HS061 What is IT Training or Education
The difference between training and education is signficant and technology industry often conflates these terms. They are vastly different ways to providing learning and we dive into why we need more education and less training.
The post HS061 What is IT Training or Education appeared first on Packet Pushers.
HS061 What is IT Training or Education
The difference between training and education is signficant and technology industry often conflates these terms. They are vastly different ways to providing learning and we dive into why we need more education and less training.BGP Challenge: Merge Autonomous Systems
Here’s a challenge in case you get bored during the Christmas break: merge two networks running BGP (two autonomous systems) without changing anything but the configurations of the routers connecting them (the red BGP session in the diagram). I won’t give you any hints; you can discuss it in the comments or a GitHub discussion.
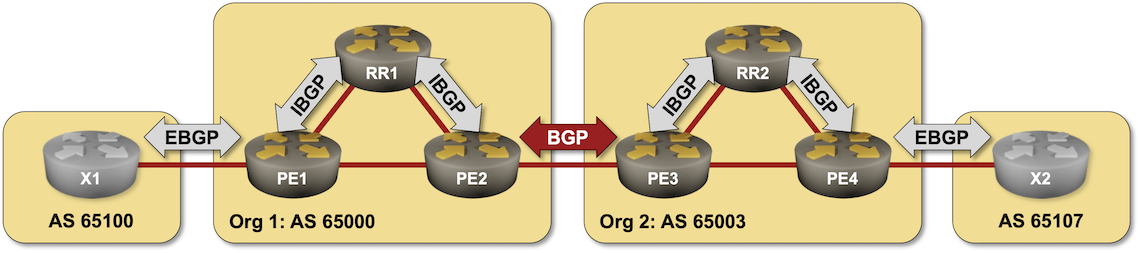
Hopefully, you won’t have to deal with something similar in real life, but then we know that crazy requirements trump good designs any day of the week.
BGP Challenge: Merge Autonomous Systems
Here’s a challenge in case you get bored during the Christmas break: merge two networks running BGP (two autonomous systems) without changing anything but the configurations of the routers connecting them (the red BGP session in the diagram). I won’t give you any hints; you can discuss it in the comments or a GitHub discussion.

Hopefully, you won’t have to deal with something similar in real life, but then we know that crazy requirements trump good designs any day of the week.
Australia’s cybersecurity strategy is here and Cloudflare is all in

We are thrilled about Australia’s strategic direction to build a world-leading cyber nation by 2030. As a world-leading cybersecurity company whose mission is to help build a better Internet, we think we can help.
Cloudflare empowers organizations to make their employees, applications and networks faster and more secure everywhere, while reducing complexity and cost. Cloudflare is trusted by millions of organizations – from the largest brands to entrepreneurs and small businesses to nonprofits, humanitarian groups, and governments across the globe.
Cloudflare first established a footprint in Australia in 2012 when we launched our 15th data center in Sydney (our network has since grown to span over 310 cities in 120 countries/regions). We support a multitude of customers in Australia and New Zealand, including some of Australia’s largest banks and digital natives, with our world-leading security products and services. For example, Australia’s leading tech company Canva, whose service is used by over 35 million people worldwide each month, uses a broad array of Cloudflare’s products — spanning use cases as diverse as remote application access, to serverless development, and even bot management to help Canva protect its network from attacks.
In support of the Australian Cyber Security Strategy Continue reading
Talkdesk Talks the Infusion of Generative AI With the Contact Center
Adopting gen AI is essential for companies to keep up with market changes as it can transform the way businesses interact with their customers.Tech Bytes: Fortinet Advisor Brings GenAI To Support SecOps Teams (Sponsored)
Today on the Tech Bytes podcast, sponsored by Fortinet, we dive into Fortinet Advisor. This is a new generative AI offering designed to act as an assistant to SoC analysts and security teams by providing context-aware event summaries, potential impacts, and recommended responses while also keeping humans in the loop.
The post Tech Bytes: Fortinet Advisor Brings GenAI To Support SecOps Teams (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Fortinet Advisor Brings GenAI To Support SecOps Teams (Sponsored)
Today on the Tech Bytes podcast, sponsored by Fortinet, we dive into Fortinet Advisor. This is a new generative AI offering designed to act as an assistant to SoC analysts and security teams by providing context-aware event summaries, potential impacts, and recommended responses while also keeping humans in the loop. Episode Guest: Kevin Faulkner |... Read more »Datacenter Infrastructure Report Card, Q3 2023
It is hard to keep a model of datacenter infrastructure spending in your head at the same time you want to look at trends in cloud and on-premises spending as well as keep score among the key IT suppliers to figure out who is winning and who is losing. …
The post Datacenter Infrastructure Report Card, Q3 2023 first appeared on The Next Platform.
Datacenter Infrastructure Report Card, Q3 2023 was written by Timothy Prickett Morgan at The Next Platform.
Kill the CLI
As the conversation about Network Automation flows around us, this topic seems to be getting some traction (and quite a reaction!). Have you disabled the CLI? Should we disable the CLI? How long before the CLI is disabled? I don’t believe those are the question we should be asking but it made me examine why READ MORE
The post Kill the CLI appeared first on The Gratuitous Arp.
2023 Network Computing Words of the Year
Which words captured our attention, piqued our fancy, sparked our interest, made our dreams come true, or kept us up at night in 2023? Drumroll, please ...NB460: VMware Ditches Perpetual Licenses; GenAI Is Coming To Network Ops
On today's Network Break we discuss why Broadcom wants VMware customers on subscription licenses, whether GenAI will be a free or paid feature for network management software, how Cisco doged a multi-billion-dollar patent infringement, what a successful test of space lasers means for satellite broadband means for Amazon's Project Kuiper, and more IT news.
The post NB460: VMware Ditches Perpetual Licenses; GenAI Is Coming To Network Ops appeared first on Packet Pushers.
NB460: VMware Ditches Perpetual Licenses; GenAI Is Coming To Network Ops
Broadcom’s VMware has announced an end to perpetual licensing, network automation provider Anuta Networks is adding generative AI capabilities to its Atom platform, and high-end firewall revenues dip but campus switch sales soared in Q3 2023. The Open Networking Foundation, which oversaw open projects around software-defined networking, is closing its doors and folding its projects... Read more »Production Reductions

You’ve probably noticed that I haven’t been writing quite as much this year as I have in years past. I finally hit the wall that comes for all content creators. A combination of my job and the state of the industry meant that I found myself slipping off my self-appointed weekly posting schedule more and more often in 2023. In fact, there were several times I skipped a whole week to get put something out every other week, especially in the latter half of the year.
I’ve always wanted to keep the content level high around here and give my audience things to think about. As the year wore on I found myself running out of those ideas as portions of the industry slowed down. If other people aren’t getting excited about tech why should I? Sure, I could probably write about Wi-Fi 7 or SD-WAN or any number of topics over and over again but it’s harder to repeat yourself for an audience that takes a more critical eye to your writing than it is for someone that just wants to churn out material.
My Bruce Wayne job kept me busy this year. I’m proud of all the content Continue reading
Integrating Turnstile with the Cloudflare WAF to challenge fetch requests

Two months ago, we made Cloudflare Turnstile generally available — giving website owners everywhere an easy way to fend off bots, without ever issuing a CAPTCHA. Turnstile allows any website owner to embed a frustration-free Cloudflare challenge on their website with a simple code snippet, making it easy to help ensure that only human traffic makes it through. In addition to protecting a website’s frontend, Turnstile also empowers web administrators to harden browser-initiated (AJAX) API calls running under the hood. These APIs are commonly used by dynamic single-page web apps, like those created with React, Angular, Vue.js.
Today, we’re excited to announce that we have integrated Turnstile with the Cloudflare Web Application Firewall (WAF). This means that web admins can add the Turnstile code snippet to their websites, and then configure the Cloudflare WAF to manage these requests. This is completely customizable using WAF Rules; for instance, you can allow a user authenticated by Turnstile to interact with all of an application’s API endpoints without facing any further challenges, or you can configure certain sensitive endpoints, like Login, to always issue a challenge.
Challenging fetch requests in the Cloudflare WAF
Millions of websites protected by Cloudflare’s WAF leverage our Continue reading
Review: Unnumbered Interfaces in netlab
A while ago, Chris Parker published a nice blog post explaining how to configure unnumbered interfaces with IS-IS in Junos. It’s well worth reading, but like my Unnumbered Ethernet Interfaces blog post, it only covers one network operating system. What if you want to do something similar on another platform?
How about using the collective efforts of the team developing device configuration templates for netlab? As of December 2023 netlab supports:
Review: Unnumbered Interfaces in netlab
A while ago, Chris Parker published a nice blog post explaining how to configure unnumbered interfaces with IS-IS in Junos. It’s well worth reading, but like my Unnumbered Ethernet Interfaces blog post, it only covers one network operating system. What if you want to do something similar on another platform?
How about using the collective efforts of the team developing device configuration templates for netlab? As of December 2023 netlab supports:
Cybersecurity, Cloud and AI: Top-of-mind themes heading into 2024
Recently I had the opportunity to host a group of forward-thinking CISOs, CIOs and other executive decision makers drawn from several enterprise organizations in the United States. The goal was to frame perspectives on trends and priorities emerging within their respective organizations while co-relating to broader industry trends. Specifically, the intent here was not to x-ray the requirements of any single organization, but rather to identify, detect and understand patterns that could, in turn guide priorities over the next few years, benefiting the broader community. The discussions unearthed a lot of commonality in terms of shared pain points and higher order goals, and I thank the leaders that participated in the exercise, as well as the talented members of my team that came together to create a successful forum for discussion.

This multi-part blog series will summarize prominent patterns and insights that emerged from these sessions, that would hopefully serve as guideposts for the next 12-24 months, mostly in the areas of security, cloud infrastructure and deployment models.
Over a few sessions, broadly we had the cohort dive engage along three axis –
- The first was to really examine their top pain points. Issues, that if solved, would help Continue reading
Debian on IPng’s VPP Routers

Introduction
When IPng Networks first built out a european network, I was running the Disaggregated Network Operating System [ref], initially based on AT&T’s “dNOS” software framework. Over time though, the DANOS project slowed down, and the developers with whom I had a pretty good relationship all left for greener pastures.
In 2019, Pierre Pfister (and several others) built a VPP router sandbox [ref], which graduated into a feature called the Linux Control Plane plugin [ref]. Lots of folks put in an effort for the Linux Control Plane, notably Neale Ranns from Cisco (these days Graphiant), and Matt Smith and Jon Loeliger from Netgate (who ship this as TNSR [ref], check it out!). I helped as well, by adding a bunch of Netlink handling and VPP->Linux synchronization code, which I’ve written about a bunch on this blog in the 2021 VPP development series [ref].
At the time, Ubuntu and CentOS were the supported platforms, so I installed a bunch of Ubuntu machines when doing the deploy with my buddy Fred from IP-Max [ref]. But as time went by, I fell back to my old habit of running Debian Continue reading
Worth Reading: The AI Supply Paradox
Eric Hoel published a spot-on analysis of AI disruptiveness, including this gem:
The easier it is to train an AI to do something, the less economically valuable that thing is. After all, the huge supply of the thing is how the AI got so good in the first place.
TL&DR: AI can easily disrupt things that are easy to generate and thus have little value. Seeing investors trying to recoup the billions pouring into the latest fad will be fun.