IPv6 Microsegmentation in Data Center Environments
The proponents of microsegmentation solutions would love you to believe that it takes no more than somewhat-stateful packet filters sitting in front of the VMs to get rid of traditional subnets. As I explained in my IPv6 Microsegmentation talk (links below), you need more if you want to have machines from multiple security domains sitting in the same subnet – from RA guard to DHCPv6 and ND inspection.
Read more ...Enterprise IoT Adoption Sluggish So Far
Companies cite security and ROI concerns as barriers to IOT deployment, study shows.
Packet Analysis: HSRP, EIGRP, STP And CDP
In this video, Tony Fortunato covers packet analysis and key protocol considerations.
iPexpert’s Newest “CCIE Wall of Fame” Additions 1/22/2016
Please join us in congratulating the following iPexpert students who have passed their CCIE lab!
CloudFlare launches new data centers in Oslo and Minneapolis
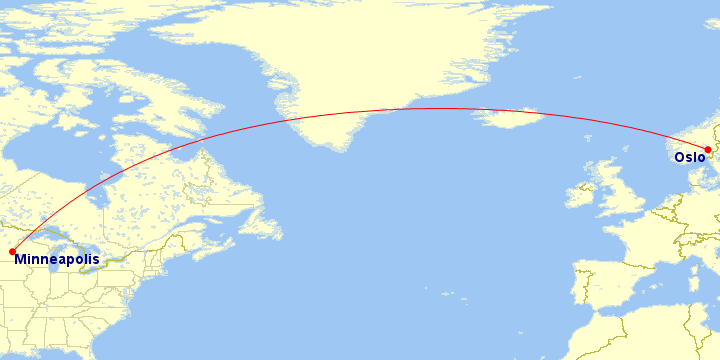
Four thousand miles (6,400 kilometers) separate CloudFlare’s latest two data centers: Oslo (#75) and Minneapolis (#76).
Oslo
In Oslo, we have now built our third data center in Scandinavia. This joins our existing facilities in Stockholm and Copenhagen. With a data center in Norway, we recognize an important country that stands above others with a staggering 95.05% of the population having Internet connectivity. This Internet penetration rate is the fourth best in the world. For reference, the Internet penetration rate in the US is 84%, the UK is 90% and Egypt, where we deployed our last data center it is only 50%
At 59.9500° N, Oslo is also the “northernmost” CloudFlare data center on our network map.
Oslo, according to the Norwegian Sagas is over 1,000 years old. CloudFlare has built itself into a facility just a handful of years old and while we respect all the wonderful history and tradition associated with Norway, we hope the locals appreciate our 21st century choice.
Norway has a very important position within the history of the Internet (well the ARPANET actually). In June 1973, the Royal Radar Establishment in Norway became one of the first international connections to Continue reading
Why Security is a Leading Network Virtualization Driver
 The SDxCentral research team dug into dozens of network virtualization customer customer case studies and use cases. We found one common characteristic emerging as a driver for many customer deployments: Security.
The SDxCentral research team dug into dozens of network virtualization customer customer case studies and use cases. We found one common characteristic emerging as a driver for many customer deployments: Security.
Sacramento Kings choose Ruckus to put extra bounce in their arena Wi-Fi
By Kash Shaikh, vice president of marketing Out with the old, in with the new. It’s a familiar phrase that still holds true. Civilization around the globe has drastically changed due to one thing: Wi-Fi. Something we lived without for...Cumulus Raises $35M
 The company has lost value in the past 2 years.
The company has lost value in the past 2 years.
Cisco ACI Policy Model Paves the Way for IT, Business Opportunities
 How much time does your network staff spend on keeping the ship upright? Simplified automation through Cisco ACI frees them to concentrate on more high-level, profitable challenges.
How much time does your network staff spend on keeping the ship upright? Simplified automation through Cisco ACI frees them to concentrate on more high-level, profitable challenges.
Silver Peak Unity EdgeConnect SD WAN – Is It Any Good?

Ok, so Silver Peak offers yet another SD-WAN solution, you say? Well yes, but is it really possible to have too many options when it comes to broadband and hybrid WANs? I say no; the more choice we have, the more likely we can find the right solution for each situation and the more each vendor is encouraged to feature match with the others. With that in mind, let’s take a look at what Silver Peak offers and perhaps see how it is differentiated from the other solutions on the market.
What Is SD WAN?
Last year I wrote a brief definition of SD WAN as I see it, and for convenience I will reproduce that here as a reference point:
SD WAN is a solution that uses real time WAN link performance monitoring and data packet inspection to autonomously manage the distribution of network traffic across multiple, likely heterogenous, WAN links with the aim of improving and optimizing WAN performance in alignment with the business requirements.
My definition is intentionally vague about how such lofty goals should be accomplished, and that’s inevitably where the special sauce of each solution comes in.
Silver Peak WAN Optimization
Silver Peak sees two Continue reading
