History of Networking: Pseudowires
In this episode of the History of Networking, Donald Sharp and I talk to Luca Martini about the origins of pseudowires—one of the more interesting innovations in the use of MPLS.
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
Short Take – Peering and Resources in the DFZ
In this Network Collective Short Take, Russ White and Tom Ammon talk through different types of Internet peering and how they are used.
The post Short Take – Peering and Resources in the DFZ appeared first on Network Collective.
Telefónica Takes AURA AI Program to More Markets
 The “cognitive intelligence” platform was developed with Microsoft as a way to use AI to help...
The “cognitive intelligence” platform was developed with Microsoft as a way to use AI to help...
You Don’t Want To Be A Rock Star

When I say “rock star”, you probably have all kinds of images that pop up in your head. Private planes, penthouse suites, grand stages, and wheelbarrows full of money are probably on that list somewhere. Maybe you’re a purist and you think of someone dedicated to the craft of entertaining the masses and trying to claw their way to fame one note at a time. But I’m also sure in both of those cases you also think about the negative aspects of being a rock star. Like ego. And lack of humility. I want to touch on some of that as it pertains to our jobs and our involvement in the community.
Great Like Elvis. Without The Tassels.
The rock star mentality at work is easy to come by. Perhaps you’re very good at what you do. You may even be the best at your company or even at the collection of companies that are your competitors. You’re the best senior architect there is. You know the products and the protocols and you can implement a complex project with your eyes closed. That’s how people start looking at you. Larger than life. The best. One of a kind.
And that Continue reading
Heavy Networking 450: Getting To Know The Open-Source VyOS Network OS
Today's Heavy Networking digs into VyOS, an open-source, Linux-based network OS for routing. Forked from the Vyatta Core, VyOS includes a full routing stack and features including firewalling, VPN, and more. Guest Yuriy Andamasov, the project coordinator, gives us a guided tour.
The post Heavy Networking 450: Getting To Know The Open-Source VyOS Network OS appeared first on Packet Pushers.
Faster script loading with BinaryAST?
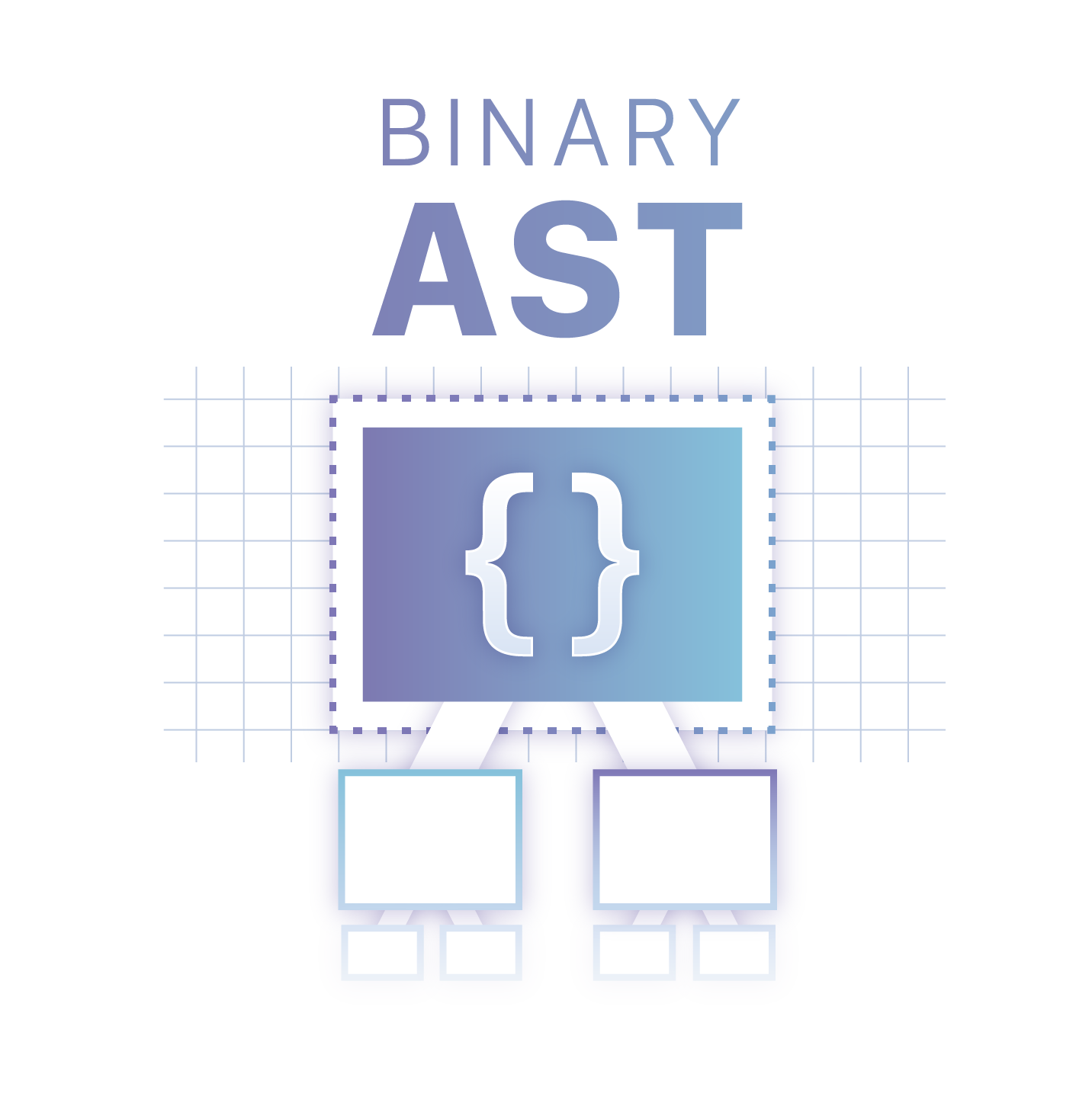
JavaScript Cold starts

The performance of applications on the web platform is becoming increasingly bottlenecked by the startup (load) time. Large amounts of JavaScript code are required to create rich web experiences that we’ve become used to. When we look at the total size of JavaScript requested on mobile devices from HTTPArchive, we see that an average page loads 350KB of JavaScript, while 10% of pages go over the 1MB threshold. The rise of more complex applications can push these numbers even higher.
While caching helps, popular websites regularly release new code, which makes cold start (first load) times particularly important. With browsers moving to separate caches for different domains to prevent cross-site leaks, the importance of cold starts is growing even for popular subresources served from CDNs, as they can no longer be safely shared.
Usually, when talking about the cold start performance, the primary factor considered is a raw download speed. However, on modern interactive pages one of the other big contributors to cold starts is JavaScript parsing time. This might seem surprising at first, but makes sense - before starting to execute the code, the engine has to first parse the fetched JavaScript, make sure Continue reading
Programmable Packet Forwarding Pipelines Using P4 on Software Gone Wild
Every time a new simple programming language is invented, we go through the same predictable cycle:
- Tons of hype;
- Unbounded enthusiasm when people who never worked in target environment realize they could get something simple done in a short time;
- Ever-worsening headaches as the enthusiasts try to get a real job done with the shiny new tool;
- Disappointment;
- A more powerful language is invented to replace the old one.
A few years ago we experienced the same cycle when OpenFlow was the-one-tool-to-bind-them all.
Read more ...IPv6 Buzz 026: MAP-T And Happy Eyeballs With Andrew Yourtchenko
The IPv6 Buzz crew talks MAP-T, MAP-E and Happy Eyeballs with Andrew Yourtchenko, co-author of the original Happy Eyeballs RFC. We discuss the role of Happy Eyeballs given current rates of IPv6 adoption, the differences between MAP-T and MAP-E, and more.
The post IPv6 Buzz 026: MAP-T And Happy Eyeballs With Andrew Yourtchenko appeared first on Packet Pushers.
IPv6 Buzz 026: MAP-T And Happy Eyeballs With Andrew Yourtchenko
The IPv6 Buzz crew talks MAP-T, MAP-E and Happy Eyeballs with Andrew Yourtchenko, co-author of the original Happy Eyeballs RFC. We discuss the role of Happy Eyeballs given current rates of IPv6 adoption, the differences between MAP-T and MAP-E, and more.BIB 078 Solo.io and Super Gloo
A quick look at Solo.io and their service mesh offeringBIB 078 Solo.io and Super Gloo
A quick look at Solo.io and their service mesh offering
The post BIB 078 Solo.io and Super Gloo appeared first on Packet Pushers.
Installing Cumulus packages on air-gapped equipment
From time to time I run into situations where someone would like to install the Cumulus Linux operating system as well as additional packages that aren’t part of the default binary install package. This short excerpt is meant to assist in helping get those additional packages into an air-gapped environment for the install where you don’t have a repo or mirror available to pull from.
For instance, let’s say we want to install TACACS+ on an air-gapped switch and we don’t have access to a mirrored repo. There is a very tedious method which I’ll outline first, then there is the more Linux admin like option which is much more streamlined.
One thing that could be done is to run through the install on a switch with outside connectivity, gather the package and dependency info… manually pull the deb’s off of the repo on whatever media you are using to transfer files to the new switch. Then copy all of the packages over and install them. It’s the hard way, but sometimes that’s the road we have to take.
The long way
Pull the package list from a switch connected to the repo:

All of the packages should be in Continue reading
Envisioning the Future in the Middle East

How can the brightest minds help transform the Middle East for the better? The MIT SciTech Conference hoped to find answers. The annual three-day conference, which took place 19-21 April in Boston, Massachusetts, brought together students and professionals from across North America and the MENA Region. This year’s theme was “Envisioning the Future: Cities of MENA,” and included an IDEAthon on Energy, Innovation, and Infrastructure.
Many people from all over the globe attended the conference, mainly Arabs who were also successful tech entrepreneurs, leveraging the Internet to reach communities across the world. They also spoke about their innovations and inspired the young participants, who included MIT students, through panels, keynotes, ideation processes, and SciTech talks.
The first day started with a tour of MIT Labs and the launch of the IDEAthon. After initial sessions and introductions, participants were left for the night to work on their ideas. Those ended up being presented at the end of the third day to judges, with cash prizes awarded to winners so that they could turn them into reality by implementing them throughout the Arab world.
Infrastructure is a challenge in the MENA region, especially with a rapidly growing population, and the conference Continue reading
Cisco Rides High on Rising Network Complexities
 Cisco's expanded push into 5G and WiFi 6 is leading the vendor into wider opportunities outside of...
Cisco's expanded push into 5G and WiFi 6 is leading the vendor into wider opportunities outside of...
Becoming an AWS Certified Solutions Architect Associate
Architecting for the cloud is becoming a highly desired skill set. Working as a consultant, I’m often in situations where clients are overwhelmed with questions about the cloud. How do I migrate my applications? How do I secure everything? How does it integrate with LDAP and DNS? What’s the best way to connect to the […]
The post Becoming an AWS Certified Solutions Architect Associate appeared first on Overlaid.