Link Propagation 121: All The Links Fit To Click
Welcome to Link Propagation, a Packet Pushers newsletter. Link Propagation is included in your free membership. Each week we hand-select the most relevant practitioner blog posts, tech news, and product announcements. We age them in oak barrels for up to seven days and then distill them using ancient craft techniques handed down by Tim Berners-Lee. […]Living in Times of Digital Uncertainty: Are Control and Trust Compatible?
The Cambridge Analytica data misuse is the most recent high-profile incident to impact Internet trust. Trust – or the lack thereof – is the term used to describe much of the current state of the Internet. For years now, we have been hearing about a decline in user trust because of fears of surveillance, cybercrime, data breaches, crack downs on speech, or misuse of their data.
However, recently updated data from a recently released edition of CIGI’s annual survey on Trust seems to shatter commonly-held views on the state of trust and raise some novel questions. While the survey covers a wide range of issues from privacy to e-commerce and online habits, one particular result is rather striking:
Three quarters of respondents (73%) said that they agree with the statement “overall, I trust the Internet.” Last year only 56% said that. The trust was highest in China (91%) and India (90%).
This result appears to contradict the assumption that overall trust in the Internet is diminishing.
If, indeed, there is an overall increase in trust, then the first question we should ask is: what type of trust are we talking about?
- Are we referring to trust with regard to Continue reading
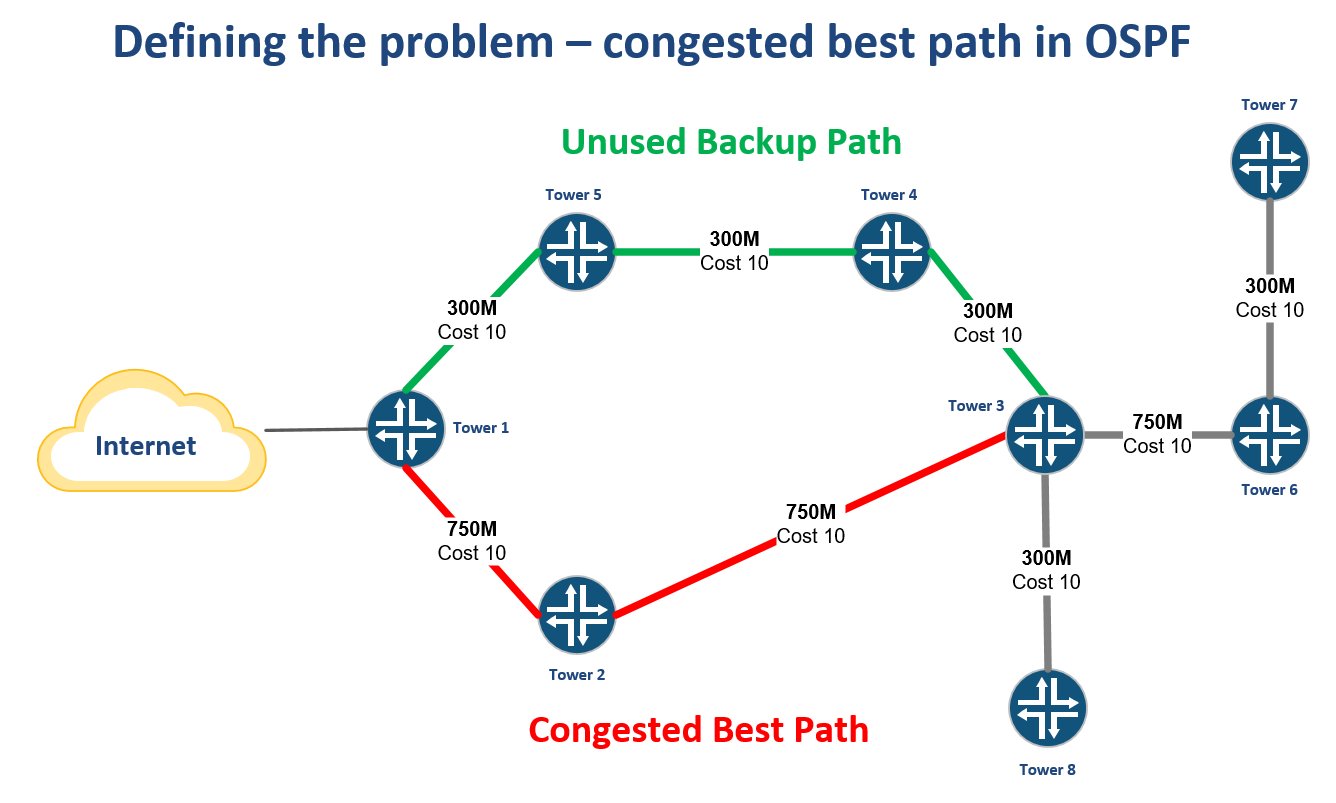
WISP Design – OSPF “Leapfrog” path for traffic engineering
Introduction
One challenge that every WISP owner or operator has faced is how to leverage unused bandwidth on a backup path to generate more revenue.
For networks that have migrated to MPLS and BGP, this is an easier problem to solve as there are tools that can be used in those protocols like communities or MPLS TE to help manage traffic and set policy.
However, many WISPs rely solely on OSPF and cost adjustment to attempt to influence traffic. Alternatively, trying to use policy routing can lead to a design that doesn’t failover or scale well.
Creating a bottleneck on a single path
WISPs that are OSPF routed will often have a primary path back to the Internet at one or more points in the network typically from a tower that aggregates multiple backhauls.
As more towers are added that rely on this path, it can create a bottleneck while other paths are unused.
Creating an alternate best path by leapfrogging another router
One way to solve this problem is to use VLANs to create another subnet for OSPF to form an adjacency.
By tagging the VLAN from Tower 6 through Tower 3 and into Tower 4, a new path Continue reading
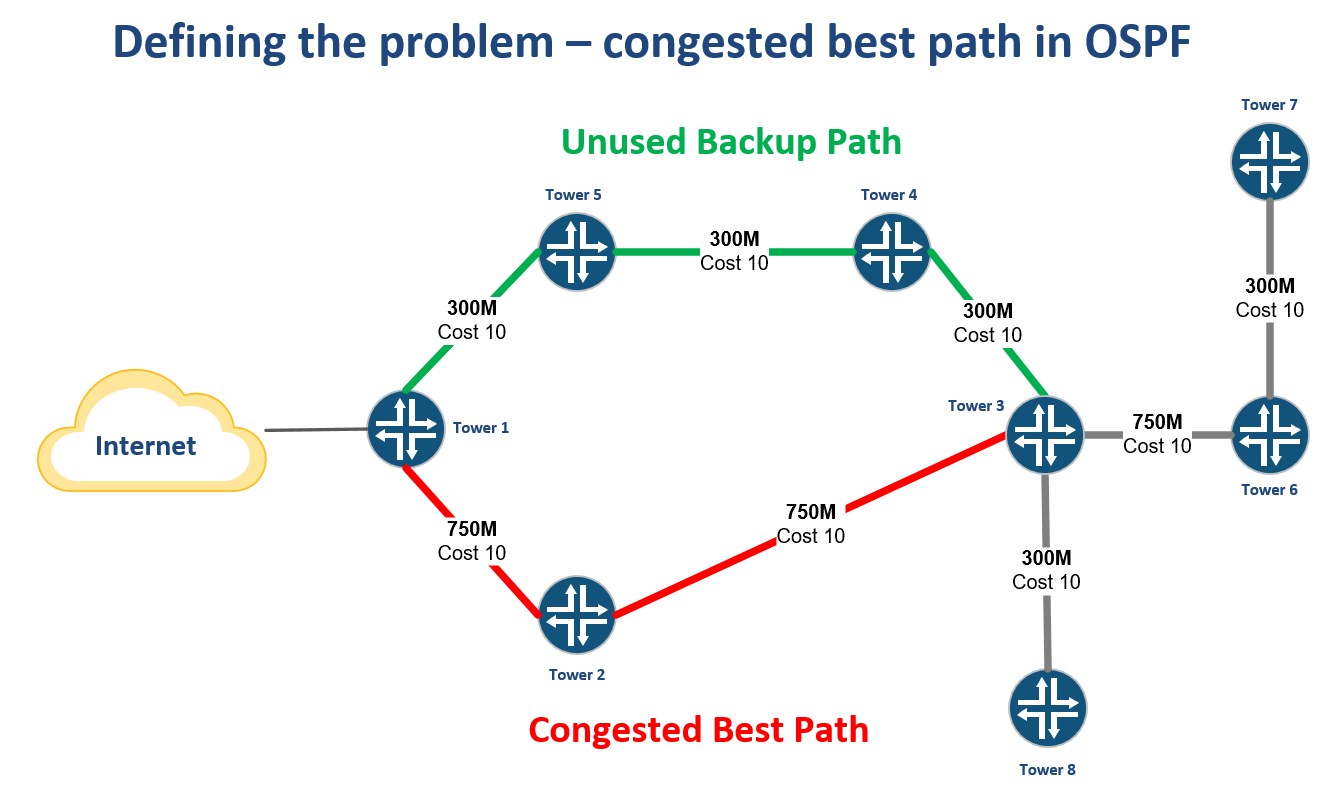
WISP Design – OSPF “Leapfrog” path for traffic engineering
Introduction
One challenge that every WISP owner or operator has faced is how to leverage unused bandwidth on a backup path to generate more revenue.
For networks that have migrated to MPLS and BGP, this is an easier problem to solve as there are tools that can be used in those protocols like communities or MPLS TE to help manage traffic and set policy.
However, many WISPs rely solely on OSPF and cost adjustment to attempt to influence traffic. Alternatively, trying to use policy routing can lead to a design that doesn’t failover or scale well.
Creating a bottleneck on a single path
WISPs that are OSPF routed will often have a primary path back to the Internet at one or more points in the network typically from a tower that aggregates multiple backhauls.
As more towers are added that rely on this path, it can create a bottleneck while other paths are unused.
Creating an alternate best path by leapfrogging another router
One way to solve this problem is to use VLANs to create another subnet for OSPF to form an adjacency.
By tagging the VLAN from Tower 6 through Tower 3 and into Tower 4, a new path Continue reading
AI for IT: Who Will Lead the Charge for a Standard?
For artificial intelligence in networking to become mainstream, we need a common standard across the IT stack.
Intent-Based Networking’s True Intent Revealed
For some companies, the goal of intent-based networking may be rather simple.
Show 392: Debating The Value Of Expert Certifications
On today’s Weekly Show the Packet Pushers jump on the live grenade that is the debate over the value of IT certifications.
Spurred by Greg’s blog about giving up his CCIE status, this episode looks at the value of technology certifications such as the CCIE and others.
Greg and guests Mike Fryar, Chris Kluka, and Jeremy Filliben discuss the benefits and limits of professional certifications, the differences between certifications and actual skills, whether certifications represent a standardized body of knowledge or just a set of instructions, and how the industry might better foster learning.
Sponsor: InterOptic
InterOptic offers high-performance, high-quality optics at a fraction of the cost. Find out more at InterOptic.com, and if you re attending Interop 2018 in Vegas, stop by the InterOptic booth to learn how they can help you spec the right optics for your network.
Sponsor: Cumulus Networks
The Cumulus Linux network OS is simple, open, untethered Linux that can run on more than 70 hardware platforms and help you transition from your legacy infrastructure. Cumulus Networks is Web-scale networking for the digital age. Go to cumulusnetworks.com to find out more.
Show Links:
Quitting My CCIE Status – Greg Ferro
Install Netmiko on Windows
Netmiko develop by kirk Byers is open source python library based on Paramiko which simplifies SSH management to network devices . Netmiko library makes task to automate . Its very tedious to find out the procedure to install Netmiko in Windows enviornment.Let’s make out task simple :- Steps: Install Anaconda ( https://www.anaconda.com/download/) From the Anaconda […]Install Netmiko on Windows
Netmiko develop by kirk Byers is open source python library based on Paramiko which simplifies SSH management to network devices .
Netmiko library makes task to automate . Its very tedious to find out the procedure to install Netmiko in Windows enviornment.Let’s make out task simple :-
Steps:
- Install Anaconda ( https://www.anaconda.com/download/)
- From the Anaconda shell, run “conda install paramiko”.

- From the Anaconda shell, run “pip install scp”.

- Install git for windows (https://www.git-scm.com/downloads)
- Clone Netmiko from Git Bash Window (https://github.com/ktbyers/netmiko).

- Change directory to netmiko.

- Run python setup.py install from Git Bash Window

- Check on Python console to confirm the availabilty of paramiko and netmiko library

Its done.. Enjoy automating tasks !!!!
From the Trenches: Rampant MacGyver-ism
Here’s a response I got from Simon Milhomme on my Why Is Network Automation So Hard article:
Read more ...Today we mitigated 1.1.1.1
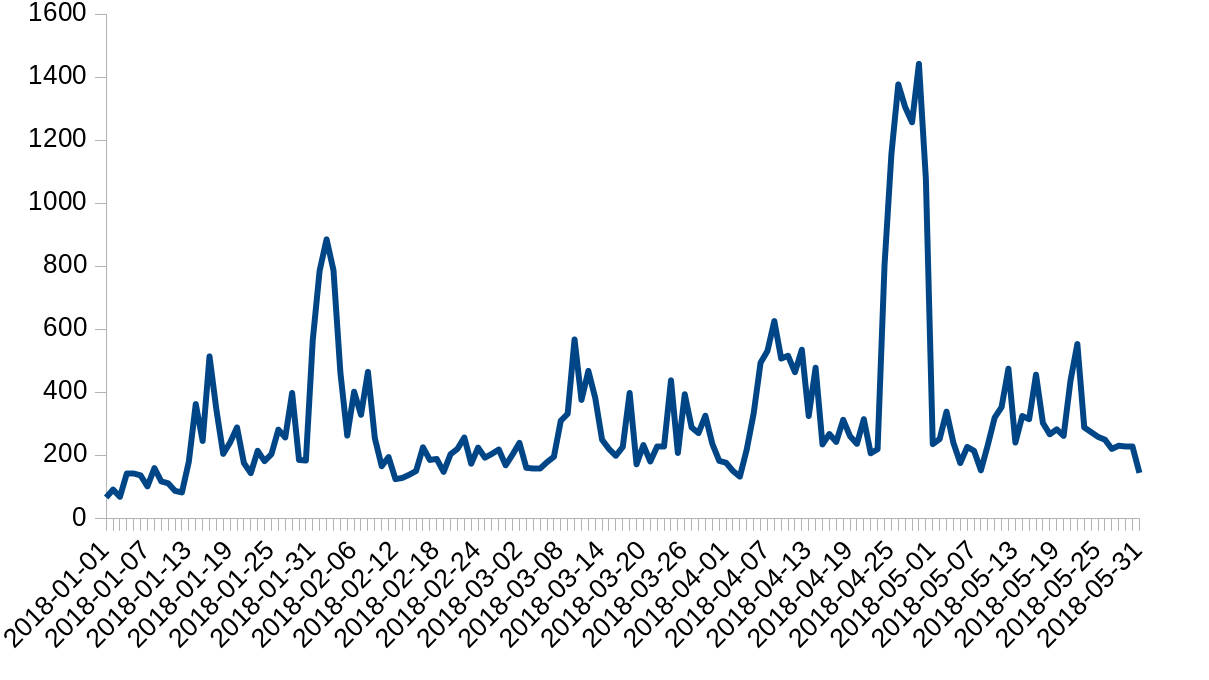
On May 31, 2018 we had a 17 minute outage on our 1.1.1.1 resolver service; this was our doing and not the result of an attack.
Cloudflare is protected from attacks by the Gatebot DDoS mitigation pipeline. Gatebot performs hundreds of mitigations a day, shielding our infrastructure and our customers from L3/L4 and L7 attacks. Here is a chart of a count of daily Gatebot actions this year:
In the past, we have blogged about our systems:
Today, things didn't go as planned.
Gatebot
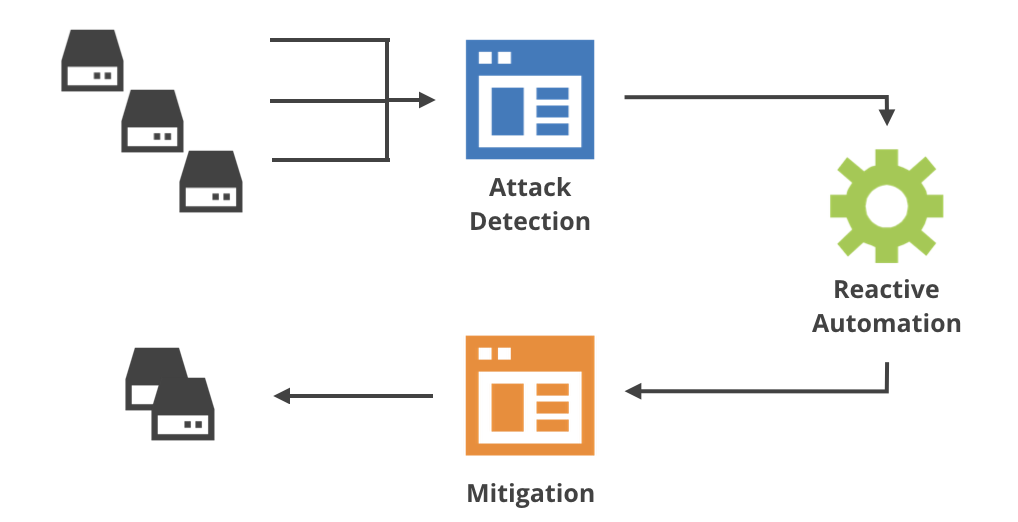
Cloudflare’s network is large, handles many different types of traffic and mitigates different types of known and not-yet-seen attacks. The Gatebot pipeline manages this complexity in three separate stages:
- attack detection - collects live traffic measurements across the globe and detects attacks
- reactive automation - chooses appropriate mitigations
- mitigations - executes mitigation logic on the edge
The benign-sounding "reactive automation" part is actually the most complicated stage in the pipeline. We expected that from the start, which is why we implemented this stage using a custom Functional Reactive Programming (FRP) framework. If you want to know more about it, see the talk and the presentation.
Is open source software a network security risk?
Networks are changing. More and more we’re hearing terms like whitebox, britebox, disaggregation, NOS, commodity hardware and open source when we talk about the future of networking. Since you’re reading this on the Cumulus Networks blog, I’ll assume you get that and spare you a description of these terms here. If you do want a crash course on network disaggregation and how it relates to orchestration/SDN, check out my previous post on the Packet Pushers blog.
With that bit of housekeeping out of the way, let’s dig right into today’s topic: open source software security.
First, why does security matter? If you’re like most network engineers, your primary goal typically is to get bits of data from one place to another. Anything that interferes with the free flow of packets and frames is a potential problem. So the goals of security can at first appear contrary to those of the network. Raise your hand if you’ve ever been frustrated by a firewall rule or some seemingly arcane security policy!
Unfortunately, we no longer have the luxury of ignoring security. Today’s network is one of the most crucial pieces of IT infrastructure for any organization and for the economies we operate in. Continue reading
FBI Blames North Korea for Malware, Kaspersky Lawsuits Dismissed
 The two malware families target U.S. media, aerospace, financial, and critical infrastructure sectors’ networks.
The two malware families target U.S. media, aerospace, financial, and critical infrastructure sectors’ networks.
Viewer’s Guide: Virtual Cloud Network Online Event
 Start Building the Virtual Cloud Network Today, join the online event June 5 at 11am PDT
Start Building the Virtual Cloud Network Today, join the online event June 5 at 11am PDT
You might not know it yet, but your network is holding you back. Unconnected clouds and data silos prevent your enterprise from securing and mining valuable data. VMware creates connections from your data center to the cloud to the edge – providing a secure, consistent foundation that drives business forward, rather than holding it back.
VMware recently announced our vision for the next era of networking – the Virtual Cloud Network. Join us for an exclusive online event to learn about how your organization can start building the network of the future. To prepare for this event, I not only spent time with the customers, technical leads and executives you hear from, but also behind the scenes, I have been part of many more conversations that I was not able to share. Pulling from those conversations, I’ve created your viewer’s guide for each segment of the event.
An overview of the Virtual Cloud Network by Rajiv Ramaswami, Chief Operating Officer, Products and Cloud Services
Rajiv and Pat share their executive views on the Virtual Cloud Network at the beginning of the event. To Continue reading
Sprint Uses 5G Network Preparations to Overhaul Its IoT Business
 Sprint hired former Vodafone IoT executive Ivo Rook to revamp its IoT business. Rook joined the company in January.
Sprint hired former Vodafone IoT executive Ivo Rook to revamp its IoT business. Rook joined the company in January.
AT&T and Tech Mahindra Sponsor an Artificial Intelligence Contest
 They're working with the Linux Foundation to host the Acumos AI Challenge, which seeks innovative open source AI solutions.
They're working with the Linux Foundation to host the Acumos AI Challenge, which seeks innovative open source AI solutions.