On Why I’m Shifting my Career Focus to Software
For the past few months I’ve been involved in a case study project with some colleagues at Cisco where we’ve been researching what the most relevant software skills are that Cisco’s pre-sales engineers could benefit from. We’re all freaking experts at Outlook of course (that’s a joke  ) but we were interested in the areas of programming, automation, orchestration, databases, analytics, and so on. The end goal of the project was to identify what those relevant skills are, have a plan to identify the current skillset in the field, do that gap analysis and then put forward recommendations on how to close the gap.
) but we were interested in the areas of programming, automation, orchestration, databases, analytics, and so on. The end goal of the project was to identify what those relevant skills are, have a plan to identify the current skillset in the field, do that gap analysis and then put forward recommendations on how to close the gap.
This probably sounds really boring and dry, and I don’t blame you for thinking that, but I actually chose this case study topic from a list of 8 or so. My motivation was largely selfish: I wanted to see first-hand the outcome of this project because I wanted to know how best to align my own training, study, and career in the software arena. I already believed that to stay relevant as my career moves along that software skills would be essential. It was just a question of what type of skills and in which specific areas.
EIGRP: A Multi-Vendor Demo
In this video, David Bombal runs the open version of Cisco's EIGRP protocol between a Linux-based router and Cisco devices.
Happy Eyeballs v2 (and how I Was Wrong Again)
In Moving Complexity to Application Layer I discussed the idea of trying to use all addresses returned in a DNS response when trying to establish a connection with a server, concluding with “I don’t think anyone big enough to influence browser vendors is interested in reinventing this particular wheel.”
I’m really glad to report I was wrong ;) This is what RFC 8305 (Happy Eyeballs v2) says:
Read more ...On Why I’m Shifting my Career Focus to Software
For the past few months I've been involved in a case study project with some colleagues at Cisco where we've been researching what the most relevant software skills are that Cisco's pre-sales engineers could benefit from. We're all freaking experts at Outlook of course (that's a joke ?) but we were interested in the areas of programming, automation, orchestration, databases, analytics, and so on. The end goal of the project was to identify what those relevant skills are, have a plan to identify the current skillset in the field, do that gap analysis and then put forward recommendations on how to close the gap.
This probably sounds really boring and dry, and I don't blame you for thinking that, but I actually chose this case study topic from a list of 8 or so. My motivation was largely selfish: I wanted to see first-hand the outcome of this project because I wanted to know how best to align my own training, study, and career in the software arena. I already believed that to stay relevant as my career moves along that software skills would be essential. It was just a question of what type of skills and in which specific Continue reading
Network Detective Ride-Along: Troubleshooting Multicast
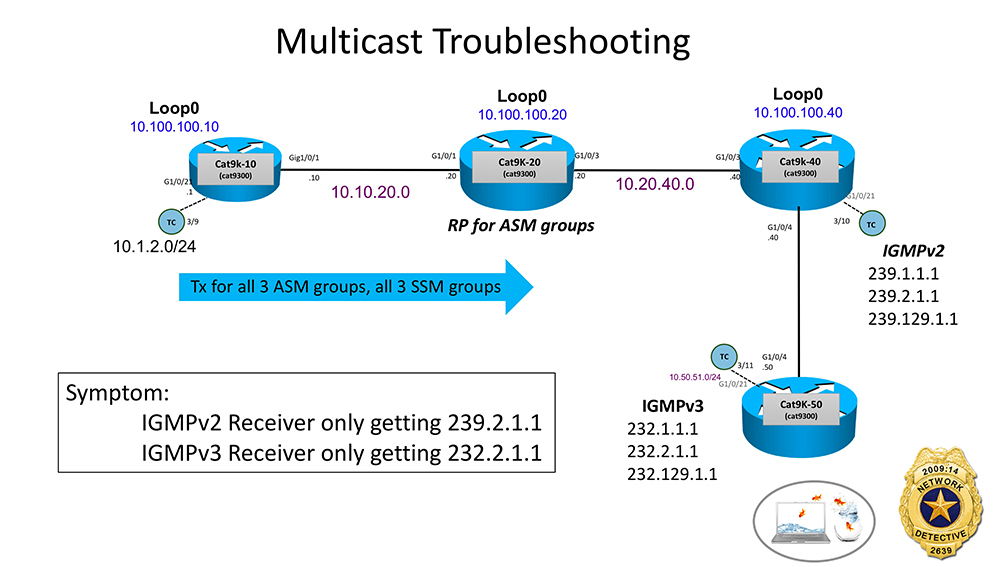
Grab your Network Detective badge! It’s time for another Network Detective ride-along.  Multicast this time.
Multicast this time.
We need to solve the case of the missing Multicast streams. ONLY 2 multicast streams (232.2.1.1 and 239.2.1.1) are getting thru to the hosts who requested them. The other 4 streams the same hosts requested are NOT getting thru. Let’s go to the crime scene and review the facts.
Fact #1 – Host off of Cat9K-40 is sending IGMPv2 membership reports to join ASM groups 239.1.1.1, 239.2.1.1 and 239.129.1.1
Fact #2 – Host off of Cat9K-50 is sending IGMPv3 membership reports to join SSM groups 232.1.1.1, 232.2.1.1 and 232.129.1.1
Fact #3 – All multicast sources are off of Cat9k-10 in subnet 10.1.2.0/24. They are sending the mcast for all 3 SSM groups and all 3 ASM groups
Fact #4 – Cat9K-20 is the Rendezvous Point (RP) for all 3 ASM groups
Any thoughts at first glance? Time to go to the YouTube ride-along ~11 minute video! Good luck! Have fun!
Raspberry Pi and AWS IOT – First steps
Hi All,
I have slightly changed this to networking, but the intention and my current use is to measure the water level of a sump, since that deviates from the network blog writing, i have extended the same to a Router.
Purpose – Have a Router and also a Syslog Server which monitors my internal network (This can easily be extended to a Car / Moisture Sensor or a Temperature/Humidity Sensor), what we want to do is to make sure if any anomaly is seen in Log Messages, it logs to IOT service. We can then take this up as a Part-2 writing to perform a specific action / automated on what action can be taken to mitigate
Discussion about configuring a Linux device is out of scope, so lets think that we all have that setup. What happens next ?
Lets quickly see our python script, which parses for a anomaly, in this lets say when someone runs a ping command, well its not a anomaly but will do for our use-case.
logparse.py is our program, so i have imported it into the readily available sample program provided by AWSIOT Kit, so you dont have to know Continue reading
Fun: Playing Battleships over BGP
BGP is the kitchen-sink of networking protocols, right? Whatever control-plane information you need to transport around, you can do it with BGP… including the battleship coordinates carried in BGP communities.
On the more serious front, it's nice to see at least some ISPs still care enough about the stability of the global Internet to use BGP route flap dampening.
Recover a RAID5 Array on Linux with healthy disks
Intel Atom failures I know the title sounds a bit weird and you may ask why would you need to recover a RAID5 array when all your disks are healthy, right? To understand what is going on, my DS1515+ has an Intel Atom C2538. (source: Synology CPU / NAS Type). It recently caused a lot of issues in the IT industry. (remember the Cisco clock issue? ? ) The Errata AVR54 of the C2000 Specifications update clearly states the following: “system may experience inability to boot or may cease operation”. My NAS was starting to have regular reboots and it completely crashed before I could back up the last delta of data. In the first instance, Synology denied any abnormal failure rate on this specific [Read More...]
The post Recover a RAID5 Array on Linux with healthy disks appeared first on VPackets.net.
NetDevOpEd: Disaggregation is key to software vulnerability management
One critical decision that executives need to make when assessing their data center architecture is their approach to software vulnerability management across all network components. Vulnerability management primarily revolves around selecting an efficient and modern software management strategy. There are several ways to execute on a software management strategy, and I believe disaggregation is a critical first step in doing it right.
In this post, I want to take a minute to first share my thoughts on the vulnerability management trends I’ve noticed. I will argue that a) you need to prioritize the network in how you manage vulnerabilities and b) disaggregation is the only way to do it properly. We’ll also take a look at the reasons why I think we never had the right framework to manage software delivery, making vulnerability management a challenge on platforms that are closed in nature.
Operations at the core of vulnerability management
Three weeks ago, I joined 40,000 security professionals in San Francisco to attend the biggest gathering of security conscious professionals — RSA Conference. While there were several presentations and moments from the event that stood out, one that caught my eye was a presentation that discussed challenges in the industry Continue reading
Link Propagation 120: Tasty Links For The Long Weekend
Welcome to Link Propagation, a Packet Pushers newsletter. Link Propagation is included in your free membership. Each week we hand-select the most relevant practitioner blog posts, tech news, and product announcements. We age them in oak barrels for up to seven days and then distill them using ancient craft techniques handed down by Tim Berners-Lee. […]Kip Compton’s Promotion Signals Bigger Cloud Strategy for Cisco
 The cloud touches all parts of Cisco’s business making this an important investment area for the company.
The cloud touches all parts of Cisco’s business making this an important investment area for the company.
Is There a Security Crisis in the Open Source Software Supply Chain?
 Following the Equifax breach, which exploited an open source framework library, many organizations increased their security postures, but that doesn't mean that open source is safe to use again.
Following the Equifax breach, which exploited an open source framework library, many organizations increased their security postures, but that doesn't mean that open source is safe to use again.
Nutanix CEO Talks ‘Sherlock’ Edge Platform, Blurred Lines Between Containers and VMs
 Sherlock, a cloud-based platform-as-a-service, will target IoT use cases and verticals including retail, manufacturing, health care, and oil and gas.
Sherlock, a cloud-based platform-as-a-service, will target IoT use cases and verticals including retail, manufacturing, health care, and oil and gas.
Containers Climb the Hype Cycle, as AT&T and Google Attest
 AT&T, Google, and Microsoft highlighted significant progress for the ecosystem, but an enterprise survey showed most remain on the sidelines of actual deployment.
AT&T, Google, and Microsoft highlighted significant progress for the ecosystem, but an enterprise survey showed most remain on the sidelines of actual deployment.
Show 391: IXP Peering Security With Cisco (Sponsored)
The Internet is a network of networks. Where do each of these networks meet to form the global Internet? At Internet Exchange Points or IXPs. In North America, these IXPs are also known as network access points, or NAPs.
Over the years, connecting to a NAP has become increasingly crucial for service providers to get right because of the sheer volume of traffic the Internet carries these days (Hello, Netflix!), the complexity of service provider peering agreements, and endless troubles with security threats.
Joining us today to discuss how to better plan, design, operate, and secure peering is our sponsor Cisco. Our guests from Cisco are Phil Bedard, Service Provider TME; and Bruce McDougall, Consulting Systems Engineer.
We discuss the evolution of Internet traffic flow and interconnection, how peering designs among service providers have changed, the role of telemetry and data, and peering security issues.
Show Links:
BGP Monitoring Protocol (BMP) – IETF
Internet Edge Peering – Current Practice – GitHub
BGP Operations and Security – IETF
Observing BGP activity with BGP Monitoring Protocol – Cisco
Streaming Network Analytics System (SNAS) – snas.io
The Death of Transit And Beyond – Geoff Huston (PDF)
Eyeball network – Wikipedia
The Continue reading