Junos IPv6 to IPv4 NAT
Recently I took the JNCIE-SEC lab (that will be another post) and wanted to cover one of the study points …
The post Junos IPv6 to IPv4 NAT appeared first on Fryguy's Blog.
5G Security Draws a Global Crowd, Results in Draft Proposals
 Delegates from 32 countries this week gathered at a conference in Prague to address security...
Delegates from 32 countries this week gathered at a conference in Prague to address security...
Juniper Pushes Open Source Past Experimentation to Implementation
 Juniper’s Julius Francis discusses how open source must evolve and consider security,...
Juniper’s Julius Francis discusses how open source must evolve and consider security,...
Canonical Sharpens Focus on Red Hat, VMware; IPO Plans Remain
 The company has simplified its service offerings in an attempt to lower cost and attract more...
The company has simplified its service offerings in an attempt to lower cost and attract more...
SDxCentral Weekly Wrap: Dell EMC, Big Switch Take On Cisco With Open Networking Deal
 SDxCentral Weekly Wrap for May 3, 2019: Dell EMC and Big Switch team up; Orange taps Dell for 5G...
SDxCentral Weekly Wrap for May 3, 2019: Dell EMC and Big Switch team up; Orange taps Dell for 5G...
Dell and HPE Spar Over Multi-Cloud, Consumption-Based Infrastructure
 A year after HPE CEO Antonio Neri said “Dell doesn’t have an edge-to-cloud approach,” Dell...
A year after HPE CEO Antonio Neri said “Dell doesn’t have an edge-to-cloud approach,” Dell...
Cisco’s Catalyst for Change

You’ve probably heard by now of the big launch of Cisco’s new 802.11ax (neé Wi-Fi 6) portfolio of devices. Cisco did a special roundtable with a group of influencers from the community called Just The Tech. Here’s a video from that event covering the APs that were released, the 9120:
Fred always does a great job of explaining the technical bits behind the APs. But one thing that caught my eye here is the name of the AP – Catalyst. Cisco has been using Aironet for their AP line since they purchased Aironet Wireless Communications back in 1999. The name was practically synonymous with wireless technologies for many people in the industry that worked exclusively with Cisco technologies.
So, is the name change something we should be concerned about?
A Rose Is a Rose Is An AP
Cisco moving toward a unified naming convention for their edge solutions makes a lot of sense. Ten years ago, wireless was still primarily 802.11g-based with 802.11n still a few months away from being proposed and ratified. Connectivity hadn’t quite yet reached the ubiquitous levels of wireless that we see today. The iPhone was only about to be on its third Continue reading
SDxCentral’s Top 10 Articles — April 2019
 VPN flaw uncovered in Cisco, F5, and more; Google Anthos soars to the clouds; and AT&T avoids...
VPN flaw uncovered in Cisco, F5, and more; Google Anthos soars to the clouds; and AT&T avoids...
Vodafone and Telefónica Get Nod for Spanish 5G Pilots
 Vodafone Spain is to work with Huawei on a pilot in Andalusia, while Telefónica teams up with...
Vodafone Spain is to work with Huawei on a pilot in Andalusia, while Telefónica teams up with...
A List Of What Makes WiFi 6 Technically Better ?

List of technical features that matter
The post A List Of What Makes WiFi 6 Technically Better ? appeared first on EtherealMind.
eBPF can’t count?!
It is unlikely we can tell you anything new about the extended Berkeley Packet Filter, eBPF for short, if you've read all the great man pages, docs, guides, and some of our blogs out there.
But we can tell you a war story, and who doesn't like those? This one is about how eBPF lost its ability to count for a while1.
They say in our Austin, Texas office that all good stories start with "y'all ain't gonna believe this… tale." This one though, starts with a post to Linux netdev mailing list from Marek Majkowski after what I heard was a long night:
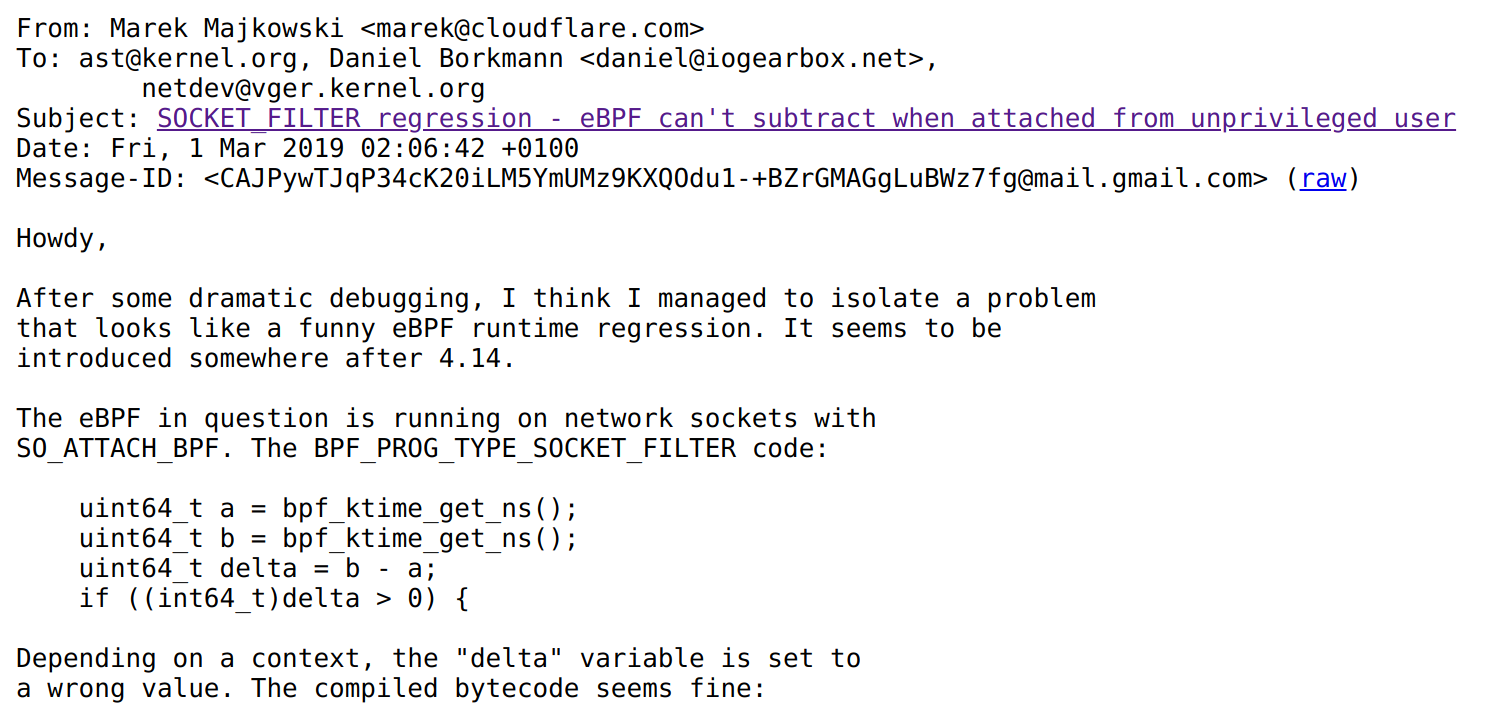
Marek's findings were quite shocking - if you subtract two 64-bit timestamps in eBPF, the result is garbage. But only when running as an unprivileged user. From root all works fine. Huh.
If you've seen Marek's presentation from the Netdev 0x13 conference, you know that we are using BPF socket filters as one of the defenses against simple, volumetric DoS attacks. So potentially getting your packet count wrong could be a Bad Thing™, and affect legitimate traffic.
Let's try to reproduce this bug with Continue reading
Cumulus content roundup: April
You know we like to stay busy here at Cumulus Networks, and April was no exception! We’ve rounded up some of our favorite podcasts, blog posts, and articles in case you missed them. So settle in and get ready for all things open networking!
From Cumulus Networks:
RIP up your dynamic routing with OSPF: Let’s RIP right into the ins and outs of Routing Information Protocol and Open Shortest Path First in this blog post by Keith Ward. Here we’ll discuss all things IGPs, history of RIPS and what you need to know about OSPFs.
Kernel of Truth season 2 episode 5: The power of community: Grab a pair of headphones and tune into Season 2 Episode 5 of our podcast, Kernel of Truth. In this episode, Brian O’ Sullivan talks with Angelo Luciani from Nutanix and our own Pete Lumbis about the power of community and self-service. Learn about the resources available surrounding building community and the importance of it all.
Cumulus NetQ Reinvented
Did you hear the news? We are pleased to announce the launch of our newest product, Cumulus NetQ! Cumulus NetQ is a highly-scalable, modern network operations toolset that provides visibility into and troubleshooting Continue reading
Microsoft Adds More AI, IoT, and Blockchain Services to Azure
 The tech giant announced several new Azure cloud services ahead of its annual Build developers’...
The tech giant announced several new Azure cloud services ahead of its annual Build developers’...
Equinix Interconnect Revenue Soars; Stateless Jumps In the Hot Market
 Networking startup Stateless rolled out its first product: a software-defined interconnection...
Networking startup Stateless rolled out its first product: a software-defined interconnection...
Airship Fixed AT&T’s AIC Pain Points, Catalyzed OpenStack Community
 The carrier is looking to the OSF's Kata container project to solve multi-tenancy concerns with...
The carrier is looking to the OSF's Kata container project to solve multi-tenancy concerns with...
Cisco Issues Largest Single-Day Security Vulnerabilities in at Least 12 Months
 Cisco previously disclosed 42 advisories in April including critical security alerts for operating...
Cisco previously disclosed 42 advisories in April including critical security alerts for operating...