Introducing Cumulus Express — open networking hardware & software all in one
In the last few months at Cumulus Networks, we’ve put a lot of focus on finding innovative ways to make web-scale networking accessible to data centers of all sizes and engineers of all backgrounds. We released features like NCLU, EVPN and PIM to make that happen.
In our minds, web-scale networking principles make data centers more powerful and make engineers’ lives easier. We take great pride in helping organizations accelerate their journey to web-scale in the fastest, simplest way possible. That’s why we are super excited to announce that web-scale networking with Cumulus Networks just got EVEN BETTER. We know, you didn’t think it was possible.
Allow us to formally introduce Cumulus Express — your turnkey solution featuring an open networking switch preloaded and licensed with Cumulus Linux. Each Cumulus Express switch is ready to go as is, improving your time to market by eliminating steps to install and research optics. That’s right, you can now deploy switches running Cumulus Linux in one easy step.
With Cumulus Express you get:
- 1G to 100G platforms: Available in 1G-T, 10G/10G-T, 25G (coming soon), 40G & 100G speeds
- NOS & license preloaded: Each switch comes preloaded with Cumulus Linux with an active license Continue reading
Using Containers For Persistent Storage
Learn how container-based storage is implemented and blurring the lines between data, storage, and applications.
A look at Auto-Tunnel Mesh Groups
In this post I would like to give a demonstration of using the Auto-Tunnel Mesh group feature.
As you may know, manual MPLS-TE tunnels are first and foremost unidirectional, meaning that if you do them between two PE nodes, you have to do a tunnel in each direction with the local PE node being the headend.
Now imagine if your network had 10 PE routers and you wanted to do a full mesh between them, this can become pretty burdensome and error-prone.
Thankfully there’s a method to avoid doing this manual configuration and instead rely on your IGP to signal its willingness to become part of a TE “Mesh”. Thats what the Auto-Tunnel Mesh Group feature is all about!
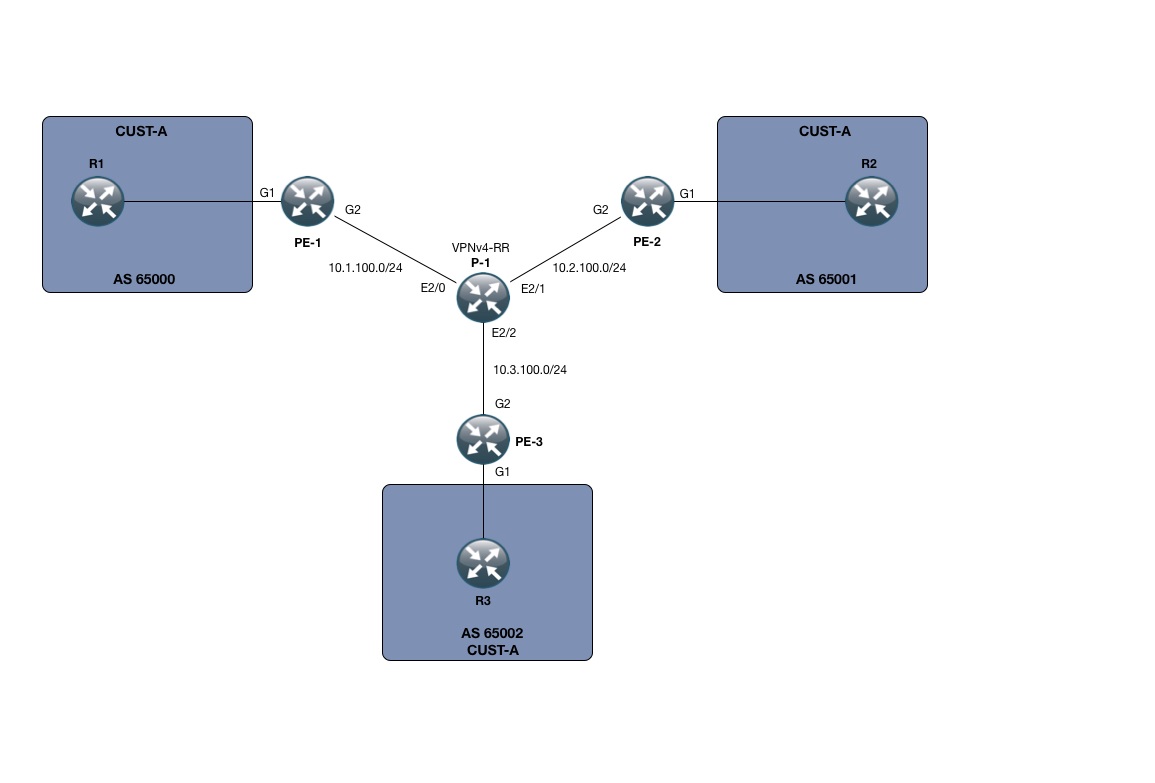
In my small SP setup, I only have 3 PE devices, namely PE-1, PE-2 and PE-3. I also only have one P node, called P-1.
However small this setup is, its enough to demonstrate the power of the Auto-Tunnel mesh functionality.
Beyond that, I have setup a small MPLS L3 VPN service for customer CUST-A, which has a presence on all 3 PE nodes. The VPNv4 address-family is using a RR which for this purpose is P-1.
We are running OSPF Continue reading
OSPF Forwarding Address: Yet another Kludge
One of my readers sent me an interesting NSSA question (more in a future blog post) that sent me chasing for the reasons behind the OSPF Forwarding Address (FA) field in type-5 and type-7 LSAs.
This is the typical scenario for OSPF FA I was able to find on the Internet:
Read more ...LSA issue @ January 19, 2017 at 10:43AM
Here is the question: if Host A wants to transmit some data across TCP/IP network to Host B with IP address of 1.2.3.4 how will this Dest_IP address be represented? Correct, it will be hex encoded, but will the bytestream be like 0x01 02 03 04 or 0x04 03 02 01? Yep, you see where2016 Year in Review
Every beginning of the year I usually review what I have done the past one year, make notes, and build the plan for the upcoming year. I made many mistakes in the past, did things I’m not proud of, however I use them as opportunity to learn and try to be better next time.Early 2016 I found that my startup company was competing directly against Cisco (that was still my employer at that time). That was quite surprising. I founded that company in 2012 initially as my pet project, the lab for my MBA, where I can practice whatever I learned from the business school. My pitch for the startup was simple: we do what Cisco (or Cisco Services) will not do. We built online learning platform to learn Cisco certification using group mentoring system. We run physical network audit. We did system integration projects to interoperate Cisco products with any other vendors.
However, since late 2014 the engineering team in my company have evolved. They grew skills in network programming. The team put more focus on Software Defined Networking (SDN). They built lab to validate Network Function Virtualization (NFV). And then the team started to develop our own Continue reading
Technology Short Take #76
Welcome to Technology Short Take #76, the first Technology Short Take of 2017. Normally, I’d publish this on a Friday, but due to extenuating circumstances (my mother-in-law’s funeral is tomorrow) I’m posting it today. Here’s hoping you find something useful!
Networking
- As of Vagrant 1.9.1, the Cumulus plugin for Vagrant is no longer needed. See this post for more details.
- Ivan Pepelnjak (one of my absolutely favorite folks in the IT industry) has a great post on using regex filters in Ansible to parse text printouts from network devices. This is a super-practical post that anyone working with network automation can put to use right away.
- Craig Matsumoto has an informative article on why machine learning is hard to apply to networking. I’ve heard David Meyer—who is quoted extensively in the article—speak several times, and most of the time his stuff is way beyond my understanding. At least now, though, I get the general direction he’s heading.
- Interested in using OVS with VXLAN on Hyper-V, but without OpenStack? This article by Alin Serdean from Cloudbase Solutions describes how it’s done.
- Here’s an article describing how to establish a site-to-site VPN between a Cisco ASA and Microsoft Azure. Anecdotally, Continue reading
Running a Pelican Blog on Docker Cloud with Let’s Encrypt
It's 2017 and my blog was starting to look a little dated so I decided it was time for a face-lift. While I was at it, I overhauled the way I deploy my blog too.