The NSX Mindset
The NSX Mindset: one’s mental capability to be a determined leader and catalyst for change in the way a company designs, implements, manages, and operates networking and security.
Change isn’t easy. Especially when it involves something personal. Unfortunately, though, it happens whether we like it or not. In the world of information technology change is upon us. IT Automation, micro-segmentation, application availability, and cross cloud services are no longer buzz words in marketing materials and executive meetings. These are realities designed and deployed in some of the world’s largest IT environments. The common thread among these concepts is the new capabilities in networking and security brought to life by VMware NSX.
VMware NSX is a platform for the next generation data center architecture. The capabilities are transforming the way enterprises approach traditional business problems and it is solving new business problems brought about by a company’s digital transformation.
As an IT professional your long term success hinges on your ability to adapt to new technologies and solutions. While VMware NSX is disruptive to the status quo, it is at the same time an opportunity for admins, engineers, and architects to become leaders Continue reading
The NSX Mindset
 The NSX Mindset: one’s mental capability to be a determined leader and catalyst for change in the way a company designs, implements, manages, and operates networking and security.
The NSX Mindset: one’s mental capability to be a determined leader and catalyst for change in the way a company designs, implements, manages, and operates networking and security.
Telco Systems and Silver Peak Offer vCPE for SD-WAN
 VNFs from companies like Fortinet, Palo Alto, and Riverbed can be integrated into the joint solution.
VNFs from companies like Fortinet, Palo Alto, and Riverbed can be integrated into the joint solution.
Nutanix Enterprise Cloud Platform Shrinks Data Center Footprint
 It beat out HPE’s SimpliVity and Cisco's Hyperflex for the customer win.
It beat out HPE’s SimpliVity and Cisco's Hyperflex for the customer win.
Aparna Systems ‘Cloud-in-a-Box’ Targets Edge Computing
 It goes beyond hyperconverged by integrating the network switching.
It goes beyond hyperconverged by integrating the network switching.
Introducing TLS with Client Authentication
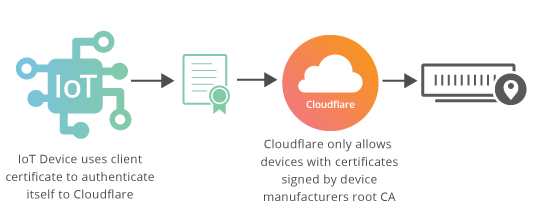
In a traditional TLS handshake, the client authenticates the server, and the server doesn’t know too much about the client. However, starting now, Cloudflare is offering enterprise customers TLS with client authentication, meaning that the server additionally authenticates that the client connecting to it is authorized to connect.
TLS Client Authentication is useful in cases where a server is keeping track of hundreds of thousands or millions of clients, as in IoT, or in a mobile app with millions of installs exchanging secure information. For example, an IoT company can issue a unique client certificate per device, and then limit connections to their IoT infrastructure to only their devices by blocking connections where the client doesn’t present a certificate signed by the company’s certificate authority.
Or in the case of a mobile banking app, where the bank wants to ensure customers’ secure financial data doesn’t get stolen by bots spoofing their mobile app, they can issue a unique certificate to every app install and in the TLS handshake validate requests are coming from their mobile app. Client authentication is also useful for VPNs, enterprise networks or staging sites, where corporations and developers need to lock down connections to only laptops Continue reading
Greenbug’s DNS-isms
Over the past few months there has been a lot of research and press coverage on the Shamoon campaigns. These have been the attacks on Saudi Arabian companies where a destructive malware known as Disttrack was deployed. The malware, using stolen credentials, spreads throughout the […]Worth Reading: How to choose a sandbox
The post Worth Reading: How to choose a sandbox appeared first on rule 11 reader.