Kubernetes Unpacked 025: The Kubernetes Developer Experience
Michael Levan and Calvin Hendryx-Parker talk about their experience using Kubernetes, the pros and cons of the orchestration platform, and its impact on infrastructure engineers and developers. Calvin offers great tips on how to make the developer experience better and what platform engineering teams can do to make everyone’s job flow properly.MLAG Clusters without a Physical Peer Link
With the widespread deployment of Ethernet-over-something technologies, it became possible to build MLAG clusters without a physical peer link, replacing it with a virtual link across the core fabric. Avaya was one of the first vendors to implement virtual peer links with Provider Backbone Bridging (PBB) transport, and some data center switching vendors (example: Cisco) offer similar functionality with VXLAN transport.
MLAG Clusters without a Physical Peer Link
With the widespread deployment of Ethernet-over-something technologies, it became possible to build MLAG clusters without a physical peer link, replacing it with a virtual link across the core fabric. Avaya was one of the first vendors to implement virtual peer links with Provider Backbone Bridging (PBB) transport, and some data center switching vendors (example: Cisco) offer similar functionality with VXLAN transport.
What is IP Subnetting? How to Subnet IP Network Addresses
Learn purpose of IP subnetting, how to read IP subnet addresses, and best practices for creating and deploying multiple subnets within your organization.The Need for a Source of Truth in Network Automation
Learn the importance of a Source of Truth (SoT) for successful network automation and how defining the intended network state can fuel your data-driven journey.Cisco Viptela drops the ball

In 2012, we saw the launch of Viptela, a pioneer in SDWAN network solutions. While they weren’t the first in SDWAN, I believe that badge goes to Talari; Viptela was the first company that caught my interest. I first saw what they were doing in 2015 on the Packet Pushers Podcast. Back then, the networking world was on fire with SDWAN offerings.
Sadly in 2017, Cisco purchased Viptela. I’m sure the leadership at Viptela was excited to be acquired by such a large networking company and hoped to develop Viptela to the pinnacle of their vision. But – despite calling themselves, and being repeatedly lamented for doing so, “a software company”, Cisco did what they so often do. They stopped platform development and tried to lower costs by integrating the vEdge software into their own. While I haven’t personally used the hybrid code, I haven’t heard good things from my coworkers. Eventually, we got the ISR1100 platform running Viptela code, but that was only a substitute for the vEdge 100 and 1000. We have still yet to see a replacement for the vEdge 2000.
May 9, 2023 – 6:57 AM UTC
certificate-status Installed
certificate-validity Not Valid – certificate has expired Continue reading
How the coronation of King Charles III affected Internet traffic


When major events in a country happen Internet traffic patterns are often impacted, depending on the type of event. But what about the coronation of a king or queen? There’s no similar precedent, with a worldwide impact, in the Internet age, except maybe the coronation of the king of Thailand, in 2019. The last time it happened in the United Kingdom was 70 years ago (June 2, 1953), with Queen Elizabeth II; it was the first British coronation to be fully televised. Neither the Internet nor ARPANET were around at the time.
Imagine a grand royal event (if you saw the broadcast or the news, there’s no need), filled with pomp and pageantry, that's so captivating it impacts Internet traffic. That's what happened during the coronation of Charles III and Camilla, the newly crowned king and queen of the United Kingdom and other Commonwealth realms. As the coronation ceremony unfolded, on Saturday morning, May 6, 2023, there were clear spikes and dips in traffic, each coinciding with key moments of the ceremony.
Then came Sunday, and with it, the Coronation Big Lunch event. As the nation sat down to enjoy a communal meal throughout the country, Internet traffic took a Continue reading
Upcoming Course: Data Center Fabrics
On the 19th and 22nd (Friday and Monday) I’m teaching the two-part series on Data Center Fabrics and Control Planes over at Safari Books Online. This is six hours total training covering everything from Clos fabrics to eVPN.
If you register for the course you can access a recording at a later date. From Safari:
This class consists of two three-hour sessions. The first session will focus on the physical topology, including a short history of spine-and-leaf fabrics, the characteristics of fabrics (versus the broader characteristics of a network), and laying out a spine-and-leaf network to support fabric lifecycle and scaling the network out. The first session will also consider the positive and negative aspects of using single- and multi-forwarding engine (FE) devices to build a fabric, and various aspects of fabric resilience. The second session will begin with transport considerations and quality of experience. The session will then consider underlay control planes, including BGP and IS-IS, and the positive and negative aspects of each. Routing to the host and the interaction between the control plane and automation will be considered in this session, as well. EVPN as an overlay control plane will be considered next, and finally Continue reading
Day Two Cloud 194: Unpacking Flexera’s State Of The Cloud Report With Keith Townsend
When you're deep in the trenches of operating your cloud, sometimes it's helpful to step back and get a broader view of what's happening in the industry. On today's Day Two Cloud we explore the results of an annual State of the Cloud survey to get a snapshot of trends impacting the cloud industry, including multicloud adoption, services used, cloud usage and spending, and the challenges of finding and training talent. Our guest to help us unpack the report is Keith Townsend.
The post Day Two Cloud 194: Unpacking Flexera’s State Of The Cloud Report With Keith Townsend appeared first on Packet Pushers.
Day Two Cloud 194: Unpacking Flexera’s State Of The Cloud Report With Keith Townsend
When you're deep in the trenches of operating your cloud, sometimes it's helpful to step back and get a broader view of what's happening in the industry. On today's Day Two Cloud we explore the results of an annual State of the Cloud survey to get a snapshot of trends impacting the cloud industry, including multicloud adoption, services used, cloud usage and spending, and the challenges of finding and training talent. Our guest to help us unpack the report is Keith Townsend.Introducing Object Lifecycle Management for Cloudflare R2


Last year, R2 made its debut, providing developers with object storage while eliminating the burden of egress fees. (For many, egress costs account for over half of their object storage bills!) Since R2’s launch, tens of thousands of developers have chosen it to store data for many different types of applications.
But for some applications, data stored in R2 doesn’t need to be retained forever. Over time, as this data grows, it can unnecessarily lead to higher storage costs. Today, we’re excited to announce that Object Lifecycle Management for R2 is generally available, allowing you to effectively manage object expiration, all from the R2 dashboard or via our API.
Object Lifecycle Management
Object lifecycles give you the ability to define rules (up to 1,000) that determine how long objects uploaded to your bucket are kept. For example, by implementing an object lifecycle rule that deletes objects after 30 days, you could automatically delete outdated logs or temporary files. You can also define rules to abort unfinished multipart uploads that are sitting around and contributing to storage costs.
Getting started with object lifecycles in R2
Cloudflare dashboard
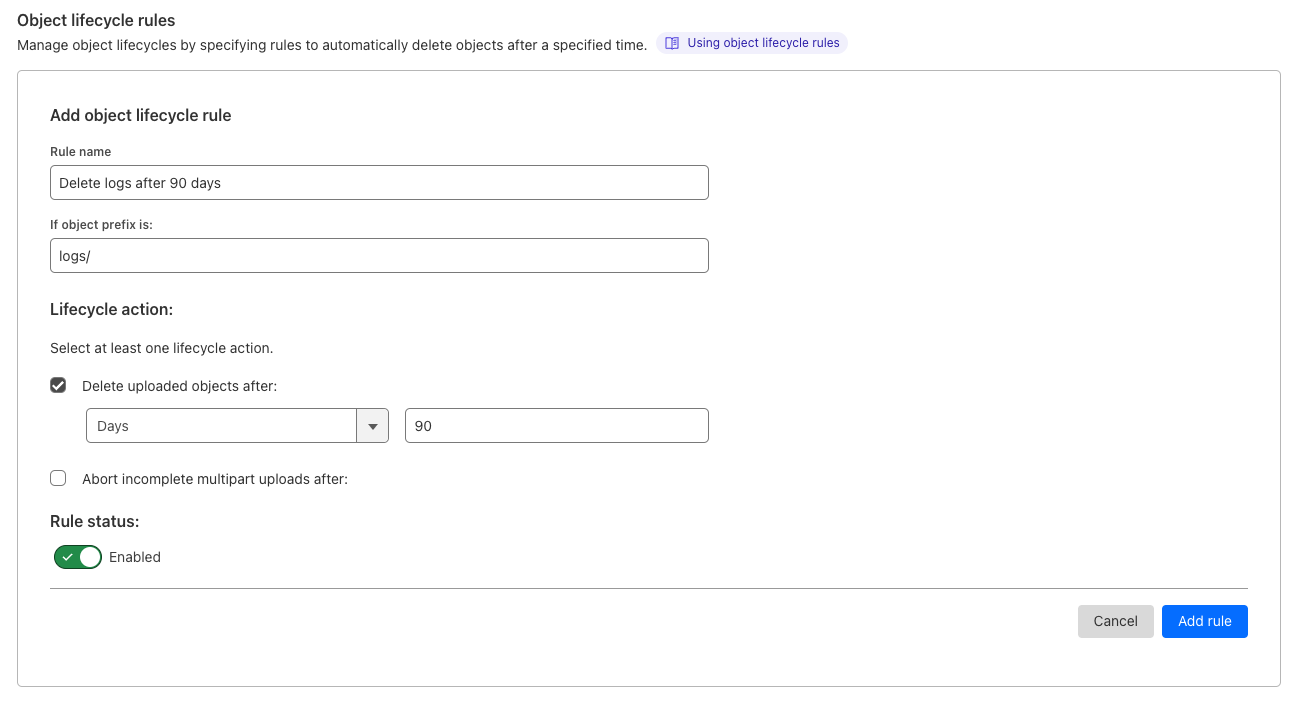
- From the Cloudflare dashboard, select R2.
- Select your R2 bucket.
- Navigate to Continue reading
Is ChatGPT an Efficiency Multiplier?
I got this comment on one of my ChatGPT-related posts:
It does save time for things like converting output to YAML (I do not feed it proprietary information), or have it write scripts in various languages, converting configs from one vendor to another, although often they are not complete or correct they save time so regardless of what we think of it, it is an efficiency multiplier.
I received similar feedback several times, but found that the real answer (as is too often the case) is It Depends.