VMware Boosts Cloud Management Automation, Promises Azure Support Soon
 VMware added new cloud management automation capabilities to its data center software and said Microsoft Azure support is “very near.”
VMware added new cloud management automation capabilities to its data center software and said Microsoft Azure support is “very near.”
Hybrid Cloud Security 101: What IT Leaders Need to Know
 Hybrid cloud environments present a revolutionary change in how organizations store and manage their data. But what happens if access to the cloud is compromised or interrupted?
Hybrid cloud environments present a revolutionary change in how organizations store and manage their data. But what happens if access to the cloud is compromised or interrupted?
Docker CTO Solomon Hykes Will Leave the Company He Co-Founded
 Hykes said the reason behind the move is because Docker Inc.’s current business requires a CTO with decades of experience shipping and supporting software.
Hykes said the reason behind the move is because Docker Inc.’s current business requires a CTO with decades of experience shipping and supporting software.
Nokia Will Slash 353 Jobs in Network, Technology Units
 Nokia total revenues dipped 1 percent to $8.3 billion in the fourth quarter of 2017.
Nokia total revenues dipped 1 percent to $8.3 billion in the fourth quarter of 2017.
Riga, Tallinn and Vilnius: Launching three new European Cloudflare data centers


Cloudflare announces the turn up of our newest data centers located in Riga (Latvia), Tallinn (Estonia) and Vilnius (Lithuania). They represent the 140th, 141st and 142nd cities across our growing global network, and our 37th, 38th, 39th cities in Europe. We are very excited to help improve the security and performance of over 7 million Internet properties across 72 countries including the Baltic states.
We will be interconnecting with local networks over multiple Internet exchanges: Baltic Internet Exchange (BALT-IX), Lithuanian Internet eXchange Point (LIXP), LITIX, Tallinn Internet Exchange (TLLIX), Tallinn Governmental Internet Exchange (RTIX), Santa Monica Internet Local Exchange (SMILE-LV), and potentially, the Latvian Internet Exchange (LIX-LV).
If you are an entrepreneur anywhere in the world selling your product in these markets, or a Baltic entrepreneur reaching a global audience, we've got your back.
Baltic Region
Photo by Siim Lukka / Unsplash
Latvia, Estonia and Lithuania join the list of other countries with shorelines along the Baltic Sea and Cloudflare data centers. That list includes Denmark, Finland, Germany, Poland, Russia and Sweden.
Of the five countries that in the drainage basin but do not border the sea, Cloudflare has deployments Continue reading
Cognitive Cloud Networking with Arista X3 Series
At Arista we have always embraced open networking trends by designing our hardware and software to be as programmable as possible, driving the use of merchant silicon and diversity for the broader industry. It has allowed our customers to select their favorite silicon architectures for the switch pipeline and choose the suite of software and hardware they want to form their cognitive network systems.
Cognitive Cloud Networking with Arista X3 Series
At Arista we have always embraced open networking trends by designing our hardware and software to be as programmable as possible, driving the use of merchant silicon and diversity for the broader industry. It has allowed our customers to select their favorite silicon architectures for the switch pipeline and choose the suite of software and hardware they want to form their cognitive network systems.
Data Center Career: Automate or Be Automated
With microservices driving data center automation, IT professionals need to prepare by adding new skills such as DevOps.
Data Center Career: Automate or Be Automated
With microservices driving data center automation, IT professionals need to prepare by adding new skills such as DevOps.
eBPF, Sockets, Hop Distance and manually writing eBPF assembly
A friend gave me an interesting task: extract IP TTL values from TCP connections established by a userspace program. This seemingly simple task quickly exploded into an epic Linux system programming hack. The result code is grossly over engineered, but boy, did we learn plenty in the process!

CC BY-SA 2.0 image by Paul Miller
Context
You may wonder why she wanted to inspect the TTL packet field (formally known as "IP Time To Live (TTL)" in IPv4, or "Hop Count" in IPv6)? The reason is simple - she wanted to ensure that the connections are routed outside of our datacenter. The "Hop Distance" - the difference between the TTL value set by the originating machine and the TTL value in the packet received at its destination - shows how many routers the packet crossed. If a packet crossed two or more routers, we know it indeed came from outside of our datacenter.
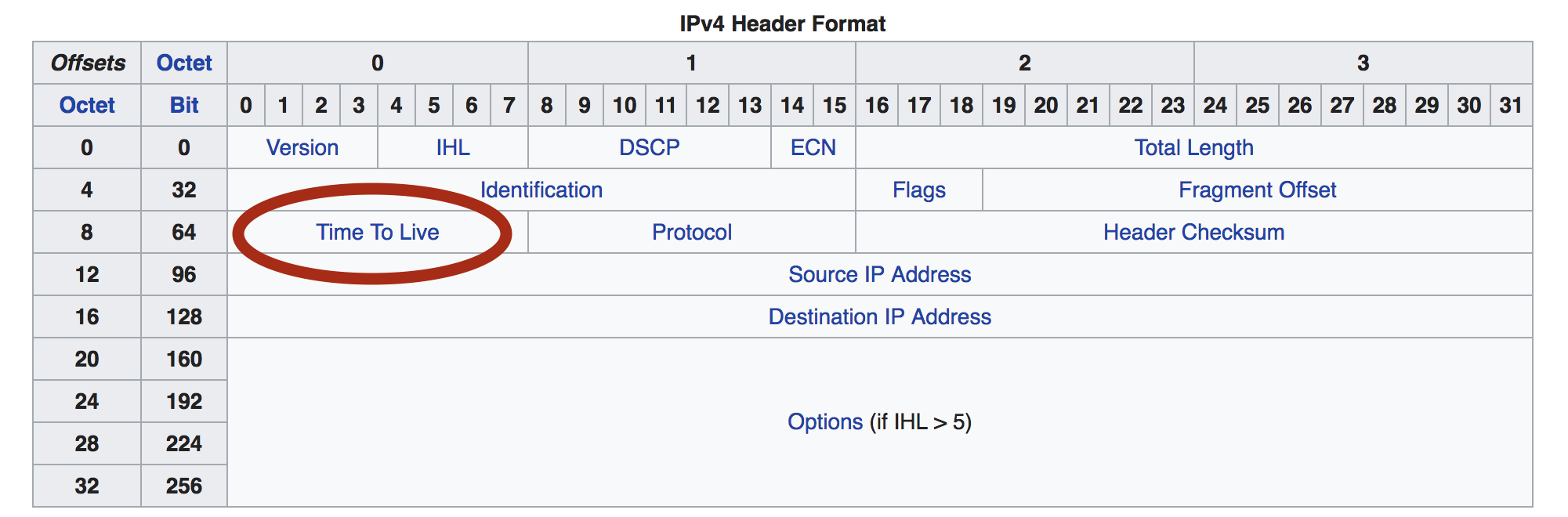
It's uncommon to look at TTL values (except for their intended purpose of mitigating routing loops by checking when the TTL reaches zero). The normal way to deal with the problem we had would be to blacklist IP ranges of our servers. But it’s not that Continue reading
Protecting the Network from Ransomware
Follow these security best practices to prevent your organization from falling victim to a ransomware attack.
Protecting the Network from Ransomware
Follow these security best practices to prevent your organization from falling victim to a ransomware attack.
VXLAN Limitations of Data Center Switches
One of my readers found this Culumus Networks article that explains why you can’t have more than a few hundred VXLAN-based VLAN segments on every port of 48-port Trident-2 data center switch.
Expect to see similar limitations in most other chipsets. There’s a huge gap between millions of segments enabled by 24-bit VXLAN Network Identifier and reality of switching silicon. Most switching hardware is also limited to 4K VLANs.
Read more ...Cloudflare is adding Drupal WAF Rule to Mitigate Critical Drupal Exploit
Drupal has recently announced an update to fix a critical remote code execution exploit (SA-CORE-2018-002/CVE-2018-7600). In response we have just pushed out a rule to block requests matching these exploit conditions for our Web Application Firewall (WAF). You can find this rule in the Cloudflare ruleset in your dashboard under the Drupal category with the rule ID of D0003.
Drupal Advisory: https://www.drupal.org/sa-core-2018-002


