Concise (Post-Christmas) Cryptography Challenges

It's the day after Christmas; or, depending on your geography, Boxing Day. With the festivities over, you may still find yourself stuck at home and somewhat bored.
Either way; here are three relatively short cryptography challenges, you can use to keep you momentarily occupied. Other than the hints (and some internet searching), you shouldn't require a particularly deep cryptography knowledge to start diving into these challenges. For hints and spoilers, scroll down below the challenges!

Challenges
Password Hashing
The first one is simple enough to explain; here are 5 hashes (from user passwords), crack them:
$2y$10$TYau45etgP4173/zx1usm.uO34TXAld/8e0/jKC5b0jHCqs/MZGBi
$2y$10$qQVWugep3jGmh4ZHuHqw8exczy4t8BZ/Jy6H4vnbRiXw.BGwQUrHu
$2y$10$DuZ0T/Qieif009SdR5HD5OOiFl/WJaDyCDB/ztWIM.1koiDJrN5eu
$2y$10$0ClJ1I7LQxMNva/NwRa5L.4ly3EHB8eFR5CckXpgRRKAQHXvEL5oS
$2y$10$LIWMJJgX.Ti9DYrYiaotHuqi34eZ2axl8/i1Cd68GYsYAG02Icwve
HTTP Strict Transport Security
A website works by redirecting its www. subdomain to a regional subdomain (i.e. uk.), the site uses HSTS to prevent SSLStrip attacks. You can see cURL requests of the headers from the redirects below, how would you practically go about stripping HTTPS in this example?
$ curl -i http://www.example.com
HTTP/1.1 302 Moved Temporarily
Server: nginx
Date: Tue, 26 Dec 2017 12:26:51 GMT
Content-Type: text/html
Transfer-Encoding: chunked
Connection: keep-alive
location: https://uk.example.com/
$ curl -i http://uk.example.com
HTTP/1.1 200 OK
Server: nginx
Content-Type: text/html; Continue readingAlibaba Cloud Gears Up for ‘Serious Combat’ Against AWS in 2018
 Alibaba Cloud has 33 availability zones across 16 economic centers globally.
Alibaba Cloud has 33 availability zones across 16 economic centers globally.
NFV Creeps into Networks in Different Ways
 NFV gets into networks via SD-WAN, turnkey software stacks, and proprietary systems.
NFV gets into networks via SD-WAN, turnkey software stacks, and proprietary systems.
Managing Switches with REST and Thrift APIs
Learn how to use APIs for networking in this excerpt from "Building Modern Networks."
The History of Stock Quotes
In honor of all the fervor around Bitcoin, we thought it would be fun to revisit the role finance has had in the history of technology even before the Internet came around. This was adapted from a post which originally appeared on the Eager blog.
The issue was not the lack of a rapid communication system in France, it just hadn’t expanded far enough yet. France had an elaborate semaphore system. Arranged all around the French countryside were buildings with mechanical flags which could be rotated to transmit specific characters to the next station in line. When the following station showed the same flag positions as this one, you knew the letter was acknowledged, and you could show the next character. This system allowed roughly one character to be transmitted per minute, with the start of a message moving down the line at almost 900 miles per hour. It wouldn’t expand to Toulouse until 1834 however, Continue reading
The History of Stock Quotes

In honor of all the fervor around Bitcoin, we thought it would be fun to revisit the role finance has had in the history of technology even before the Internet came around. This was adapted from a post which originally appeared on the Eager blog.
The issue was not the lack of a rapid communication system in France, it just hadn’t expanded far enough yet. France had an elaborate semaphore system. Arranged all around the French countryside were buildings with mechanical flags which could be rotated to transmit specific characters to the next station in line. When the following station showed the same flag positions as this one, you knew the letter was acknowledged, and you could show the next character. This system allowed roughly one character to be transmitted per minute, with the start of a message moving down the line at almost 900 miles per hour. It wouldn’t expand to Toulouse until 1834 however, Continue reading
Simple Cyber Security Tips (for your Parents)

Today, December 25th, Cloudflare offices around the world are taking a break. From San Francisco to London and Singapore; engineers have retreated home for the holidays (albeit with those engineers on-call closely monitoring their mobile phones).
Software engineering pro-tip:
— Chris Albon (@chrisalbon) December 20, 2017
Do not, I repeat, do not deploy this week. That is how you end up debugging a critical issue from your parent's wifi in your old bedroom while your spouse hates you for abandoning them with your racist uncle.
Whilst our Support and SRE teams operated on a schedule to ensure fingers were on keyboards; on Saturday, I headed out of the London bound for the Warwickshire countryside. Away from the barracks of the London tech scene, it didn't take long for the following conversation to happen:
- Family member: "So what do you do nowadays?"
- Me: "I work in Cyber Security."
- Family member: "There seems to be a new cyber attack every day on the news! What can I possibly do to keep myself safe?"
If you work in the tech industry, you may find a family member asking you for advice on cybersecurity. This blog post will hopefully save you Continue reading
Simple Cyber Security Tips (for your Parents)

Today, December 25th, Cloudflare offices around the world are taking a break. From San Francisco to London and Singapore; engineers have retreated home for the holidays (albeit with those engineers on-call closely monitoring their mobile phones).
Software engineering pro-tip:
— Chris Albon (@chrisalbon) December 20, 2017
Do not, I repeat, do not deploy this week. That is how you end up debugging a critical issue from your parent's wifi in your old bedroom while your spouse hates you for abandoning them with your racist uncle.
Whilst our Support and SRE teams operated on a schedule to ensure fingers were on keyboards; on Saturday, I headed out of the London bound for the Warwickshire countryside. Away from the barracks of the London tech scene, it didn't take long for the following conversation to happen:
- Family member: "So what do you do nowadays?"
- Me: "I work in Cyber Security."
- Family member: "There seems to be a new cyber attack every day on the news! What can I possibly do to keep myself safe?"
If you work in the tech industry, you may find a family member asking you for advice on cybersecurity. This blog post will hopefully save you Continue reading
Top 5 Blogs of 2017 – Build and run your first Docker Windows Server container
As 2017 comes to a close, we looked back at the top five blogs that were most popular with our readers. For those of you that have yet to set up your first Docker Windows container, we are kicking off the week with a blog that will help you get up and running on Windows containers.
Earlier this year, Microsoft announced the general availability of Windows Server 2016, and with it, Docker engine running containers natively on Windows. This blog post describes how to get setup to run Docker Windows Containers on Windows 10 or using a Windows Server 2016 VM. Check out the companion blog posts on the technical improvements that have made Docker containers on Windows possible and the post announcing the Docker Inc. and Microsoft partnership.
Before getting started, It’s important to understand that Windows Containers run Windows executables compiled for the Windows Server kernel and userland (either windowsservercore or nanoserver). To build and run Windows containers, a Windows system with container support is required.
Windows 10 with Anniversary Update
For developers, Windows 10 is a great place to run Docker Windows containers and containerization support was added to the the Windows 10 kernel with the Anniversary Continue reading
How Kubernetes Conquered 2017 (and is Positioned for 2018)
 Rivals and major cloud providers are all part of the push.
Rivals and major cloud providers are all part of the push.
General – Merry Christmas And A Little Gift
Hi all,
I had some issues with the site and I haven’t blogged as much lately as I would have hoped but I wanted to wish you a Merry Christmas and send you a little gift from Martin Duggan.
Martin recently released part two of his CCDE Practical Scenarios. Like the last time he is giving you, my readers a discount when you buy it from Leanpub. It’s a really good scenario and you have to stay focused and do your best even if you are not comfortable with the scenario. This is very much how the real scenarios are. You may not be comfortable working with say a cable provider but that might be the scenario you are given. Focus on what is important and find the requirements and constraints and answer as best you can.
Follow this link to receive a discount on the scenario.
Merry Christmas!
The post General – Merry Christmas And A Little Gift appeared first on Daniels Networking Blog.
TLS 1.3 is going to save us all, and other reasons why IoT is still insecure
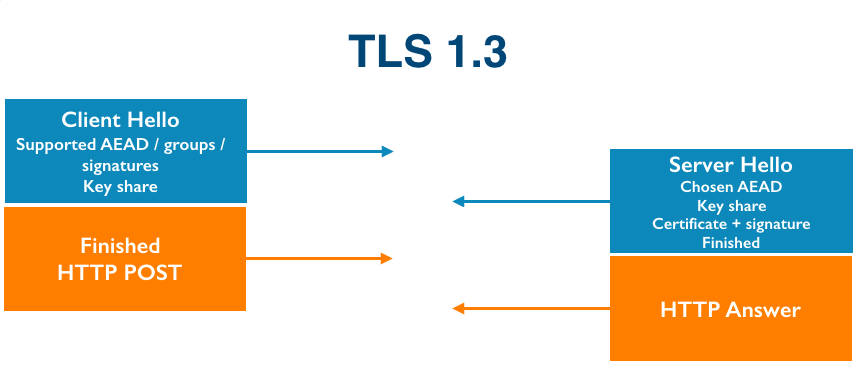
As I’m writing this, four DDoS attacks are ongoing and being automatically mitigated by Gatebot. Cloudflare’s job is to get attacked. Our network gets attacked constantly.
Around the fall of 2016, we started seeing DDoS attacks that looked a little different than usual. One attack we saw around that time had traffic coming from 52,467 unique IP addresses. The clients weren’t servers or desktop computers; when we tried to connect to the clients over port 80, we got the login pages to CCTV cameras.
Obviously it’s important to lock down IoT devices so that they can’t be co-opted into evil botnet armies, but when we talk to some IoT developers, we hear a few concerning security patterns. We’ll dive into two problematic areas and their solutions: software updates and TLS.
The Trouble With Updates
With PCs, the end user is ultimately responsible for securing their devices. People understand that they need to update their computers and phones. Just 4 months after Apple released iOS 10, it was installed on 76% of active devices.
People just don’t know that they are supposed to update IoT things like they are supposed to update their computers because they’ve never had to update things Continue reading
TLS 1.3 is going to save us all, and other reasons why IoT is still insecure

As I’m writing this, four DDoS attacks are ongoing and being automatically mitigated by Gatebot. Cloudflare’s job is to get attacked. Our network gets attacked constantly.
Around the fall of 2016, we started seeing DDoS attacks that looked a little different than usual. One attack we saw around that time had traffic coming from 52,467 unique IP addresses. The clients weren’t servers or desktop computers; when we tried to connect to the clients over port 80, we got the login pages to CCTV cameras.
Obviously it’s important to lock down IoT devices so that they can’t be co-opted into evil botnet armies, but when we talk to some IoT developers, we hear a few concerning security patterns. We’ll dive into two problematic areas and their solutions: software updates and TLS.
The Trouble With Updates
With PCs, the end user is ultimately responsible for securing their devices. People understand that they need to update their computers and phones. Just 4 months after Apple released iOS 10, it was installed on 76% of active devices.
People just don’t know that they are supposed to update IoT things like they are supposed to update their computers because they’ve never had to update things Continue reading
Introduction to Uni-Directional Link Detection (UDLD) Protocol
 |
| Fig 1.1- UDLD Protocol Tx and Rx |
Switching Basics : STP Root Bridge Election Procedure
Displaying Pi Output on an LCD
A few weeks ago, I shared an article about leveraging the Meraki API and a Raspberry Pi to create a Dummy Light for My Network. Today’s article expands on this slightly by adding a 16×2 LCD Display for additional output flexibility. For the sake of demonstration, we will continue to use the Meraki API as the source of what will be displayed. An example of what I have built is shown immediately below in this short video.
TL;DR
To accomplish this, I added the HD44780 to my Raspberry Pi (Pi 2 Model B) using the following pinout.
#connect LCD Pin 1 (VSS) to Ground #connect LCD Pin 2 (VDD) to 5v rail #connect LCD Pin 3 (VO) to potentiometer #connect LCD Pin 4 (RS) to 37 #connect LCD Pin 5 (RW) to Ground #connect LCD Pin 6 (E) to 35 #connect LCD Pin 12 #connect LCD Pin 13 #connect LCD Pin 14 #connect LCD Pin 15 #connect LCD andode (a) to 5v rail (Phy Pin 2) with resistance #connect LCD cathode (k) to Ground Rail (Phy Pin 6) #connect potentiometer to 5v and ground rails

Next, I wrote the following Python Script.
import requests import json import RPi.GPIO as GPIO import Continue reading
Displaying Pi Output on an LCD
A few weeks ago, I shared an article about leveraging the Meraki API and a Raspberry Pi to create a Dummy Light for My Network. Today’s article expands on this slightly by adding a 16×2 LCD Display for additional output flexibility. For the sake of demonstration, we will continue to use the Meraki API as the source of what will be displayed. An example of what I have built is shown immediately below in this short video.
TL;DR
To accomplish this, I added the HD44780 to my Raspberry Pi (Pi 2 Model B) using the following pinout.
#connect LCD Pin 1 (VSS) to Ground #connect LCD Pin 2 (VDD) to 5v rail #connect LCD Pin 3 (VO) to potentiometer #connect LCD Pin 4 (RS) to 37 #connect LCD Pin 5 (RW) to Ground #connect LCD Pin 6 (E) to 35 #connect LCD Pin 12 #connect LCD Pin 13 #connect LCD Pin 14 #connect LCD Pin 15 #connect LCD andode (a) to 5v rail (Phy Pin 2) with resistance #connect LCD cathode (k) to Ground Rail (Phy Pin 6) #connect potentiometer to 5v and ground rails

Next, I wrote the following Python Script.
import requests import json import RPi.GPIO as GPIO import Continue reading
Displaying Pi Output on an LCD
A few weeks ago, I shared an article about leveraging the Meraki API and a Raspberry Pi to create a Dummy Light for My Network. Today’s article expands on this slightly by adding a 16×2 LCD Display for additional output flexibility. For the sake of demonstration, we will continue to use the Meraki API as the source of what will be displayed. An example of what I have built is shown immediately below in this short video.
TL;DR
To accomplish this, I added the HD44780 to my Raspberry Pi (Pi 2 Model B) using the following pinout.
#connect LCD Pin 1 (VSS) to Ground #connect LCD Pin 2 (VDD) to 5v rail #connect LCD Pin 3 (VO) to potentiometer #connect LCD Pin 4 (RS) to 37 #connect LCD Pin 5 (RW) to Ground #connect LCD Pin 6 (E) to 35 #connect LCD Pin 12 #connect LCD Pin 13 #connect LCD Pin 14 #connect LCD Pin 15 #connect LCD andode (a) to 5v rail (Phy Pin 2) with resistance #connect LCD cathode (k) to Ground Rail (Phy Pin 6) #connect potentiometer to 5v and ground rails

Next, I wrote the following Python Script.
import requests import json import RPi.GPIO as GPIO import Continue reading
My new Journey – Cisco to Google cloud
After an amazing 10+ years stint in Cisco Systems, I have decided to move on. I have joined Google’s cloud division. I thought its a good time to reflect on my learnings in Cisco and what I am looking forward for the next few years. Before joining Cisco, I worked in few startups in US. … Continue reading My new Journey – Cisco to Google cloudWhen it Comes to Software-Defined Storage, The Particulars are Important
 The SDS market is projected to grow 29 percent each year between now and 2025.
The SDS market is projected to grow 29 percent each year between now and 2025.
