DNSOP at IETF117
After the flurry of work in various aspects of DNS privacy, the IETF’s agenda for DNS has shifted towards more maintenance and update. This does not mean that the volume of work has abated in any way, but it has dropped the more focussed stance of previous meetings to a broader diversity of topics in operating DNS infrastructure.Zscaler Report Finds VPNs are No Longer Cutting the Mustard
The report finds that since VPNs can expose an organization to various cyber threats, enterprises are starting to prioritize zero trust adoption.Using Web Application Firewall at container-level for network-based threats
The microservices architecture provides developers and DevOps engineers significant agility that helps them move at the pace of the business. Breaking monolithic applications into smaller components accelerates development, streamlines scaling, and improves fault isolation. However, it also introduces certain security complexities since microservices frequently engage in inter-service communications, primarily through HTTP-based APIs, thus broadening the application’s attack surface. This scenario is similar to breaking a chunk of ice into smaller pieces, increasing its surface area. It is crucial that enterprises address these security challenges before benefiting from adopting a microservice architecture.
Challenges implementing defense-in-depth for containers with perimeter-based Web Application Firewall
Kubernetes is the de-facto standard for microservices orchestration. However, as organizations increasingly adopt Kubernetes, they run the risk of inadvertently introducing security gaps. This is often the result of attempts to integrate traditional security tooling into a cloud-native ecosystem that is highly dynamic, ephemeral, and non-deterministic. Instead of implementing security around the platform, DevOps, security, and platform teams must look at enforcing defenses through the platform.
Let’s look at an example of a web application firewall (WAF) which is typically deployed at the ingress of a network or application. As shown in the diagram below, HTTP traffic is Continue reading
What’s Causing Cloud Outages? A Network Managers’ Guide
From fat-finger errors to fishing boats, here are the leading reasons cloud outages at AWS, Microsoft, and others are a growing network resilience challenge.Failure Simulations Fireside Chat Presented by Panduit
In this archived panel discussion, Panduit’s Bob Wagner and Jeff Paliga deliver a fireside chat during our 'Network Resilience Boot Camp' presented by Data Center Knowledge and Network Computing. This excerpt is from our live 'Network Resilience Boot Camp' virtual event moderated by Bonnie D. Graham on June 29, 2023.Integrate Cloudflare Zero Trust with Datadog Cloud SIEM


Cloudflare's Zero Trust platform helps organizations map and adopt a strong security posture. This ranges from Zero Trust Network Access, a Secure Web Gateway to help filter traffic, to Cloud Access Security Broker and Data Loss Prevention to protect data in transit and in the cloud. Customers use Cloudflare to verify, isolate, and inspect all devices managed by IT. Our composable, in-line solutions offer a simplified approach to security and a comprehensive set of logs.
We’ve heard from many of our customers that they aggregate these logs into Datadog’s Cloud SIEM product. Datadog Cloud SIEM provides threat detection, investigation, and automated response for dynamic, cloud-scale environments. Cloud SIEM analyzes operational and security logs in real time – regardless of volume – while utilizing out-of-the-box integrations and rules to detect threats and investigate them. It also automates response and remediation through out-of-the-box workflow blueprints. Developers, security, and operations teams can also leverage detailed observability data and efficiently collaborate to accelerate security investigations in a single, unified platform. We previously had an out-of-the-box dashboard for Cloudflare CDN available on Datadog. These help our customers gain valuable insights into product usage and performance metrics for response times, HTTP status codes, cache hit rate. Continue reading
New Project: BGP Hands-On Labs
Approximately 30 years ago I managed to persuade the powers-that-be within Cisco’s European training organization that they needed a deep-dive BGP course, resulting in a 3 (later 5) day Advanced BGP Configuration and Troubleshooting (ABCT) course1. I was delivering that course for close to a decade, and gradually built a decent story explaining the reasoning and use cases behind most of (then available) BGP features, from simple EBGP sessions to BGP route reflectors and communities2.
Now imagine having more than a dozen hands-on labs that go with the “BGP from rookie to hero” story available for any platform of your choice3. I plan to make that work (eventually) as an open-source project that you’ll be able to download and run free-of-charge.
New Project: BGP Hands-On Labs
Long story short: I decided to create open-source BGP configuration labs, and (so far) created a superset of labs we used in an ancient Advanced BGP Configuration and Troubleshooting (ABCT) course
Stable Diffusion Web UI on Linux
In this tutorial, I will share my experience installing the web-based user interface for Stable […]
The post Stable Diffusion Web UI on Linux first appeared on Brezular's Blog.
Day Two Cloud 205: States Of Quantum Computing With Abby Mitchell
Today's Day Two Cloud peers inside the box of quantum computing. We explore how it works, what qbits are and why they matter, the current state of quantum computing hardware, what problems could be solved with quantum computing, and how you can get involved with it via the Qiskit open-source project. Our guest is Abby Mitchell, Quantum Developer Advocate at IBM.
The post Day Two Cloud 205: States Of Quantum Computing With Abby Mitchell appeared first on Packet Pushers.
Day Two Cloud 205: States Of Quantum Computing With Abby Mitchell
Today's Day Two Cloud peers inside the box of quantum computing. We explore how it works, what qbits are and why they matter, the current state of quantum computing hardware, what problems could be solved with quantum computing, and how you can get involved with it via the Qiskit open-source project. Our guest is Abby Mitchell, Quantum Developer Advocate at IBM.HS053 IT Facilities in 2023
The use of physical infrastructure has changed substantially in the last three years. Data centres are scaling down, offices and branches are being re-considered. One view is that offices are ‘playgrounds’ where white collar workers gather to chat, socialise, drink free coffee and have face-to-face for one or two days a week. An opposing view is that its legacy way of working but it will take time for people to adapt to remote work.
The post HS053 IT Facilities in 2023 appeared first on Packet Pushers.
HS053: IT Facilities in 2023
The use of physical infrastructure has changed substantially in the last three years. Data centres are scaling down, offices and branches are being re-considered. One view is that offices are ‘playgrounds’ where white collar workers gather to chat, socialise, drink free coffee and have face-to-face for one or two days a week. An opposing view is that its legacy way of working but it will take time for people to adapt to remote work.Hardening Workers KV
Over the last couple of months, Workers KV has suffered from a series of incidents, culminating in three back-to-back incidents during the week of July 17th, 2023. These incidents have directly impacted customers that rely on KV — and this isn’t good enough.
We’re going to share the work we have done to understand why KV has had such a spate of incidents and, more importantly, share in depth what we’re doing to dramatically improve how we deploy changes to KV going forward.
Workers KV?
Workers KV — or just “KV” — is a key-value service for storing data: specifically, data with high read throughput requirements. It’s especially useful for user configuration, service routing, small assets and/or authentication data.
We use KV extensively inside Cloudflare too, with Cloudflare Access (part of our Zero Trust suite) and Cloudflare Pages being some of our highest profile internal customers. Both teams benefit from KV’s ability to keep regularly accessed key-value pairs close to where they’re accessed, as well its ability to scale out horizontally without any need to become an expert in operating KV.
Given Cloudflare’s extensive use of KV, it wasn’t just external customers impacted. Our own internal teams felt the pain Continue reading
Cloudflare Workers database integration with Upstash


During Developer Week we announced Database Integrations on Workers a new and seamless way to connect with some of the most popular databases. You select the provider, authorize through an OAuth2 flow and automatically get the right configuration stored as encrypted environment variables to your Worker.
Today we are thrilled to announce that we have been working with Upstash to expand our integrations catalog. We are now offering three new integrations: Upstash Redis, Upstash Kafka and Upstash QStash. These integrations allow our customers to unlock new capabilities on Workers. Providing them with a broader range of options to meet their specific requirements.
Add the integration
We are going to show the setup process using the Upstash Redis integration.
Select your Worker, go to the Settings tab, select the Integrations tab to see all the available integrations.
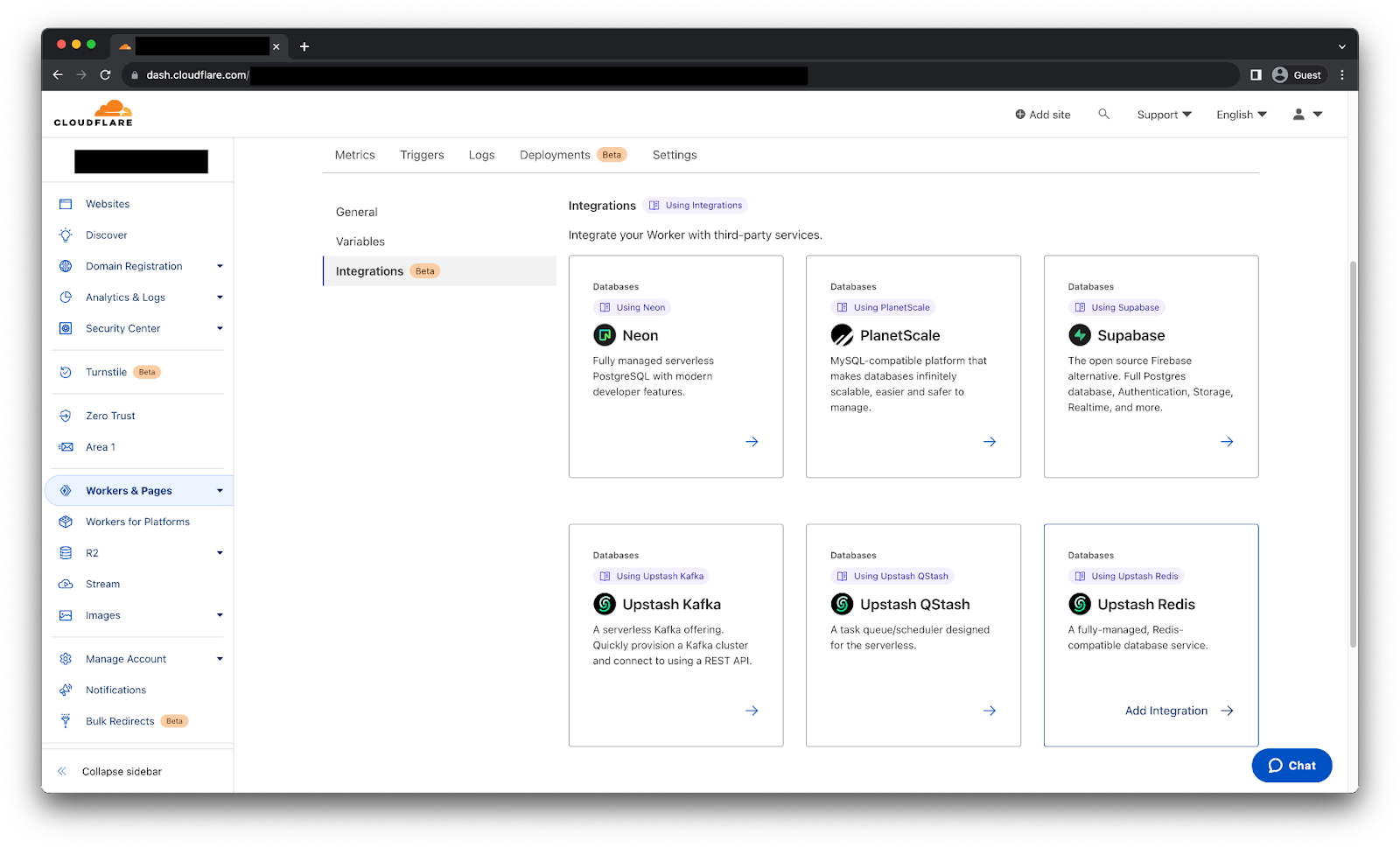
After selecting the Upstash Redis integration we will get the following page.
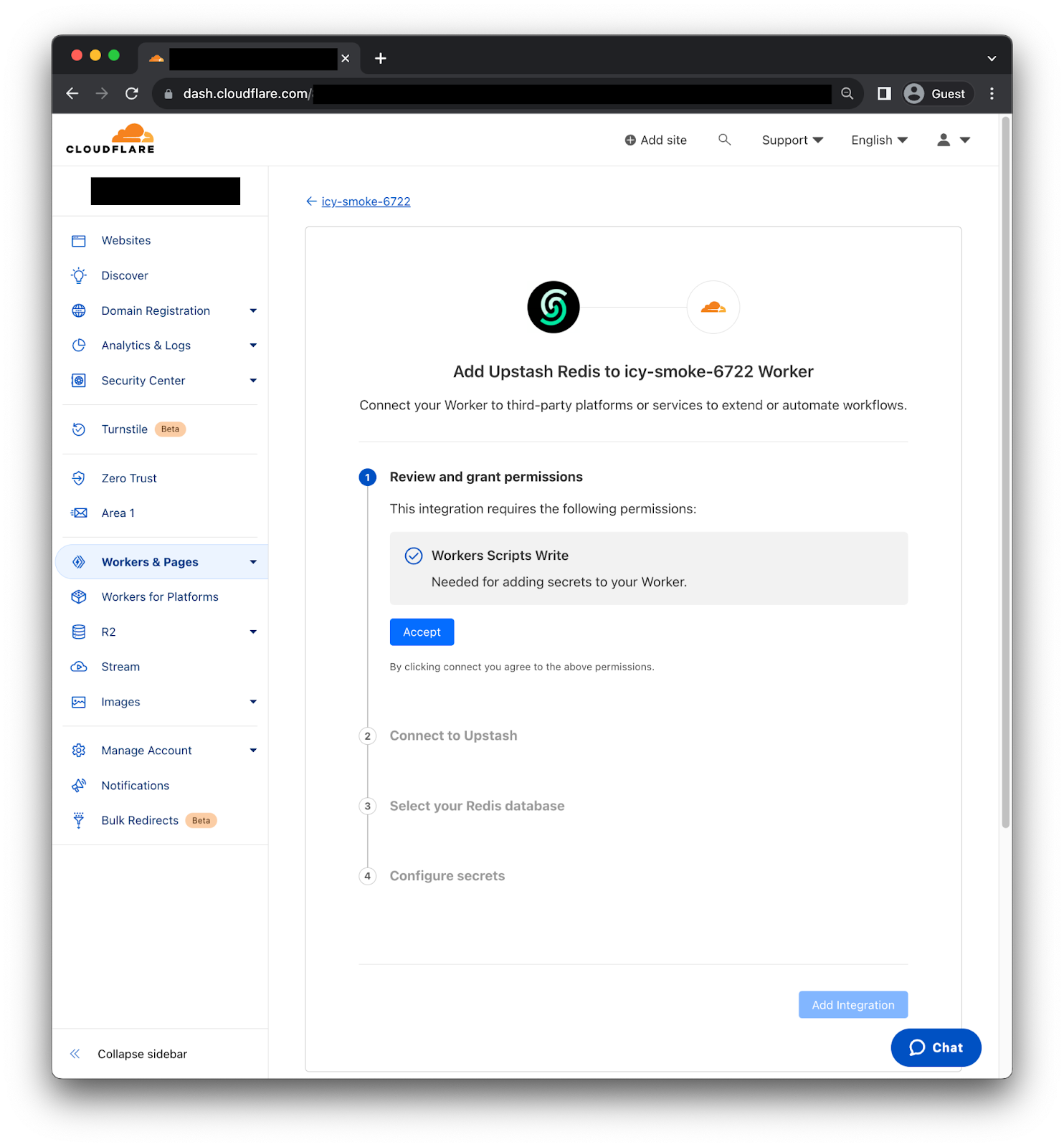
First, you need to review and grant permissions, so the Integration can add secrets to your Worker. Second, we need to connect to Upstash using the OAuth2 flow. Third, select the Redis database we want to use. Then, the Integration will fetch the right information to generate the credentials. Finally, click “Add Continue reading