You can now use Google Authenticator and any TOTP app for Two-Factor Authentication
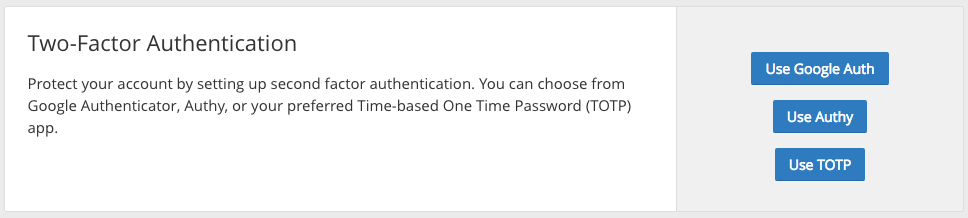
Since the very beginning, Cloudflare has offered two-factor authentication with Authy, and starting today we are expanding your options to keep your account safe with Google Authenticator and any Time-based One Time Password (TOTP) app of your choice.
If you want to get started right away, visit your account settings. Setting up Two-Factor with Google Authenticator or with any TOTP app is easy - just use the app to scan the barcode you see in the Cloudflare dashboard, enter the code the app returns, and you’re good to go.
Importance of Two-Factor Authentication
Often when you hear that an account was ‘hacked’, it really means that the password was stolen.
If the media stopped saying 'hacking' and instead said 'figured out their password', people would take password security more seriously.
— Khalil Sehnaoui (@sehnaoui) January 5, 2017
Two-Factor authentication is sometimes thought of as something that should be used to protect important accounts, but the best practice is to always enable it when it is available. Without a second factor, any mishap involving your password can lead to a compromise. Journalist Mat Honan’s high profile compromise in 2012 is a great example of the importance of two-factor authentication. When Continue reading
Internet Society speaks out against proposed password disclosure requirements
Today, the Internet Society, along with 50 organizations and trade associations and nearly 90 individual experts who care deeply about an open, trusted Internet, expressed our deep concerns that the U.S. Department of Homeland Security may require individuals to disclose their social media account passwords as a condition of entry into the United States. Last week, the new U.S. Secretary of Homeland Security indicated that the U.S. government is considering such a policy as an element of border screening.
Charter Jumps Into 5G Testing as Part of Its Mobile Ambitions
 Charter activated an MVNO agreement with Verizon.
Charter activated an MVNO agreement with Verizon.
OPNFV Tests its Software on OCP Hardware
 It married open source software with open source hardware.
It married open source software with open source hardware.
Worth Reading: Got a license for that YouTube channel?
The post Worth Reading: Got a license for that YouTube channel? appeared first on 'net work.
Triangle Network Engineers
I’m speaking at the Triangle Network Engineers meeting on the 9th of March; click below to find out more.
The post Triangle Network Engineers appeared first on 'net work.
