break with a Walk
Every time I feel stressed or need a break from everything around me, I go for a walk. It's a simple act, but it refreshes me more than anything else. These quiet moments alone with my thoughts are important for recharging and gaining a new perspective on whatever is bothering me. Walking not only gives me the physical exercise I need but also eases my mind and allows me to return to my tasks with renewed energy and focus.
AI/ML Networking: Part-IV: Convolutional Neural Network (CNN) Introduction
Feed-forward Neural Networks are suitable for simple tasks like basic time series prediction without long-term relationships. However, FNNs is not a one-size-fits-all solution. For instance, digital image training process uses pixel values of image as input data. Consider training a model to recognize a high resolution (600 dpi), 3.937 x 3.937 inches digital RGB (red, green, blue) image. The number of input parameters can be calculated as follows:
Width: 3.937 in x 600 ≈ 2362 pixels
Height: 3.937 in x 600 ≈ 2362 pixels
Pixels in image: 2362 x 2362 = 5,579,044 pixels
RGB (3 channels): 5,579,044 pxls x 3 channels = 16 737 132
Total input parameters: 16 737 132
Memory consumption: ≈ 16 MB
FNNs are not ideal for digital image training. If we use FNN for training in our example, we fed 16,737,132 input parameters to the first hidden layer, each having unique weight. For image training, there might be thousands of images, handling millions of parameters demands significant computation cycles and is a memory-intensive process. Besides, FNNs treat each pixel as an independent unit. Therefore, FNN algorithm does not understand dependencies between pixels and cannot recognize the same image if it shifts within the frame. Besides, FNN does not detect edges and other crucial details.
A better model for training digital images is Convolutional Neural Networks (CNNs). Unlike in FFN neural networks where each neuron has a unique set of weights, CNNs use the same set of weights (Kernel/Filter) across different regions of the image, which reduces the number of parameters. Besides, CNN algorithm understands the pixel dependencies and can recognize patterns and objects regardless of their position in the image.
The input data processing in CNNs is hierarchical. The first layer, convolutional layers, focuses on low-level features such as textures and edges. The second layer, pooling layer, captures higher-level features like shapes and objects. These two layers significantly reduce the input data parameters before they are fed into the neurons in the first hidden layer, the fully connected layer, where each neuron has unique weights (like FNNs).
LLM for configuration Generation – No jinja2 Template, No problem
Disclaimer: All Writings And Opinions Are My Own And Are Interpreted Solely From My Understanding. Please Contact The Concerned Support Teams For A Professional Opinion, As Technology And Features Change Rapidly.
And No! This can’t replace the accuracy of static templating configurations. This helps us to better understand and develop the templates. This was almost rocket science to me when I first got to know about them.
Most modern day deployments have some sort of variable files and template files (YAML and Jinja2). These can be intimidating. It was mysterious. When I first looked at them years ago, I found them confusing. Today, with LLM you don’t have to really be worried about how to generate it. The parser in itself can come up on the fly to generate popular networking gear. More than that, it’s more than willing to take in the data to spit out whatever configuration is needed.

Lets say I just appreciated the way the configuration files are generated today. I wanted to quickly see if an LLM can generate the config. It also do the deployment for me. Then it helps me with some pre-checks, all without writing the code.
Let’s not go too far Continue reading
HN744: How BackBox Helps You Mitigate CVEs for Network Devices (Sponsored)
Today we explore a network automation use case for configuration compliance in the face of never-ending common vulnerabilities and exposures, or CVEs. If you can automate that compliance, you have a shot at keeping pace with the bots and attackers attempting to exploit those CVEs and breaching your network. Our guest is Rekha Shenoy, CEO... Read more »Setting Up Palo Alto Firewall in VMWare Workstation

Hi all, welcome back to another Palo Alto Firewall blog post. In this post, we will explore how to add a VM-Series Firewall into VMWare Workstation, set up the interfaces, and make initial configurations. This guide is designed for beginners who want to try the Palo Alto Firewall in their home lab but aren’t sure where to start.
Download the Image from the Palo Alto Portal
The first step is to download the image from the Palo Alto Customer Support Portal. To do this, you will need a valid support contract, as sharing the image with others is not allowed. I understand this can be frustrating, as it may seem like vendors make it difficult for users to access and use their products. However, if you use Palo Alto products at work, you might be able to download it there.
To download the required file, navigate to Updates > Software Updates in the portal. Look for the PA-VM section and download the file named PA-VM-ESX-10.1.3.ova (note that the version might differ).
Prepare VMWare Workstation
When setting up the Palo Alto Firewall in VMWare Workstation, I usually allocate 8 GB of RAM, 60 GB of disk space, Continue reading
TNO000: Announcing Total Network Operations – a New Podcast for Network Operators
Welcome to Total Network Operations, the podcast dedicated to the hardworking network operators who keep the bitpipes running smoothly. We focus on sharing best practices, the operations tool stack, and engage with vendors and solution providers to get insights into new technologies and tools so you can make informed decisions for your ops environment. Podcast... Read more »Why SecureCRT Works Best for Me?

What’s one tool you find is irreplaceable as a Network Engineer? For me, it’s SecureCRT. I’ve relied on it for over eight years and have picked up plenty of tricks along the way. Whenever I start a new job, I always make a case for the business to invest in SecureCRT licenses. Once my colleagues see what it can do, they often decide to get their own. In this blog post, I’ll walk you through some of its key features. Hopefully, you’ll see the benefits and maybe even consider trying it out for yourself.
Why SecureCRT When You Have Other Free Tools?
But you might wonder why you should pay for SecureCRT when there are free tools available. That's a fair question. If you're on Windows, tools like PuTTY are readily available, and I believe Windows 11 even comes with its own SSH client. For those on MacOS or Linux, the native terminal app usually does the job. There are also plenty of other free tools out there, like iTerm or Tmux. I’ve tried most of them, but I still prefer SecureCRT for the following reasons.
IPB157: IPv6 Adoption Update and Transition Challenges
Nathan Sherrard shares insights from his Cisco Live US sessions on today’s show. We discuss the current state of IPv6 adoption, adoption challenges, and the strategic importance of transitioning to IPv6. Nathan rounds out the show with IPv6 topics worth keeping an eye on. Episode Guest: Nathan Sherrard, Sales Engineer, Cisco Nathan Sherrard is a... Read more »Calico monthly roundup: July 2024
Welcome to the Calico monthly roundup: July edition! From open source news to live events, we have exciting updates to share—let’s get into it!
Exclusive: Cloud and container security leaders round table and dinner
An exclusive, invite-only round table and dinner designed specifically for cloud and container security leaders. This intimate gathering will discuss today’s most pressing issues facing cloud and container security. |
Your Guide to Observability
This guide explains what observability is and shows you how to use Calico’s observability tools. With these tools, you can find and troubleshoot issues with workload communications, performance, and operations in a Kubernetes cluster. |
Customer case study: Playtech
Calico seamlessly integrated with Amazon EKS GitOps model to enhance Playtech’s application security. Read the case study to learn more. |
Open source news
Calico Live stream: Mitigating RCE zero-day attacks with Calico security policies – This live session on July 31, 2024 will examine the capabilities of Calico security policies to mitigate RCE attacks in a cloud-native environment. You can watch the live session on YouTube or LinkedIn.
Calico enhancements
- Calico v3.27.4 is out and here is why you should install or update your Calico instance:
Introducing Automatic SSL/TLS: securing and simplifying origin connectivity
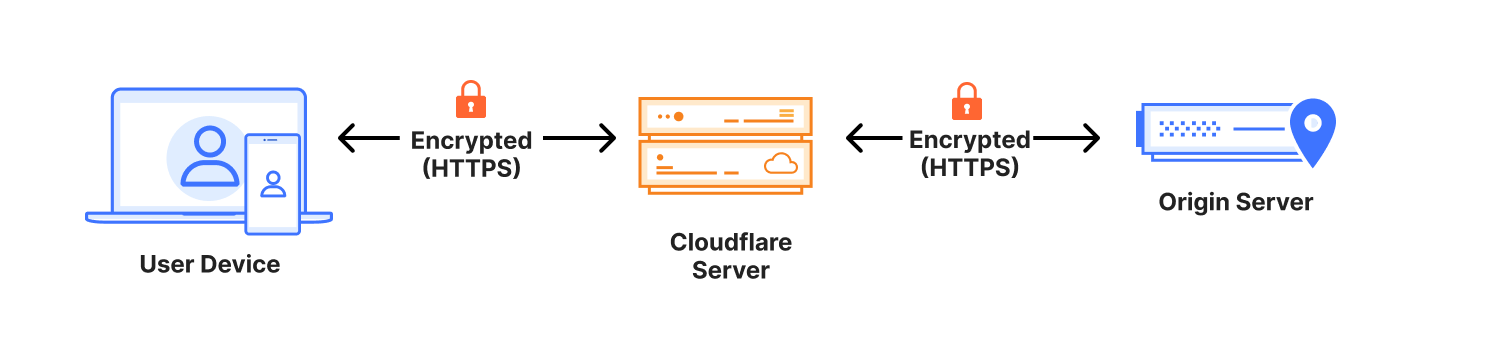
During Birthday Week 2022, we pledged to provide our customers with the most secure connection possible from Cloudflare to their origin servers automatically. I’m thrilled to announce we will begin rolling this experience out to customers who have the SSL/TLS Recommender enabled on August 8, 2024. Following this, remaining Free and Pro customers can use this feature beginning September 16, 2024 with Business and Enterprise customers to follow.
Although it took longer than anticipated to roll out, our priority was to achieve an automatic configuration both transparently and without risking any site downtime. Taking this additional time allowed us to balance enhanced security with seamless site functionality, especially since origin server security configuration and capabilities are beyond Cloudflare's direct control. The new Automatic SSL/TLS setting will maximize and simplify the encryption modes Cloudflare uses to communicate with origin servers by using the SSL/TLS Recommender.
We first talked about this process in 2014: at that time, securing connections was hard to configure, prohibitively expensive, and required specialized knowledge to set up correctly. To help alleviate these pains, Cloudflare introduced Universal SSL, which allowed web properties to obtain a free SSL/TLS certificate to enhance the security of connections between browsers Continue reading
Celebrating one year of Project Cybersafe Schools
August 8, 2024, is the first anniversary of Project Cybersafe Schools, Cloudflare’s initiative to provide free security tools to small school districts in the United States.
Cloudflare announced Project Cybersafe Schools at the White House on August 8, 2023 as part of the Back to School Safely: K-12 Cybersecurity Summit hosted by First Lady Dr. Jill Biden. The White House highlighted Cloudflare’s commitment to provide free resources to small school districts in the United States. Project Cybersafe Schools supports eligible K-12 public school districts with a package of Zero Trust cybersecurity solutions – for free, and with no time limit. These tools help eligible school districts minimize their exposure to common cyber threats.
Cloudflare’s mission is to help build a better Internet. One way we do that is by supporting organizations that are particularly vulnerable to cyber threats and lack the resources to protect themselves through projects like Project Galileo, the Athenian Project, the Critical Infrastructure Defense Project, Project Safekeeping, and most recently, Project Secure Health.
Schools are vulnerable to cyber attacks
In Q2 2024, education ranked 4th on the list of most attacked industries. Between 2016 and 2022, there were 1,619 K-12 cyber incidents. Continue reading
Introducing Automatic SSL/TLS: securing and simplifying origin connectivity
During Birthday Week 2022, we pledged to provide our customers with the most secure connection possible from Cloudflare to their origin servers automatically. I’m thrilled to announce we will begin rolling this experience out to customers who have the SSL/TLS Recommender enabled on August 8, 2024. Following this, remaining Free and Pro customers can use this feature beginning September 16, 2024, with Business and Enterprise customers to follow.
Although it took longer than anticipated to roll out, our priority was to achieve an automatic configuration both transparently and without risking any site downtime. Taking this additional time allowed us to balance enhanced security with seamless site functionality, especially since origin server security configuration and capabilities are beyond Cloudflare's direct control. The new Automatic SSL/TLS setting will maximize and simplify the encryption modes Cloudflare uses to communicate with origin servers by using the SSL/TLS Recommender.
We first talked about this process in 2014: at that time, securing connections was hard to configure, prohibitively expensive, and required specialized knowledge to set up correctly. To help alleviate these pains, Cloudflare introduced Universal SSL, which allowed web properties to obtain a free SSL/TLS certificate to enhance the security of connections between browsers and Continue reading
Celebrating one year of Project Cybersafe Schools

August 8, 2024, is the first anniversary of Project Cybersafe Schools, Cloudflare’s initiative to provide free security tools to small school districts in the United States.
Cloudflare announced Project Cybersafe Schools at the White House on August 8, 2023 as part of the Back to School Safely: K-12 Cybersecurity Summit hosted by First Lady Dr. Jill Biden. The White House highlighted Cloudflare’s commitment to provide free resources to small school districts in the United States. Project Cybersafe Schools supports eligible K-12 public school districts with a package of Zero Trust cybersecurity solutions – for free, and with no time limit. These tools help eligible school districts minimize their exposure to common cyber threats.
Cloudflare’s mission is to help build a better Internet. One way we do that is by supporting organizations that are particularly vulnerable to cyber threats and lack the resources to protect themselves through projects like Project Galileo, the Athenian Project, the Critical Infrastructure Defense Project, Project Safekeeping, and most recently, Project Secure Health.
Schools are vulnerable to cyber attacks
In Q2 2024, education ranked 4th on the list of most attacked industries. Between 2016 and 2022, there were 1,619 K-12 cyber incidents. Continue reading
Hedge 238: What Went Wrong? (Crowdstrike)
The massive failure resulting from a failed update to 8.5 million Windows hosts by Crowdstrike will live in Internet history for years to come. The failure will be studied by engineering teams and college classes to understand what went wrong and how we can stop this from happening in the future. Derick Winkworth (@cloudtoad), Eyvonne Sharp, Tom Ammon, and Russ White hang out at the hedge to talk about what happened and lessons learned from a network engineering perspective.
download
Crowdstrike released a detailed description of the problematic update here.
Building Layer-3-Only EVPN Lab
A few weeks ago, Roman Dodin mentioned layer-3-only EVPNs: a layer-3 VPN design with no stretched VLANs in which EVPN is used to transport VRF IP prefixes.
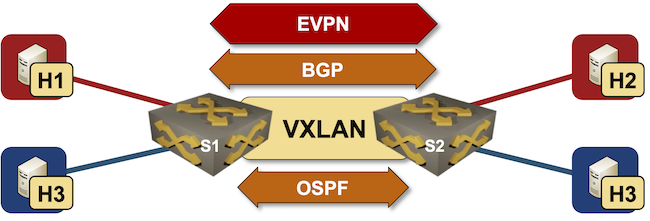
The reality is a bit muddier (in the VXLAN world) as we still need transit VLANs and router MAC addresses; the best way to explore what’s going on behind the scenes is to build a simple lab.
