The Future is About the Business, Not the Technology
There has been plenty of change throughout the evolution of information technology. Now it's time for the corporate world to catch up and reshape how they do business and serve their customers.
Don’t Miss Keith Bogart’s May CCNA Kickoff!
It’s that time again! Tune in on May 7 at 10 am PST/ 1 pm EST for our monthly CCNA Kickoff session with expert instructor Keith Bogart.
This is a FREE session in which Keith (CCIE #4923) will present everything you need to know to get started on your CCNA journey.
What Keith will cover in this months webinar:
- How to get started by making a study schedule
- Strategies to prevent you from becoming overwhelmed throughout the exam process
- CCNA certification test format
- Which topics to study, and how in depth
- What study tools will be the most useful
- What to expect when you walk into the testing center
You can view this, and all of our other webinars here.
Oracle Cloud Drives The Factory’s Car Marketplace Into the Digital Age
 The pre-owned car marketplace app sometimes processes upwards of 20,000 vehicles in a busy weekend.
The pre-owned car marketplace app sometimes processes upwards of 20,000 vehicles in a busy weekend.
European Agenda on Digital for Development: Can the Multistakeholder Approach Help?
The year 2017 was an important milestone in moving forward the European agenda for Digital for Development (D4D). The European Commission (EC) paper on mainstreaming digital technologies into EU development policy and the European Council conclusions on Digital for Development have activated the European development community to share opinions and ideas on how to help bridge the global digital divide.
In the past month, we have had a couple of open events in Brussels to discuss this important issue. The European Parliament’s EPP group hosted a public hearing on Digitalisation for Development to collect ideas and to push for more progress. Two weeks later, the EC held the first multistakeholder meeting for Digital4Development with a focus on Africa.
Building a Balanced Agenda
There are a number of pillars of activities that most stakeholders agree on. These include Internet access with a focus on last mile; Internet as an enabler across different sectors; skills; and entrepreneurship. During the recent meetings, the EC, the national development agencies and the private sector showcased impressive and innovative digitalisation programmes.
However, several stakeholders pointed out that while it is important to continue to invest in Internet access, this is no longer enough. We need Continue reading
Short Take – Cisco Field Area Networking
In this Network Collective Short Take, guest commentator Nick Buraglio shares his thoughts on field area networking after watching Cisco’s presentation on the topic at Networking Field Day 17. You can see the original NFD17 presentation here: https://vimeo.com/253197120
The post Short Take – Cisco Field Area Networking appeared first on Network Collective.
Network Automation with Brigade on Software Gone Wild
David Barroso was sick-and-tired of using ZX Spectrum of Network Automation and decided to create an alternative with similar functionality but a proper programming language instead of YAML dictionaries masquerading as one. The result: Brigade, an interesting network automation tool we discussed in Episode 90 of Software Gone Wild.
Notes:
- If you want to test-drive Brigade, start here;
- To get the references at the end of our chat, watch this and this;
- David will talk about Brigade in autumn 2018 session of Building Network Automation Solutions online course.
Software-Defined Storage: The 5 Must-Haves You Need in Your Toolkit
 Software-defined storage is rising to the top of the storage market, but before selecting a solution, it’s important to determine the features and capabilities for your specific set of needs.
Software-defined storage is rising to the top of the storage market, but before selecting a solution, it’s important to determine the features and capabilities for your specific set of needs.
Radware Reports Third Consecutive Quarter of Double Digit Growth
 The company’s recent transition to a SaaS subscription model proves favorable as it reported an 11 percent increase in revenue year over year, along with several deals in the first quarter of 2018.
The company’s recent transition to a SaaS subscription model proves favorable as it reported an 11 percent increase in revenue year over year, along with several deals in the first quarter of 2018.
NetQ + Kubernetes: bringing container visibility with the leading container orchestrator
Businesses today have to get applications to market faster than ever, but with the same or less budget. Because of this requirement, modern data centers are evolving to support a change in application delivery. In order to get applications to market faster and increase revenue, applications that were once built as one monolithic entity are becoming segmented and deployed separately, communicating amongst themselves. The pieces of applications, sometimes referred to as microservices, are often deployed as containers. This results in much faster deployment and a quicker update cycle. However, the network teams operating the infrastructure supporting the applications often have no visibility into how their networks are being utilized, and thus are making design, operations and troubleshooting decisions blindly. Now, Cumulus NetQ provides this visibility from container deployments all the way to the spine switches and beyond — accelerating operations and providing the crucial information to efficiently design and operate the networks running containers.
Understanding the challenges of container management
Traditionally, the new application design and deployment method using containers makes operating and managing the infrastructure to support them very challenging. The containers often have to talk with each other within or across data centers or to the outside world. An Continue reading
Encryption Is Key to Safety of Journalists
At a time when we notice increasing and alarming threats to media freedom around the world, World Press Freedom Day (WPFD) is more pertinent today than ever before. We therefore can’t afford to celebrate this important day without both considering the damage done to the free press over the past year and intensifying our efforts to protect journalists and the future of journalism around the world.
To ensure that we can continue to celebrate the media’s vital role in democracies in the future, we must tackle the increasing number of Internet shutdowns around the world and find better ways to secure the safety of journalists.
Let’s start with the latter. The surveillance of journalists, in particular, has profound implications for democratic institutions, including freedom of the press. It threatens journalists’ ability to confidently and confidentially work with sources and to unlock information about controversial issues. It therefore hinders their ability to play their roles as watchdogs in democratic or undemocratic, developed or developing societies alike. But reports indicate that more and more journalists are at risk of facing state or societal surveillance.
Encryption offers a vital and relatively simple defense for such intrusions. Building on last year’s Continue reading
Google Secures 5 Partners for Its Cloud Security Command Center
 The five container-focused partners include Aqua Security, Capsule8, Stackrox, Sysdig Secure, and Twistlock.
The five container-focused partners include Aqua Security, Capsule8, Stackrox, Sysdig Secure, and Twistlock.
Equinix Interconnection Revenues Jump 16% in First Quarter 2018
 The data center giant also added private, direct connections to Microsoft Azure cloud services in Miami and Paris.
The data center giant also added private, direct connections to Microsoft Azure cloud services in Miami and Paris.
BiB 41: VMware NSX SD-WAN By VeloCloud
VMware's networking and cloud ambitions come into sharper focus with the introduction of NSX SD-WAN by VeloCloud.
The post BiB 41: VMware NSX SD-WAN By VeloCloud appeared first on Packet Pushers.
Cloud Provider RapidScale Offers Citrix NetScaler SD-WAN
 The partnership between a cloud provider and an SD-WAN vendor allows Citrix’s technology to run on a RapidScale’s global backbone.
The partnership between a cloud provider and an SD-WAN vendor allows Citrix’s technology to run on a RapidScale’s global backbone.
Call for Contributions to Northern Public Affairs: Internet Connectivity in Indigenous and Northern Communities
Northern Public Affairs, in collaboration with the Internet Society, is pleased to release a call for contributions to the Fall 2018 special issue of NPA Magazine focusing on emerging developments in community networks among Indigenous peoples in North America.
Internet connectivity for Indigenous Peoples in Canada and the United States has long been difficult to implement due to many environmental and socioeconomic factors such as remoteness of communities, difficulty gaining first mile access, reliable networks, slow speeds, expensive equipment, and high data costs. Community networks are communications infrastructure deployed and operated by local people, offering Indigenous communities a way to access the Internet to meet their own needs. For many, affordable, high-quality Internet access means community sustainability. Community networks encourage policymakers and regulators to examine new ways and means to fill local digital divides, like supporting local content in the appropriate language(s).
In this special edition issue of NPA Magazine the goal is to assemble diverse voices to explore the impact of access in the areas of education, healthcare, digital literacy, cultural/language promotion and preservation, as well as any negative impacts. We will seek existing Indigenous Community Networks and developing ones, highlighting successful and promising initiatives bringing Internet connectivity Continue reading
Against metrics: how measuring performance by numbers backfires | Aeon Ideas

Metrics lead to gaming the system
Custom Page Selection for Cloudflare Apps
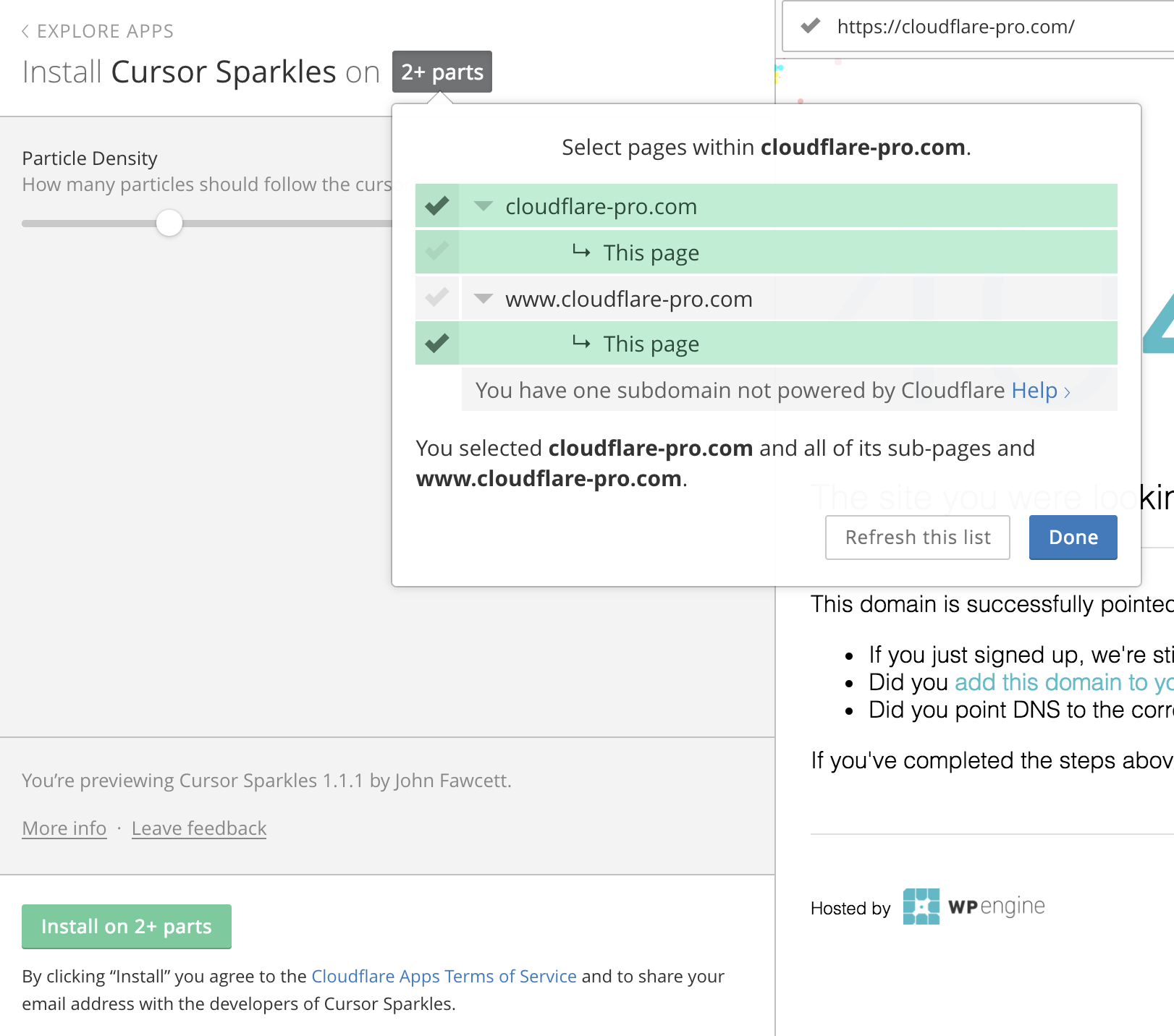
In July 2016, Cloudflare integrated with Eager - an apps platform. During this integration, several decisions were made to ensure an optimal experience installing apps. We wanted to make sure site owners on Cloudflare could customize and install an app with the minimal number of clicks possible. Customizability often adds complexity and clicks for the user. We’ve been tinkering to find the right balance of user control and simplicity since.
When installing an app, a site owner must select where - what URLs on their site - they want what apps installed. Our original plan for selecting the URLs an app would be installed on took a few twists and turns. Our end decision was to utilize our Always Online crawler to pre-populate a tree of the user’s site. Always Online is a feature that crawls Cloudflare sites and serves pages from our cache if the site goes down.
The benefits to this original setup are:
1. Only valid pages appear
An app only allows installations on html pages. For example, since injecting Javascript into a JPEG image isn’t possible, we would prevent the installer from trying it by not showing that path. Preventing the user from that type of Continue reading
Networking Pros: Get Out of Your Comfort Zone
Surviving tumultuous times in enterprise IT means networking pros need to focus on learning new skills and participating in the community, panelists at Interop ITX said.