Considerations for the Use of 5G in the Enterprise
Measured adoption of 5G via practical use-cases such as fixed wireless will enable enterprises to get the experience and taste of what it is to come.
Tracing Soon-to-Expire Federal .gov Certificates with CT Monitors

As of December 22, 2018, parts of the US Government have “shut down” because of a lapse in appropriation. The shutdown has caused the furlough of employees across the government and has affected federal contracts. An unexpected side-effect of this shutdown has been the expiration of TLS certificates on some .gov websites. This side-effect has emphasized a common issue on the Internet: the usage of expired certificates and their erosion of trust.
For an entity to provide a secure website, it needs a valid TLS certificate attached to the website server. These TLS certificates have both start dates and expiry dates. Normally certificates are renewed prior to their expiration. However, if there’s no one to execute this process, then websites serve expired certificates--a poor security practice.
This means that people looking for government information or resources may encounter alarming error messages when visiting important .gov websites:
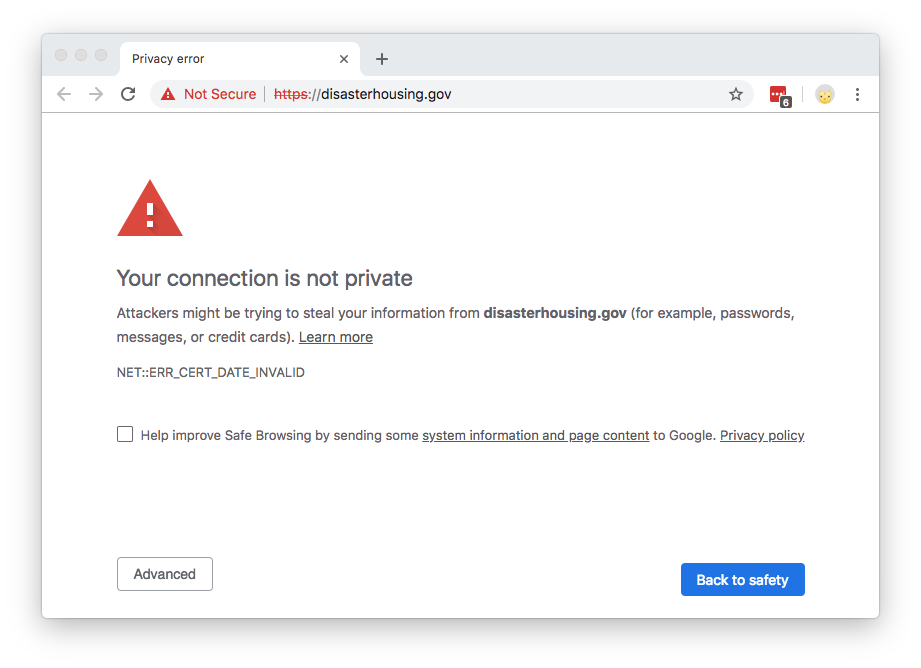
The content of the website hasn’t changed; it’s just the cryptographic exchange that’s invalid (an expired certificate can’t be validated). These expired certificates present a trust problem. Certificate errors often dissuade people from accessing a website, and imply that the site is not to be trusted. Browsers purposefully make it difficult to continue to Continue reading
Q-in-Q Support in Multi-Site EVPN
One of my subscribers sent me a question along these lines (heavily abridged):
My customer is running a colocation business, and has to provide L2 connectivity between racks, sometimes even across multiple data centers. They were using Q-in-Q to deliver that in a traditional fabric, and would like to replace that with multi-site EVPN fabric with ~100 ToR switches in each data center. However, Cisco doesn’t support Q-in-Q with multi-site EVPN. Any ideas?
As Lukas Krattiger explained in his part of Multi-Site Leaf-and-Spine Fabrics section of Leaf-and-Spine Fabric Architectures webinar, multi-site EVPN (VXLAN-to-VXLAN bridging) is hard. Don’t expect miracles like Q-in-Q over VNI any time soon ;)
Read more ...Episode 43 – Peering With Providers
In this episode of the Network Collective Community Roundtable, the panel discusses the nuances of getting your organization connected to the internet. Is it as simple as connecting a cable and calling it a day, or is there more to think about when designing your Internet edge? Joining the Network Collective team for this conversation is Dr. Pete Welcher and Tom Ammon.
 We would like to thank VIAVI Solutions for sponsoring this episode of Network Collective. VIAVI Solutions is an application and network management industry leader focusing on end-user experience by providing products that optimize performance and speed problem resolution. Helping to ensure delivery of critical applications for businesses worldwide, Viavi offers an integrated line of precision-engineered software and hardware systems for effective network monitoring and analysis. Learn more at www.viavisolutions.com/networkcollective.
We would like to thank VIAVI Solutions for sponsoring this episode of Network Collective. VIAVI Solutions is an application and network management industry leader focusing on end-user experience by providing products that optimize performance and speed problem resolution. Helping to ensure delivery of critical applications for businesses worldwide, Viavi offers an integrated line of precision-engineered software and hardware systems for effective network monitoring and analysis. Learn more at www.viavisolutions.com/networkcollective.
 We would also like to think PathSolutions for sponsoring this episode of Network Collective. PathSolutions TotalView is designed to automatically dig deep into network devices to learn what they know about your network’s performance. This means your network is no longer full of mysteries because you know everything your network knows. Try TotalView on your network, and it will show you 5 things about your network that you didn’t previously know. You can find out Continue reading
We would also like to think PathSolutions for sponsoring this episode of Network Collective. PathSolutions TotalView is designed to automatically dig deep into network devices to learn what they know about your network’s performance. This means your network is no longer full of mysteries because you know everything your network knows. Try TotalView on your network, and it will show you 5 things about your network that you didn’t previously know. You can find out Continue reading
BGP in 2018 – Part2: BGP Churn
The scalability of BGP as the Internet’s routing protocol is not just dependant on the number of prefixes carried in the routing table. Dynamic routing updates are also part of this story. If the update rate of BGP is growing faster than we can deploy processing capability to match then the routing system will lose data, and at that point the routing system will head into turgid instability. This second part of the report of BGP across 2018 will look at the profile of BGP updates across 2018 to assess whether the stability of the routing system, as measured by the level of BGP update activity, is changing.Operations guide
One of the most common requests we, as consultants, get from our customers is for an operations guide as the final deliverable for any data center build out. There are a few goals for such a guide:
- Allow the customer to better transfer knowledge as their teams grow and change.
- Provide an “as built” guide that explains step-by-step how to deploy and manage the infrastructure.
- Tie together the operational workflow for all the new components that are leveraged in the modern open-networking paradigm.
Since Scott and I have been working on many operations guides, we thought it would be great to document our process so that customers can write their own operations guides.
The operations guide for web scale networking goes beyond just documenting configuration backups, user account access and change requests though. Web scale networking integrates proven software development processes and as such, the operations guide needs to account for these workflows.
As Built
The starting point of all operations guides is the initial build. Most of the cabling architecture, traffic flows and features, along with decision making and architectural choices, are captured within the High level Design and Low Level Design document. The operations guide on the other Continue reading
Silver Peak SD-WAN Supports Multi-Cloud With Google Cloud Certification
 Silver Peak’s EdgeConnect SD-WAN platform is now certified by Google Cloud, Amazon Web Services, Microsoft Azure, and Oracle Cloud.
Silver Peak’s EdgeConnect SD-WAN platform is now certified by Google Cloud, Amazon Web Services, Microsoft Azure, and Oracle Cloud.
Nutanix CEO to VMware: ‘Stop Being a Bully’
 The Nutanix-VMware battle escalated with a Nutanix blog accusing VMware COO Sanjay Poonen of “bullying” Nutanix customers.
The Nutanix-VMware battle escalated with a Nutanix blog accusing VMware COO Sanjay Poonen of “bullying” Nutanix customers.
Canonical Brings IoT Security to Ubuntu Core
 Canonical says the latest version of its platform for IoT and container deployments will reduce three things: time to market, software development risk, and security maintenance costs.
Canonical says the latest version of its platform for IoT and container deployments will reduce three things: time to market, software development risk, and security maintenance costs.
SDxCentral Promotes Dan Meyer to Editor-in-Chief
 SDxCentral is pleased to announce Dan Meyer has been promoted to editor in chief at SDxCentral. Read more in this post by CEO Matt Palmer.
SDxCentral is pleased to announce Dan Meyer has been promoted to editor in chief at SDxCentral. Read more in this post by CEO Matt Palmer.
Enjoy a slice of QUIC, and Rust!

During last year’s Birthday Week we announced early support for QUIC, the next generation encrypted-by-default network transport protocol designed to secure and accelerate web traffic on the Internet.
We are not quite ready to make this feature available to every Cloudflare customer yet, but while you wait we thought you might enjoy a slice of quiche, our own open-source implementation of the QUIC protocol written in Rust.

Quiche will allow us to keep on top of changes to the QUIC protocol as the standardization process progresses and experiment with new features more easily. Let’s have a quick look at it together.
Simple and genuine ingredients
The main design principle that guided quiche’s initial development was exposing most of the QUIC complexity to applications through a minimal and intuitive API, but without making too many assumptions about the application itself, in order to allow us to reuse the same library in different contexts.
For example, while we think Rust is great, most of the stack that deals with HTTP requests on Cloudflare’s edge network is still written in good ol’ C, which means that our QUIC implementation would need to be integrated into that.
The quiche API can process Continue reading
Deutsche Telekom Flags Further 5G Tests in 2019
 The German carrier signed an agreement with the Berlin Senate Department for Economics, Energy and Public Enterprises to drive 5G deployment in the capital.
The German carrier signed an agreement with the Berlin Senate Department for Economics, Energy and Public Enterprises to drive 5G deployment in the capital.
Community Networks: In Tanzania, Helping to Close the Connectivity Gap

Community established networks, also referred to as “community networks” (CNs), have existed for many years and provide a sustainable solution to address the connectivity gaps that exist in urban, remote, and rural areas around the world. While the global statistics estimate that about half of the world population has access to the Internet, the connectivity gap is wide between the developed and developing countries.
In Tanzania, there are 41.8 million voice telephone subscriptions and only 23 million Internet users. A study by Research ICT Africa reported that when Internet access is compared between rural and urban areas, 86% of rural dwellers remain unconnected to the Internet compared to 44.6% in urban areas. Similarly, in Tanzania, fewer women have access to and use of the Internet than men.
In order to address the connectivity challenges in Tanzania, the Internet Society Tanzania Chapter in partnership with the University of Dodoma, supported by Beyond the Net Funding Programme, has built a pilot project using TV white space as a community network solution. The deployed network has connected four educational institutions in rural Tanzania and at the same time provided Internet access to community members around the schools.
In order Continue reading
A New Breed of IT Pro: The Hybrid Engineer
Today there is a need for a new breed of IT professional−the hybrid engineer. This is an engineer who understands DevOps and has the technical skills and ability to communicate in business terms.