The NVMe Transition
A look at how vendors implementing the new storage protocol in their products and what to consider before integrating the technology into your data center.
Video: What Excites Me In Networking – Two Beer Networking
In the latest round of Two Beer Networking I talk about why I'm excited about whitebox hardware and formal verification. This show came from an audience question.Amazon Web Services Networking Overview
Traditional networking engineers, or virtualization engineers familiar with vSphere or VMware NSX, often feel like Alice in Wonderland when entering the world of Amazon Web Services. Everything looks and sounds familiar, and yet it all feels a bit different
I decided to create a half-day workshop (first delivery: June 13th in Zurich, Switzerland) to make it easier to grasp the fundamentals of AWS networking, and will publish high-level summaries as a series of blog posts. Let’s start with an overview of what’s different:
Read more ...APNIC Labs/CloudFlare DNS 1.1.1.1 Outage: Hijack or Mistake?
At 29-05-2018 08:09:45 UTC, BGPMon (A very well known BGP monitoring system to detect prefix hijacks, route leaks and instability) detected a possible BGP hijack of 1.1.1.0/24 prefix. Cloudflare Inc has been announcing this prefix from AS 13335 since 1st April 2018 after signing an initial 5-year research agreement with APNIC Research and Development (Labs) to offer DNS services.
Shanghai Anchang Network Security Technology Co., Ltd. (AS58879) started announcing 1.1.1.0/24 at 08:09:45 UTC, which is normally announced by Cloudflare (AS13335). The possible hijack lasted only for less than 2min. The last announcement of 1.1.1.0/24 was made at 08:10:27 UTC. The BGPlay screenshot of 1.1.1.0/24 is given below:

Anchang Network (AS58879) peers with China Telecom (AS4809), PCCW Global (AS3491), Cogent Communications (AS174), NTT America, Inc. (AS2914), LG DACOM Corporation (AS3786), KINX (AS9286) and Hurricane Electric LLC (AS6939). Unfortunately, Hurricane Electric (AS6939) allowed the announcement of 1.1.1.0/24 originating from Anchang Network (AS58879). Apparently, all other peers blocked this announcement. NTT (AS2914) and Cogent (AS174) are also MANRS Participants and actively filter prefixes.
Dan Goodin (Security Editor at Ars Technica, who extensively covers malware, computer espionage, botnets, and hardware hacking) reached Continue reading
Simple, Efficient, and Modern: VMware NSX introduces new HTML5 UI
Along with the advancements in context-aware micro-segmentation and network virtualization, we are also continually raising the bar on making VMware NSX simple to deploy, manage, and operationalize at scale – and that, of course, involves a responsive and easy-to-use HTML-based UI to access VMware NSX functionality.
With VMware NSX for vSphere 6.4.1, you can now access all NSX installation and security functionality through a responsive HTML-based vSphere Client, including Distributed Firewall, Service Composer, Application Rule Manager, and more. This modern interface does not have any dependencies on browser plugins (e.g. Adobe Flash), has a more minimalistic look-and-feel, and loads so much faster! Beyond the immediate aesthetic improvements, here’s a quick look at some of the key enhancements to how we’re simplifying the NSX user experience.
NSX Firewall – Better Visibility and Efficient Rule Management
Given how feature-rich the NSX Firewall page is, our usability designers focused extra attention on streamlining the day-to-day tasks of creating, managing and troubleshooting firewall rules.
For starters, at the top of the Firewall page, we’ve introduced a new Status Bar and elevated table-level actions (like Publish and Save) to their own dedicated Toolbar. Now, at a glance, you can immediately Continue reading
Linux Foundation Offers Free Open Networking Training
IT pros can sign up for new online course to learn the basics of open source networking technologies for SDN and more.
Datanauts 136: ChatOps Using PoshBot With Brandon Olin
On this episode of Datanauts, we chat with Brandon Olin, the creator of PoshBot, a PowerShell based chatbot for ops teams. What does PoshBot do? How was PoshBot built? How do chatbots impact Brandon’s delivery model?
ChatBots?
Bots have been around for a long time. They re really handy, too, often being able to answer simple questions by submitting a special command that has some sort of prefix or identifier associated with them. Especially if you re on Twitch and want to know how long your favorite streamer has been online.
Maybe that isn t the most helpful thing in the world, but what if we changed the narrative to be all about operations and how talking to a bot (with your peers watching) could actually up-level your day-to-day enjoyment of IT?
That’s our conversation today.
What is PoshBot?
PoshBot is a chat bot written in PowerShell. It makes extensive use of classes introduced in PowerShell 5.0. PowerShell modules are loaded into PoshBot and instantly become available as bot commands. PoshBot currently supports connecting to Slack to provide you with awesome ChatOps goodness.
For More Information About PoshBot
- PoshBot on GitHub, Home of the PoshBot Project
https://github.com/poshbotio - PoshBot Continue reading
AT&T’s Mixed Messages on 5G Fixed Wireless
 AT&T executives tout the company’s 5G fixed wireless trial results but cast doubt on the cost effectiveness of deploying the technology. Is the company just protecting its DirecTV business?
AT&T executives tout the company’s 5G fixed wireless trial results but cast doubt on the cost effectiveness of deploying the technology. Is the company just protecting its DirecTV business?
Kubernetes Driving Broader, Deeper Container Usage, Study Finds
 Organizations are packing 50 percent more running containers per host, with a vast majority running less than one hour.
Organizations are packing 50 percent more running containers per host, with a vast majority running less than one hour.
IBM’s New Cloud Data Service Targets Enterprise AI, Could Capture Microsoft’s Attention
 Recent updates ahead of its official launch included a product to help organizations deal with the EU's recently implemented GDPR rules.
Recent updates ahead of its official launch included a product to help organizations deal with the EU's recently implemented GDPR rules.
Cisco’s Cloud Team Contends With Old-School Cisco Sales Team
 Compton’s job will be to orchestrate across a hodge podge of clouds and internal business units. And he’ll need to inspire the sales force to sell cloud technology, too.
Compton’s job will be to orchestrate across a hodge podge of clouds and internal business units. And he’ll need to inspire the sales force to sell cloud technology, too.
French Hosting Provider Fends Off DDoS Attacks With NetScout vAPS
 As a hosting provider, Jaguar Networks has a higher risk of DDoS attacks because it aggregates its customers' risks in a shared infrastructure.
As a hosting provider, Jaguar Networks has a higher risk of DDoS attacks because it aggregates its customers' risks in a shared infrastructure.
Extending the Power of NSX to Bare-metal Workloads
Authors – Sridhar Subramanian and Geoff Wilmington
VMware NSX Data Center was built with the goal of consistent networking and security services independent of changing application frameworks or physical infrastructure. In the last couple of years, NSX Data Center has focused on delivering network and security abstractions for applications on any compute platform. In our journey, we have handled VM’s, containers, cloud, and now we are also looking to help our customers with scenarios where they need a unified experience for bare-metal workloads. The goal being to maintain a consistent security experience regardless of location or platform the workload is running on.
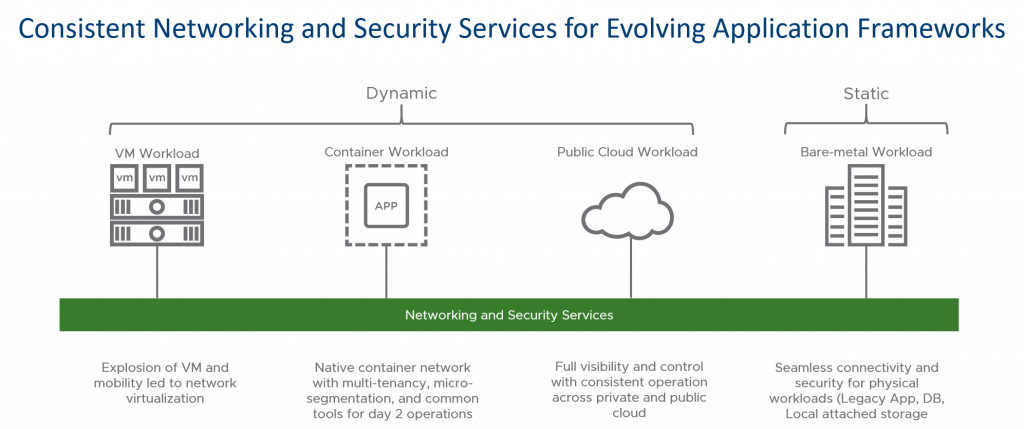
This experience means being able to take any workload, add it to an NSX Data Center Security Group and through the NSX Data Center Distributed Firewall have a consistent policy applied regardless of location and workload type. This consistent approach leverages the NSX DFW capabilities with stateful firewalling for the workloads. This is accomplished outside of using native OS capabilities like IP Tables or Windows Firewall so security admins only need to understand how to apply security through NSX DFW, and not have to understand the myriad of native OS approaches and complexity. By centralizing Continue reading
To Tackle the VPNFilter Botnet, It’s Going to Take Help from You and Me
If you’ve been reading the news lately, you might have seen headlines like “FBI to America: Reboot Your Routers, Right Now” or “F.B.I.’s Urgent Request: Reboot Your Router to Stop Russia-Linked Malware”. These headlines can be pretty alarming, and you may find yourself thinking, “things must be pretty bad if the FBI is putting out such an urgent warning.”
Cyber threats are not uncommon, but the good news is that the security community is working around the clock to tackle these threats as early and quickly as possible. Most of the time we do not see all this hard work, nor are we often asked to play a large part in taking down a botnet. But this time, by rebooting our routers, we can help the law enforcement and information security communities to identify infected routers so they can be cleaned up, moving us closer to a permanent fix for a particular kind of malware – VPNFilter.
Here is what happened …
From Discovery to Takedown
On 23 May, 2018, researchers at Cisco’s Talos publicly shared their findings about a large botnet of infected networking devices (home routers) they called “VPNFilter” because of concerns that the Continue reading