BT Likes the Potential of NFV Containers
 Try not to overdo the overlays, though.
Try not to overdo the overlays, though.
Datanauts 055: All About Scaling Out
The Datanauts delve into the nitty-gritty of how scale-out works for servers, networking, and storage; what it means for application design and operations; and how vendors, open source projects, and cloud services are positioning themselves in a scale-out world. The post Datanauts 055: All About Scaling Out appeared first on Packet Pushers.Facebook And Google Building Transpacific Cable
Internet giants team up on super-fast undersea link between Hong Kong and Los Angeles.
Ericsson’s Stock Plunges on Warning of Weak Earnings
 It's stock is down 18 percent this morning.
It's stock is down 18 percent this morning.
Legacy TLS cipher support in Firefox
After upgrading Firefox recently, I noticed that I could no longer access certain embedded devices via HTTPS. It seems that recent versions of Firefox and Chrome no longer support certain TLS ciphers due to recently discovered vulnerabilities. That's all well and good, except the error returned offers no recourse if you need to connect anyway.

Firefox returns the error SSL_ERROR_NO_CYPHER_OVERLAP with no option to temporarily allow connectivity. (Chrome reports a similar error named ERR_SSL_VERSION_OR_CIPHER_MISMATCH.) Presumably, this choice was made by the developers with the intention of forcing people to upgrade outdated devices. Unfortunately, in order to upgrade an out-of-date device, we typically must first be able to connect to it. I wasted a fair bit of time digging up a solution, so I figured I'd document the workaround here for when I inevitably run into this problem again a year from now and have forgotten what I did.
Legacy TLS cipher support in Firefox
After upgrading Firefox recently, I noticed that I could no longer access certain embedded devices via HTTPS. It seems that recent versions of Firefox and Chrome no longer support certain TLS ciphers due to recently discovered vulnerabilities. That's all well and good, except the error returned offers no recourse if you need to connect anyway.

Firefox returns the error SSL_ERROR_NO_CYPHER_OVERLAP with no option to temporarily allow connectivity. (Chrome reports a similar error named ERR_SSL_VERSION_OR_CIPHER_MISMATCH.) Presumably, this choice was made by the developers with the intention of forcing people to upgrade outdated devices. Unfortunately, in order to upgrade an out-of-date device, we typically must first be able to connect to it. I wasted a fair bit of time digging up a solution, so I figured I'd document the workaround here for when I inevitably run into this problem again a year from now and have forgotten what I did.
Legacy TLS cipher support in Firefox
After upgrading Firefox recently, I noticed that I could no longer access certain embedded devices via HTTPS. It seems that recent versions of Firefox and Chrome no longer support certain TLS ciphers due to recently discovered vulnerabilities. That's all well and good, except the error returned offers no recourse if you need to connect anyway.
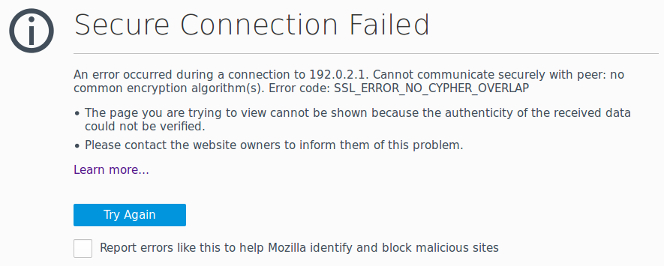
Firefox returns the error SSL_ERROR_NO_CYPHER_OVERLAP with no option to temporarily allow connectivity. (Chrome reports a similar error named ERR_SSL_VERSION_OR_CIPHER_MISMATCH.) Presumably, this choice was made by the developers with the intention of forcing people to upgrade outdated devices. Unfortunately, in order to upgrade an out-of-date device, we typically must first be able to connect to it. I wasted a fair bit of time digging up a solution, so I figured I'd document the workaround here for when I inevitably run into this problem again a year from now and have forgotten what I did.
Reaction: DNS is Part of the Stack
Over at ipspace.net, Ivan is discussing using DNS to program firewall rules—
Could you use DNS names to translate human-readable rules into packet filters? The traditional answer was “no, because I don’t trust DNS”.
This has been a pet peeve of mine for some years—particularly after my time at Verisign Labs, looking at the DNS system, and its interaction with the control plane, in some detail. I’m just going to say this simply and plainly; maybe someone, somewhere, will pay attention—
The Domain Name System is a part of the IP networking stack.
Network engineers and application developers seem to treat DNS as some sort of red-headed-stepchild; it’s best if we just hide it in some little corner someplace, and hope someone figures out how to make it work, but we’re not going to act like it should or will work. We’re just going to ignore it, and somehow hope it goes away so we don’t have to deal with it.
Let’s look at some of the wonderful ideas this we’ll just ignore DNS has brought us over the years, like, “let’s embed the IP address in the packet someplace so we know who we’re talking to,” and “we Continue reading
Colt Rolls Out SD-WAN to 13 European Countries
 Colt moves from proprietary routers to x86.
Colt moves from proprietary routers to x86.
US Cellular Used Nokia’s AirScale Platform For 5G Tests
 Both indoor and outdoor tests resulted in speeds of 5 Gb/s and latency under 2 milliseconds.
Both indoor and outdoor tests resulted in speeds of 5 Gb/s and latency under 2 milliseconds.