Day Two Cloud 206: Making The Most Of Red Teaming With Gemma Moore
Red teams attack a customer's security systems. The idea of a red team, whether consultants or in-house, is to approach the target like an attacker would. A red team includes technical and human-based exploit and attempts to test defenses, probe for weaknesses, and identify vulnerable systems and processes. On today's episode we look at how to get the most out of a red team engagement--it's much more than just an attack and a report.Can We Trust Worldcoin’s Aspirin For AI Headaches?
This post originally appeared in the Packet Pushers’ Human Infrastructure newsletter, a weekly mailing of essays, links to technical blogs and IT news, and whatever else think is interesting. Subscribe for free here. Let’s say I invent an autonomous mobile robot. It can lift heavy items for you, wash your dishes, do your grocery shopping, […]
The post Can We Trust Worldcoin’s Aspirin For AI Headaches? appeared first on Packet Pushers.
Navigating the Connectivity Landscape: Best Practices for Securing Network Architecture
Connectivity is no longer just an enabler. Network architecture must now take security and resilience into account, as well.Navigating the Connectivity Landscape: Best Practices for Securing Network Architecture
Connectivity is no longer just an enabler. Network architecture must now take security and resilience into account, as well.Introducing per hostname TLS settings — security fit to your needs
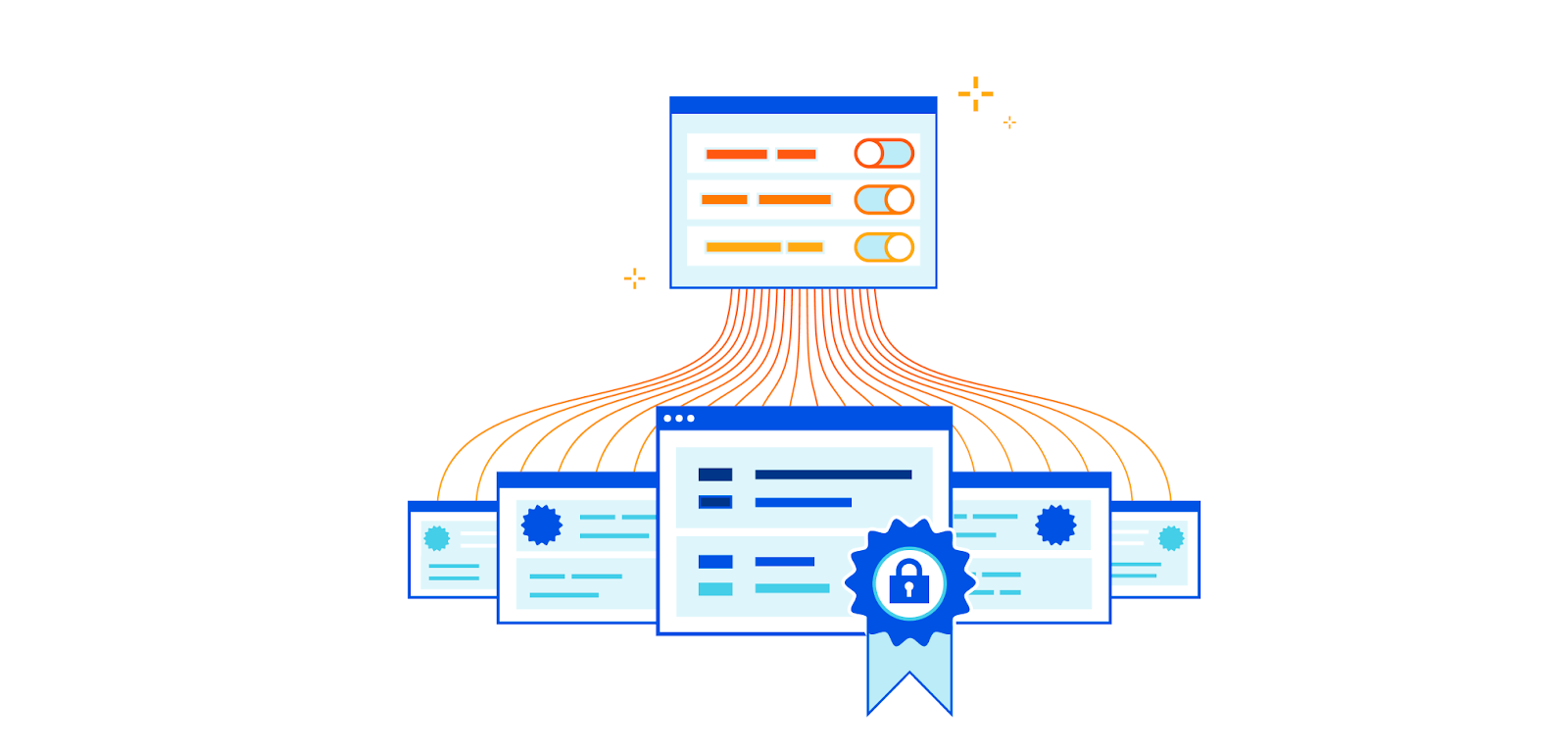
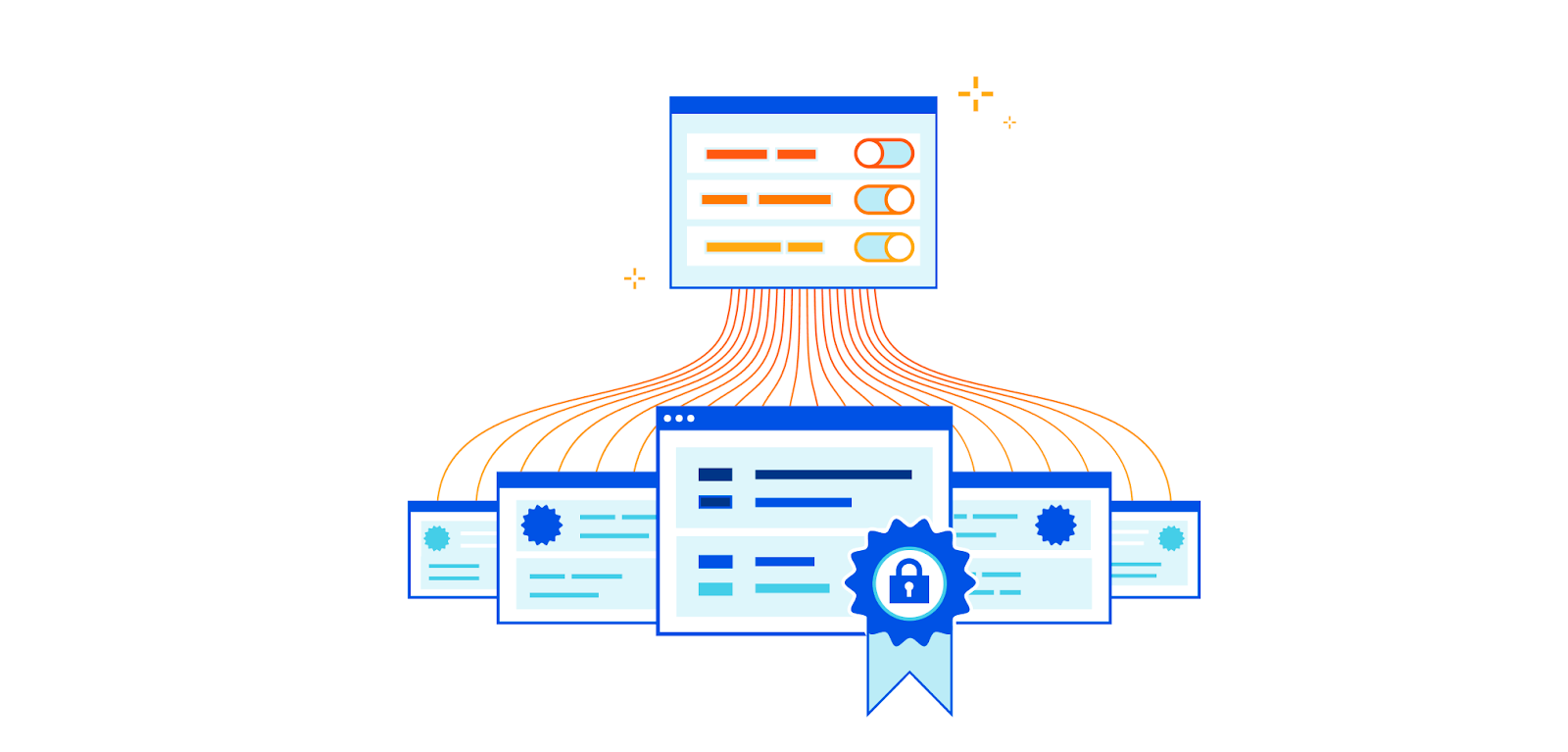
One of the goals of Cloudflare is to give our customers the necessary knobs to enable security in a way that fits their needs. In the realm of SSL/TLS, we offer two key controls: setting the minimum TLS version, and restricting the list of supported cipher suites. Previously, these settings applied to the entire domain, resulting in an “all or nothing” effect. While having uniform settings across the entire domain is ideal for some users, it sometimes lacks the necessary granularity for those with diverse requirements across their subdomains.
It is for that reason that we’re excited to announce that as of today, customers will be able to set their TLS settings on a per-hostname basis.
The trade-off with using modern protocols
In an ideal world, every domain could be updated to use the most secure and modern protocols without any setbacks. Unfortunately, that's not the case. New standards and protocols require adoption in order to be effective. TLS 1.3 was standardized by the IETF in April 2018. It removed the vulnerable cryptographic algorithms that TLS 1.2 supported and provided a performance boost by requiring only one roundtrip, as opposed to two. For a user to benefit from Continue reading
Top Security Benefits of Improving Network Resiliency
In this archived panel discussion sponsored by Absolute Software, Steve Fallin connects with Ariel Robinson and Sherelle Moore to deliver an in-depth conversation detailing the 'Security Benefits of Improving Network Resiliency' during our 'Network Resilience Boot Camp' presented by Data Center Knowledge and Network Computing. This excerpt is from our live 'Network Resilience Boot Camp' virtual event moderated by Bonnie D. Graham on June 29, 2023.Heavy Wireless 008: 3D Printing For Wireless Engineers
3D printing is a popular activity among wireless network engineers. Given that they deal with invisible, intangible radio waves all day, maybe it's no surprise they'd enjoy making things they can touch and feel. On today's Heavy Wireless we talk about why the wireless community enjoys 3D printing, and how engineers can make and use printed objects on the job--and at home.
The post Heavy Wireless 008: 3D Printing For Wireless Engineers appeared first on Packet Pushers.
Heavy Wireless 008: 3D Printing For Wireless Engineers
3D printing is a popular activity among wireless network engineers. Given that they deal with invisible, intangible radio waves all day, maybe it's no surprise they'd enjoy making things they can touch and feel. On today's Heavy Wireless we talk about why the wireless community enjoys 3D printing, and how engineers can make and use printed objects on the job--and at home.A Look At Broadcom’s Jericho3-AI Ethernet Fabric: Schedules, Credits, And Cells
Broadcom has come up with some interesting mechanisms to address the challenges of building an Ethernet-based fabric that supports AI workloads. These mechanisms, which include a scheduling framework, cells, and credits, are intended to minimize congestion, latency, and dropped frames or packets in the fabric. In this post I talk about what I learned at […]
The post A Look At Broadcom’s Jericho3-AI Ethernet Fabric: Schedules, Credits, And Cells appeared first on Packet Pushers.
Grafana Network Weathermap
The screen capture above shows a simple network weathermap, displaying a network topology with links animated by real-time network analytics. Hovering over a link in the weathermap pops up a trend chart showing traffic on the link over the last 30 minutes.Deploy real-time network dashboards using Docker compose, describes how to quickly deploy a real-time network analytics stack that includes the sFlow-RT analytics engine, Prometheus time series database, and Grafana to create dashboards. This article describes how to extend the example using the Grafana Network Weathermap Plugin to display network topologies like the ones shown here.
First, add a dashboard panel and select the Network Weathermap visualization. Next define the three metrics shown above. The ifinoctets and ifoutoctets need to be scaled by 8 to convert from bytes per second to bits per second. Creating a custom legend entry makes it easier to select metrics to associate metric instances with weathermap links. Add a color scale that will be used to color links by link utilization. Defining the scale first ensures that links will be displayed correctly when they are added later. Add the nodes to the canvas and drag them to their desired locations. There is a Continue readingProject Cybersafe Schools: Bringing security tools for free to small K-12 school districts in the US


Like other under-resourced organizations, schools face cyber attacks from malicious actors that can impact their ability to safely perform their basic function: teach children. Schools face email, phishing, and ransomware attacks that slow access and threaten leaks of confidential student data. And these attacks have real effects. In a report issued at the end of 2022, the U.S. Government Accountability Office concluded that schools serving kindergarten through 12th grade (K-12) reported significant educational impact and monetary loss due to cybersecurity incidents, such as ransomware attacks. Recovery time can extend from 2 all the way up to 9 months — that’s almost an entire school year.
Cloudflare’s mission is to help build a better Internet, and we have always believed in helping protect those who might otherwise not have the resources to protect themselves from cyberattack.
It is against this backdrop that we’re very excited to introduce an initiative aimed at small K-12 public school districts: Project Cybersafe Schools. Announced as part of the Back to School Safely: K-12 Cybersecurity Summit at the White House on August 8, 2023, Project Cybersafe Schools will support eligible K-12 public school districts with a package of Zero Trust cybersecurity solutions — for Continue reading




