Not one, not two, but three undersea cables cut in Jersey
Sometime before midnight Monday (UK local time) a ship dropped its anchor and broke, not one, not two, but three undersea cables serving the island of Jersey in the English Channel. Jersey is part of the Channel Islands along with Guernsey and some smaller islands.
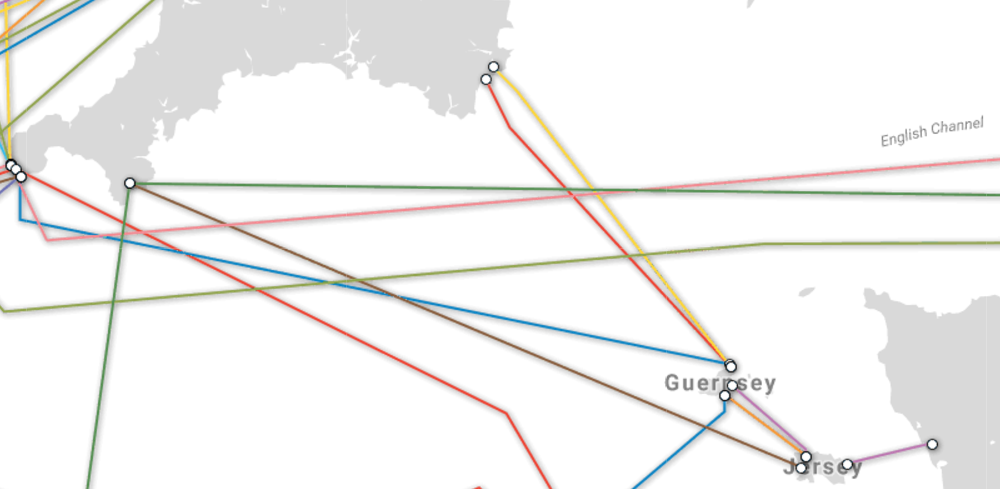 Image courtesy TeleGeography Submarine Cable Map
Image courtesy TeleGeography Submarine Cable Map
These things happen and that’s not a good thing. The cut was reported on the venerable BBC news website. For the telecom operators in Jersey (JT Global) this wasn’t good news. However looking at the traffic from Cloudflare’s point of view; we can see that while the cable cut removed the direct path from London to Jersey, it was replaced by the backup path from Paris to Jersey. The move was 100% under the control of the BGP routing protocol. It's a relief that there's a fallback for when these unpredictable events happen.
Here's a look at one network on the island.
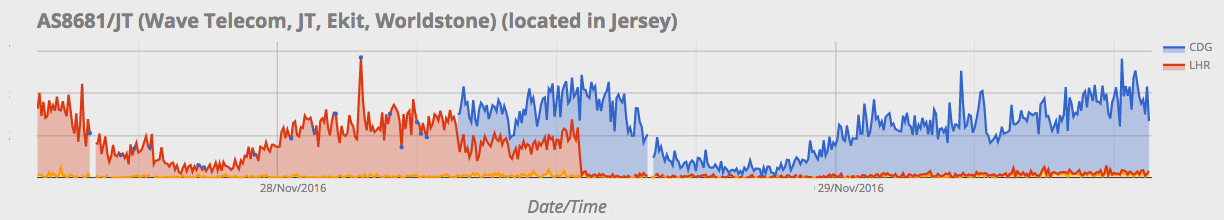 The red traffic is being served from our London data center (the normal location for all Jersey traffic) and the blue traffic is coming from our Paris data center. The step could well be caused by either a delayed break in one of the cables or the Continue reading
The red traffic is being served from our London data center (the normal location for all Jersey traffic) and the blue traffic is coming from our Paris data center. The step could well be caused by either a delayed break in one of the cables or the Continue reading
Intel Recruits an ARM Exec to Run IoT
 Tom Lantzsch makes the jump in January.
Tom Lantzsch makes the jump in January.
Netbox IPAM/DCIM – What all Network Engineers beg for!
We found it!!!
Have you ever sat at your desk, hoping on a miracle, that somebody somewhere will develop a fully comprehensive application for tracking network information??? I know I have, along with millions of other fellow network professional’s I have to assume. What exactly am I referring to? IP addresses, vlans, VRF’s, Rack Elevations and on and on and on. We all have to keep up with this information, for most it is located in spreadsheets; some in notepads; others try to lock it all away in the vast empty space we call a brain.
So, the stage is set. Yes, there are claims of applications that can keep track of what your CORE router IP address is and what vlan you assigned to one of your customers, or even where in the bloody rack it sits in relation to your other devices. Some can even keep track of which VRF routing table your management lies in along with which physical port it connects to. Going a little further, maybe the application claims to give you a basic map layout to which you can refer to…
BUT, very few paid applications actually combine most of these functions into one and very Continue reading
Netbox IPAM/DCIM – What all Network Engineers beg for!
We found it!!!
Have you ever sat at your desk, hoping on a miracle, that somebody somewhere will develop a fully comprehensive application for tracking network information??? I know I have, along with millions of other fellow network professional’s I have to assume. What exactly am I referring to? IP addresses, vlans, VRF’s, Rack Elevations and on and on and on. We all have to keep up with this information, for most it is located in spreadsheets; some in notepads; others try to lock it all away in the vast empty space we call a brain.
So, the stage is set. Yes, there are claims of applications that can keep track of what your CORE router IP address is and what vlan you assigned to one of your customers, or even where in the bloody rack it sits in relation to your other devices. Some can even keep track of which VRF routing table your management lies in along with which physical port it connects to. Going a little further, maybe the application claims to give you a basic map layout to which you can refer to…
BUT, very few paid applications actually combine most of these functions into one and very Continue reading
Nutanix’s First-Ever Earnings Report Bears No Surprises
 Yep, still losing money (but growing mightily).
Yep, still losing money (but growing mightily).
On the ‘Net: BGP Security, LACNOG 26
The post On the ‘Net: BGP Security, LACNOG 26 appeared first on 'net work.
Worth Reading: Security and BYOD
The post Worth Reading: Security and BYOD appeared first on 'net work.
Tips for building SD-WANs
The substantially high cost of MPLS circuits ($200-$400/Mbps/month) compared to easily deployed, lower cost broadband Internet (with a price tag of $1/Mbps/month) has triggered a shift in enterprise architectures to the software defined WAN. SD-WAN provides the flexibility to choose the most optimal transport and dynamically steer traffic over a mix of MPLS circuits, the public Internet, or even wireless LTE circuits.
The access transport selection depends on a variety of factors, including the type of application, traffic profile, security requirements, QoS and network loss and latency. When implemented correctly, SD-WAN truly has significant advantages: Faster service deployment, increased flexibility, unified management and improved application performance, to name a few. But, while familiarity about SD-WAN has increased over the last year, a survey by Silver Peak and IDG shows only 27% of small- to mid-sized enterprises have shifted to SD-WAN.
To read this article in full or to leave a comment, please click here