Brief Me At Interop?
Want to brief me about your product or otherwise have a chat? Send an e-mail to [email protected] while there's still room on my calendar. I look forward to seeing you at Interop!Badu Networks WarpGateway Improves Internet for Wifi
Badu Networks WarpGateway is a TCP proxy appliance improving Internet performance for wireless clients.
The post Badu Networks WarpGateway Improves Internet for Wifi appeared first on Packet Pushers.
Badu Networks WarpGateway Improves Internet for Wifi
Badu Networks WarpGateway is a TCP proxy appliance improving Internet performance for wireless clients.
The post Badu Networks WarpGateway Improves Internet for Wifi appeared first on Packet Pushers.
Taipei: CloudFlare’s 77th Data Center is Now Live
台北:CloudFlare的第七十七個數據中心已經上線喔!

We are excited to announce the launch of our Taipei data center, which is our 28th data center in Asia, and our 77th data center globally. Millions of websites which were previously served from Hong Kong are now served locally from Taipei.
我們高興地宣布CloudFlare的的台北機房建置完成。這是我們在亞洲的第二十八個,在全球的第七十七個數據中心。從現在起台灣的網民可以直接從CloudFlare在台北的節點訪問數以百萬計的網站,不再繞道到香港。
Taipei today
今天的台北

Taipei, home to many renowned tech companies, is famous not only for its vibrant night markets, but also for its warm and welcoming people. From soup dumplings to computer peripherals to Kangsi Coming, its contribution to the world is enormous.
科技重鎮台北,不單擁用充滿活力的夜市,台北人的熱情而友善的人情味也是舉世聞名的。從小籠包、電腦周邊零件到康熙來了,台北對世界的貢獻碩大無朋。
Improved availability and performance
更進一步的可用性和性能
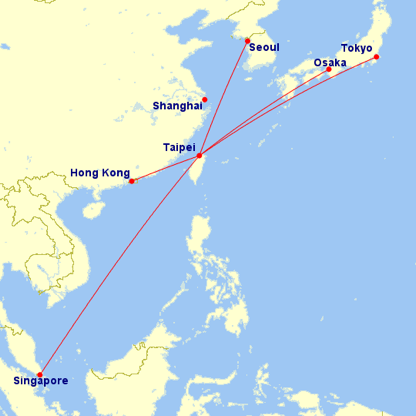
Taipei has one of the fastest Internet speeds. Yet, being located far away from other Internet interconnect centers makes for some unique challenges. When traffic is delivered to local eyeballs from Hong Kong, Tokyo, Singapore or worse-still Los Angeles, it is often subject to long latency and the constraints of limited capacity before arriving in Taipei. Additionally, traffic flowing on undersea cables around Taipei have been subject to cable cuts over the years, mainly because of the active fault lines around the island.
台北有世界上首屈一指的網路速度。可是,因為台北和其他互聯網交換中心的距離,來自香港,東京,甚至洛杉磯的流量往往要通過高延時和有限的頻寬才能傳送到台北。另外,台北位於板塊交界處,地震發生頻繁,海底電䌫中斷時有發生。
With the launch of our Taipei data center, visitors to millions of CloudFlare websites will experience a 4x improvement in performance and Continue reading
Cultural Shifts: Telcos Insist Employees Adapt for SDN
 AT&T isn't the only one retraining its employees.
AT&T isn't the only one retraining its employees.
Failover Mechanism Part-1
Redundancy is must for ISP in Core and also its equally important for Enterprise
to have network up always thus resulting in zero business impact due to network outage.
There are different scenarios of failover mechanism depending upon the requirement.
First of its kind is Dual POP Dual last mile Dual CE (DPDLDC). It provides redundancy both for WAN connectivity as well as LAN connectivity.
DUAL POP—customer primary and secondary link terminated on different PE router.
DUAL LAST MILE—last mile connectivity between PE and CE is different for primary and secondary
DUAL CE -Primary and secondary terminated on different CPE device.
I would be sharing Multiple Scenarios of Fail over Mechanism in coming posts.
ISP is very much transparent in this scenario, traffic control is being done from CPE end.
Considering the below topology

Failover Mechanism —
1. Outgoing Traffic from CPE wan is controlled using HSRP + IP SLA
2. Incoming traffic to CPE is controlled using AS Path Prepend attribute of BGP at secondary( lower as path count , better path)
Normal Scenerio
1)Primary WAN link is up .HSRP running towards LAN is active state. Secondary link is having AS-Prepend so primary link is preferred with having less number Continue reading
How to manage IT in a growing business: Implementing IT policies
Although vendor-written, this contributed piece does not promote a product or service and has been edited and approved by Network World editors.
As business leaders grow their companies, corporate assets should always be top of mind. As such, business leaders should be implementing IT policies early on in order to set standards and expectations for employees when it comes to the use of corporate technology and managing corporate data.
In parts one and two of this three-part series, I rolled out a playbook on when companies should hire their first IT consultant and what to keep in mind when appointing a CIO. In this third and final part of this series on the IT Lifecycle I’ll discuss when companies should start rolling out formal IT policies and how to do so.
To read this article in full or to leave a comment, please click here
How to manage IT in a growing business: Appointing a CIO
Although vendor-written, this contributed piece does not promote a product or service and has been edited and approved by Network World editors.
Timing is everything when hiring a CIO. The primary function of a CIO is to be forward-looking for developing and implementing IT initiatives, but it can be difficult for a CIO to fulfill this duty if he or she is brought in too late and provided with inadequate technologies and processes. The earlier a company invests in a CIO, the earlier everyone can be in tune with what will make the business most efficient. But most companies don’t know when it’s too early and when it’s too late.
In the first article of this three-part series on the IT Lifecycle, I discussed recommendations for when to hire an IT consultant, and what to consider when doing so. During this process, it’s important to recognize when a CIO will be a valuable addition. In this second part of the series, I will continue to follow Joe’s Widget Shop, a hypothetical software development company, as they move onto the next stage in the IT lifecycle. I’ll provide you with insight on what to look for when appointing a CIO Continue reading
