Thoughts on Open/R
Since Facebook has released their Open/R routing platform, there has been a lot of chatter around whether or not it will be a commercial success, whether or not every hyperscaler should use the protocol, whether or not this obsoletes everything in routing before this day in history, etc., etc. I will begin with a single point.
If you haven’t found the tradeoffs, you haven’t looked hard enough.
Design is about tradeoffs. Protocol design is no different than any other design. Hence, we should expect that Open/R makes some tradeoffs. I know this might be surprising to some folks, particularly in the crowd that thinks every new routing system is going to be a silver bullet that solved every problem from the past, that the routing singularity has now occurred, etc. I’ve been in the world of routing since the early 1990’s, perhaps a bit before, and there is one thing I know for certain: if you understand the basics, you would understand there is no routing singularity, and there never will be—at least not until someone produces a quantum wave routing protocol.
Ther reality is you always face one of two choices in routing: build a protocol specifically tuned Continue reading
OpenStack and CITC – Creating and learning about OpenStack networking
Part 1 – Examining the existing network
In my previous post, I was playing around with Cumulus in the Cloud (CITC) and how it was integrated with OpenStack. Now that I was playing with OpenStack in CITC, I wanted to dive deeper into the networking specific technology.
In this blog post I will be discussing how I leveraged a flat network to initially create simple instance deployments. Then I’ll dive more deeply into how I created a VXLAN network for my OpenStack instances to create more scalable east-west communication. In the previous post I used the CITC console as my primary interface for configuration. This time I will be using an SSH client and the direct SSH information, as the outputs I’m gathering have wider width that is easier to obtain via an SSH client.
To do so, I just clicked the SSH access button on the right hand side of the GUI. This provided me with the username, password and IP address that would allow me to use my own SSH client to connect to the CITC infrastructure.
For the uninitiated, here is a great intro doc into OpenStack networking. In addition, my colleague Eric Pulvino pointed me Continue reading
Living In A Multi-Cloud World

A few months ago at Cloudflare’s Internet Summit, we hosted a discussion on A Cloud Without Handcuffs with Joe Beda, one of the creators of Kubernetes, and Brandon Phillips, the co-founder of CoreOS. The conversation touched on multiple areas, but it’s clear that more and more companies are recognizing the need to have some strategy around hosting their applications on multiple cloud providers.
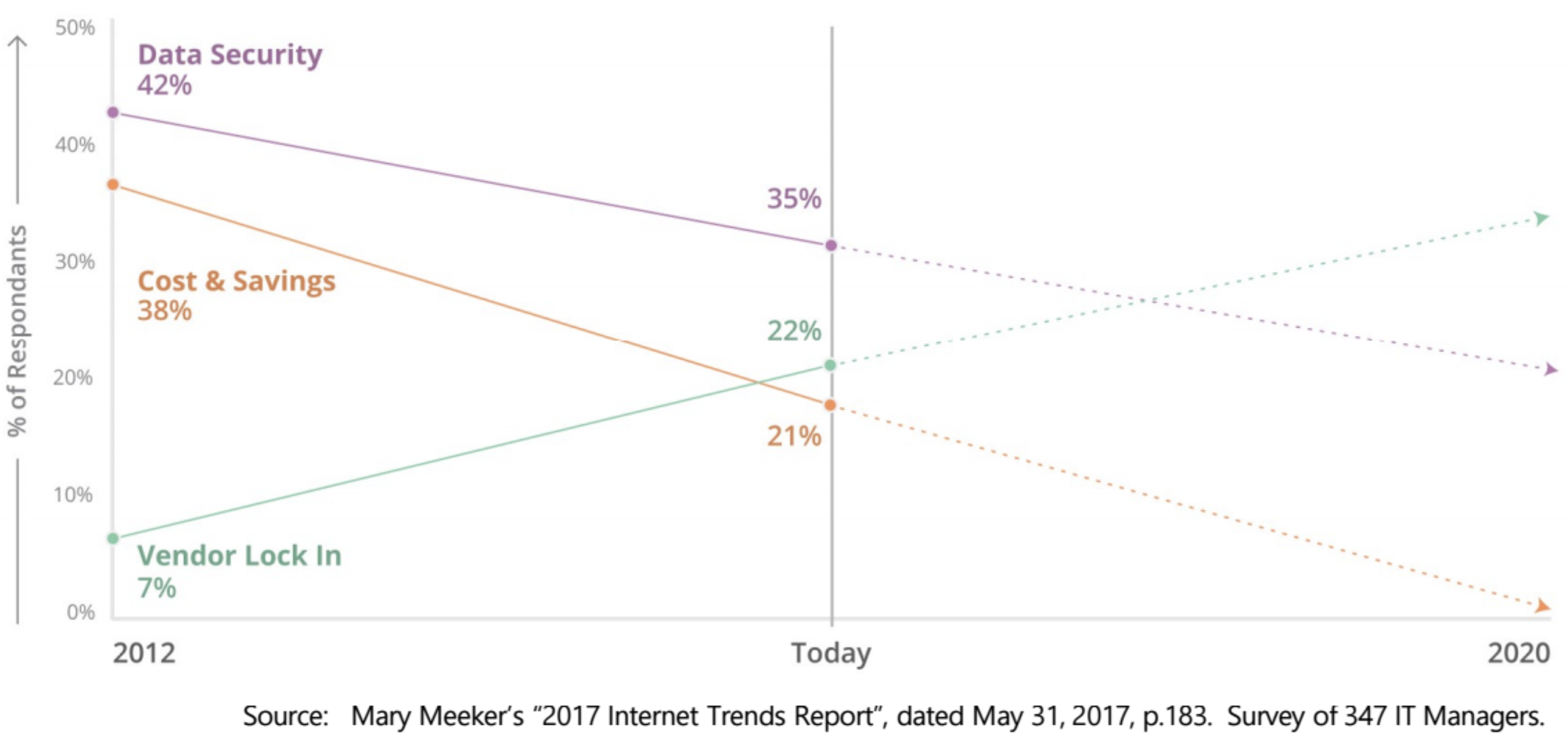
Earlier this year, Mary Meeker published her annual Internet Trends report which revealed that 22% of respondents viewed Cloud Vendor Lock-In as a top 3 concern, up from just 7% in 2012. This is in contrast to previous top concerns, Data Security and Cost & Savings, both of which dropped amongst those surveyed.
At Cloudflare, our mission is to help build a better internet. To fulfill this mission, our customers need to have consistent access to the best technology and services, over time. This is especially the case with respect to storage and compute providers. This means not becoming locked-in to any single provider and taking advantage of multiple cloud computing vendors (such as Amazon Web Services or Google Cloud Platform) for the same end user services.
The Benefits of Having Multiple Cloud Vendors
There are Continue reading
Starboard Value discloses 10.7% stake in Mellanox
Too Much R&D Makes a Vulnerable Tech Company ? Really ?InfoSight Moves HPE Closer to Autonomous Data Center
 HPE acquired the technology from Nimble Storage, which it bought for $1 billion earlier this year.
HPE acquired the technology from Nimble Storage, which it bought for $1 billion earlier this year.
Facing the Hybrid Cloud Reality
Public cloud has its pros and cons, but enterprises today can't afford to be anti-cloud.
Feedback: Ansible for Networking Engineers
Got this feedback on my Ansible for Networking Engineers webinar:
This webinar is very comprehensive compared to any other Ansible webinars available out there. Ivan does great job of mapping and using real life example which is directly related to daily tasks.
The Ansible online course is even better: it includes support, additional hands-on exercises, sample playbooks, case studies, and lab instructions.
However, Ansible is just a tool that shouldn’t be missing from your toolbox. If you need a bigger picture, consider the Building Network Automation Solutions online course (and register ASAP to save $700 with the Enthusiast ticket).
Route Filtering Techniques : Access-lists, Route-map and Distribution-lists
Back to Basics : Access-Lists and Types
Before we talk about these protocols, I would like to tell you guys that we have our own youtube channel for various network videos that can further help you guys to study further. I will going to add many more videos soon on the channel, Please subscribe to the channel for the study network related videos
But now if we are talking about all these route filtering protocol, we will take one by one to explain how and what they filter out in the network
IP Access List Route Filtering
Unifi US-8 PoE Passthrough With The Cisco 3560CX
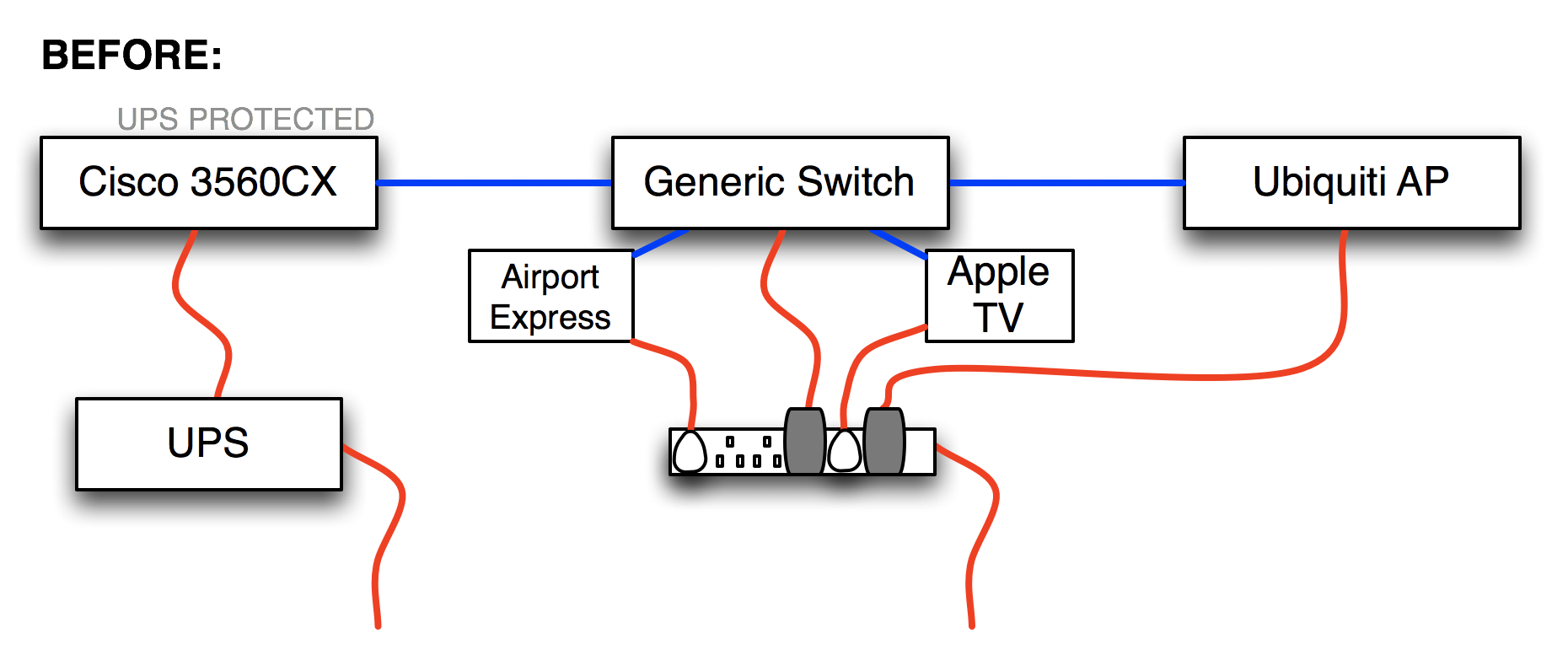
As part of my “everything should be on a UPS” strategy, I recently replaced a regular 8-port gigabit switch with a Ubiquiti Unifi US-8 Ethernet switch because the US-8 can be powered using POE (Power Over Ethernet) provided by a UPS-protected switch in my basement, so it should stay up in the event of a power outage. This also allowed me to indirectly provide UPS protection for the Ubiquiti wireless AP in that location because the US-8 has a PoE passthrough port with which I could power the AP. Clever, right?

POE Passthrough
To clarify (because a picture is worth many thousands of my words), here’s how things were:
And here’s how things are after installing the Ubiquiti Unifi US-8:
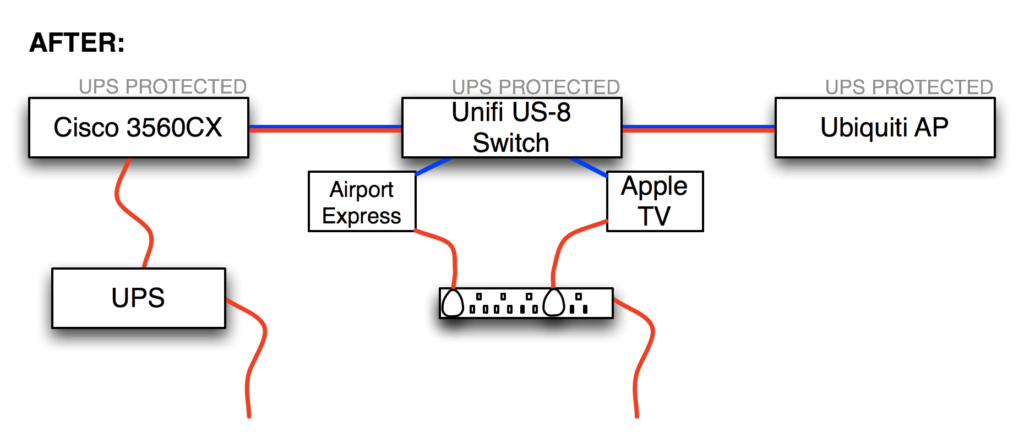
The new setup worked well, but I noticed after a few days that the uptime for the Unifi US-8 kept on resetting; that is, it appeared to be rebooting. The Cisco 3560CX switch which is providing the POE can supply 30W per port, which is plenty enough for the US-8 and the wireless AP to be daisy-chained like this, yet when I looked at the logs on the 3560CX, I found an error:
Oct 23 18:23:12.124 UTC: %ILPOWER-3-CONTROLLER_PORT_ERR: Continue reading