Video: Software Secures the World
Martin Casado doesn’t have a proper job since he left VMware. This gives him times to think deeply about the future of IT security as part of his role of wasting investors money at A16Z and considering where the next advances or futures will be. This video makes a lot of sense to me.
Once upon a time, we thought of security measures as being built like a wall around a medieval city. Then, as threats grew in complexity, we began to think of it more like securing a city or nation-state. Finally, security grew alike to aerial warfare — mobile, quick, wide-ranging. Each of these new modes for thinking about security represented a major misalignment between the security threats that had evolved and our strategies/tactics for dealing with them.
Now we are once again at another such major misalignment — thanks largely to the cloud and new complexity — requiring both a shift in how we think about and respond to threats. But we also have security “overload” given the vast size of our systems and scale of notifications.
How do security threats develop? How should CEOs and CSOs think of planning for them? What role will AI and Continue reading
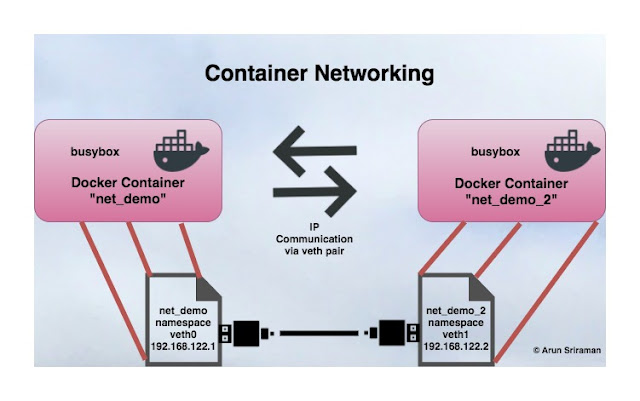
Container Namespaces – How to add networking to a docker container
Today, lets deep dive into adding interfaces to a container manually and in-turn gain some insight into how all of this works. Since this discussion is going to revolve around network namespaces I assume you have some background in that area. If you are new to the concept of namespaces and network namespaces, I recommend reading this.
Step 1: We will first bring up a docker container without networking. From docker docs, using the --network none when running a docker container leaves out container interface creation for that docker instance. Although docker skips network interface creation it brings up the container with Continue reading