Verizon Buys Software-Defined Perimeter Assets From Vidder
 Vidder’s technology is already integrated into Verizon’s SDP service.
Vidder’s technology is already integrated into Verizon’s SDP service.
IBM Boosts Cloud Migration, Management
 Its Cloud Migration Factory platform gained new automation features, while its Multicloud Management Platform was infused with ServiceNow support.
Its Cloud Migration Factory platform gained new automation features, while its Multicloud Management Platform was infused with ServiceNow support.
BiB 057: Oracle Cloud Infrastructure Wants Your Workloads
Oracle Cloud Infrastructure is slowly working its way towards being feature competitive with the Big 3 - AWS, Azure, and GCP. How are they doing that? By building out robust cloud infrastructure aimed at the typical enterprise.
The post BiB 057: Oracle Cloud Infrastructure Wants Your Workloads appeared first on Packet Pushers.
Weekly Wrap Podcast: Germany Jumps on Huawei 5G Ban Plans
 SDxCentral Weekly Wrap for Nov. 16, 2018: Germany Jumps on Huawei 5G Ban Plans.
SDxCentral Weekly Wrap for Nov. 16, 2018: Germany Jumps on Huawei 5G Ban Plans.
Former Oracle Exec Thomas Kurian Replaces Google Cloud CEO Diane Greene
 Kurian spent 22 years at Oracle before abruptly resigning last month. Reports quickly surfaced saying that Kurian clashed with CTO Larry Ellison over Oracle’s cloud strategy.
Kurian spent 22 years at Oracle before abruptly resigning last month. Reports quickly surfaced saying that Kurian clashed with CTO Larry Ellison over Oracle’s cloud strategy.
BlackBerry Bets $1.4B on IoT Security With Cylance Acquisition
 In a year when security startups are raising hundreds of millions in initial public offerings — including Cylance competitor Carbon Black that scored $152 million in its May IPO — it was widely assumed Cylance would follow suit.
In a year when security startups are raising hundreds of millions in initial public offerings — including Cylance competitor Carbon Black that scored $152 million in its May IPO — it was widely assumed Cylance would follow suit.
SDxCentral’s Weekly Roundup — November 16, 2018
 AWS adds new infrastructure regions; The Linux Foundation launches a lab for SDN projects; ZTE contributes 5G patents to ETSI.
AWS adds new infrastructure regions; The Linux Foundation launches a lab for SDN projects; ZTE contributes 5G patents to ETSI.
Weekly Show 416: From Reactive To Proactive NetOps With Cisco NAE (Sponsored)
Today's sponsored Weekly Show dives into Cisco's Network Assurance Engine. This software creates a real-time and continuously updated model of the network that IT can use to assess the impact of changes, get deep visibility into network state, and move network ops from reactive to proactive. We hear from an IT engineer inside Cisco who uses NAE in production.
The post Weekly Show 416: From Reactive To Proactive NetOps With Cisco NAE (Sponsored) appeared first on Packet Pushers.
Oracle Buys SD-WAN Vendor Talari Networks
 Cloud service providers have come to realize the importance of high-quality network connectivity to ensure a happy end user, says IHS Markit analyst Cliff Grossner.
Cloud service providers have come to realize the importance of high-quality network connectivity to ensure a happy end user, says IHS Markit analyst Cliff Grossner.
HPE InfoSight Pushes AI Into Data Center Servers
 InfoSight’s predictive capabilities also move the needle closer to enabling autonomous data centers.
InfoSight’s predictive capabilities also move the needle closer to enabling autonomous data centers.
Independent Testing Confirms Performance, Resiliency & Automation Benefits of Open Networking and Pluribus’ Adaptive Cloud Fabric
The Tolly Group has “worked with virtually every major vendor and evaluated the most important products and technologies to appear...Short Take – Policy At The Edge
Today’s networks are enforcing policy at an even greater scale but where does it make sense to enforce this policy? In this Network Collective Short Take, Russ and Eyvonne talk through the merits of enforcing policy at the edge of your network.
The post Short Take – Policy At The Edge appeared first on Network Collective.
Why Is The CCIE Lab Moving?

Cisco confirmed big CCIE rumor this week that the RTP lab was going to be moved to Richardson, TX.
The language Cisco used is pretty neutral. San Jose and RTP are being shut down as full time lab locations and everyone is moving to Richardson. We knew about this thanks to the detective work of Jeff Fry, who managed to figure this out over a week ago. Now that we know what is happening, why is it coming to pass?
They Don’t Build Them Like They Used To
Real estate is expensive. Anyone that’s ever bought a house will tell you that. Now, imagine that on a commercial scale. Many companies will get the minimum amount of building that they need to get by. Sometimes they’re bursting at the seams before they upgrade to a new facility.
Other companies are big about having lots of area. These are the companies that Continue reading
Introducing Apps with Workers
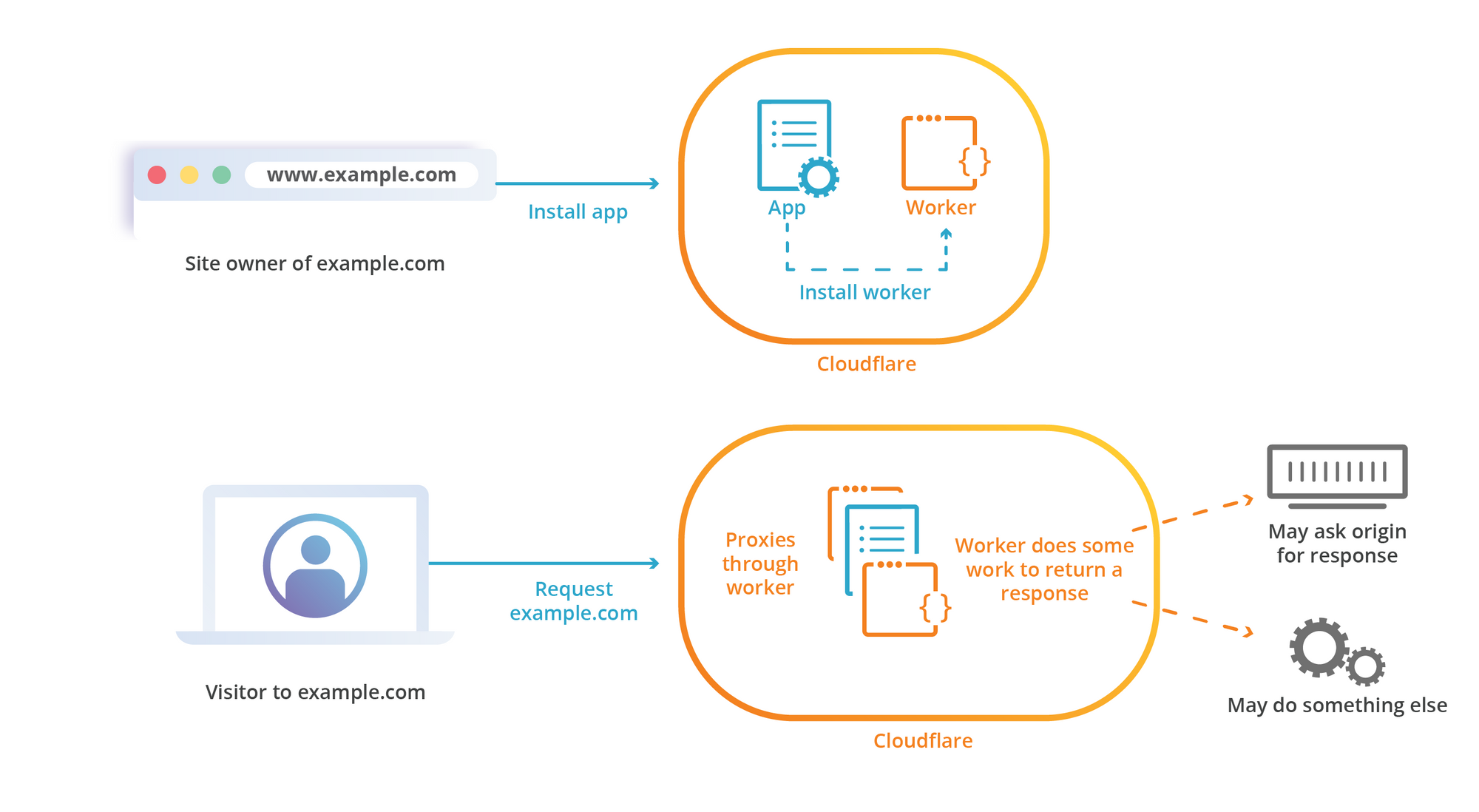
Since its inception, Cloudflare Apps has made it possible for website owners to install a tool or a service directly onto a domain they have that lives on the Cloudflare network. As an App Developer, you’ve had the ability to deliver your product by modifying traffic and content of a user’s website using a combination of Javascript, HTML, CSS injection with the ability to modify Cloudflare features such as DNS.
Today we are announcing a public beta for our Cloudflare Apps with Workers! If you are a developer who has been using Workers or Cloudflare Apps, this is a significant step forward to bring together our server-less platform allowing you the next wave of innovation in the Cloudflare marketplace.
Wait! Yet more Workers news? It’s already been a furious year of releases for Workers, from our GA launch in February to numerous improvements including the beta of Cache API and a flurry of updates during Cloudflare’s Birthday week, where we made available our K/V Storage and WASM support. With this beta, developers can now package all Workers capabilities, deliver new worker-powered experiences to Cloudflare customers all within a few clicks via Cloudflare Apps.
Now your Apps can be more powerful, Continue reading
El Buen Fin: Tips to Shop Smart

Last week I had the opportunity to participate in the first edition of the International Internet and Entrepreneurship Forum (FIIE), in Monterrey, Mexico. The event was convened by NIC Mexico and other organizations of the Internet community of Latin America and the Caribbean as part of the activities of INCmty, an entrepreneurial festival with several years of tradition. The intersection between both topics is a fertile ground for reflection, especially in relation to the security of Internet of Things (IoT) devices.
IoT for Innovation and Entrepreneurship
The Internet has been known as a technology for facilitating innovation and entrepreneurship. The pace of technological development, together with the evolution of the Internet, has given rise to new solutions that seek to make life easier. Such is the case of the various devices connected to the Internet, which form the Internet of Things ecosystem.
Therefore, one of the issues addressed during the Forum was the role of IoT devices in the entrepreneurial ecosystem in the LAC region. There I took the opportunity to share the Internet Society’s vision of IoT security: we want people to benefit from the use of these devices in a trustworthy environment. The issue is particularly Continue reading
