Using MPLS+EVPN in Data Center Fabrics
Here’s a question I got from someone attending the Building Next-Generation Data Center online course:
Cisco NCS5000 is positioned as a building block for a data center MPLS fabric – a leaf-and-spine fabric with MPLS and EVPN control plane. This raised a question regarding MPLS vs VXLAN: why would one choose to build an MPLS-based fabric instead of a VXLAN-based one assuming hardware costs are similar?
There’s a fundamental difference between MPLS- and VXLAN-based transport: the amount of coupling between edge and core devices.
Read more ...Fun in the Lab: FTDv & FMC – Install and Deploy
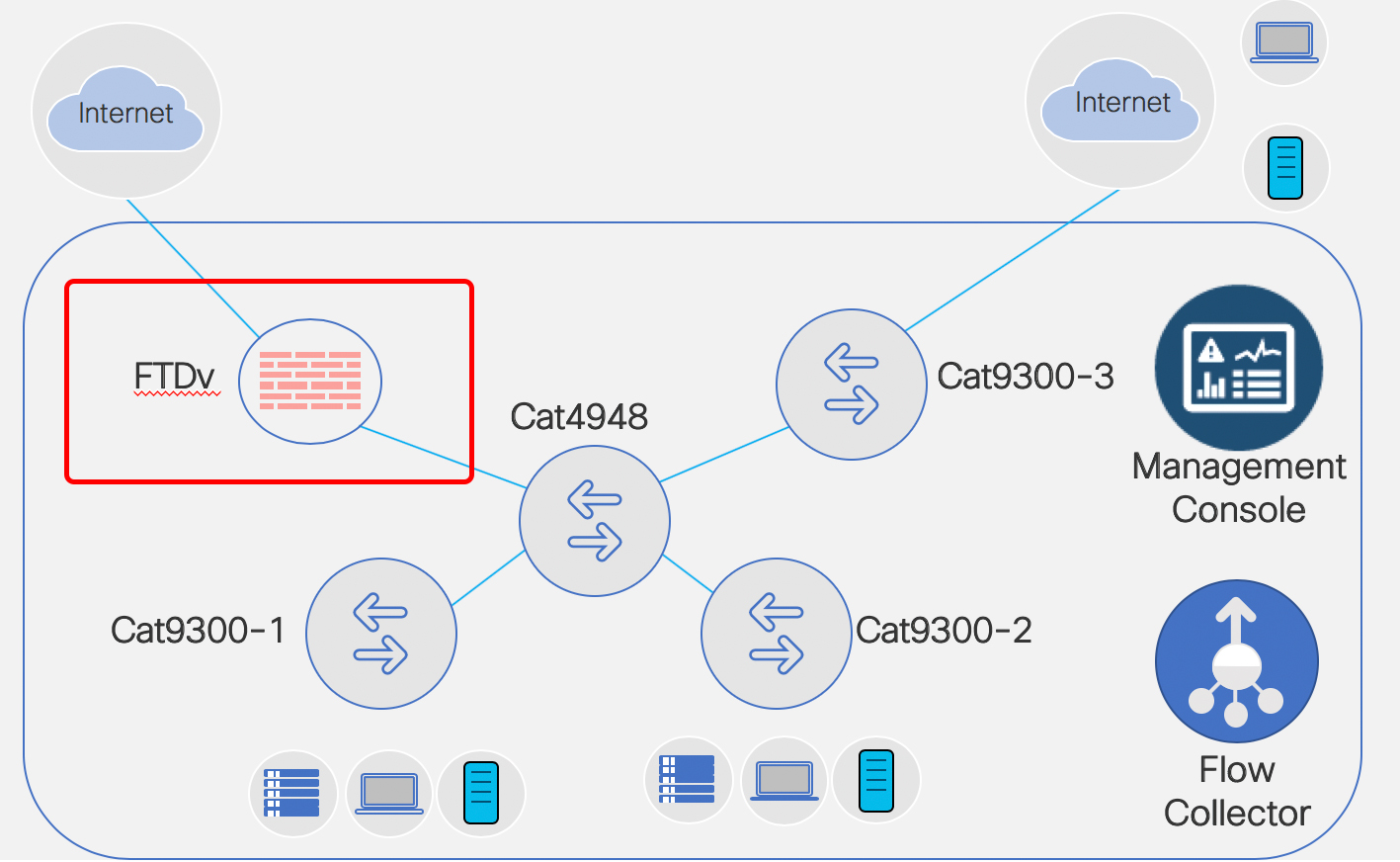
This is my Stealthwatch playground…. errrr… I mean … ahem… “work environment” for a Technical Solution Workshop I am working on for Stealthwatch.
Going to set up FTDv and FMC today. A co-worker and friend, Scott Barasch, helped me get jump started… so figure I’ll pass on what I just learned to you. 
What this blog will cover is
- DEPLOY
- Deploying the OVF for FTDv
- Deploying the OVF for FMC
- VMware settings
- Tweak for FTDv
- Tweak for FMC
- Prepping to Power On
- Snapshot Both Before Power On
- Power Both On
- Setup via Console
- FMC – console in and setup IP address
- FTDv – console in and step thru the prompts
- Test IP Connectivity
- Ping FMC and FTDv from the PC
- Notice Can’t ping FTDv
- Fix
- Ping
- Browse into FMC
- Change password
- Setup DNS
- Setup NTP
- Accept EULA
- Apply
- LICENSING
- License FMC
- FMC/FTDv: Make the Connection
- FTDv – Point FTDv to FMC
- FMC – bring the FTDv into the fold.

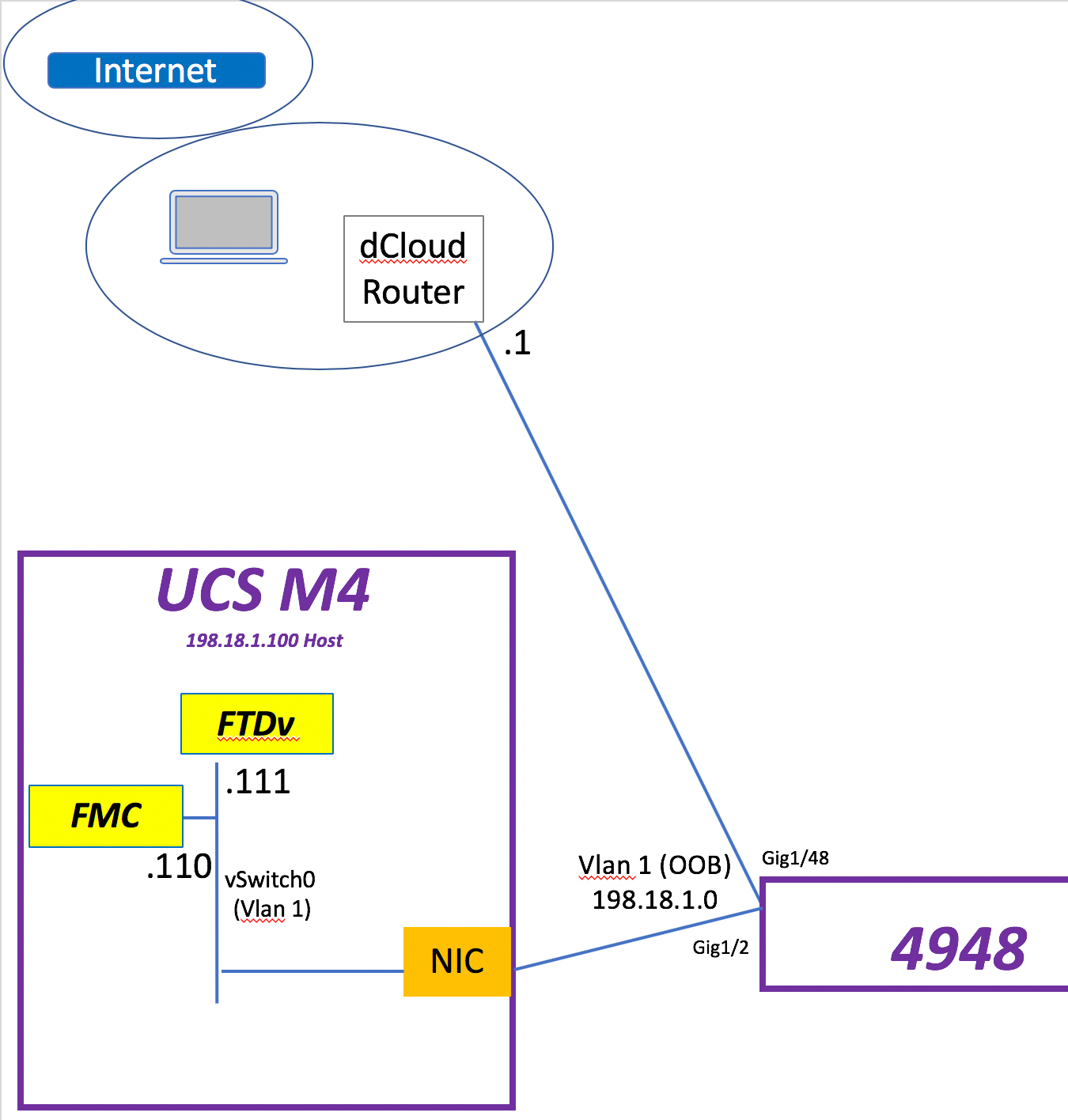
So let’s begin. What I have to host my FMC & FTDv VMs is a UCS M4 with a NIC connected to a Cat4948 in vlan 1. That NIC is tied to vSwitch0 in the UCS. Continue reading
Use Cumulus HTTP API to Help Automate Common Network Tasks
Cumulus Linux includes a RESTful programming interface for accessing network devices running that OS. It’s called HTTP API, and it implements an API to access the OpenStack ML2 driver and Network Command Line Utility, or NCLU. Understanding exactly what this means, and how it works, is essential before digging into the possibilities it presents. Here’s an overview to get this going.
The OpenStack ML2 Driver
The ML2 Driver, a.k.a. (in OpenStack’s terms) the Modular Layer 2 neutron plug-in, provides a framework. It enables OpenStack-based networking to use a variety of Layer 2 networking technologies, including those from Cumulus (for which a specific ML2 driver is available and ready to use). To use the OpenStack ML2 driver with Cumulus Linux switches, two essential ingredients must be present:
- The REST API, which comes installed in Cumulus Linux. This includes an ML2 HTTP Server, which recognizes and responds to such requests. This runs on Cumulus-based network nodes to which management consoles or nodes will attach to interrogate, configure, or otherwise interact underlying devices.
- Elsewhere on the network, the Cumulus ML2 Mechanism Driver should be installed on a VM or system running Cumulus Linux. This is called a “controller node.” Continue reading
IETF 103, Day 3: DNS Privacy, TLS & IoT

This week is IETF 103 in Bangkok, Thailand, and we’re bringing you daily blog posts highlighting the topics of interest to us in the ISOC Internet Technology Team. Wednesday is a relatively light day in this respect, although there’s some pretty important matters being discussed today.
DPRIVE kicks off the day at 09.00 UTC+9, and will mostly be discussing user perspectives with respect to the recently introduced implementations of DNS-over-TLS and DNS-over-HTTPS, as well as the issues of DNS privacy between resolvers and authoritative servers. There’s also a new draft up for discussion on DNS-over-TLS for insecure delegations that describe an alternative authentication mechanism without need for DNSSEC support.
NOTE: If you are unable to attend IETF 103 in person, there are multiple ways to participate remotely.
TLS holds its second session of the week immediately after lunch at 12.20 UTC+7. This will carry-on where it left off on Monday, although will be discussing a DANE Record and DNSSEC Authentication Chain Extension for TLS. The intention is to allow TLS clients to perform DANE authentication of a TLS server without needing to perform additional DNS record lookups.
Then at 13.50 UTC+7, Homenet will be focusing on Homenet Naming Continue reading
BGP Unnumbered Overview
The Border Gateway Protocol (BGP) is an IP reachability protocol that you can use to exchange IP prefixes. Traditionally, one of the nuisances of configuring BGP is that if you want to exchange IPv4 prefixes you have to configure an IPv4 address for each BGP peer. In a large network, this can consume a lot of your address space, requiring a separate IP address for each peer-facing interface.
BGP Over IPv4 Interfaces
To understand where BGP unnumbered fits in, it helps to understand how BGP has historically worked over IPv4. Peers connect via IPv4 over TCP port 179. Once they’ve established a session, they exchange prefixes. When a BGP peer advertises an IPv4 prefix, it must include an IPv4 next hop address, which is usually the address of the advertising router. This requires, of course, that each BGP peer has an IPv4 address.
As a simple example, using the Cumulus Reference Topology, let’s configure BGP peerings as follows:
Between spine01 (AS 65020, 10.1.0.0/31) and leaf01 (AS 65011, 10.1.0.1/31)
Between spine01 (10.1.0.4/31) and leaf02 (AS 65012, 10.1.0.5/31)
Leaf01 will advertise the prefix 192.0.2.1/32 and leaf02 will Continue reading
VMware Embraces Containers at VMworld Europe
 The virtualization giant updated its hybrid cloud stack with new Kubernetes support and also announced a new integration with IBM Cloud’s managed Kubernetes service.
The virtualization giant updated its hybrid cloud stack with new Kubernetes support and also announced a new integration with IBM Cloud’s managed Kubernetes service.
Telefónica Business Solutions Uses VMware for Its Virtual Data Center Cloud Service
 The VDC service is based on VMware’s Cloud Provider Platform, and it enables customers to create virtual infrastructure combining compute, storage, and advanced networking.
The VDC service is based on VMware’s Cloud Provider Platform, and it enables customers to create virtual infrastructure combining compute, storage, and advanced networking.
VMware Snaps Up Heptio to Boost Its Kubernetes Cred
 The deal was based on growing demand from enterprise customers that want to use Kubernetes as the basis for their cloud-agnostic infrastructure.
The deal was based on growing demand from enterprise customers that want to use Kubernetes as the basis for their cloud-agnostic infrastructure.
Thoma Bravo Acquires Veracode From Broadcom for $950 Million
 Broadcom took over Veracode as part of its $18.9 billion purchase of CA Technologies, which it completed this week. CA bought Veracode in 2017.
Broadcom took over Veracode as part of its $18.9 billion purchase of CA Technologies, which it completed this week. CA bought Veracode in 2017.
Dish’s 5G Aspirations Move Closer to Reality With NB-IoT Deals
 The company will use Ericsson NB-IoT equipment and SBA Communications’ towers for the first phase of its 5G network, which it says will be done in March 2020.
The company will use Ericsson NB-IoT equipment and SBA Communications’ towers for the first phase of its 5G network, which it says will be done in March 2020.
Internet Hall of Fame Nominations Open 1 January
Do you know someone who has played a major role in the development and advancement of the Internet? On 1 January 2019, the Internet Hall of Fame will open nominations for its 2019 class of inductees.
The Internet Hall of Fame was launched in 2012 by the Internet Society. With more than 100 inductees, the Internet Hall of Fame celebrates Internet pioneers and innovators from around the world who have helped change the way we live and work today. Their trailblazing accomplishments are as broad and diverse as the Internet itself; expanding the Internet’s benefits into new regions and communities, and creating new technologies and standards that were foundational to the Internet’s development and expansion.
The Internet Hall of Fame recognizes:
- Individuals who were instrumental in the design and development of the Internet with exceptional achievements that impacted the Internet’s global advancement and evolution; or
- Individuals who made outstanding technological, commercial, or other advances and helped to expand the Internet’s positive impact on the lives of others; or
- Individuals who made major contributions to the growth, connectivity, and use of the Internet, either on a global scale or within a specific region that resulted in global impact.
If you know Continue reading