The Overoptimization Meltdown
In simple terms Meltdown and Spectre are simple vulnerabilities to understand. Imagine a gang of thieves waiting for a stage coach carrying a month’s worth of payroll.
There are two roads the coach could take, and a fork, or a branch, where the driver decides which one to take. The driver could take either one. What is the solution? Station robbers along both sides of the branch, and wait to see which one the driver chooses. When you know, pull the resources from one branch to the other, so you can effectively rob the stage. This is much the same as a modern processor handling a branch—the user could have put anything into some field, or retreived anything from a database, that might cause the software to run one of two sets of instructions. There is no way for the processor to know, so it runs both of them.
To run both sets of instructions, the processor will pull in the contents of specific memory locations, and begin exexuting code across these memory locations. Some of these memory locations might not be pieces of memory the currently running software is supposed to be able to access, but this is not Continue reading
Security Startup Arctic Wolf Raises $49M for SOC Services
 The service includes cloud-based security information and event management.
The service includes cloud-based security information and event management.
Meet and Greet in Silicon Valley from 15 Jan – 3 Feb 2018
 I’ve reduced the travel and conferences I’m attending in 2018 to focus on content – writing, podcasting and video is my future. The negative impact is that I’ll miss meeting many people in the industry. So I am spending 3 weeks in San Jose 15 Jan – 3 Feb 2018 and hoping to meet as many […]
I’ve reduced the travel and conferences I’m attending in 2018 to focus on content – writing, podcasting and video is my future. The negative impact is that I’ll miss meeting many people in the industry. So I am spending 3 weeks in San Jose 15 Jan – 3 Feb 2018 and hoping to meet as many […]
Apcela Preps for What’s Next with Funding and New President
 Its product overlays application delivery and monitoring on SD-WANs from Cisco and Versa Networks.
Its product overlays application delivery and monitoring on SD-WANs from Cisco and Versa Networks.
U.S. Congressman Bashes ZTE and Huawei in New Bill
 The bill would prohibit the U.S. government from buying from the companies.
The bill would prohibit the U.S. government from buying from the companies.
Network Break 167: Meltdown & Spectre Strike; Oracle CEO Predicts IT Shakeout
Listen to this week Network Break as we examine the Meltdown and Spectre vulnerabilities, Oracle CEO Mark Hurd's remarks about the disruption of traditional IT & more tech news. The post Network Break 167: Meltdown & Spectre Strike; Oracle CEO Predicts IT Shakeout appeared first on Packet Pushers.Can IPv4 Networks Be Compromised via IPv6?
Fox-IT is recommending that IPv6 is disabled when it is not being used, as disabling Proxy Auto Detection. This of course means that Windows-based hosts are unable to switch preference to IPv6 when it is available (which all versions since Windows Vista will do), and that IPv6 would need to be explicitly re-enabled on hosts.
The article makes some important points, but IPv4 and IPv6 are fundamentally incompatible on a wire level and it needs to be understood they can’t communicate with each other except through translation devices. There are a number of known issues (including this one) with the security of automatic configuration mechanisms running on Local Area Networks, both under IPv6 and IPv4, but these require physical access to Continue reading
SYN packet handling in the wild
Here at Cloudflare, we have a lot of experience of operating servers on the wild Internet. But we are always improving our mastery of this black art. On this very blog we have touched on multiple dark corners of the Internet protocols: like understanding FIN-WAIT-2 or receive buffer tuning.

CC BY 2.0 image by Isaí Moreno
One subject hasn't had enough attention though - SYN floods. We use Linux and it turns out that SYN packet handling in Linux is truly complex. In this post we'll shine some light on this subject.
The tale of two queues
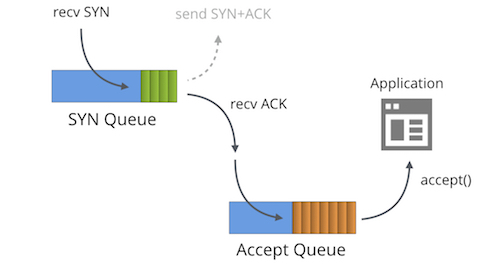
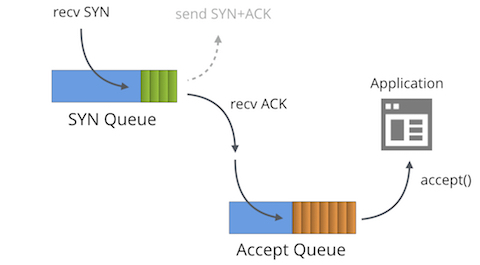
First we must understand that each bound socket, in the "LISTENING" TCP state has two separate queues:
- The SYN Queue
- The Accept Queue
In the literature these queues are often given other names such as "reqsk_queue", "ACK backlog", "listen backlog" or even "TCP backlog", but I'll stick to the names above to avoid confusion.
SYN Queue
The SYN Queue stores inbound SYN packets[1] (specifically: struct inet_request_sock). It's responsible for sending out SYN+ACK packets and retrying them on timeout. On Linux the number of retries is configured with:
$ sysctl net.ipv4.tcp_synack_retries
net.ipv4.tcp_synack_retries = 5
Meltdown and Its Networking Equivalents
One of my readers sent me this question:
Do you have any thoughts on this meltdown HPTI thing? How does a hardware issue/feature become a software vulnerability? Hasn't there always been an appropriate level of separation between kernel and user space?
There’s always been privilege-level separation between kernel and user space, but not the address space separation - kernel has been permanently mapped into the high-end addresses of user space (but not visible from the user-space code on systems that had decent virtual memory management hardware) since the days of OS/360, CP/M and VAX/VMS (RSX-11M was an exception since it ran on 16-bit CPU architecture and its designers wanted to support programs up to 64K byte in size).
Read more ...Salt From The Start To The Beginning
Salt quick start guide.Salt From The Start To The Beginning
As described by their website; Salt is "Event-driven automation for a software-defined world". You gotta love marketing :) Salt is a large project with many features including; configuration management, an event based reactor, cloud management and network automation. Salt can do ALOT but...NSX-T: OpenAPI and SDKs
Nowadays everything is about automation. Organizations are moving away from the traditional static infrastructure to full automation and here the need of NSX is significant. There are many use-cases for NSX, but the common in all of them is that they all need to be automated.
VMware is investing heavenly for different tools to ease the automation aspect of NSX but in order to take full advantage of it one need to understand what happens under the hood. It is also important if someone wants to build their own custom automation tool or CMP (Cloud Management Platform). Many existing solutions like Openstack, Kubernetes, vRO and so on automate NSX-T using different plugins. In fact, those plugins are sending REST API calls to NSX Manager in order to automate logical topology CRUD(Create, Read, Update, Delete) operations.
Based on our experience we decided that NSX-T APIs will be based on JSON format following OpenAPI standard. The use of Open APIs is to enable third party developers to build applications and services around NSX-T by standardising on how REST APIs are described. This means one can use standard tools like Swagger to read and use those APIs. Below is a quick example from my Mac on Continue reading
Worth Reading: Robust IPAM
Elisa Jasinska covered several IPAMs in her overview of open-source network automation tools, and we had Jeremy Stretch talking about NetBox in the Building Network Automation Solutions online course, but if you’re looking for a really robust easy-to-implement solution, check out this document from 1998 (deployment experience, including a large-scale one).
Deleting Checkpoint Logs
The directories that need to be emptied to delete all the logs on the Checkpoint managers.
Checkpoint Identity Awareness
The 3 main elements that run identity awareness under the hub are Active Directory Query (ADQ), PDP and PEP. They all intertwine in some way to allow the different blades of the Checkpoint to track and restrict access based on AD user and machine name. I tested these features as part of a POC and personally I would not consider them fit for purpose in a production environment. See the caveats at the end of the post for more details on this.