What’s Next For OpenFlow
As SDN use cases expand, OpenFlow must become independent of specific applications and data-path protocols.
Hyperconvergence Benefits Come With Challenges
Study highlights top drivers for enterprise adoption of hyperconverged infrastructure and emerging pain points.
Response: Japan researchers warn of fingerprint theft from ‘peace’ sign
Another one from the Biometrics is not useful for authentication dumpster:
The NII researchers were able to copy fingerprints based on photos taken by a digital camera three metres (nine feet) away from the subject.
Japan researchers warn of fingerprint theft from ‘peace’ sign : http://phys.org/news/2017-01-japan-fingerprint-theft-peace.html
The post Response: Japan researchers warn of fingerprint theft from ‘peace’ sign appeared first on EtherealMind.
Viptela Snags Former Cisco & VCE Exec Praveen Akkiraju as CEO
 Viptela hosts 90% of its SD-WAN customers out of AWS.
Viptela hosts 90% of its SD-WAN customers out of AWS.
Parsing Printouts with Ansible Regular Expression Filters
Ansible is great at capturing and using JSON-formatted data returned by REST API (or any other script or method it can invoke), but unfortunately some of us still have to deal with network devices that cannot even spell structured data or REST.
Read more ...Introducing Accelerated Mobile Links: Making the Mobile Web App-Quick
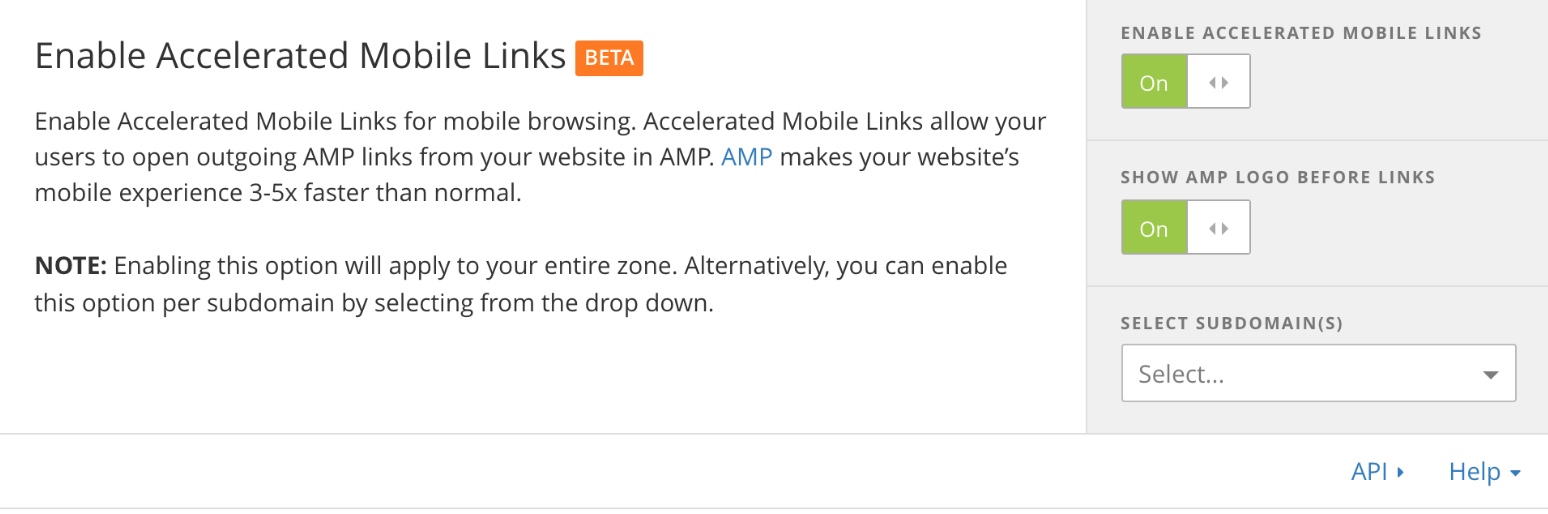
In 2017, we've predicted that more than half of the traffic to Cloudflare's network will come from mobile devices. Even if they are formatted to be displayed on a small screen, the mobile web is built on traditional web protocols and technologies that were designed for desktop CPUs, network connections, and displays. As a result, browsing the mobile web feels sluggish compared with using native mobile apps.
In October 2015, the team at Google announced Accelerated Mobile Pages (AMP), a new, open technology to make the mobile web as fast as native apps. Since then, a large number of publishers have adopted AMP. Today, 600 million pages across 700,000 different domains are available in the AMP format.
The majority of traffic to this AMP content comes from people running searches on Google.com. If a visitor finds content through some source other than a Google search, even if the content can be served from AMP, it typically won't be. As a result, the mobile web continues to be slower than it needs to be.
Making the Mobile Web App-Quick
Cloudflare's Accelerated Mobile Links helps solve this problem, making content, regardless of how it's discovered, app-quick. Once enabled, Accelerated Mobile Continue reading